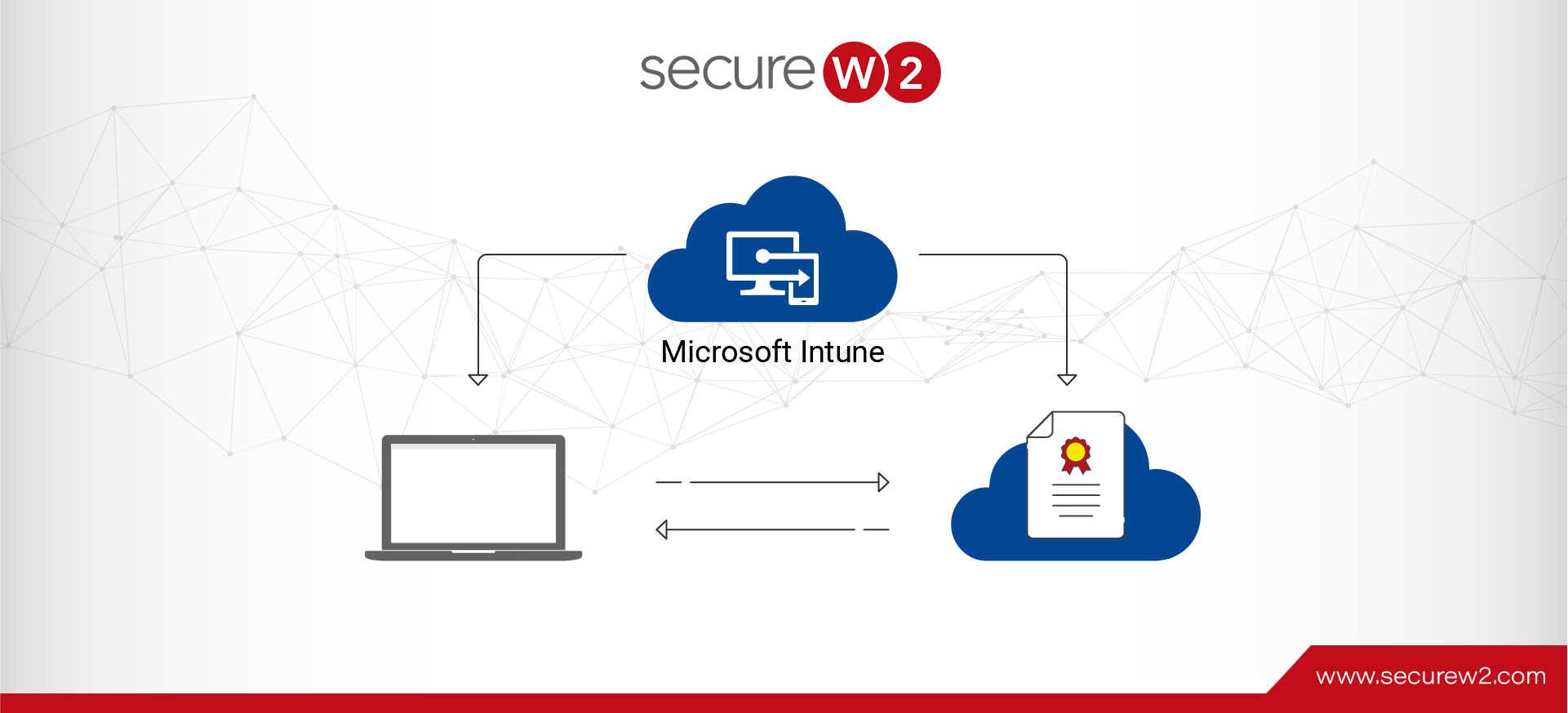
A Complete Guide to Intune 802.1x
The 802.1X standard provides secure authentication for users and devices looking to connect to wired and wireless networks. It uses an authentication server known as the RADIUS server that validates the users against their credentials and network policies to provide ... Read More
