Key Points
- In MAC Spoofing attacks, hackers change a device's MAC address to imitate a different device present on the network using techniques like cloning and randomizing a MAC address.
- Various warning signs of a MAC spoofing attack include duplicate IP addresses, unknown MAC addresses, and any other unusual network activities.
- You can prevent MAC spoofing attacks by implementing zero-trust security principles in your network. This includes segmenting your network based on robust network policies and a reliable onboarding solution to help you achieve this.
New cyberattacks and breaches are reported every day in our news feeds. Cybercriminals target people as well as large corporations and other businesses. One of the many techniques hackers employ to exploit unsuspecting victims is MAC spoofing.
In 2016, a malicious actor executed a MAC spoofing attack to illicitly acquire $81 million from the Bangladesh Bank, serving as a tangible instance of such an attack in the physical realm.
Following a successful network infiltration, the perpetrator deployed malicious software to obtain the necessary login credentials, which were subsequently utilized to initiate illicit fund transfers to North Korean accounts. The perpetrator executed the breach by leveraging the MAC spoofing technique to alter the MAC address of their device to match that of a bank personnel’s device, thereby obtaining access to the SWIFT payment system. The perpetrator successfully bypassed the bank’s security protocols, thereby enabling them to carry out unauthorized transactions.
An unexpected spelling error noticed in a fake transaction sparked more suspicion and spurred an investigation that resulted in the recent hack revelation. This incident highlights the urgent need for strong network security measures capable of repelling such malicious activity by serving as a crucial reminder of the wide-ranging effects that MAC spoofing attacks can have.
In the following discussion, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place to resist these threats.
What Is a MAC Address?
Having a comprehensive understanding of MAC spoofing requires prior knowledge of MAC addresses. The nomenclature “IP address” is widely recognized, while the MAC address seems to be less ubiquitous. Some relevant points are as follows:
- Each device on a network has a unique media access control (MAC) address, sometimes called a physical address. Networking two devices requires an IP and MAC address. Every device’s NIC has a Media Access Control (MAC) address.
- As a cybersecurity professional, you should know that no two devices may have the same MAC address since this identification is unique. The hexadecimal encoding 00:0a:95:9d:67:16 is present in every device.
- The 12-digit alphanumeric identifier comprises 48 bits, with the initial 24 bits allocated for the OUI (Organization Unique Identifier), while the remaining 24 bits are designated for NIC/vendor-specific data.
- It operates on the OSI model’s data link layer.
- It is supplied by the device’s manufacturer and included in its NIC, which is ideally fixed and cannot be modified.
- A logical address is connected to a physical or MAC address using the ARP protocol.
What Is MAC Spoofing?
Each network-connected device possesses a distinct Media Access Control (MAC) address, which serves as an exclusive identifier assigned to its network interface card. Malicious actors possess the ability to utilize the method commonly known as MAC spoofing to modify the MAC address of a device in order to imitate another device present on the network. The vulnerability in question allows the attacker to bypass network security protocols that are dependent on MAC addresses, such as MAC filtering or access control based on MAC addresses.
MAC Filtering
MAC filtering is a security method used in computer networks to restrict access to network resources based on the MAC address, a distinctive number that is provided to each network interface card (NIC). Network administrators can add specific MAC addresses to a whitelist or blacklist using MAC filtering, allowing or disallowing network connectivity as necessary.
Organizations can improve their network security by limiting unauthorized devices from connecting to the network and accessing critical data or resources by filtering network access at the MAC address level. When integrated with other security protocols, this provides an extra layer of protection against unauthorized entry and can serve as a valuable asset.
Network security can be significantly impacted by MAC spoofing. Attackers may be able to get around MAC address-based security measures, giving them access to sensitive information or enabling them to attack other networked devices. Also, because the attacker’s equipment is a trusted device on the network, MAC spoofing might be challenging to spot.
How Does a MAC Spoofing Attack Work?

MAC spoofing is a commonly employed tactic by malicious actors to alter the Media Access Control (MAC) address of their device to mimic that of another device present on the network. The aforementioned vulnerability enables the assailant to surpass network security measures such as MAC filtering and MAC-based access controls.
In order to execute a MAC spoofing assault, the perpetrator leverages a specialized tool or software to modify the MAC address of their device to match that of a trusted device present on the network. Upon successful alteration of the MAC address, the perpetrator can potentially infiltrate the network, execute malicious activities against other endpoints, and potentially exfiltrate sensitive information.
How Do Hackers Use MAC Spoofing to Impersonate Devices on the Network?
It is crucial to acknowledge that threat actors may leverage MAC spoofing techniques to masquerade as legitimate network devices by altering their MAC address to match that of a trusted device. After a successful MAC address spoofing attempt, the perpetrator can illicitly infiltrate the network and potentially execute further malicious activities, such as compromising other devices or exfiltrating sensitive data.
MAC spoofing is a frequently employed tactic to circumvent MAC filtering, a security protocol that confines network entry solely to devices with recognized MAC addresses. The malicious entity possesses the ability to bypass the current security measures and attain illicit entry into the network through the fabrication of the MAC address of a reliable device. After that, hackers can do different kinds of cyber attacks, like stealing network communications, putting in harmful code, or getting private information.
It’s important to keep in mind that bad actors can use MAC spoofing to pretend to be network equipment and launch man-in-the-middle (MITM) attacks. A Man-in-the-Middle attack happens when an unauthorized third party listens in on conversation between two networked devices and claims to be one of the devices to the other. By making up a fake MAC address for one or both ends, an attacker can listen in on conversations and possibly get access to sensitive information.
MAC spoofing is a commonly employed tactic by threat actors to illicitly obtain access to confidential information in diverse situations. The perpetrator executes this by assuming the identity of reliable network equipment, thus granting them access to the system without being noticed. In order to effectively counter MAC spoofing attacks, it is crucial for network administrators to enforce rigorous security measures such as MAC address filtering and network access control.
Techniques Used in MAC Spoofing Attacks
The two major techniques carried out by hackers for MAC spoofing attacks are –
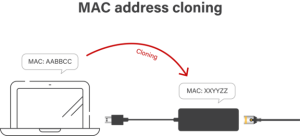
- Cloning
- Randomizing a MAC address
Cloning:
The act of cloning involves the replication of a legitimate device’s MAC address for the purpose of masquerading as that device on the network. In instances where a perpetrator has unfettered physical access to a target device, such as a router or switch, this method is often employed.
The perpetrator has the capability to bypass MAC filtering and gain entry to the network by duplicating the MAC address of the authorized device. This particular technique enables the assailant to intercept and potentially launch additional assaults on the network traffic, particularly when the gateway or router is the intended victim.
Randomizing a MAC Address:
Randomization involves generating a new MAC address and using it to impersonate a network device. When an attacker lacks access to a trusted device to copy its MAC address, they frequently apply this method.
The attacker creates a fresh MAC address that is unrelated to any known network devices. By exploiting this vulnerability, the adversary has successfully circumvented the MAC filtering mechanism and gained unauthorized access to the network.
The utilization of randomized MAC addresses can pose a significant challenge for network administrators in identifying MAC spoofing attacks, particularly in cases where the attacker’s device lacks any known MAC addresses.
Tools and Software Used for MAC Spoofing Attacks
MAC spoofing attacks are carried out by hackers using a range of tools and software, some of which are easily accessible online:
- MAC address changer
- Ettercap
MAC Address Changer:
The utilization of a freely available software, namely MAC Address Changer, empowers users to alter the MAC address of their network interface card (NIC). MAC address spoofing is a potential vulnerability that can be leveraged by threat actors to compromise the network and obtain unauthorized access. The tool for changing MAC addresses demonstrates cross-platform compatibility, facilitating a wide spectrum of operating systems including Windows, macOS, and Linux.
Ettercap:
Ettercap is a robust software application utilized for scrutinizing network traffic and conducting security assessments. Additionally, by manipulating MAC addresses and intercepting network traffic, cybercriminals can carry out MAC spoofing attacks. Ettercap is a versatile open-source software that is cross-platform and supports multiple operating systems, such as Windows, macOS, and Linux.
Cain and Abel, Netcut, and SMAC are additional popular tools for MAC spoofing attacks. MITM attacks can be conducted using these tools, which can also be used to clone or randomize MAC addresses.
Warning Signs of MAC Spoofing Attacks
There are various red flags that may point to a MAC spoofing attack on a network. Some of these warnings include:
- Duplicate IP addresses: The presence of a common IP address among various network devices may suggest that a malevolent actor is leveraging MAC spoofing techniques to impersonate a legitimate device.
- Unknown MAC addresses: It is imperative for network administrators to maintain a record of the MAC addresses of all connected devices. The presence of unfamiliar MAC addresses on the network may suggest the possibility of MAC spoofing.
- Unusual network activity: MAC spoofing attacks frequently include intercepting and altering network traffic. Network activity that is irregular or unexpected could be a symptom of a MAC spoofing attack.
- Inconsistent device behavior: Devices that are being spoofed could act strangely or react differently than planned. This might be because the attacker was manipulating and intercepting network traffic.
- Unexpected network failures: MAC spoofing attacks can cause network failures or disturbances. Unexpected network disruptions might be an indication of a MAC spoofing attack.
How to Prevent MAC Spoofing
Thankfully, there exist measures that can be implemented to thwart a MAC spoofing assault.
Using encryption technologies to protect network data could make it much harder for an attacker to perform a MAC faking attack. The reason for this is that it will be harder for an attacker to change network activity if they can’t read or change the data. Encryption also protects the privacy of any information a hacker might steal during a security breach.
Access Control Lists (ACLs) let network managers limit access to only media access control (MAC) addresses that have been approved. By taking this safety measure, we can make sure that an unauthorized user can’t use faking to take over the name of a legal device. To make these kinds of attacks less dangerous, the network could be broken up into smaller subnets.
You must be mindful of port security as well. Network switches offer the capability to configure port security, which restricts network access via a specific port to only authorized MAC addresses. Implementing this measure can effectively prevent unauthorized network access and thwart any attempts of MAC spoofing by potential hackers.
Dynamic ARP Inspection (DAI) is a security mechanism that enables the validation of Address Resolution Protocol (ARP) requests and responses within a network. DAI can stop attackers from forging ARP answers, which are required to translate an IP address to a MAC address.
Steps to Take If You’ve Fallen Victim to a MAC Spoofing Attack
If a user suspects that they have been the victim of a MAC spoofing attack, they should take immediate measures to secure their devices and network. The following are some actions users may take:
- MAC authentication bypass: MAC authentication bypass (MAB) uses a device’s Media Access Control Address (MAC address), commonly referred to as a hardware ID number, to identify, authenticate, and establish the level of access. Bypassing RADIUS MAC authentication can significantly reduce the security concerns associated with IoT devices. With MAB, you may now have more control over the visibility of IoT devices and their level of network access, even though it’s not as secure as 802.1X.
- Change your MAC address: To stop such attacks, users should change their MAC addresses if theirs have been faked. Users can accomplish this by contacting the manufacturer of their device or by using MAC Address Changer software.
- Update security configurations: To prevent unauthorized access to their network, users should update their security settings, including passwords and firewall configurations.
- Speak with your network administrator: To report the attack and collaborate with them to stop others, users should get in touch with their network administrator.
The Role of Zero Trust in Minimizing the Damage of MAC Spoofing Attacks
The zero-trust paradigm is a security framework that posits that no user or device should be deemed trustworthy by default, irrespective of their physical location or network access privileges. It is imperative that resources are only granted access after successful verification and authorization of the user or device. Additionally, it is crucial to monitor and restrict this access in accordance with the user’s role and contextual factors.
Implementing the zero-trust principle can effectively mitigate the deleterious impact of MAC spoofing attacks by restricting unapproved entry to the network and its associated resources. In a zero-trust model, an adversary would be required to undergo authentication and authorization procedures prior to accessing any resources, even if they managed to spoof a MAC address and infiltrate the network. Implementing this measure could potentially limit the lateral movement of threat actors within the network and impede their ability to compromise sensitive information or resources.
SecureW2’s onboarding solution adheres to the zero-trust concept by providing a safe and simple approach for authenticating and authorizing network devices and users. Digital certificates, which are more secure than passwords, are used in the solution to authenticate people and devices.
The onboarding process is quick and easy, allowing users to effortlessly transition from passwords to certificates without substantial training or technical understanding. With SecureW2’s solution, network administrators can easily regulate access and implement security regulations, lowering the risk of MAC spoofing attacks and other security risks.
SecureW2’s Solutions for Preventing MAC Spoofing Attacks
SecureW2’s solutions play a critical role in preventing MAC spoofing and other similar attacks by adhering to the zero-trust principle and segmenting the network based on numerous policies available in the policy engine. Network administrators can authenticate and authorize devices and users using digital certificates, which are more secure than passwords, with the help of SecureW2’s solutions.
Only authorized devices and users can gain access by segmenting the network based on policies, and their access can be controlled and monitored depending on their role and the context of their access. This lessens the possibility of MAC spoofing attacks and other security threats by preventing unauthorized access to the network and its resources.
Additionally, SecureW2’s solutions are made to make it simple for users to migrate from passwords to digital certificates by streamlining and simplifying the device and user onboarding process. This can lessen the chance of using weak or hacked passwords, which are frequently the starting point for MAC spoofing attacks and other risks of a similar nature. With SecureW2’s solutions, network administrators can enforce strong password standards and eliminate the use of passwords, lowering the risk of password-based attacks.
Contact SecureW2 today to learn how our solutions can help prevent MAC spoofing and other similar attacks on your network.