Lightweight Directory Access Protocol (LDAP) is an integral component of digital identity frameworks, providing an open and cross-platform protocol used for directory service authentication. It provides a systematic method for querying and modifying items in a directory service, essentially facilitating access to an ordered and distributed set of records, or objects, in a network.
Before LDAP, there was the Directory Access Protocol (DAP), designed to access the X.500 directory. However, its requirement for sizable resources made it difficult for smaller computers and devices to handle. This protocol was conceived as a lightweight alternative to DAP, providing similar functionality with less resource overhead.
LDAP has evolved to play a crucial role in managing diverse sets of networked data efficiently. Its versatility and adaptability have seen it evolve from LDAPv1 to LDAPv3, each iteration representing significant advancements in functionality, security, and performance. Understanding this protocol is crucial due to its pervasive use in many organizations’ network infrastructures. Its role in organizing and accessing data effectively, user management, and safeguarding sensitive information, makes LDAP fundamental to many networked systems and operations.
Basic Concepts Related to LDAP
To understand the Lightweight Directory Access Protocol, it is essential to grasp a few fundamental concepts:
Key LDAP Features
- Hierarchical Structure: LDAP adopts a tree-like structure, organizing data hierarchically. This facilitates efficient data retrieval and management.
- Portability: LDAP is platform-independent, ensuring seamless integration across diverse environments.
- Security Measures: With robust authentication mechanisms and secure data transmission, LDAP safeguards sensitive information.
LDAP Use Cases & Applications
LDAP finds applications across various sectors, making it a versatile solution for identity management. Its main applications are as follows:
Directory Service
A directory server may use LDAP to query its records. User credentials and access rights are stored in a directory, and applications can use it to authenticate users against this directory. This protocol can be used to manage and enforce access control policies. It helps determine which resources and services a user is allowed to access, which is known as authorization.
Address Book and Contact Management
LDAP is employed for creating and managing address books and contact directories. Email clients, such as Microsoft Outlook and Thunderbird, often use this protocol to access and search for contact information.
Single Sign-On (SSO)
LDAP is an integral part of many single sign-on solutions. It allows users to log in once and access multiple applications and services without the need to log in separately for each.
Network Services
LDAP is used in network services for centralized management of network resources, such as printers, file servers, and other devices. This streamlines administration and ensures consistent access across the network.
Logging and Auditing
LDAP can be used to store and retrieve audit logs and other security-related information. This is crucial for monitoring and analyzing user activities within an organization.
Web Application Authentication
Many web applications use LDAP for user authentication. This is particularly common in enterprise environments where a central directory is used to manage user identities.
Security Services
LDAP plays a crucial role in security services by providing a standardized way to store and retrieve security-related information, such as digital certificates and public keys.
Cloud Services
Some cloud services use LDAP for user authentication and authorization. LDAP integration allows organizations to extend their existing directory service to manage access to cloud-based resources. It’s important to note, however, that this is often achieved by creating a duplicate cloud server that syncs with the LDAP directory server due to LDAP’s ties to on-premise infrastructure.
System and Application Integration
LDAP is utilized for integrating various systems and applications, providing a standardized mechanism for exchanging directory information between different platforms.
LDAP Architecture
An understanding of the LDAP architecture is invaluable to fully grasp how it operates. Let’s explore this structure.
LDAP Models
The LDAP model consists of four parts:
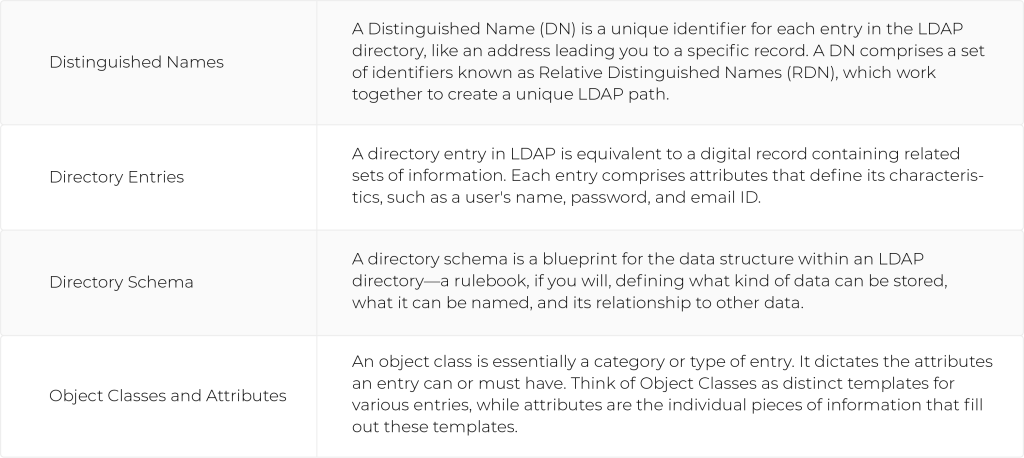
- Information Model: This model represents the data structure within an LDAP directory, defining the entries, attributes, and schema.
- Naming Model: The Naming Model underpins the process of assigning unique DNs to entries. It’s like the postal system of the LDAP world, ensuring each ‘address’ is unique.
- Functional Model: The Functional Model outlines the operations that can be performed within an LDAP directory, like searching, modifying, and deleting entries.
- Security Model: This Model is concerned with user authentication and access control, ensuring valuable data is kept secure.
LDAP Directory Structure
An LDAP directory can be organized into two types of structures:
- Hierarchical Structure: This structure organizes data in a tree-like system. It’s intuitive and optimal for large databases with clear hierarchies.
- Flat Structure: This structure presents data in a single-level file system, optimal for less complex, smaller databases.
LDAP Protocol
The LDAP Protocol defines the rules and formats for communication between the client and the LDAP server. It’s the backbone of the protocol, governing the flow of information and ensuring smooth operation.
LDAP Server
LDAP servers are the backbone of LDAP operations. They store the data from the directory server and handle client requests. They provide a centralized way to manage users, groups, and devices in a network. They handle operations like retrieving user data, managing network resources, synchronizing passwords, and enforcing security policies. Their robust functionality and flexibility make them an invaluable resource in various network environments and a crucial component in system administration, identity management, and access control, as outlined above.
How Does LDAP Work?
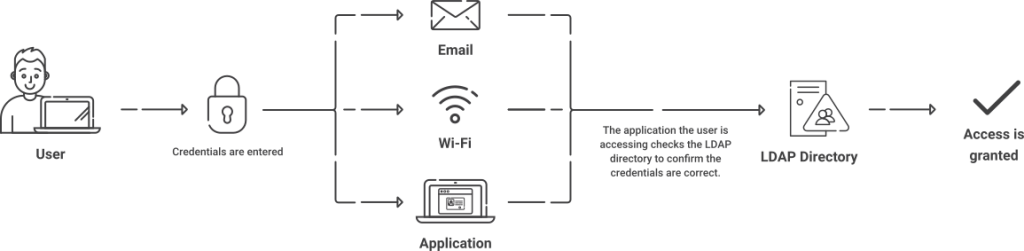
The primary role of LDAP is to provide a mechanism for querying and modifying items in a directory server. So, how does it accomplish this? Let’s break down the various operations and processes involved.
LDAP Operations and Processes
LDAP’s functioning revolves around a series of distinct operations:
Connect Operation
The connect operation establishes a network connection between a client and LDAP server. It’s the equivalent of dialing a number on your phone—you’re making the first move to start a conversation.
Bind Operation
Following the connection, the bind operation authenticates the client to the LDAP server. Is it a trusted client?
Search Operation
The search operation is used by clients to retrieve information from the LDAP database. It’s akin to using a library’s computer system to locate a book.
Modify Operation
The modify operation allows clients to make changes to the directory’s entries. Think of it like editing an entry in your contacts list—adding a new phone number or changing an email address.
Add Operation
Add operation facilitates clients to add new entries to the directory. It’s like adding a new contact to your phone—you provide a name, number, and other relevant details.
Delete Operation
The delete operation enables clients to remove entries from the LDAP directory. It’s much like deleting an unwanted contact from your phone.
LDAP Sessions and Connections
Just as you have calls and messaging sessions with people, you also have sessions and connections in LDAP. These precisely define the stateful interaction between the client and the LDAP server.
LDAP Replication and Its Benefits
LDAP also supports replication—creating multiple copies of the directory database. This ensures robust data protection and provides redundancy in case of system failure.
LDAP Security
In a world rife with data breaches and cyber-attacks, let’s explore how this protocol shields its users and their information.
LDAP Authorization
LDAP plays a significant role in systems access authorization by defining and enforcing user management policies, similar to a bouncer allowing individuals into a club based on set criteria.
LDAP Authentication
LDAP also handles user authentication. LDAP authentication verifies users’ identities before granting them access to resources, much like a login system.
LDAP authentication works by connecting a client to an LDAP server, where user credentials are stored. The client sends a username and password. If the credentials match with the ones on the server, access is granted. If they don’t match, the server rejects the client’s access request.
RADIUS Authentication with LDAP
There are many resources out there that compare LDAP and RADIUS. While they both can perform similar functions, it doesn’t make much sense to compare considering that an LDAP server can store user information and a RADIUS server cannot. LDAP doesn’t provide MFA capabilities or accounting logs, but you can perform those functions by adding RADIUS.
If your LDAP server contains your user directory, you can connect a RADIUS server to authenticate against your LDAP directory to authorize access to Wi-Fi, VPN, and all your web applications.
A cloud-based RADIUS server is the best practice for authenticating users because the industry is moving away from on-premise infrastructures. Cloud RADIUS can be integrated into an AD/LDAP environment and dynamically authenticate users by directly referencing the directory. Any policies attributed to a user will be enforced in real-time, simplifying user segmentation.
Cloud RADIUS comes pre-built for 802.1x/EAP-TLS authentication with x.509 certificates, which is an easy way to configure a WPA2-Enterprise network.
LDAPS: Enabling LDAP over SSL/TLS
LDAP security is imperative since it involves the storage and retrieval of sensitive information. However, standard LDAP traffic is not encrypted, leaving it vulnerable to cyber-attacks. LDAP isn’t able to secure authentication on its own, which spawned the implementation of Secure LDAP (LDAPS). After connecting to a client, LDAPS encrypts web traffic with SSL/TLS to establish a bind with the directory.
SSL/TLS encryption is an internet standard because it uses digital x.509 certificates to secure a connection between client and server. Certificates serve as identifiers for the device/server in which it resides.
Most organizations that encrypt LDAP traffic use a username and password for authentication purposes. While that method works, it leaves much to be desired in regard to security. LDAP systems that rely on credential-based authentication are still fairly vulnerable. Passwords can be easily forgotten, shared, and stolen, leaving the network susceptible to over-the-air credential theft.
Worse, the standard LDAP authentication method doesn’t even encrypt web traffic, meaning network admins are left with the job of configuring LDAP to securely encrypt their environments.
The main problem lies with organizations authenticating users with passwords because passwords are insufficient to protect against modern cyber-attacks. Passwords lack the fortitude to stand against modern cyber attacks like the brute force attack, which is a method that sends endless credential attempts, or the man-in-the-middle attack, which pretends to be a legitimate network entity and connects with an approved network user.
Default LDAP settings barely stand a chance against modern cyberattacks. Luckily, there is a better security measure: digital certificates with a PKI.
LDAP Security Strengths and Flaws
While LDAP provides robust security features such as SSL/TLS encryption and robust access controls, it is not without its flaws. For instance, unsecured LDAP can be vulnerable to man-in-the-middle attacks or LDAP injection attacks.
Additionally, LDAP tends to be used in on-premise infrastructure and directory services. This means that organizations looking to move their directory services to the cloud, such as moving from Active Directory to Azure Active Directory (Entra ID), may need to consider using other protocols.
Mitigating LDAP Vulnerabilities
To mitigate potential LDAP vulnerabilities, it is essential to implement best practices such as using secure SSL/TLS connections, employing strong authentication measures, and continuously auditing and monitoring LDAP authentication activities to detect any unusual patterns or breaches.
LDAP in Cloud Computing
As cloud computing continues to dominate the technological landscape, let’s examine how LDAP fits into this picture.
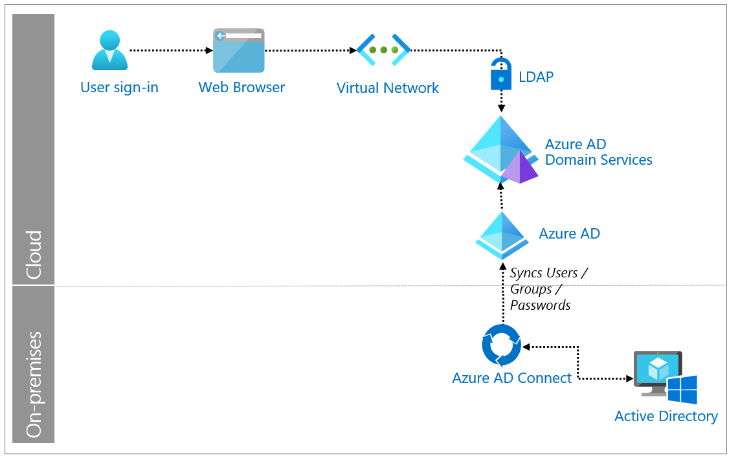
In a cloud context, LDAP can manage users and resources, authorize applications, and facilitate communication between different components.
Cloud-based directory services can be built on LDAP or sync with LDAP servers, offering scalable, robust, and accessible solutions for managing identities and resources. They organize and manage access to a vast array of digital assets.
LDAP can also play a critical role in cloud-based identity management, ensuring users can securely access the resources they need while keeping unwanted entities out. It’s like a digital doorman, checking IDs and controlling access.
Implementation and Use of LDAP
To wrap up our exploration, let’s see how this protocol is implemented and used in various settings.
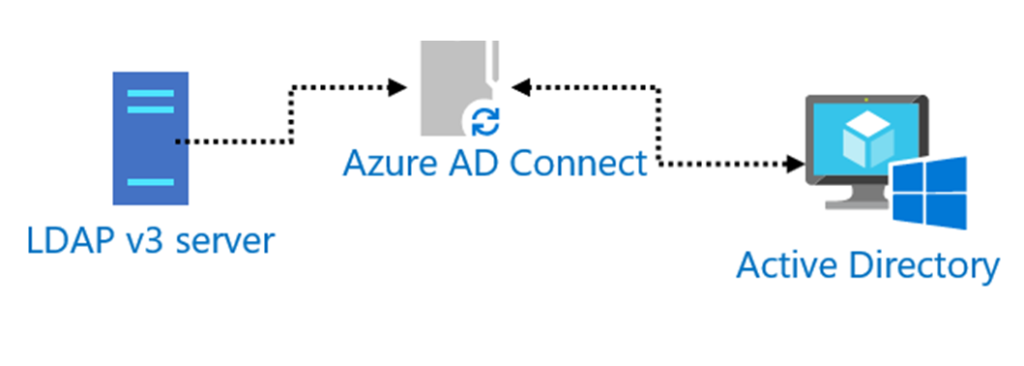
LDAP and Active Directory
LDAP and Active Directory are significant in managing network resources. Active Directory, a Microsoft product and one of the most common directory services, heavily relies on LDAP as its primary protocol to support a wide range of directory-based identity-related services. Essentially, Active Directory uses LDAP to structure and store data in a hierarchical format for swift and efficient data retrieval. Moreover, Active Directory implements LDAP to authenticate and authorize users. Every time a user logs into a network, Active Directory uses LDAP to search for the user’s login details in its database.
Active Directory integrates LDAP to allow users and administrators to manage data. For instance, an administrator can use LDAP commands to add, delete, or modify objects such as users or computers in Active Directory. Also, the interplay between LDAP and Active Directory ensures efficient data replication among servers. In Active Directory, LDAP calls the shots in the synchronization of directory data across multiple servers to maintain consistency. Overall, the resilience and flexibility of LDAP make it an essential component of Active Directory server, improving network management and user experience. It’s, therefore, safe to say Active Directory without LDAP would be a body without a backbone.
LDAP and Azure AD (Microsoft Entra ID)
Azure AD does not use LDAP natively. It uses other protocols. However, in integrating LDAP with Azure Active Directory, this Microsoft cloud-based service effectively becomes a repository for user identities. It provides access to applications and resources, essentially performing LDAP functions, but on a more extensive scale. Azure Active Directory’s synchronization feature seamlessly transfers LDAP data into the cloud, making the centralization and management of Active Directory resources in hybrid environments easier and more efficient.
LDAP as a Lightweight Database for Applications
LDAP serves as a robust but lightweight database for many applications, providing an organized, efficient, and flexible way to manage and access data. It efficiently sorts folders filled with data necessary for applications.
LDAP Application Programming Interface
LDAP Application Programming Interface (API) provides programmers with a set of routines, protocols, and tools for building software and applications. The LDAP API makes integrating directory services into applications a breeze.
LDAP in Intrusion Detection Systems
An Intrusion Detection System often relies on LDAP for managing users and their activities. Through this protocol, suspicious activities or unauthorized access attempts can be monitored and flagged, acting like a vigilant security guard on the lookout for any signs of intrusion.
LDAP Use Cases Across Industries
Industries including healthcare, telecommunications, and e-commerce, use this protocol for managing user identities and authorizations, and for organizing vast amounts of data efficiently.
LDAP Best Practices
To maximize the benefits of LDAP implementation, consider these best practices:
- Regular Backups: Implement a robust LDAP server backup strategy to safeguard critical directory data.
- Access Control: Define granular access controls, ensuring that users only access the information relevant to their roles.
- Scalability: Plan for scalability from the outset, accommodating future growth seamlessly.
Alternatives to Lightweight Directory Access Protocol
Although LDAP sees some use in cloud environments, it’s historically been used in on-premise implementations. It was popularized, for example, in on-premise directory services like Active Directory.
Those looking for more secure alternative protocols for use in the cloud can look to options such as Security Assertion Markup Language (SAML), a cloud-based protocol designed to power secure Single Sign-On in modern cloud environments. OAuth is another authentication protocol that can be used to communicate with cloud directory services to securely authenticate users.
Implementing LDAP Alternatives Quickly and Easily with SecureW2
With an increasing number of organizations looking to move their infrastructure to the cloud, it’s important to look forward for authentication systems and not backward. SecureW2’s managed PKI and RADIUS server work together to integrate with your infrastructure and provide secure, passwordless authentication through cloud-native protocols like OAuth.
We provide everything you need to leverage existing policies in your cloud directory services and apply them to network authentication, application access, and so much more. If you’d like to learn more, check out our pricing and contact us today.