Physical security tokens like the Yubikey have smartcards that can be configured to store several certificates, the quantity of which depends on the specifications of the secure cryptoprocessor at the heart of the smartcard.
It’s a virtual “slot”, so there’s no need to tear apart the key looking for a place to stick your (equally virtual) digital certificate. For most end users, certificate slot management is entirely unnecessary.
For an enterprising enterprise, however, manipulating the certificate slots of your Yubikeys is a powerful tool for multiplying the security key’s benefits. You can integrate it with your own certificate-based WPA2 network to reap the benefits of public-private key cryptography.
How to Configure a Yubikey for Certificate Authentication
Pre-Configured Yubikey Certificate Slots
By default, many smartcards have at least one certificate slot occupied by an x.509 digital certificate. The Yubikey has several.
Slot 9a is the PIV identification slot; it’s the meat and potatoes of the security key. This certificate authenticates the device or user for whatever service they are attempting to access. Typically, it is used to access web applications, but its scope is only limited by your PKI. SecureW2 can enroll Yubikeys for certificates that authenticate for web access, desktop login, Wi-Fi, VPN, and more.
Slot 9c is the digital signature slot. The certificate contained within is used any time a digital signature is needed, such as when signing documents or files.
Slot 9d is called the “Key Management” slot, but it’s used when encryption is necessary to ensure confidentiality. If a file or email needs to be encrypted you can use the private key stored in the certificate of this slot for encryption.
Slot 9e is the card authentication slot. It’s similar to the PIV Identification slot, but the 9e certificate only authenticates physical access applications. It’s commonly used in scenarios in which only certain employees have the clearance to access physical locations like restricted buildings or rooms.
Slot f9 is reserved for attestation of itself and other certificates on the device. It’s the only slot that isn’t cleared upon performing a device reset because the smartcard needs to continue to use that certificate to establish trust. Should you want to replace the attestation certificate with your own, you can simply overwrite the slot.
Slots 82-95 receive an honorable mention as they used to be reserved as management key slots, but have been reappropriated for general use on the most recent Yubikey 4 and 5 generations.
Attesting Yubikey Certificates
Yubikeys arrive factory-sealed with an attestation certificate in slot f9 that is signed by Yubico’s internal certificate authority (CA). You can confirm for yourself that this certificate was generated on the device and signed with the authority of the Yubico CA, which lends it the trust necessary to digitally sign other valid digital certificates on the device.
Unfortunately, the native Yubikey attestation process is a little unrefined. You have to download and run piv-action-tool commands for each certificate that you want to attest. That’s fine for a single device, but if you are using more than a handful of Yubikeys (as is the case with most security key deployments), it’s simply not scalable.
We’ve discussed Yubikey digital certificate attestation at length in this article if you’d like to know more.
Enhanced Yubikey Certificate Management
As a Yubico Partner, SecureW2 has developed solutions that enhance the attestation functionality of Yubikeys. By integrating it with our cloud PKI suite and robust certificate management platform, we can attest multiple keys on multiple devices simultaneously. It’s also possible to replace the default certificates with ones signed by your own CA, and even integrate the Yubikeys with your directory so that they can authenticate desktop login, Wi-Fi, and VPN.
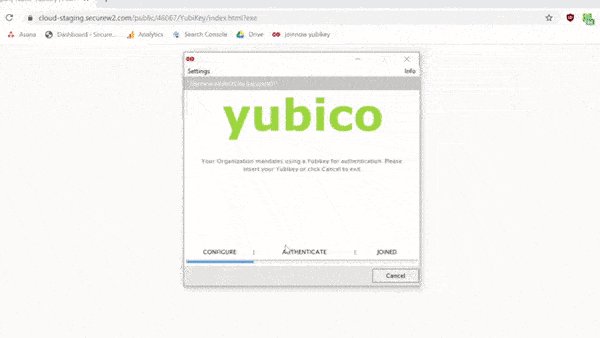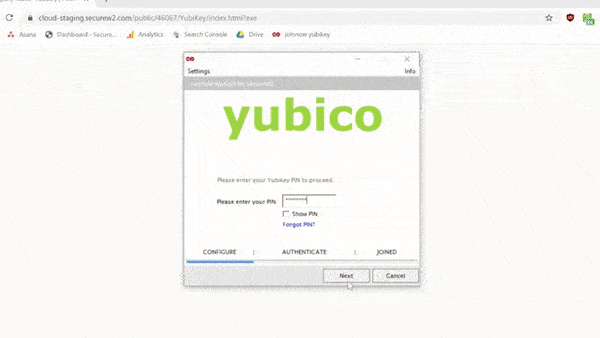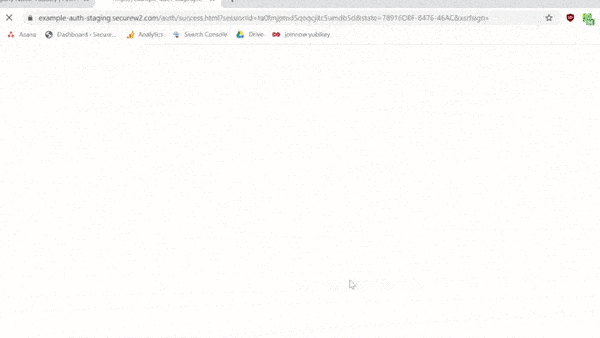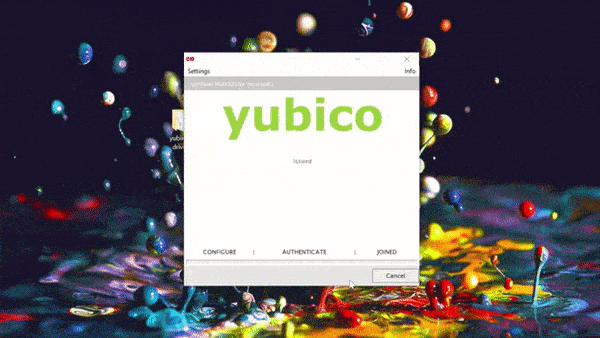
While you’re at it, you can adjust the PIN/PUK complexity requirements and a host of other features, allowing you to fully customize your Yubikey for your security needs. The best part is that the user-enrollment procedure is foolproof. Here’s a quick clip of the whole process.
Upgrade your Yubikeys so they can better protect your users and your network. We have affordable options for organizations of all sizes. Click here to see our pricing page.