Key Points
- Security keys (hardware tokens like YubiKeys) deliver a stronger form of MFA, making phishing and credential theft far harder
- Modern standards like FIDO U2F and FIDO2 enable passwordless or biometric authentication directly via the key, improving both security and user experience.
- SecureW2’s solution allows organizations to provision certificates onto YubiKeys—combining physical tokens with robust PKI for seamless, self‑service onboarding.
Security keys, also called hardware security keys, are a method of authentication that offers an additional layer of hardened security. They can be used to login to desktops, Wi-Fi, and be integrated into the sign-in process of many popular websites and apps.
As hacking techniques become more advanced and data is stolen at a rate of almost 6 million records per day, companies and individuals are increasingly looking towards physical security as the safest solution.
What’s a Security Key?
While they’ve recently surged in popularity due to impressive innovation from Yubico, security keys have existed in one form or another for decades.
The keys are most commonly used as a secondary requirement for login, though they sometimes serve as the sole requirement. Using them in addition to other methods, such as credentials (username and password), is called multi-factor authentication (MFA). If you’ve ever had to add a phone number to your email account or use a PIN as a second step to log in to your bank, you’ve already encountered a form of MFA: two-factor authentication (2FA).
Security keys, like other connected token authentication methods, are unique because they subvert the security paradigm. Instead of access being dependent on what you know, (an email and an 8-character password) it’s dependent on what you have – in this case, a small USB device.
The advantage of a physical token being required during the login process is that you’re protected from the most standard hacking attempts. A clever hacker might be able to pilfer your credentials, but it takes an entirely different set of skills to steal an object off your person.
So, calling the device a “security key” is a more apt description than you might expect. It is simultaneously a complex device that enables MFA on its own while also being a literal, physical key that requires your touch to operate.
How Do Security Keys Work?
It’s a little misleading to imply that security keys represent an infallible, impenetrable layer of security. If it was an actual key for an actual lock, it would be true that it can’t be wirelessly hacked (though lockpicks might present a hazard). Instead of a physical barrier, modern security keys rely on the integrity of FIDO U2F to keep their contents secure.
The Basics of FIDO
FIDO U2F is an open authentication standard developed primarily by Google and Yubico. It uses a physical token, the security key, to securely access a wide variety of online services without the need for installing new software or drivers. The project has been taken up by the newly formed FIDO Alliance, which has improved and expanded on the standard public key cryptography technology over the past few years.
When registering the key to a new account, a Public and Private key pair are generated on the client-side and user-side. When the user sends data, it is encrypted by the shared public key. That message can only be decrypted by the receiver’s private key. It works the same in reverse.
The matched keys have the additional benefit of confirming that the other party is the exact entity that they registered a key pair with, which prevents Man-in-the-Middle attacks. Importantly, a security key can’t communicate with any device or network until it’s unlocked locally by the user, commonly by pushing a button on the key.
FIDO2 is on the Horizon
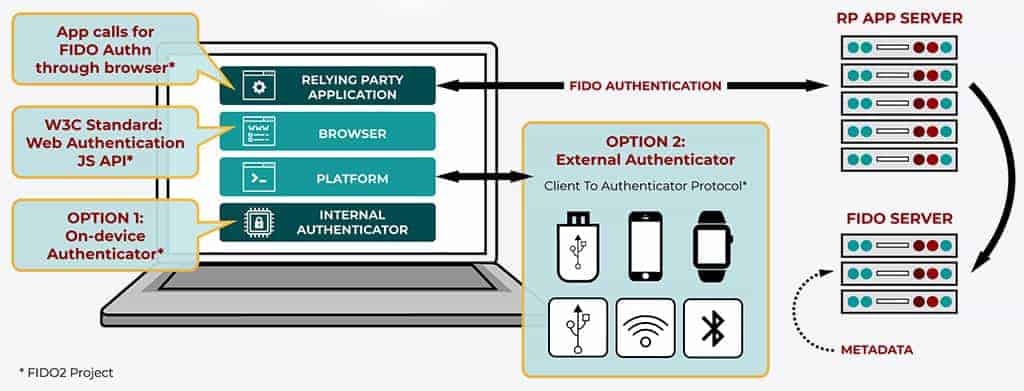
FIDO2 U2F is the successor to the original FIDO and is already being rolled out by a few early adopters, such as Yubico (who also helped to develop this standard as well). In simple terms, it utilizes the newly-minted Web Authentication (WebAuthn) and FIDO Alliance’s Client-To-Authenticator-Protocol (CTAP) to expand an incrementally improved FIDO to more browsers and more devices.
One significant improvement of FIDO2 is that it enables more ‘factors’ of authentication to be verified by a single key. It expands the range from just 2FA to passwordless authentication and even MFA that supports biometric options.
As of yet, few key manufacturers are utilizing the new standard. A notable exception are the Yubico products “Yubikey 5” and “Security Key Series”.
Security Key Communication Methods
The majority of the security keys on the market today are simple USB-A dongles, they plug directly into a standard USB port on a laptop or desktop.
For those that want to secure mobile devices, there are several options. Some security keys are NFC-enabled (Near-Field Communication), which is the technology that allows you to briefly tap your phone or credit card against another device to perform an action. In this instance, your key will authenticate upon tapping your NFC-enabled device. There are a few keys that have USB-C dongles and Lightning Adapters for your Android and iPhone respectively.
There’s a whole class of Bluetooth-enabled security keys. Their reputation is marred somewhat by the mishap that plagued Google and Feitian, but it remains a viable and secure method of communication for keys. Unlike USB and NFC keys, Bluetooth keys need to be charged, but they have the advantage of not needing direct contact with the device.
Smart Cards
One of the core components of a security key is called a ‘smart card’, which is a physical electronic authorization device. It’s essentially a small, simple computer that has just one task: to be a secure cryptoprocessor.
You’re more familiar with smart cards and secure cryptoprocessors than you think. The chip on your credit or debit card is a cryptoprocessor – security keys just have a few extra features. Just as a credit card requires a PIN to authorize your transaction, a security key uses a digital handshake to authorize a transaction of data.
PIV
Many security key smart cards are PIV-compliant (Personal Identity Verification). PIV is an application run on a smart card that contains a certificate and a private key that are used for highly secure authentication.The biggest user of PIV is the US government – they use ID cards or badges that grant access to buildings or computers based on the individual’s clearance.
SecureW2 has partnered with Yubico to put certificates on Yubikeys. We’ve opened up new possibilities for Yubikey integration: Wi-Fi access, desktop login, VPN login, and more. For more information on our Yubikey solution, get in touch.
Uses of Security Keys

Security keys are a useful, even necessary, tool for people and organizations at every level. Individuals can rest easy knowing their social media and bank credentials are secure. Organizations, from SMBs to universities to international enterprises, will find myriad uses for security keys.
Use cases for hardware security keys are manifold. They can integrate into most authentication processes you encounter:
- Log in to a user account on a laptop or desktop
- Log in to a VPN or proxy service
- Log in to W-Fi networks
- Log in to email accounts, social media, banks, and other websites and web apps
- Regulate access to secure buildings, rooms, servers, etc.
- Control privileged account access
Adding more authentication factors to important accounts improves the validity of a user’s identity. However, people are understandably reluctant to introduce more inconvenience to the already bland task of authentication.
Instead of repeating tired platitudes like “better safe than sorry!”, some security keys incentivize the increased security by making the process even simpler. A few have the ability to store multiple forms of authentication within the key – usually a generated password, the intrinsic security key challenge-pair, and a biometric scanner. With such keys you merely have to plug it in and tap the key to authenticate to any service, which is far simpler than remembering a password and typing it in.
Security Keys Protect Against Phishing
Phishing is a data theft technique that utilizes psychological manipulation to coerce victims into giving their information to the wrong source. It’s becoming alarmingly common – the number of phishing attacks rose 65% from 2018 to 2019.
A common phishing strategy is to get users to follow a link to an imposter website that looks identical to the real one. The victim will navigate to something like “Googel.com” and input their credentials, effectively handing them over to the data thief.
Security keys utilize FIDO’s Universal 2nd Factor (U2F) protocol to prevent people from accidentally falling victim to a phishing attack. It will only authenticate on the correct domain, and even if a user managed to mistakenly register the key to the wrong site, it would create a new pair locked to the false domain. That’s not an issue because the hacker is no closer to gaining access to your accounts.
A correctly-configured security key makes a user almost invincible to classic phishing, which is especially important in high-stakes environments where Man-In-The-Middle attacks are prevalent. Google, using the Yubikey, went an entire year without a single successful phishing attempt on any of their 85,000 employees.
Security Key Retailers
Yubico
Yubico was founded in 2007 – and while they weren’t the first to come up with idea of security keys, they were certainly the first to execute it well on a large scale. Much of the renewed interest in security keys is due to the development of FIDO and the ever-increasing threat of cyberattacks.
The company has the lion’s share of the security key market. Ever since they blazed the trail, competitors have been popping up almost monthly. The newcomers have a lot of catching up to do, as Yubico’s catalogue is rapidly growing with new products and exciting features.
Google Titan
The Google Titan is unfortunately named, as it failed to become a strong contender in the security key space. It suffered the one-two punch of an underwhelming response to release followed by a quickly-discovered security flaw.
The Titan’s issue lay in a Bluetooth misconfiguration. While the problem itself was a minor blip, the news made waves and the result was a loss of confidence in its security. It also helped bring to light that Google does not manufacture security keys themselves – they essentially white label keys from the Chinese company Feitian.
China has a less-than-stellar reputation for security, with a heavy-handed government that often exerts pressure on companies for data or to include backdoors. The revelation about Google’s choice in manufacturing partner did them no favors.
Feitian Security Key
Feitian produces both Google’s Titan keys and their own branded products. Naturally, they suffered the same Bluetooth setback as Google and also willingly replaced affected keys.
They have a wide product catalog that includes many products that are security-key adjacent, such as smartcard readers and cryptocurrency wallets.
Security Key Vulnerabilities
 While the keys are a superb defensive measure, they’re not foolproof.
While the keys are a superb defensive measure, they’re not foolproof.
As is the case with all cybersecurity, the most vulnerable part of a security key is the human using it! This is doubly true when the authentication factor is a physical object people are responsible for.
Security keys can’t really be hacked in the traditional sense, but they can be lost or stolen. They can also be broken, which shouldn’t permanently lock you out of any accounts but is certainly a setback.
There can be software flaws in security keys that expose weaknesses hackers can exploit. One example is Google’s Bluetooth issue, in which a person within Bluetooth range could potentially connect their own device to your key if they timed it precisely. Likewise, Yubico also reported a hiccup in which their FIPS key (for government use) wasn’t randomizing properly, which made the credentials it produced predictable.
In both known cases of security key flaws, the company voluntarily admitted the problem and offered replacement products to users. The flaws were discovered before they could be exploited, so no damage was done in either case. The public acknowledgement and rapid-response of the key manufacturers is promising – they were as transparent as possible and the industry benefits from that kind of honesty.
It’s important to note that even in the event that a security key is hacked, it doesn’t magically expose all of your data and passwords to the hacker. That’s the beauty of multi-factor authentication: the key is just one part of the identity authentication puzzle. Even if it’s compromised, other authentication methods are preventing unauthorized access.
Upgrade Your Security Key with SecureW2
One of the most glaring shortcomings of security keys is that they, too, are credential-based. They absolutely do an excellent job at protecting their credentials, but at the end of the day, they’re really just obscuring a simple string.
Certificates are a superior alternative to credentials as they take the security out of the fallible hands of users and relies on rigorously-tested security protocols and encrypted key pairs. Instead of relying on users to follow security best practices, certificates offer an automated authentication method that securely connects to the correct network every time.
SecureW2 has the industry’s only solution for using certificates with security keys. Furthermore, our onboarding software converts the cumbersome act of setting up and registering security keys into a streamlined, guided process so users can self-enroll.
That takes an immense burden off of the IT department that would otherwise need to configure each device manually. For organizations that intend to deploy tens or hundreds of keys, it’s a no-brainer.
Currently, the SecureW2 security key solution only extends to products made by Yubico. Sign up for our mailing list using the form below to be alerted when we expand our offering to other keys.
If you’re interested in exploring the possibilities of certificate onboarding and simple self-enrollment, read about our Yubico integration here.