SecureW2 has developed two solutions that offer major functionality upgrades to Windows Hello for Business:
- A Yubikey Management Solution that allows you to use your Azure AD or AD directory for Yubikey authentication to Windows Hello for Business.
- A more general credential/certificate management system (CMS) for Azure AD (Microsoft Entra ID) that allows you to use your PKI to expand the features of Windows Hello for Business
In this article we will discuss both solutions so that you can maximize your Windows Hello for Business authentication security and expand its functionality with more integrations. Alternately, click here to go straight to our Yubikey SCMS page.
(Working) Yubikey Authentication for Windows Hello for Business
Windows Hello is one of the easiest ways to add biometric security to your authentication protocols, and if you’re already using other common components of the Microsoft ecosystem for authentication (AD or Azure AD), integration is a cinch.
One of the most useful features of Windows Hello is the ability to use FIDO2 security keys, such as the Yubikey, in addition to (or as a replacement for) the primary device’s biometric hardware. It’s particularly useful in situations where devices don’t have an inbuilt biometric scanner – such as is the case in most managed device deployments.
Unfortunately, there’s two big problems with the current state of the Yubikey-Windows Hello solution. The first is that only the Yubikey 4 series keys are compatible, not the vastly superior series 5.
But that’s a moot point because of the second, much bigger, issue: Yubikey removed their Windows Hello solution from the Microsoft store in September of 2019. Because Microsoft deprecated their Companion Device Framework for Windows Hello, the integration no longer worked.
However, Windows Hello does still support FIDO2. And, in our capacity as an official Yubico Partner, SecureW2 has developed a solution for enrolling Yubikey 5 series keys for digital certificates. So, yes, it’s still possible to use Yubikeys to access Windows Hello (and Windows Hello for Business) with our solution – and our implementation comes with some significant upgrades.
Advantages of using Certificates on Yubikeys
PIV-Backed security keys like the Yubikey are an excellent tool for hardening your security because they offer an additional factor of authentication – “something you have”.
Passwords and PINs are another form of authentication – “something you know”. Since a Yubikey uses both a PIN and the physical authentication token, it has two factors of authentication, making it 2FA in and of itself.
Adding digital certificates to a Yubikey with our software adds the third and final factor of authentication – “something you are”. A digital certificate is like a photo ID: it’s tied to the identity of the user or device and can’t be transferred. It also doesn’t add any burden to the end user like a password does, preserving the user experience.
Having all three factors of authentication on a Yubikey make it a supremely secure MFA tool. Limiting network access to those with a properly configured security key makes your network virtually impenetrable.
PIV vs FIDO2 Authentication
Most enterprises prefer PIV Certificate YubiKey authentication security over FIDO2. It’s significantly simpler to manage and ties in easily with existing infrastructure.
FIDO2, on the other hand, requires you to configure your security key with each application individually. This is an especially terrible user experience when a security key gets lost, as the user has to individually set up every application all over again.
Using certificates with security keys negates all of these issues, while allowing the security key to be used for various other applications that FIDO2 doesn’t support, like VPN or Wi-Fi authentication.
Easily Install Certificates via Windows Hello on PIV-Backed Smartcards

Our Yubikey solution allows end users to easily self-enroll and configure their security keys for certificates. It also enables admins to set up group policies to manage user access and dynamically segment network resources. Certificate management is easily handled through our intuitive management portal.
Our management portal also supports security key attestation, as our software client can attest to the location a private key has been generated on a security key, or any other device with a TPM.
These same certificates can be enrolled to existing credentials, as SecureW2 integrates with any Identity Provider (Azure AD, Okta, G-Suite, etc.) so you can ensure that only your users have access to your critical applications.
Yubikey 5 Windows Hello for Business Login Configuration
Configuring your Yubikey for Windows Hello for Business authentication is also a breeze. You just have to push the configuration payload to each device, then have the user run Windows Hello normally. They will be prompted to enter a PIN, after which their inserted Yubikey will be enrolled for a certificate automatically using their Windows Hello credentials.
Here’s a quick .gif that shows the whole enrollment process:
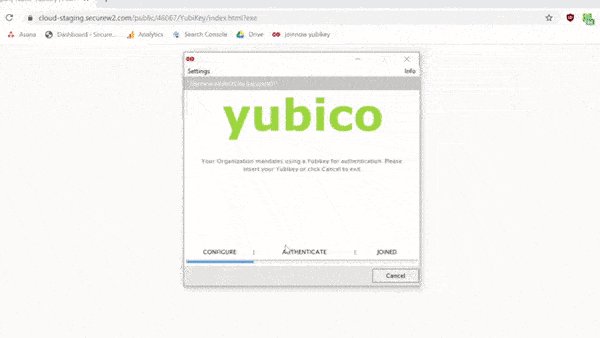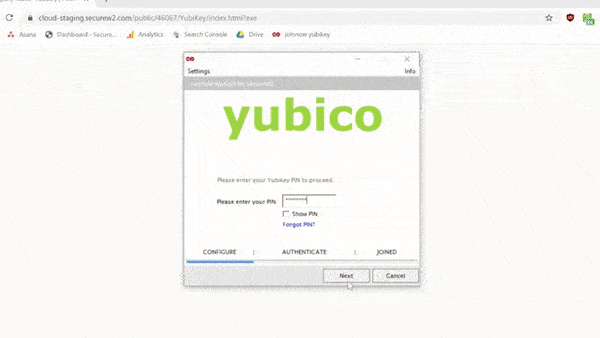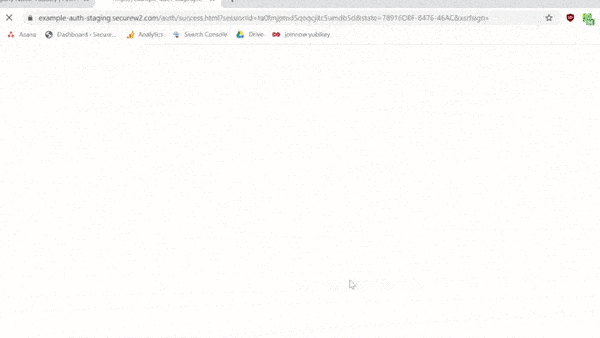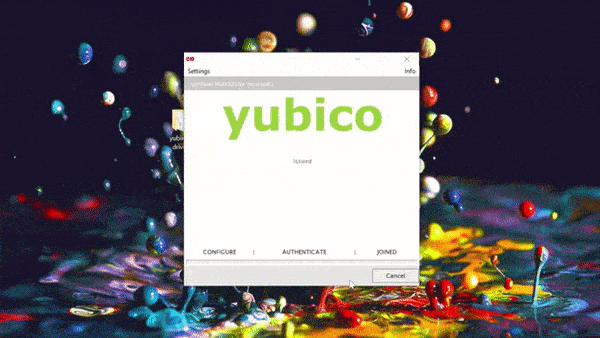
Future login attempts will require a PIN or biometric authentication for the Yubikey, whichever the user sets up. In the background, however, it will also authenticate the certificate without hassling the user for more input.
This solution is ideal for enterprises and large organizations that have issued Yubikeys to their employees for secure access to email, web apps, and other services. It allows you to more fully integrate your Microsoft ecosystem with your network security. Issuing certificates to your Yubikeys with our platform also opens up other Yubikey integrations – Wi-Fi, desktop login, and VPN to name a few.
Enhanced Windows Hello for Business Features
The Yubikey integration detailed above is an adaptation of our renowned SCMS (Smart Card Management System) / CMS (Certificate Management System). SecureW2’s vendor neutral products can be integrated into your existing network environment to leverage your infrastructure to build a PKI – a necessary foundation to deploy a CMS. If your organization does not yet have a WPA2-Enterprise network or 802.1X authentication, our managed Cloud RADIUS and managed cloud PKI can get you up to speed in a matter of hours.
Azure AD and Windows Hello already have support for a number of digital certificate-based features, but there’s a big problem in that Windows Hello for Business only natively support certificates signed by the Microsoft CA.
The lack of support for other certificate authorities could be an issue for a number of reasons:
- May need to authenticate with a service that doesn’t trust the Microsoft CA
- May need to customize certificates
- Organization may require full PKI control for compliance/security reasons
Fortunately, there’s a way around it.
How to Use Non-Microsoft Windows CA with Windows Hello
The SecureW2 CMS will allow you to integrate your Azure AD directory for passwordless authentication via certificates that you generate. By connecting your Azure directory to our managed PKI, you can distribute certificates that have added functionality such as:
- Self-enrollment via Azure credentials
- Document/File Signing
- S/MIME
- Smart card authentication
- Multiple certificates per user/device
You can configure Windows Hello for Business to accept the same certificates you use for Yubikey smart card authentication, for example, and use the same certificate to authenticate other web apps like Slack.
Utilizing a fully-featured cloud PKI both increases your network security and streamlines the user experience making it a win-win. Upgrade your Windows Hello for Business with our exclusive Yubikey SCMS today.