Key Points
- Traditional NAC and on-premise RADIUS servers are complex, rely on vulnerable password-based protocols and are ill-suited for modern, cloud-centric security.
- Upgrading from password to certificate-based authentication significantly strengthens a NAC framework by using a Public Key Infrastructure (PKI) to verify devices and users.
- SecureW2's Cloud RADIUS and managed PKI provide a cloud-based solution that automates the certificate lifecycle and enforce real-time network policies.
Network Access Control (NAC) is an advanced cybersecurity measure designed to regulate who, what, and how entities gain access to network resources. As the traditional security perimeter is no longer sufficient, NAC provides an extra layer of security by enforcing access policies and ensuring that only compliant devices and authorized users gain network access.
Whether safeguarding an internal network from unauthorized access or ensuring endpoint compliance, NAC solutions play a critical role in modern network architecture. This article defines Network Access Control, exploring its architecture, various authentication methods, and comparing it with other network security measures like RADIUS. Additionally, we will provide insights into best practices and step-by-step guidelines for implementing NAC effectively within your existing IT infrastructure.
Learn more about how SecureW2 transformed AEBSD’s network security and streamlined student Wi-Fi access.
What is Network Access Control?
Network Access Control (NAC) is a security solution designed to fortify an organization’s network by regulating how devices and users access network resources. NAC functions as a gatekeeper that enforces predefined access policies, ensuring that only authorized users and compliant devices are granted network access. This is achieved through a combination of authentication, authorization, and endpoint compliance checks. NAC systems operate by integrating with various network components, including policy servers, a Network Access Server (NAS), and wireless access points, to create a comprehensive security architecture.
By continuously monitoring network admissions and enforcing security posture compliance, NAC helps organizations mitigate potential network threats and maintain robust security controls. NAC provides the additional security layer needed to protect sensitive data and critical resources from unauthorized access and network vulnerabilities.
Types of Network Access Control
Network Access Control (NAC) encompasses various types to address different security needs within an organization’s network infrastructure. Each type plays a specific role in ensuring that only authorized users and compliant devices access network resources while mitigating risks from unauthorized users and devices.
Pre-admission NAC
Pre-admission control evaluates devices before they are allowed to connect to the network. This type of NAC performs stringent security posture checks, ensuring that endpoint devices meet compliance standards, such as up-to-date antivirus software and necessary patches. Pre-admission control acts as the frontline defense, preventing unauthorized users and non-compliant devices from gaining access to the network. It is particularly useful for securing wireless networks and protecting remote access points.
Example: A company requires that all laptops connecting to its corporate Wi-Fi network must have the latest antivirus definitions and all critical operating system patches installed. Before a device can connect to the network, a NAC solution checks the device’s security posture. If the laptop does not meet these requirements, it is denied access and redirected to a remediation network where it can download and install necessary updates before attempting to reconnect.
Post-admission NAC
Post-admission control operates by continuously monitoring devices after they have been granted access to the network. This approach ensures ongoing compliance with security policies by regularly performing security posture checks. If a device falls out of compliance, it can be moved to a quarantine network or have its access restricted. Post-admission control provides an additional layer of security by dynamically adjusting access levels based on real-time compliance status.
Example: An organization uses post-admission NAC to monitor devices on its internal network continuously. Suppose an employee’s laptop was compliant when initially connected but subsequently became infected with malware. The NAC system detects the malware and automatically moves the compromised device to a quarantine network, where it can only access minimal resources necessary for remediation, preventing the malware from spreading to other devices on the network.
Role-based Access Control (RBAC)
RBAC assigns network access permissions based on the user’s role within the organization. By categorizing users into different roles, such as administrators, employees, and guests, RBAC ensures that each user has access only to the resources necessary for their job functions. This minimizes the risk of unauthorized access and helps tailor access policies to diverse organizational needs.
Example: In a hospital, different staff members have varying levels of access to patient information. Doctors can access full patient records, including medical history, medications, and lab results. Nurses have access only to the information needed for administering medication and taking vital signs. Administrative staff can access only billing and scheduling information. By using RBAC, the hospital ensures that staff members have access only to the information necessary for their roles, protecting sensitive patient data.
Time-based Access Control
Time-based access control restricts network access based on predefined time windows. For example, employees might only have access during business hours, while certain critical systems could be accessible 24/7. This approach enhances security by reducing the likelihood of unauthorized access outside of designated times, thereby aligning network solutions with organizational security policies.
Example: A financial firm restricts access to its trading systems to business hours (9 AM to 5 PM) for most employees. However, IT and security staff have 24/7 access to monitor and maintain system integrity. During non-business hours, trading systems are inaccessible to regular employees, significantly reducing the risk of unauthorized trading activities or breaches during off-hours.
Components of NAC Architecture
Building a robust Network Access Control architecture involves integrating several critical components that work in unison to enforce access control and ensure network security.
Policy Servers in NAC
Policy servers are like the brain of a NAC system. They store and manage the access policies that govern who can access the network, what resources they can use, and under what conditions. These policies can be intricate, incorporating various factors such as user roles, device types, and real-time security posture checks. The policy server evaluates these factors and makes dynamic access decisions.
Network Access Servers
The Network Access Server (NAS) acts as the gatekeeper, controlling the entry point to the internal network. Upon receiving an access request, the NAS communicates with the policy server to authenticate users and enforce access policies. This ensures that only authorized and compliant devices and users can connect to the network, thus creating a controlled and secure environment.
User and Device Identification Mechanisms
Effective identification mechanisms are essential for a NAC system. These mechanisms involve various methods such as usernames and passwords, digital certificates, or multi-factor authentication. By accurately identifying users and devices, the NAC system can apply the appropriate access policies and ensure that only authorized entities gain network access.
Network Admission Control
Network Admission Control is a specialized subset of NAC focused on evaluating device compliance before granting network access. This involves conducting rigorous security posture checks, such as verifying antivirus updates and security patches, to ensure devices meet organizational standards. Devices that fail to meet these criteria may be quarantined or given limited access until necessary updates are applied.
Quarantine and Guest Network Management
Managing non-compliant devices and guest access is a critical function of a NAC system. Quarantine networks isolate devices that fail to meet security standards, guiding users through remediation steps to achieve compliance. Guest network management provides temporary, restricted access to visitors, ensuring they can connect without compromising sensitive internal resources. This dual approach maintains network integrity while accommodating diverse access needs.
How NAC Works
Network Access Control employs a multi-faceted approach to ensure that only authorized users and compliant devices gain access to network resources. Understanding the intricacies of how NAC works is crucial for implementing a robust security framework.
NAC Authentication Methods
Authentication serves as the first line of defense in NAC, ensuring that only verified users and devices can access the network. There are several NAC authentication methods, including:
- Certificate-based Authentication: Utilizes digital certificates issued by a trusted Certificate Authority (CA) to authenticate users and devices, providing a high level of security through Public Key Infrastructure (PKI).
- Password-based Authentication: Relies on user-provided credentials, such as usernames and passwords. Though widely used, it is considered less secure due to vulnerability to password theft and guessing.
- Multi-Factor Authentication (MFA): Requires multiple forms of identification, such as a password and a biometric scan. This method significantly enhances security by reducing the likelihood of unauthorized access.
- Biometric Authentication: Uses biological characteristics like fingerprints, facial recognition, or retina scans to authenticate users. This method is highly secure due to the uniqueness of biometric data.
Authorization and Accounting in NAC
Once a device or user is authenticated, NAC evaluates their authorization to access specific network resources. This involves:
- Authorization: Determines what resources a user or device can access based on predefined access policies. It checks against criteria such as user roles, device types, and security posture.
- Accounting: Keeps track of user activities on the network, providing visibility into who accessed what resources and when. This helps in ensuring compliance with access policies and identifying potential security breaches.
Endpoint Compliance Checks
Endpoint compliance checks are vital for maintaining network integrity. Before a device gains full network access, it undergoes rigorous compliance checks, including:
- Ensuring that antivirus software is up-to-date
- Verifying the application of necessary security patches
- Checking for proper configurations and settings
Non-compliant devices are often quarantined or given restricted access until they meet the required standards.
Remediation Processes in NAC
When a device fails compliance checks, NAC initiates remediation processes to bring it up to standard. This could involve any of the following or a combination of the following:
- Guiding the user through the installation of required updates
- Applying necessary patches or configuring settings
- Re-running compliance checks to confirm that the device now meets the standards
Only after successful remediation is the device granted full network access.
VLANs for Network Segmentation
Virtual Local Area Networks (VLANs) are integral to NAC for achieving precise network segmentation. By creating isolated network segments, VLANs help in segregating devices based on compliance levels, user roles, and other criteria. For instance, devices that fail compliance checks can be placed into a restricted VLAN with limited network access, ensuring that potential threats are contained. This segmentation not only improves security but also optimizes network performance by reducing unnecessary traffic.
Network Access Control and RADIUS
Network Access Control (NAC) and Remote Authentication Dial-In User Service (RADIUS) are both critical for managing access, but they serve different purposes and offer distinct benefits.
What is a RADIUS Server?
A RADIUS server is used for authenticating and authorizing users who wish to access a network. RADIUS centralizes authentication data and standardizes the process across the network. RADIUS is widely used for managing remote access, but it also integrates well with other network solutions like VPNs and Wi-Fi networks.
How Does RADIUS Fit Into a NAC Solution?
RADIUS can seamlessly integrate into a NAC solution to enhance its overall security framework. Within a NAC architecture, RADIUS servers can act as the authentication backbone, validating user credentials before granting network access. This integration streamlines the authentication process by leveraging RADIUS’s centralized database for user credentials, enabling efficient and consistent user verification across various access points, including wired, wireless, and VPN connections.
RADIUS can also facilitate dynamic VLAN assignment, allowing NAC solutions to segment network traffic based on user roles and compliance levels. This dynamic assignment ensures that users and devices are placed into appropriate network segments, maintaining organizational security policies.
RADIUS supports Extensible Authentication Protocol (EAP), which can be used for certificate-based authentication, thereby enhancing NAC’s ability to enforce endpoint compliance and secure network access. By combining RADIUS’s robust authentication and authorization capabilities with NAC’s comprehensive endpoint management and continuous monitoring, organizations can achieve a multi-layered security approach that mitigates risks and enforces stringent access controls. This synergy not only fortifies the security perimeter but also ensures that network access remains both secure and efficient.
SecureW2’s Cloud RADIUS and JoinNow NetAuth Enhances Network Access Control
SecureW2’s Cloud RADIUS is designed to enhance network security by providing robust authentication and seamless access management. Our Cloud RADIUS simplifies the process of Network Access Control by offering a scalable, cloud-based RADIUS server that integrates easily with existing network infrastructure. Unlike traditional RADIUS servers, SecureW2’s Cloud RADIUS provides advanced features such as certificate-based authentication, ensuring that only compliant and authorized users and devices gain network access. This aligns with the NAC goal of enforcing stringent security policies and maintaining continuous compliance checks.
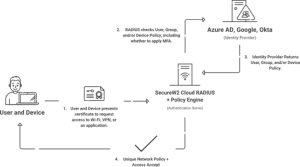
SecureW2’s agentless 802.1x technology enforces network access control (NAC) by utilising rules from Okta, Entra ID, Jamf, CrowdStrike, and other providers, ensuring that only trusted, compliant people and devices may access your network. Our Certificate Lifecycle Management solution works seamlessly with your cloud identity environment, automating certificate enrolment and revocation, making it easier than ever to manage digital certificates and improve network security.
Schedule a free demo to learn more.