IT organizations that want to leverage PIV and store their certificates on YubiKeys need key security components to make deployments easier. SecureW2 bundles together turnkey PKI services, onboarding software for end users to enroll for certificates, and authentication services.
In the SecureW2 Management Portal, everything that is needed to enroll a YubiKey for a certificate
can be done using the Getting Started Wizard, which is available under Device Onboarding > Getting Started.
Configure the Wizard with the following settings:
1. Choose your Identity Provider: SecureW2 supports Google, Active Directory, Okta, LDAP and every other major Identity Provider to authenticate users for certificate enrollment. Specify your IDP here.
2. PIN/PUK Requirements: Ensuring YubiKeys are not using default PIN and PUKs are extremely important. Configure your organization’s security policies regarding PIN/PUK here.
3. Certificate Template: The SecureW2 PKI services empower organizations to generate custom certificates for Desktop Login, VPN, Wi-Fi, and more. Specify the application of your certificate here.
4. Run the Wizard: After configure the settings above, run the Wizard and it will configure everything required to configure your YubiKeys for certificates.
1.1 Configuring YubiKey Certificate Enrollment Settings
There are a number of Certificate Enrollment settings available for configuration with SecureW2, for an incredibly easy and customizable end-user experience.
To configure these settings:
-
- Navigate to Network Profiles.
- Click Edit on the Network Profile you created in the Getting Started Wizard.
- Click Edit on Network Settings.
- Under the Client Certificate section, configure the following settings:
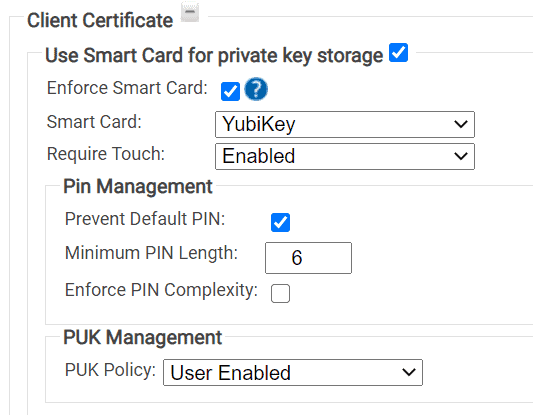
a. Select the Enforce Smart Card checkbox.
b. Select YubiKey from the Smart Card drop-down list.
c. Select Enabled from the Require Touch drop-down list, if you want the users to touch their YubiKeys.
d. Optionally, configure PIN Management.
-
-
- Select the Prevent Default PIN if you want to prevent YubiKeys with default PINs from
enrolling for certificates. - Minimum PIN Length allows you to require a minimum PIN length.
- Enforce PIN Complexity enforces the following PIN complexity conditions. Contain characters from the following categories:
- English uppercase characters (A through Z).
- English lowercase characters (a through z).
- Base 10 digits (0 through 9).
- Select the Prevent Default PIN if you want to prevent YubiKeys with default PINs from
-
e. Optionally, configure PUK Management.
-
-
- PUK Policy:
- Select Disable PUK to prompt only for resetting YubiKey PIN.
- Select User Enabled to prompt for resetting both YubiKey PIN and PUK.
- PUK Policy:
-
f. Click Update.
5. Click Update.
1.2 Key Attestation Settings
SecureW2 offers the ability for YubiKeys to perform Key Attestation, attesting that the private key was generated on the YubiKey itself. This allows administrators to create high security clearance access policies specifically for YubiKeys.
YubiKeys come by default with an attestation certificate signed by the standard Yubico PIV CA. Some YubiKeys, when ordered as a large custom batch, come with attestation certificates issued via a custom Root CA. If your YubiKeys have a custom attestation Root CA, you can also upload that here.
- Navigate to Identity Management > Key Attestation Providers.
- Click Add Key Attestation Provider.
a. Create a Name.
b. Select Type as YUBIKEY.
c. Click Save. - Navigate to the Configuration tab. To upload your custom Key Attestation Root CA:
a. Select Choose File.
b. Upload your CA. Allowed certificate file extensions are .cer, .crt, and .pem.
c. Click Upload.
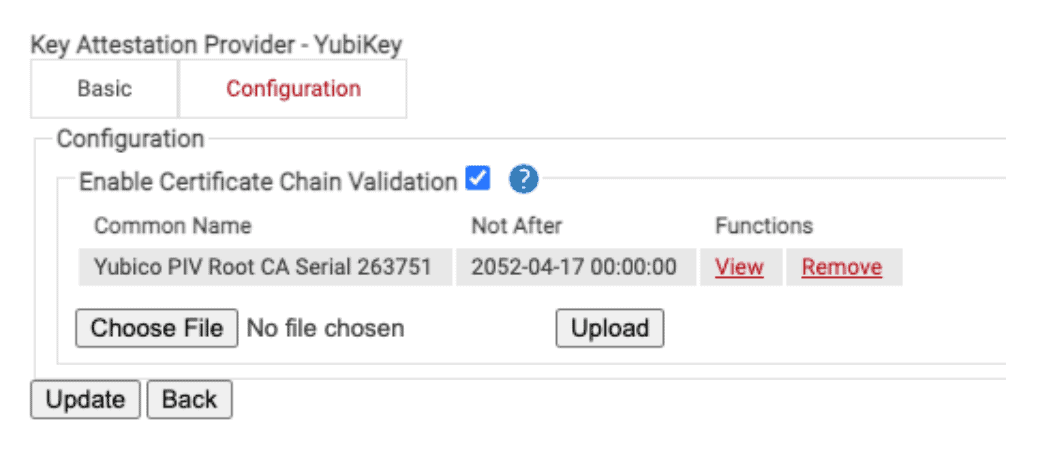
- Click Update.
- Now, your Key Attestation Provider will be a configurable setting when creating Device Policies.
1.3 Generate the Onboarding Page for YubiKey Self-Enrollment
After the Getting Started Wizard has finished, a landing page will be generated. This is where you will instruct your end-users to navigate to, so they can self-service their YubiKeys for certificates.
Every aspect of this page is completely customizable. Contact us for more information.
To get your landing page:
- Navigate to Network Profiles and click View.You will be taken to the JoinNow Landing Page, which automatically detects the device’s Operating System and deploys the appropriate client to configure their YubiKey
- Copy this URL and instruct end-users to navigate to the page.
There are many other features you can configure in SecureW2, but the steps above outline the minimum setup required to start configuring YubiKeys for Certificates.
2. YubiKey Certificate Enrollment End User Flow
The following steps outline how the end-users can self-enroll themselves for unique certificates for their YubiKeys, using a macOS or a Windows device.
2.1 macOS
- Download the YubiKey Manager from https://www.yubico.com/products/servicessoftware/download/yubikey-manager.
- After you download and install the YubiKey Manager, reboot your computer.
- Open YubiKey Manager, and then insert your YubiKey.
- Go to the JoinNow MultiOS landing page.
- Click JoinNow and the JoinNow client will download.
- Click the SecureW2 JoinNow app and click Open in the window that appears and the JoinNow client will begin configuration.
2.1.1 Enter or Reset PIN/PUK
Ensuring YubiKeys are not using default PIN and PUKs are extremely important. The JoinNow client can enforce any PIN/PUK complexity rules, detect if the user is using a default PIN/PUK, and prevent certificate enrollment until they have configured a secure and unique PIN/PUK.
Note: : For security reasons, you can disable PUK reset YubiKeys from enrolling for certificates. To do this, navigate to step 4.e in the “Configuring YubiKey Certificate Enrollment Settings” section.
If you have forgotten or need to reset your PIN, follow these steps:
- In the SecureW2 client, click Forgot PIN?.
- You are prompted to Use my (default) PUK or Reset your Yubikey.
• If you choose use my (default) PUK:
a. Enter your PUK.
b. Upon successful authentication, a new screen appears. This screen notifies you that resetting your YubiKey will erase all existing information stored on the YubiKey.
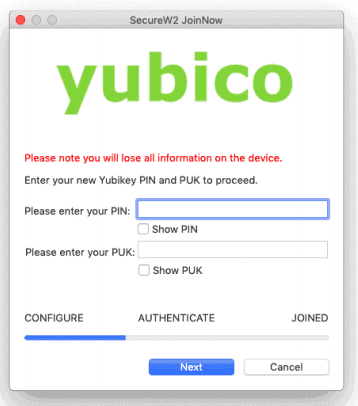
c. Enter your new PIN and PUK, and then click Next. A screen confirming you have set a new PIN and PUK appears.
d. Certificate enrollment resumes per the instructions in the next section.
• If you choose Reset your YubiKey:
a. A new screen appears. This screen notifies you that resetting your YubiKey will erase all existing information stored on the YubiKey.
b. Enter your new PIN and PUK, and then click Next.
c. A screen appears confirming you have set a new PIN and PUK.
d. Certificate enrollment resumes per the instructions in the next section.
NOTE: If you enter your default PIN/PUK, you will be prompted to reset your YubiKey.
2.1.2 Certificate Enrollment and Installation
After the client has ensured the YubiKey has a secure PIN, users can begin the certificate enrollment and installation process.
- Click Next and the login page opens in a new tab.This login page can be configured for use with any LDAP (Active Directory) or SAML (Google Apps, Okta, OneLogin, and other major vendors) Identity Provider.
- Enter your organization’s credentials. After the credentials are validated, you are returned to the JoinNow client.
3. Enter your device credentials to allow JoinNow to configure your device.
4. The JoinNow client now enrolls and configures the YubiKey for a certificate. When it finishes, click Done.
5. Open the Yubikey Manager and click Applications > PIV > Configure Certificates to verify the SecureW2 certificate successfully installed on your YubiKey.
2.1.3 Desktop Logon
Not only are YubiKeys enrolled for certificates with SecureW2, they are also configured for certificate applications such as desktop logon. After running the client, users can immediately start using their YubiKey for desktop logon.
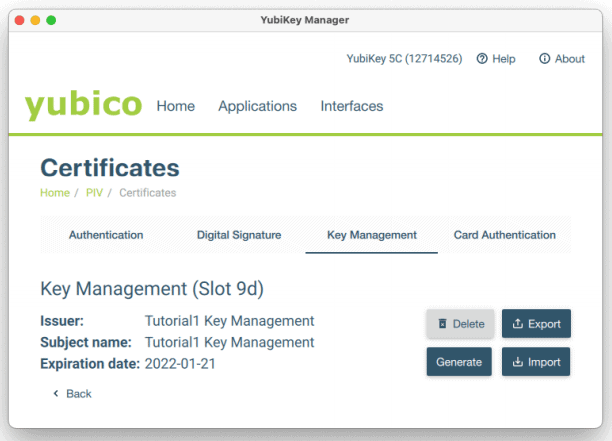
In order to unlock the keychain in macOS, which is necessary for desktop logon, a self-signed certificate must be configured in Slot 9d. The client automatically does this, which can be seen by opening up the YubiKey Manager client.
2.2 Windows
- Download the YubiKey Smartcard Mini Driver for Windows: https://www.yubico.com/products/services-software/download/smart-card-drivers-tools.
a. Click here for Yubico’s documentation on installing the Mini Driver.
b. After you download and install the driver, reboot your computer. - Navigate to your organization’s JoinNow landing page, and click JoinNow to download the client.
- Open the .exe file that is downloaded to begin the configuration process.
2.2.1 Enter or Reset PIN/PUK
Ensuring YubiKeys are not using default PIN and PUKs are extremely important. The JoinNow client can enforce any PIN/PUK complexity rules, detect if the user is using a default PIN/PUK, and prevent certificate enrollment until they have configured a secure and unique PIN/PUK.
Note: For security reasons, you can disable PUK reset YubiKeys from enrolling for certificates. To do this, navigate to step 4.e in the “Configuring YubiKey Certificate Enrollment Settings” section.
If you have forgotten, or need to reset your PIN, follow these steps:
- In the SecureW2 client, click Setup YubiKey/Forgot PIN.
- You are prompted to Use PUK or Reset YubiKey.
• If you choose Use PUK:
a. Enter your PUK.
b. Upon successful authentication, a new screen appears prompting you to enter your new PIN and PUK.
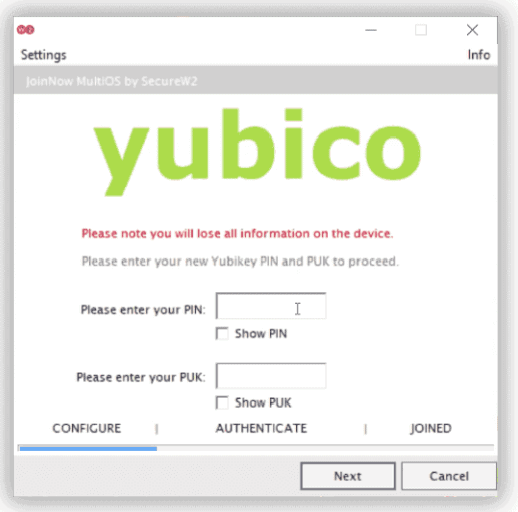
c. Enter your new PIN and PUK, and then click Next. A screen appears confirming you have set a new PIN and PUK.
d. Certificate enrollment resumes per the instructions in the next section.
• If you choose Reset YubiKey:
a. A new screen appears. This screen notifies you that resetting your YubiKey will erase all
existing information stored on the YubiKey.
b. Enter your new PIN and PUK, and then click Next. A screen appears confirming you’ve set a new PIN and PUK.
c. Certificate enrollment resumes per the instructions in the following section.
NOTE: If you enter your default PIN/PUK, you will be prompted to reset your YubiKey.
2.2.2 Certificate Enrollment and Installation
After the client has ensured the YubiKey has a secure PIN, users can begin the certificate enrollment and installation process.
- Click Next and a login page will open in a new tab. This login page can be configured for use with any LDAP (Active Directory) or SAML (Google Apps, Okta, OneLogin, and other major vendors) Identity Provider.
- Enter your organization’s credentials. Once the credentials are validated, you are returned to the JoinNow client.
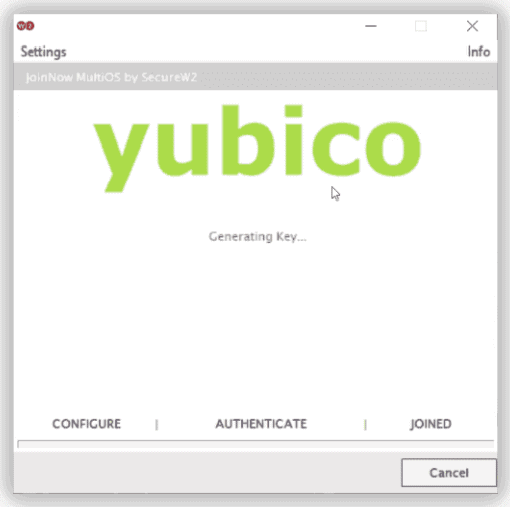
- The JoinNow client now enrolls and configures the YubiKey for a certificate. When it indicates you have joined the network, click Done.
- Open the Yubikey Manager and click Applications > PIV > Configure Certificates to verify the SecureW2 certificate successfully installed on your YubiKey.
Interested in receiving pricing information regarding our Security Key Solutions?
Yubikey is registered trademark of Yubico in the United States and/or other countries. Other trademarks, logos and service marks used in this site are the property of SecureW2 or other third parties.

