Key Points
- NaaS provides scalable network services using a cloud-based, subscription-driven paradigm. It eliminates on-premise hardware and allows dynamic resource provisioning.
- NaaS provides seamless scalability, integrated security services, and cost-effective administration without hardware maintenance by enabling real-time reconfiguration of network architecture through virtualized infrastructure.
- SecureW2's Cloud RADIUS ensures safe and efficient network access for NaaS by enabling passwordless authentication and strong integration with Azure AD, Okta, and Google.
NaaS, or Network as a Service, is a cloud-based networking model that modifies how businesses handle and use their networks. Instead of having a lot of network equipment on-site, you can subscribe to network services on a pay-as-you-go basis.
NaaS is a flexible, scalable, and affordable option for organizations since it enables them to allocate network resources as needed. It’s revolutionary for businesses that value adaptability and speed in their network administration.
NaaS provides an essential link between static networking and the ever-changing demands of cloud computing in today’s cloud-centric environment. Businesses can quickly adjust to new requirements, such as growing operations, moving to a hybrid cloud architecture, or accommodating remote employees. Since NaaS can be accessed practically from anywhere, it guarantees constant connection, making it an invaluable resource in today’s decentralized digital workplace.
Security becomes more important as NaaS changes how businesses operate their networks. The cutting-edge cloud-based technologies and services provided by SecureW2 discreetly fortify network security and authentication.
Read this case study and discover how SecureW2 assisted a healthcare provider in taking Network security to the cloud.
Understanding NaaS
How Did NaaS Develop?
Most companies were designing their network architecture before the internet was trusted. They established private internet and linked facilities with leased connections. They configured their own WANs and required firewall gear, DDoS protection, load balancing, etc., at each office. Enterprises also required MPLS-based dedicated connections between locations.
Employees who connected to the internet instead of the internal network had to use a VPN to cross the company network. As certain corporate functions moved to the cloud, this strategy proved inefficient. As cloud computing grows more efficient, more features are offered. Today, the cloud can host DDoS mitigation, firewalls, load balancing, and other networking services, removing the need for internal IT staff to design and operate them.
For these reasons, NaaS is more efficient than internally managed WANs, which need regular maintenance and sometimes choke network traffic. Instead of internal IT teams trying to meet network demand, NaaS lets individuals connect to their cloud services directly over a virtual network managed and secured by an external provider.
Components of NaaS
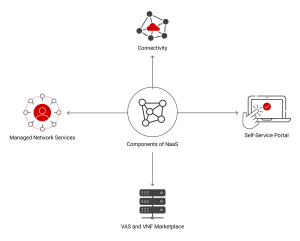
Connectivity
Connectivity focuses on delivering network channels with predetermined bandwidth and quality of service (QoS). It enables various devices, systems, and networks within the organization to exchange data and communicate.
Connectivity enables organizations to access the virtual hardware services offered by NaaS vendors, allowing them to conduct their daily operations efficiently and satisfy customer demands. This component grants organizations access to storage units for storing data, firewalls for protecting sensitive data, and switches or routers for controlling network traffic.
Self-Service Portal
The self-service portal is a component of NaaS that enables organizations to communicate and access their virtual network functions (VNFs) ecosystem in almost real-time. This portal has a user-friendly interface and is accessible via web browsers and proprietary software. Through the NaaS portal and integrated VNF marketplace, organizations can administer their network and value-added services (VAS) with a single click after establishing connectivity.
VAS and VNF Marketplace
Value Added Services (VAS) and Virtual Network Functions (VNF) are NaaS components that enable organizations to access and acquire network services and fundamental connectivity. VAS services enhance a network’s functionality and capabilities. Completely managed LANs, firewalls, and other forms of network security, VoIP, and MVNs are all possible examples of such services.
The VNF marketplace provides organizations with an accessible and simple-to-use portal for purchasing VAS. Typically, these VAS consist of VNFs. The VNF marketplace provides businesses with multiple alternatives for acquiring additional network functions such as routers, firewalls, and load balancers without investing in additional hardware. Consequently, they can readily scale up or down their operations to meet demand.
Managed Network Services
Managed network services refer to the networking tasks businesses delegate to a managed service provider (MSP), the NaaS provider. During the relocation and implementation phases, these services enable existing IT teams to focus on other duties. This increases operational efficiency because the NaaS provider can monitor and troubleshoot particular services.
NaaS operations span from basic network connectivity to virtual network services. The NaaS provider may also provide managed services for WAN optimization, unified communications, network administration, cable installations, and network monitoring.
Key Features and Benefits
Flexibility
Cloud services offer greater adaptability and customization. The network is modified using software, not hardware. IT departments can frequently reconfigure corporate networks on demand.
Scalability
Traditional hardware-based services are inherently less scalable than cloud services like NaaS. Enterprise NaaS clients can purchase additional capacity from a vendor instead of purchasing, installing, and activating additional infrastructure.
Access From Anywhere
Users may be able to access a cloud-based network from anywhere — and on any device — depending on how it is set up, albeit this creates the need for effective access control. Ideal users require only an internet connection and login credentials.
No Maintenance
The cloud provider manages software and hardware enhancements and maintains the network.
Bundled with security
NaaS enables a single provider to provide networking and security services like firewalls. This results in enhanced network and network security integration.
Cost Savings
This benefit is contingent on the vendor. However, purchasing cloud services rather than developing one’s own services frequently results in cost savings: cloud customers do not need to purchase and maintain hardware, and the vendor already possesses the infrastructure necessary to provide the service.
Challenges of NaaS
Compatibility
The NaaS provider’s infrastructure may not be compatible with legacy systems, such as antiquated hardware and on-premises applications.
Legacy Data Centers
Critical applications and processes in many organizations are still hosted on-premises, not in the cloud. This makes migration to a NaaS model more difficult.
Vendor Lock-in
Moving to a cloud service always introduces the possibility that an organization will become overly reliant on a single service provider. Vendor lock-in can have serious repercussions if the service provider’s infrastructure fails or if they increase their prices.
How Does NaaS Relate to SASE?
Secure access service edge (SASE) is a combination of software-defined networking and network security functions provided by a singular service provider. As with NaaS, SASE integrates networking and security functions and hosts them in the cloud. In many respects, NaaS and SASE are similar models for how an increasing number of businesses operate today.
Key Differences and Similarities
1 – Architecture and Infrastructure
NaaS – The service predominantly concentrates on subscription-based network services, typically via a virtualized infrastructure. It centralizes network management and access control, but connectivity may still rely on traditional VPNs or dedicated circuits.
SASE – In contrast, Secure Access Service Edge incorporates network and security functions into a single cloud architecture. It integrates network connectivity and security functions, facilitating access and security in a more unified fashion.
2 – Security and Access Control
NaaS – NaaS may not provide the same level of comprehensive security as SASE, even though it provides network services and frequently incorporates security features. It may be necessary to incorporate additional security measures to ensure robust protection against emergent threats.
SASE – Security is central to SASE. It employs Zero Trust Network Access (ZTNA) and other technologies to provide secure resource access. This integrated security approach protects data and applications regardless of the user’s location, making it ideal for today’s decentralized workforce.
3 – Use Cases and Applicability
NaaS – NaaS provides network services that are scalable and accessible. It is an excellent option for organizations seeking network management flexibility and agility. Use cases for NaaS include expanding operations, facilitating remote work, and supporting hybrid cloud environments.
SASE – SASE is designed for secure, scalable, and efficient cloud resource access. It is intended for businesses prioritizing security and replacing traditional VPN and SD-WAN solutions with cloud-native alternatives. SASE is a preferred option for organizations undergoing digital transformation because it is especially good at securing data and apps in the cloud.
The Role of Cloud RADIUS SecureW2 in NaaS
SecureW2’s Cloud RADIUS is critical in solving compatibility issues between NaaS and on-premise configurations, especially in the context of network security. Cloud RADIUS is a robust solution that lets organizations move away from ineffective password-based security in a world where passwords are becoming more easily cracked.
Cloud RADIUS is the best way to improve network security and lower the risks of password-based authentication, as industry leaders like Microsoft and reputable groups like CISA support certificate-based network authentication.
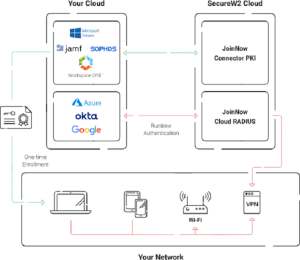
Cloud RADIUS’s best feature is that it can provide a 100% passwordless login system, meaning it doesn’t need LDAP or Active Directory (AD) servers. Cloud RADIUS ensures network security is very safe by using digital certificates and integrating natively with Azure AD, Okta, and Google settings.
Its use of digital certificates, especially in the EAP-TLS security system, makes getting full information about the device and user easier, strengthening the Zero Trust Network Security method. Cloud RADIUS is a complete solution for improving network security that works with many operating systems and allows easy management and integration. It has features like real-time user lookup, MDM integration, and a customized access policy engine.
Emerging Network Models and Their Impact on Cybersecurity
As the networking and cybersecurity landscape evolves, emerging models are poised to shape the future. Zero Trust Networking, a paradigm that considers every user and device untrusted until proven otherwise, is becoming a linchpin of network security in the twenty-first century. Edge computation Networks, which bring computation closer to the data source, transform how data is processed by providing both speed and data sovereignty advantages. While still in its early stages, Quantum Networking retains the promise of unhackable communication via quantum key distribution.
These innovative models have significant implications for cybersecurity beyond simply advancing technology. As cyber threats evolve, enhanced security measures, such as continuous authentication and data encryption, will become increasingly crucial.
With an ever-changing threat landscape characterized by the emergence of new attack vectors and vulnerabilities, robust cybersecurity becomes essential. Artificial Intelligence (AI) and Machine Learning (ML) will increasingly play a vital role in threat detection, mitigation, and response.
These technologies will be instrumental in predicting and defending against cyber threats in real time, allowing for a more proactive approach to cybersecurity. In the coming years, businesses and organizations will need to adopt these future models and modify their cybersecurity strategies to remain resilient in a digital landscape that is constantly evolving.
As organizations adjust to a fast-changing technology world, the relevance of cloud computing cannot be more emphasized. Cloud infrastructure delivers scalability, flexibility, and accessibility, allowing organizations to manage their data and applications more effectively.
Companies that use cloud services may simplify processes, boost communication, and increase overall efficiency. However, these advantages are accompanied by security concerns since the cloud yields its own set of challenges and vulnerabilities.
Empowering Your Network With NaaS and SecureW2 in the Cloud
Network-as-a-Service (NaaS) has emerged as a transformative force in the cloud computing industry. Its subscription-based model, accessibility from anywhere, and centralized management have transformed how businesses manage their networks.
NaaS provides a dynamic solution that adapts to changing requirements, making it an essential option for businesses seeking flexibility and efficacy in network management. This strategy improves connectivity, scalability, and cost-effectiveness while meeting the requirements of a modern, decentralized work environment.
SecureW2’s contribution to NaaS is instrumental in overcoming obstacles, especially on-premise compatibility. SecureW2’s cloud-based products and services integrate seamlessly with NaaS, enhancing network security and authentication. Contact us and improve the overall NaaS experience with a secure, scalable, and accessible solution.