Key Points
- A PKI, or Public Key Infrastructure, enables passwordless authentication encrypted communication, facilitates web-server communication, and is used for authentication by organizations like NIST, CISA, and NSA.
- A PKI uses public-private cryptography to create impenetrable, secure keys that are impossible to duplicate. They are used for Web and VPN authentication, Application security, and Email security using S/MIME.
- A PKI comprises a Certificate authority, CRL, Templates, and a hardware component. It follows a trust chain consisting of a Root CA, an Intermediate CA, and certificate templates. This determines how it should be structured to define identity and access management.
- SecureW2’s managed PKI automates certificate management so you can provision all your end users and devices with digital certificates and authenticate them safely to the network.
Digital signatures are pivotal to cybersecurity. They offer a robust mechanism to verify the authenticity and integrity of a document or message. Imagine sending a handwritten letter; your signature assures the recipient that the letter is genuinely from you.
Similarly, digital signatures assure the receiver of an electronic document that it hasn’t been tampered with and confirm the signer’s identity. In this article, we’ll explain what a PKI digital signature is, how it works, and why it’s crucial for ensuring data integrity and authenticity.
What is a PKI Digital Signature?
A PKI digital signature is a cryptographic mechanism used to authenticate the sender’s identity and ensure the integrity of a digital document or message. In a PKI, or Public Key Infrastructure, a digital signature operates on the principles of asymmetric cryptography—where a key pair, comprising a public key and a private key, is used. The private key, kept secure by the signer, encrypts a hash of the document, creating the digital signature. The corresponding public key, accessible to anyone, decrypts the signature for verification.
PKI provides the framework necessary for managing digital certificates, which are digital documents issued by a Certificate Authority (CA). These certificates link a public key to an individual or entity, confirmed through a rigorously vetted process by the CA. The CA, a trusted entity, ensures the validity and authenticity of the digital certificates it issues, underpinning the trust in secure digital communications. When a user signs a document with their private key, their digital certificate enables recipients to verify the signature using the associated public key, ensuring data authenticity and integrity while preventing tampering or impersonation.
Digital Signatures vs. Digital Certificates
Digital signatures and digital certificates are pivotal in cryptographic security but serve distinct roles. Digital signatures authenticate the identity of a message or document sender, ensuring data integrity through the use of a private key to generate the signature. Conversely, a digital certificate, issued by a Certificate Authority (CA), binds a public key to an entity’s identity, enabling others to verify the public key’s owner. While digital signatures validate content authenticity, a digital certificate establishes entity authenticity.
What is Public Key Infrastructure (PKI)?
A PKI is a comprehensive framework designed to manage public-key encryption and digital certificates, ensuring secure digital communications and transactions. Essentially, PKI provides the framework for creating, distributing, managing, and revoking digital certificates. It employs asymmetric cryptography, which relies on a pair of keys—public and private keys—to secure data.
Components of PKI
PKI comprises several critical components that work in unison to maintain its security and functionality:
- Certification Authorities (CAs): Trusted entities that issue and manage digital certificates, verifying the identity of entities requesting certificates.
- Registration Authorities (RAs): Entities that vet and authenticate individuals or organizations before a CA issues a certificate.
- Central Directory: A repository where issued certificates and their status are stored, accessible for verification by users. This is generally achieved through the use of a Certificate Revocation List (CRL) that stores lists of manually revoked certificates.
- Certificate Management System: Tools and protocols used for generating, distributing, and revoking digital certificates. An example of this is the JoinNow MultiOS Management Portal used by SecureW2’s PKI, which allows you to manage the entire certificate lifecycle from a single pane of glass.
- Public and Private Keys: Unique pairs of cryptographic keys used for encrypting and decrypting data, essential for creating and verifying digital signatures.
What is the Role of PKI in Digital Signatures?
PKI plays a vital role in the realm of digital signatures. It ensures that digital certificates, which bind public keys to individuals or entities, are managed securely and reliably. When electronic documents are digitally signed, the signer’s private key generates a unique digital signature. The recipient can then use the signer’s public key, obtained from the digital certificate, to verify the signature. This verification process ensures data authenticity and integrity, which are crucial for secure electronic transactions and communications.
Asymmetric Cryptography
Asymmetric cryptography, also known as public key cryptography, underpins PKI. It involves two distinct but mathematically linked keys: a public key, which anyone can use to encrypt data or verify a digital signature, and a private key, which the owner keeps secret to decrypt data or create a digital signature. This dual-key approach ensures that even if the public key is widely distributed, only the private key holder can decrypt the data or generate a valid signature, providing robust security and establishing trust in digital exchanges.
The Role of Certificate Authorities in PKI
CAs are integral to the PKI ecosystem. Their core functions include:
- Issuing Digital Certificates: CAs issue digital signature certificates, verifying the association between public keys and their owners.
- Identity Assurance: CAs provide identity assurance by rigorously vetting entities before issuing certificates.
- Revoking Certificates: CAs have the authority to revoke certificates if they are compromised or no longer valid.
- Publishing Certificate Status: Through mechanisms like Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP), CAs maintain an updated status of all issued certificates.
Trusted Root Certificates
Trusted root certificates form the foundation of the PKI trust model. These root certificates, held by a trusted certificate authority, anchor the trust chain, ensuring all derivative certificates are trustworthy. CAs ensure trust by conducting thorough identity verification processes, they maintain a secure infrastructure to protect their operations, and adhere to industry standards and best practices to maintain their position as trusted third parties.
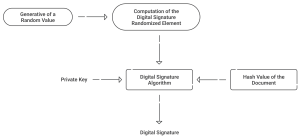
How Do PKI Digital Signatures Work?
PKI digital signatures work through a multi-step signing process underpinned by asymmetric cryptography, ensuring data authenticity and integrity. Here’s a detailed breakdown:
- Document Hashing: The document or message to be signed is first fed through a cryptographic hash function, producing a unique hash value representing the document’s contents.
- Hash Encryption: The signer uses their private key to encrypt this hash value, creating the digital signature. This private key, an essential part of their identity, must be kept secure.
- Certificate Attachment: The digital signature, along with the signer’s public key embedded in their digital certificate, is attached to the document. The digital certificate, issued by a CA, verifies the signer’s identity and associates it with the public key.
- Signature Verification: The recipient uses the public key from the digital certificate to decrypt the digital signature, retrieving the original hash value. Concurrently, the recipient hashes the received document independently.
- Hash Comparison: If the independently computed hash matches the decrypted hash value, the document is verified, confirming its integrity and the authenticity of the signer.
This process not only ensures that the document hasn’t been altered but also verifies the signer’s identity, leveraging the trust vested in the CA-issued digital certificate. This robust mechanism forms the cornerstone of secure digital communications and transactions, providing assurance of authenticity.
Components of a PKI Digital Signature
A PKI digital signature comprises of:
Encryption Keys
At the heart of a PKI digital signature are the public and private keys. A public key is widely distributed and used by recipients to verify digital signatures and encrypt data, while a private key is securely stored and used by the signer to create digital signatures and decrypt received data.
Certificate Authorities (CA)
CAs are trusted third parties responsible for the issuance and management of digital certificates.
- Signing Certificate: The CA generates a signing certificate that binds a public key to an entity’s identity, ensuring the legitimacy and authenticity of the key.
- Third-Party Certificate Authority: These CAs operate independently to provide unbiased verification and issuance of certificates, ensuring a robust trust hierarchy.
Registration Authorities (RA)
Registration Authorities (RAs) play a supportive role in PKI by validating the identities of entities before a CA issues a digital certificate. RAs undertake rigorous identity verification processes to ensure the authenticity of the entities requesting certificates.
With the use of private PKIs inside an organization, this role can be performed with the use of an internal directory, such as a SAML Identity Provider. As an example, consider our managed PKI, which can issue certificates to both devices managed by an MDM such as Intune, or unmanaged devices/BYODs. In the former case, the device is issued a certificate through the MDM with the use of the Simple Certificate Enrollment Protocol (SCEP). In the latter case, end users can configure their own devices for certificates by using our device onboarding application and verifying their credentials, whether those are Okta, Azure AD (Entra ID), Google, OneLogin, or other credentials.
How to Create a PKI Digital Signature
Creating a PKI digital signature involves several technical steps, facilitated by specialized software:
- Obtain a Digital Signature Certificate: You need to obtain a digital signature certificate from a trusted third party certificate authority (CA).
- Generate a Key Pair: Use the certificate management software to generate a pair of public and private keys.
- Sign the Document: When you intend to sign a document, the private key is used to encrypt the document’s hash value, thereby creating the digital signature.
- Attach the Signature: The digital signature is then embedded into the document, along with the signer’s public key found in the digital certificate.
Verifying Your PKI Digital Signature
Verifying a PKI digital signature ensures that the signer is authenticated and the document’s integrity is intact:
- Retrieve the Public Key: Access the signer’s public key from the attached digital signature certificate.
- Access the Digital Signature: Extract the digital signature from the signed document.
- Decrypt the Signature: Use the extracted public key to decrypt the digital signature, retrieving the document’s original hash value.
- Hash the Document Independently: Independently hash the received document using the same cryptographic hash function.
- Compare Hash Values: Compare the independently computed hash value with the decrypted hash value.
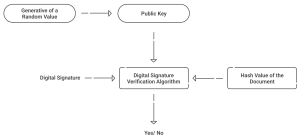
If the hash values match, the document is verified as authentic and unaltered, thus confirming the signer’s identity.
The Security of Digital Signatures Made Easy with SecureW2
Our managed PKI delivers robust encryption and identity verification mechanisms, making enterprise-grade security accessible to organizations of all sizes. Whether you are a small business or a large corporation, SecureW2 simplifies the complexities associated with PKI by providing automated certificate issuance, key management, and seamless integration with existing IT infrastructure.
Our managed RADIUS service significantly enhances certificate-based authentication. By leveraging the identity information stored in your existing SAML Identity Provider (IDP), SecureW2 enables real-time application of network access policies for both wired and wireless networks. This ensures that only authenticated and authorized users can access your network, effectively reducing the risk of unauthorized access.
Request a demo to see how our passwordless platform could protect your organization from messaging manipulation, man-in-the-middle attacks, and more.