Key Points
- Wi-Fi networks are vulnerable to various hacks like MITM, brute force, and phishing attacks, which can steal data or disrupt services.
- Using strong encryption methods, VPNs, and digital certificates can significantly reduce the risk of unauthorized access to WiFi networks.
- SecureW2’s JoinNow PKI and Cloud RADIUS solutions offer passwordless authentication, enhancing enterprise Wi-Fi security and simplifying network management.
Our lives now wouldn’t be the same without an internet connection, and WiFi networks give us quick and easy access. Nonetheless, hackers find WiFi networks a desirable target due to their vulnerability to internet attacks.
Any method used to enter a WiFi network without authorization is called a “WiFi hack.” This is often accomplished by exploiting security weaknesses or vulnerabilities, allowing the attacker to steal private information or disrupt routine network operations.
In this article, we’ll examine popular methods for breaking into WiFi networks and offer helpful tips for protecting your network and guaranteeing a safe online experience.
How to Hack a WiFi Password
There are various kinds of WiFi hacks, and each poses a different risk to both individuals and companies. In this section, we’ll review different types of WiFi hacks you should know about.
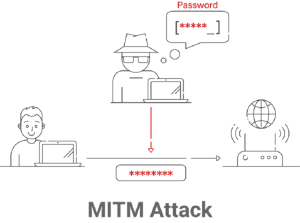
Man-in-the-middle Attack
A man-in-the-middle (MITM) attack occurs when the culprit puts himself into a conversation between a user and an application, either to eavesdrop or to mimic one of the parties, giving the impression that a regular flow of information is occurring.
An attack aims to get personal data, including credit card numbers, account information, and login passwords. Users of banking apps, SaaS companies, e-commerce websites, and other websites requiring logins are usually the targets.
An attacker may utilize information gathered during an attack for various things, such as identity theft, unauthorized financial transactions, or unauthorized password changes.
It can also establish a foothold within a guarded area while an advanced persistent threat (APT) attack is in its infiltration phase.
In general, a Man-in-the-Middle (MITM) attack can be compared to the mailman reading your bank statement, noting your account information, resealing the package, and having it delivered to your door.
Brute Force Attack
Brute force attacks are a well-known method of bypassing security. In a brute force attack, unauthorized access to a framework is increased by “speculating” usernames and passwords. Brute force is a very successful attack tactic that is simple to use.
A few attackers employ applications or simply guess passwords in brute force attacks. These tools assess different combinations of secret words to avoid filling out confirmation forms. Attackers try to access web applications in various ways by looking for the proper session ID. The end result of a successful brute force attack could be stealing information, infecting websites with malware, or interfering with assistance.
Nowadays, almost all brute force attacks are carried out by bots; however, some attackers still use manual methods. Attackers have arranged for commonly used certifications, or legitimate customer credentials, obtained through security lapses. Bots attempt these accreditation arrangements on purpose, attack targets, and notify the attacker when they have access.
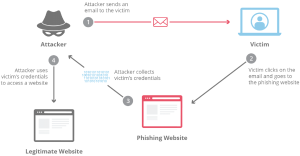
Phishing Attack
An effort to get sensitive information, usually in usernames, passwords, credit card numbers, bank account information, or other critical data, to use or sell the information is called “phishing.” Similar to how a fisherman uses bait to capture fish, an attacker tricks the victim by posing as a reliable source and making an alluring request.
Phishing is often used to accomplish other malicious activities, such as cross-site scripting and on-path attacks. These assaults fall into a few broad types, usually over email or instant messaging. To recognize phishing attacks in the wild, it’s helpful to familiarise yourself with a couple of these attack vectors.
Cross-site Scripting – In a cross-site scripting (XSS) attack, malicious code is added to a trustworthy website to run when the victim views it. There are several ways to introduce that unsafe code. The most common uses are posting it straight onto a page showcasing user-generated content or appending it to the end of a URL.
On-path Attacks – Attackers using an on-path approach insert themselves in the way of two devices (usually a web browser and a web server) to intercept or alter communications between the two. This allows the attackers to get information and adopt the identity of two agents.
Phishing is one type of social engineering attack. Social engineering, in general, describes most techniques that take advantage of mistakes made by others to get valuables, private information, or access. Cybercriminals often utilize these “human hacking” schemes to trick gullible people into divulging personal information, disseminating malicious programs, or granting access to forbidden systems. Attacks can occur through various contacts, in person and online.
Social engineering-based scams revolve around human behavior and thought patterns. Therefore, social engineering assaults effectively influence a user’s behavior. An attacker may successfully trick and control a user if they know what drives their behavior.
Evil Twin AP Attacks
A rogue wireless access point (AP) that poses as genuine and steals confidential data without the end user’s awareness is known as an evil twin attack. A smartphone or other internet-capable gadget, together with certain readily accessible software, may be used by an attacker to construct an evil twin quickly.
Attackers place themselves near a genuine wireless network and allow their devices to identify the radio frequency and service set identification used by the real AP. Then, they broadcast their own radio signal using the same name as the official AP.
The evil twin AP appears to the end user to be a hotspot with a strong signal.
This is because the attackers have not only impersonated the “good twin” by using the same wi-fi network name and configurations but also physically positioned themselves close to the end user, where the signal is most likely to be strongest.
The evil twin becomes the end user’s wireless AP if the powerful signal lures in the user and connects to it manually to access the internet or if the user’s computer automatically selects the fake AP due to its promiscuous mode.
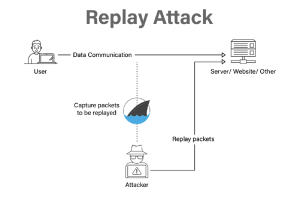
Replay Attack
Replay attacks happen when hackers listen in on a secure network conversation, intercepts it, and then deceitfully delays or resends it to trick the recipient into completing the hacker’s desired action. Replay attacks carry an additional risk in that a hacker can capture a communication from the network and decode it without the need for sophisticated abilities. Just resending the entire thing might make the assault successful.
Think about this actual attack scenario. A staff member sends an encrypted message to the company’s finance administrator requesting a money transfer. This communication is intercepted by an attacker, who then has the ability to resend it. The communication seems authentic to the financial administrator and is already appropriately encrypted because it is a valid message that has just been resent.
Unless there is a valid cause to be suspicious, the financial administrator will probably reply to this new request. Sending a sizable quantity of money to the attacker’s bank account may be part of such a response.
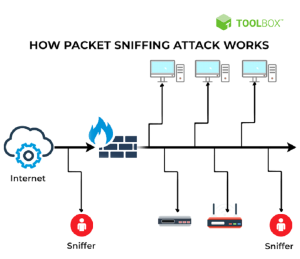
Packet Sniffing
A “packet sniffing” hacking method entails gathering data packets as they pass over an unprotected computer network. Packet sniffers aim to collect sensitive data (such as private financial information) and sell it or use it in further attacks. They do this by monitoring the data packets in network traffic.
A packet sniffing attack operates by keeping an eye on someone else’s wi fi network activity and gathering information sent to and from the internet via your network. The data that has been “sniffed” might contain any information that travels over the network or private information such as login passwords or financial information. Attackers can then use the information obtained via sniffing in subsequent hacking efforts.
Use a VPN to encrypt your connection and help stop hackers from obtaining any personal data you post online if you’re connected to any public Wi-Fi networks like a coffee shop, airport, or hotel. Sniffing attacks are most effective on unencrypted networks. And stick to websites you are certain are secure.
Jamming Attacks
Jamming attacks involve the use of unwanted interference on wireless communication systems such as Wi-Fi, Bluetooth, and mobile phone or home networks. Jamming attacks can also be directed on GPS systems.
The goal of a jamming attack is to “jam” a network, which can stop devices from interacting, interfere with the provision of necessary services, or even cause a denial of service (DOS) attack that takes down the network completely.
Physical devices are typically used in jamming attacks to flood a network with powerful signals and interfere with regular operations. Call spoofing is one example of a telecommunications fraud attack that fraudsters might use to capitalize on the service disruption and uncertainty it causes for callers.
Jamming attacks can occur on a local or large scale. They can be employed for comparatively small goals, militarised as a strategy during a conflict, or in terrorist acts. Jamming attacks, for instance, can be used to silence Bluetooth speakers during a noisy party in the neighborhood.
MAC Spoofing
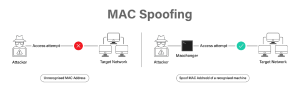
To put it simply, changing your MAC address is what it means to spoof. On your devices, you cannot modify the physical address; however, there are applications on a network that can allow you to do this. MAC spoofing offers benefits such as gaining access to networks restricted to specific MAC addresses, concealing the true identity of the originating device, and preventing tracking or traceback.
However, MAC spoofing may also be employed maliciously. Data delivered to your device may be redirected to another device, giving an attacker access to your data by imitating your MAC address.
A MAC spoofing attack occurs when a hacker modifies their device’s MAC address to coincide with another on a network to obtain unapproved access or initiate a Man-in-the-Middle attack. It can be used to conceal the identity of the attacker’s equipment and get beyond network wifi security settings like MAC filtering that rely on the MAC address.
Why are Wi Fi Passwords Vulnerable?
Once regarded as the first line of defense for online accounts, passwords are now frequently the weakest link because of common flaws. One significant risk is the common practice of people reusing wifi passwords for many accounts. Using this technique, a password breach for one service could be used as a key for several others. Hackers take advantage of this inclination and profit from platform vulnerabilities that are less secure to obtain unauthorized access to more sensitive accounts. The cumulative impact of reusing the same wi-fi password emphasizes how important it is for consumers to develop a fresh passphrase for every online transaction.
The widespread usage of obvious passwords is also alarming, as it provides hackers with an open invitation to commit fraud. Still, many people choose easy options like “password123” or simple information, such as birthdays or pet names. These recurring trends make it simple for automated password-cracking software to compromise accounts quickly. Users must use strong and complicated password combinations to strengthen their digital defenses since cyber criminals frequently utilize advanced algorithms that can quickly read a weak wi-fi password. The increasing sophistication of cyber threats necessitates adopting more secure authentication procedures, which are becoming increasingly important as technology develops.
Preventive Measures for Your Wi Fi Network Security
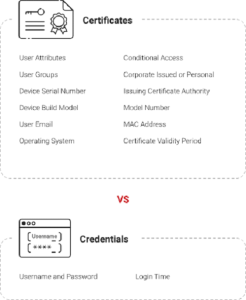
In the world of Wi-Fi settings and security, the transition from conventional passwords to digital certificates represents a fundamental change in wi-fi network security. Digital certificates improve security by offering more information than just identity verification. In contrast to passwords, which frequently only allow access if the right combination of characters is entered, digital certificates provide a thorough understanding of both the user and their devices. This contains information on the type of user, whether they possess a corporate or personal devices, the brand and model of the device, and when they were last permitted to access it.
Using digital certificates to enable passwordless access increases security and answers important queries regarding the user and their network interactions. This change enables organizations to respond to basic inquiries about the user, including their present function or group membership within the company, the terms and limitations governing their access, and more. Adding additional levels of authentication through digital certificates greatly decreases the danger of unwanted access and potential breaches. By implementing this advanced authentication mechanism, organizations may improve their security posture and guarantee a more resilient defense against the constantly changing cyber threat landscape.
Why Go Passwordless?
When weighed against the abundance of information digital certificates provide the shortcomings of passwords become evident. Businesses essentially have no information about the person using credentials to connect to the network when they utilize passwords. Digital certificates, on the other hand, offer a comprehensive perspective that allows organizations to address important queries about user identification, device information, authorization history, and current organizational responsibilities. Adopting a passwordless strategy with digital certificates is a calculated step towards a more knowledgeable and robust network architecture and a security improvement.
Strong Network Security With SecureW2’s JoinNow PKI and Cloud RADIUS
In an ever-changing digital environment, the necessity for strong Wi-Fi security measures has never been more vital. As this detailed examination of Wi-Fi password vulnerabilities demonstrates, the traditional technique of relying on passwords falls short of providing essential security against advanced cyber assaults. However, the use of digital certificates offers a revolutionary remedy.
JoinNow PKI and Cloud RADIUS from SecureW2 offer improved security and simplified onboarding procedures, paving the way for a passwordless future. Cloud RADIUS adds another validation level to ensure that only authorized devices can access the network. This improves visibility and control over the authentication process while strengthening the security perimeter and enabling centralized administration. The extensive context that certificates offer—which includes user identification, device information, and network authorization—exceeds the constraints of conventional passwords. In addition to facilitating a smooth transfer, the onboarding solutions offer comprehensive administration of the full certificate lifetime, from enrollment to revocation and expiration.
Contact us today and discover how SecureW2 can fortify your defenses against Wi-Fi vulnerabilities.