Key Points
- Merging two completely different IT environments can make a complex merger/acquisition even more so.
- Your network is uniquely vulnerable during M&A, and your security teams need to be aware of potential threats.
Mergers and acquisitions (also known as M&A) lead to both exciting and stressful times for all parties involved. While they can ultimately be strategically, economically, and even culturally beneficial, there are a lot of stress points to be considered. One such example is the herculean challenge of merging networks which may be totally different from each other.
As is often the case, it’s probable that each network has its own entirely different architecture, which means updating your network access control for all entities in the M&A can be daunting. This aspect alone requires a lot of planning and resources, which we’ll examine in more detail.
Modern Network Infrastructure in M&A
There are a lot of pieces involved in modern network infrastructure, and like any two things with many components, combining two separate network access control approaches is complicated. The first step is to assess all the environments in the merger, taking inventory of the pieces. Examples of things you may want to consider in your inventory include the following:
- Your Identity Provider (IDP)
- Any mobile device management (MDMs) used by the merging organizations
- Managed and unmanaged devices/BYODs
- IoTs in use by the organizations (and the methods used to manage them)
- Access points
Building a clear picture of the infrastructural elements used by all entities involved in the merger or acquisition is critical. So, too, is defining the network access control (NAC) practices of the organizations in question.
For instance, one company may allow the use of BYODs, while the other may only permit company-managed devices. Getting all merging organizations on the same page and establishing a uniform set of standards is vital.
Of course, it would be ideal to adjust to the practices of whichever organization has the most rigorous standards. On the flipside, though, it’s also important to consider what will be the most seamless experience for the end users. Repeated disconnects and difficulty connecting to your network will only decrease productivity during the transition.
Possible NAC Risks & Complications During M&A
While oftentimes exciting, mergers and acquisitions also create an especially vulnerable environment that can leave your network at risk during the integration process. Patient hackers wait in the wings to exploit vulnerabilities to gain application access – and what better time to do so than in the turbulence of a merger?
Vigilance is key. There are a handful of risks you’ll want to be aware of in advance, such as:
- Misconfiguration of End-User Devices
- Forgotten or Outdated IoTs
- Differing NAC Approaches
- Inherited Cybersecurity Risks
- Increased Scrutiny from Regulatory Agencies and Insurance Providers
Misconfiguration of End-User Devices
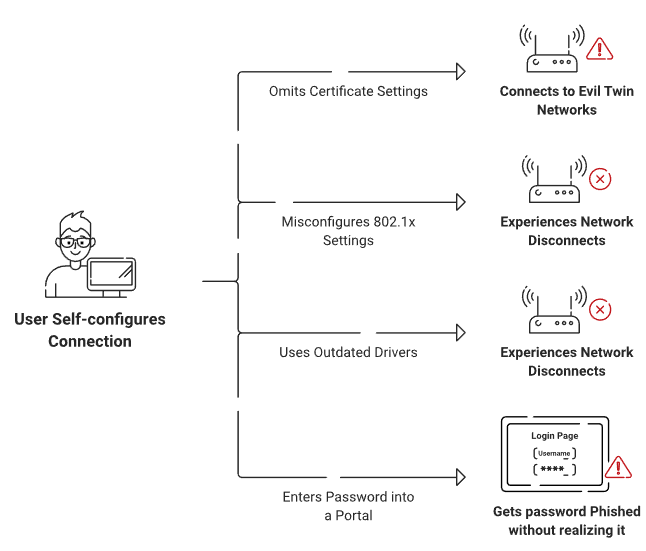
Device misconfiguration may not be as much of an issue in environments managed via MDM. However, if there are BYODs present on the network, it’s entirely possible – even likely – that their users may not have properly configured them. One example of a commonly misconfigured setting is server certificate validation, which ensures that users don’t connect to evil twin networks.
Additionally, those end-user devices might not be updated with the most recent patches and drivers, which leaves them vulnerable to new exploits. Many users are less inclined to endure a lengthy update, delaying updates for as long as possible
Forgotten/Outdated IoTs
It’s hard to keep track of all the devices connected to a home network – needless to say, the complexities multiply when you factor in the numerous groups of IoTs connected to a company’s Wi-Fi…now exponentially increase the complexity when you look at bringing together multiple company networks. Like other devices, your IoTs often have patches and updates that need to be regularly applied to keep them secure.
Each one presents a possible entry to your network by an attentive hacker. Failure to regularly update them increases the odds of this occurring.
Updates aside, you’ll also want to find a way to account for them in your network authentication, which can be challenging since some IoTs can’t store certificates. One way to achieve this goal is to use a RADIUS server with Mac Auth Bypass capabilities, which allows it to authenticate IoTs using their MAC addresses.
Differing Approaches to NAC
In any merger, you are combining two unique network structures, which can include drastically different security resources, security teams, and security practices. This means you might end up having to utilize multiple IDPs and MDMs, as well as numerous other IT infrastructure components. That can certainly complicate day-to-day work for your IT and support departments.
Certain security ecosystems only play well with their own components, which could be a problem in a merger. On-premise Active Directory (AD), for example, tends to only work well in Microsoft-heavy environments. If one of the companies in the merger or acquisition uses other providers for its identity management or other operating systems, combining the two IT environments can be a bit trickier.
In this scenario, a neutral third party could effectively handle those two entirely different networks authenticating to the same or different directories. The solution would be a centralized Cloud RADIUS that can integrate with any IDP for authentication.
Inherited Cybersecurity Risks
When you acquire or merge with another company, you inherit the entirety of its IT infrastructure – including its vulnerabilities and technical issues. This can include a number of problems, such as previous data breaches, password mismanagement, outdated components, and patchy security policies or network access control (NAC) policies.
A single red flag shouldn’t cause you to slam on the merger brakes, but it’s a good idea to be aware of the security risks you’re inheriting so you can prepare to mend them and secure access to critical business applications.
Increased Scrutiny from Regulatory Agencies/Insurance Providers
Because of the numerous risks possible during a merger, you’ll likely face heightened scrutiny from both regulatory agencies and cyber insurance providers looking to ensure you meet cybersecurity standards. This may be doubly true if yours is an industry with stringent regulations, such as the healthcare or financial sectors.
There isn’t necessarily anything you can do to alleviate or avoid such scrutiny. However, being mindful of it and prepared with documentation may smooth the transition for you. Recent Security Risk Assessment (SRA) results and logs, such as RADIUS event logs, can help you demonstrate your security posture.
M&A Network Access Control Best Practices
Now that we’ve covered the threats worthy of consideration, it’s time to get more proactive and look at what you can do to update your NAC once the merger is complete. There are a few updates you can implement to smooth the conclusion of your merger:
- Manage Identity Context
- Use an Onboarding Solution to Prevent Misconfiguration
- Create Advanced Custom Policies Based on Attributes
- Transition to the Cloud
Manage Identity Context
If you’re not planning on merging IDPs with one of the organizations involved in the M&A, then you may want to at least ensure they’re using the same resources. The best way for you to leverage the policies from each IDP (or a single one) and apply them to all your users is to utilize certificate-based authentication (CBA).
Digital certificates are comprised of templates that contain detailed information on users and devices. PKIs are necessary to manage certificates, but building or regulating a PKI doesn’t need to be something you spend resources on – especially right after or during M&A. A managed PKI such as JoinNow Connector PKI can integrate with any infrastructure – including multiple sources of truth – and utilize the policies you’ve already created within them for network authentication.
Use an Onboarding Solution to Prevent Misconfiguration
If you’re going to use certificate-based authentication to secure your network, getting those certificates to all the devices could be another puzzle. Luckily, this is a puzzle that is easily solved with the right onboarding tools.
In this case, an onboarding solution can help ensure end-users properly configure their own devices in case there are BYODs. JoinNow MultiOS is a solution that makes configuration for certificate-based authentication fast and easy for users of any technical level. In fact, it is so simple that it can be completed within a minute, and it works with any major operating system.
For organizations with MDMs, we offer our JoinNow Connector Gateway APIs. These can work with any major MDM to automatically enroll your devices for certificates. The end-user will notice no difference and will enjoy seamless network access.
Create Advanced Custom Policies Based on Attributes
Attribute-based access control (ABAC) and role-based access control (RBAC) are two different approaches to network access control (NAC). RBAC allows for broader control by applying policies to whole groups of users. An example would be putting different groups on their own VLANs, such as DevOps and Marketing being put on separate VLANs.
ABAC is more granular, giving administrators more ability to apply policies based on specific attributes. The reason ABAC may be the better choice after M&A is that there’s no guarantee all entities involved in the merger define their groups the same way. It may be much easier to look at specific attributes.
Your directories store a wealth of information about users that you can tap into for these policies. Things like name, email address, and password are obvious choices for ABAC policies. But there are other attributes to use for policies, like limiting access to certain resources only to users from a particular geographic location.
Transition to the Cloud
If you haven’t already, now is as good a time as any to consider transitioning your infrastructure to the cloud. There are a number of reasons to think about moving past on-prem infrastructure. A quick list of compelling reasons could be the high cost of on-premise infrastructure, the large degree of setup involved, and the necessity for duplication across multiple locations.
Moving to the cloud now factors in not only your present security but that of your future. It’s much more scalable and doesn’t require replication at every single one of your offices. Our Cloud RADIUS service, for example, is hosted in the cloud, which allows it to authenticate your users from any region at any time.
SecureW2 Helps You Improve Your NAC – Before and After a Merger or Acquisition
Mergers and acquisitions can seem overwhelming at first, especially when you factor in how complex combining two or more IT environments can be. However, there’s another way to look at it, too: as an opportunity to update your network access control and improve your security.
Fortunately, SecureW2’s full suite of network security products can make this process simple. With our managed PKI, you can deploy ironclad certificate-based authentication for all members of the organization. These certificates are easy to get to all your devices – thanks to our self-service onboarding application for BYODs and our auto-enrollment gateways for MDMs. And, once all that is said and done, we even offer a managed RADIUS service to authenticate all your certificates.
These solutions all have some things in common: they’re remarkably fast to deploy, highly customizable, and can integrate smoothly with any existing infrastructure you have. Reach out to us for a free demo – we’ll show you our solutions in action.