Key Points
- SecureW2’s managed PKI lets users enroll for X.509 certificates via SSO with Okta—even without Active Directory
- You start by configuring a SAML Identity Provider in SecureW2 and creating a SAML application in Okta, linking them using ACS URL and Entity ID for seamless certificate issuance
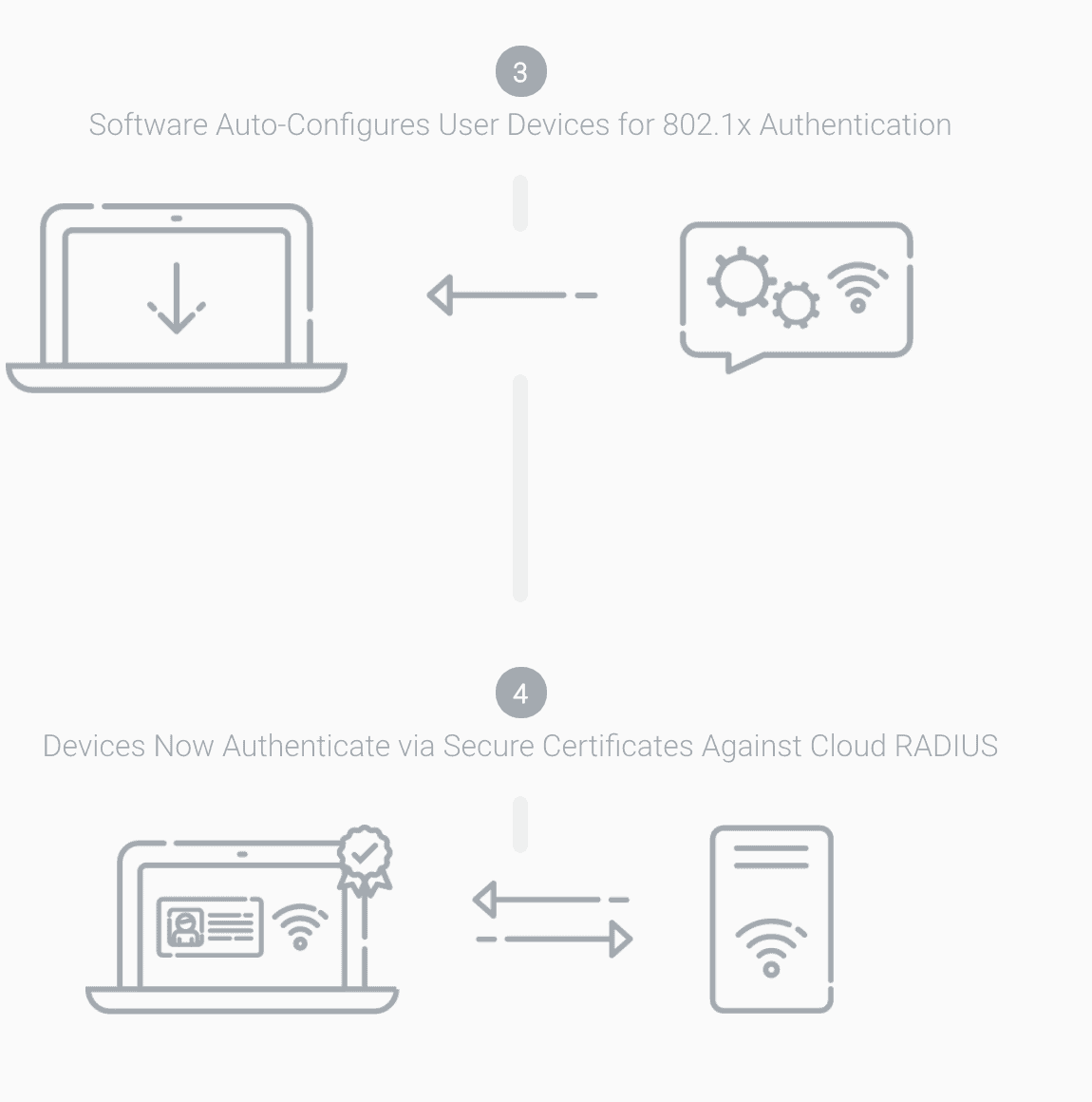
- For managed devices, SecureW2 can use Gateway APIs (e.g., with Intune) to automatically push 802.1X certificate provisioning, simplifying deployment and minimizing IT configuration errors.
A major challenge that organizations face in regards to certificates is enrolling users without Active Directory. In response, SecureW2 has developed a solution that can provide a certificate-based network regardless of the directory in use.
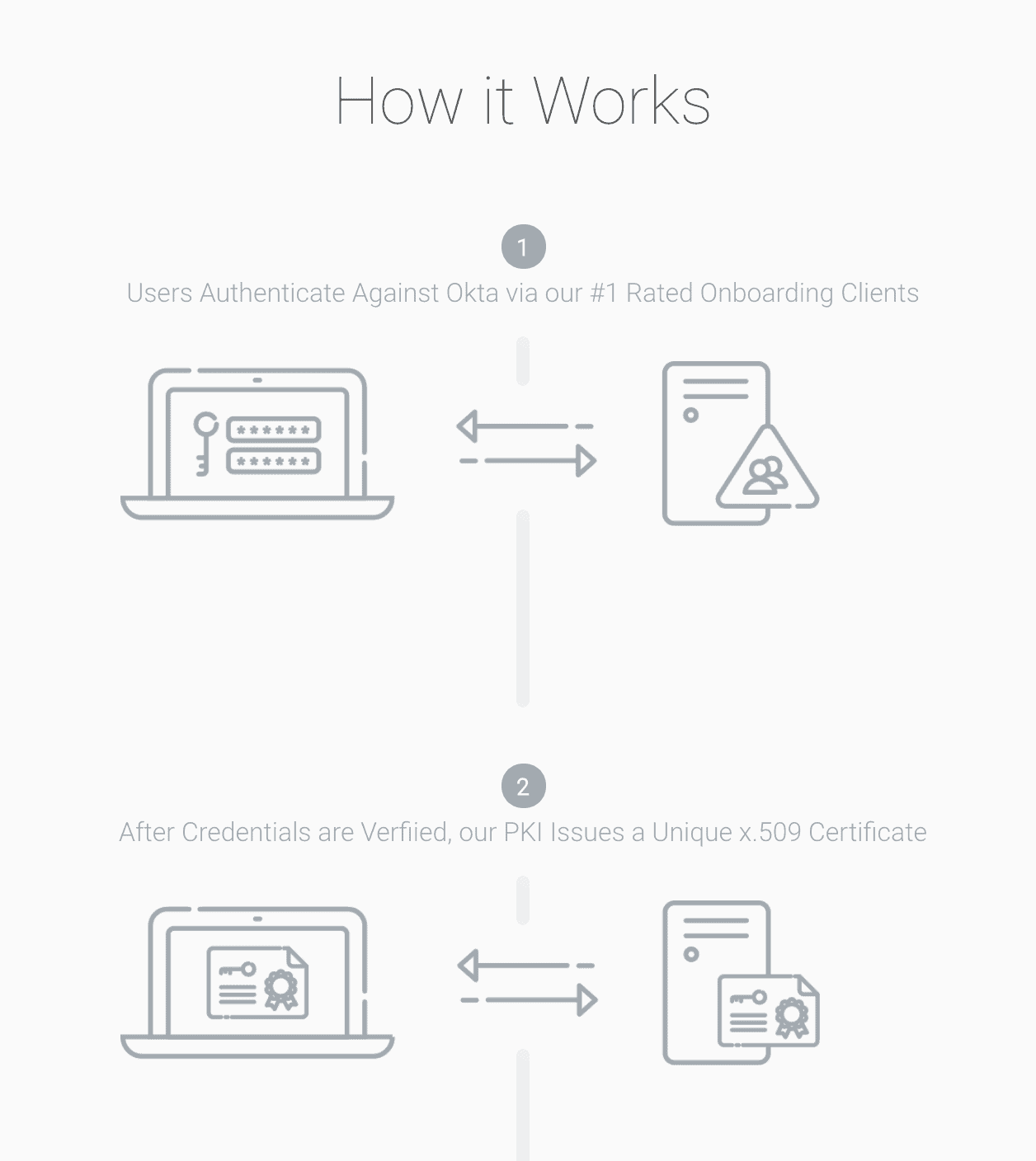
SecureW2’s managed PKI allows end-users to easily enroll themselves for certificate authentication with a simple Single Sign-On (SSO) that works out of the box with Identity Providers like Azure, Google, and Okta. Check out how easy it is from one of our customers.
In the past, certificates were only used by large entities with high-security requirements., However, with the increase in cybercriminal activity, surpassing all other types of crime and the advancement in data theft techniques, certificates have become the quintessential method for network authentication. Certificates provide a substantial upgrade to network security and user experience as proper use of certificates can eliminate the threat of Man-in-the-Middle attacks and password-based headaches.
SecureW2 can provision devices with certificates easily through our #1 rated onboarding software. Paired with a variety of useful certificate management features available through our Cloud Managed PKI Service, employing Public Key Cryptography on your network has never been easier. This guide will show you how to generate x.509 certificates with Okta, so you can take advantage of a maximum-grade security network.
How x.509 Certificates Work With Okta
Create an Identity Provider in SecureW2
Creating an IDP in SecureW2 tells our 802.1x onboarding software and Cloud RADIUS server how to connect to your Okta IDP so SecureW2 can verify user credentials and issue certificates that can be authenticated by a RADIUS server.
To create an IDP in SecureW2:
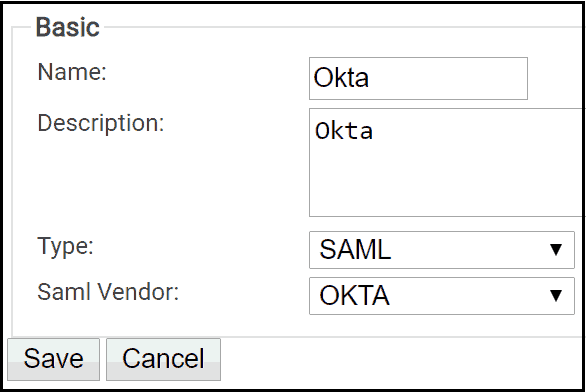
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers.
- Click Add Identity Provider.
- For Name, enter a name.
- For Description, enter a description.
- Click the Type dropdown and select SAML.
- Click the Saml Vendor dropdown and select Your chosen vendor.
- Click Save.
Create a SAML Application in Okta
By combining Okta identity management and SecureW2’s EAP-TLS certificate solutions, network users can be easily equipped with certificates for RADIUS authentication.
- From your Okta dashboard, go to the Dashboard page.
- Under Shortcuts, click Add Applications.
- Click Create New App.
- In the Create a New Application Integration prompt:
- Click the Platform dropdown and select Web.
- For the Sign on method, select the radio button for SAML 2.0.
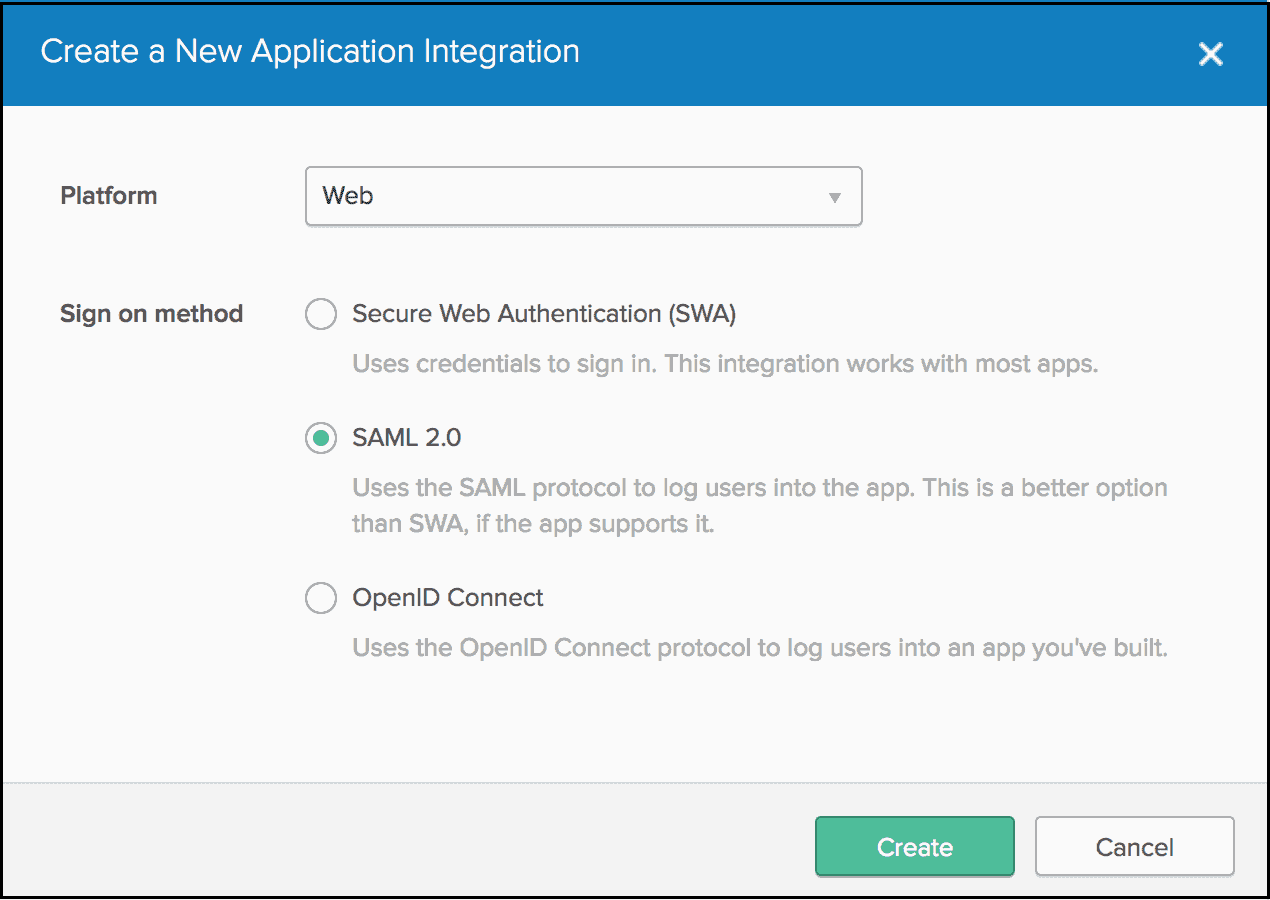
- Click Create.
- On the 1 General Settings step, for App name, enter a name.
- Click Next.
- In a new browser tab/window, log in to your SecureW2 Management Portal and go to Identity Management > Identity Providers.
- Click Edit for the IDP you created in the section “Create an Identity Provider in SecureW2”.
- Select the Configuration tab.
- Copy and paste as follows:
- From SecureW2, copy the information for ACS URL and EntityId, and
- Paste respectively into Okta (2 Configure SAML step) for Single sign on URL and Audience URI (SP Entity ID).
- Click Next.
- On the 3 Feedback step, “Are you a customer or partner?”, select the appropriate radio button.
- Click Finish.
Enrolling BYODs for Okta
SecureW2 automates the onboarding process for end-users using our #1 rated 802.1x onboarding clients. This eliminates any risk of user misconfiguration and MITM credential theft, ensuring that you have the safest network available.
The SecureW2 solution redirects users to Okta’s Single-Sign-On where they enter their credentials and are then enrolled for a certificate that is automatically configured for 802.1x by SecureW2.
Organizations no longer have to be restricted by outdated hardware such as on-premise Active Directory servers. Devices only need to be authenticated once and are set until the certificate expires, which can be adjusted by network administrators.
Enrolling Managed Devices for Okta
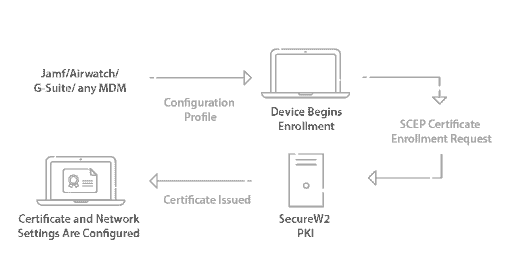
For managed devices, many organizations with Okta integrate their Mobile Device Management software through our Gateway APIs so they can silently auto-enroll their managed devices for certificates. You can use these gateways to generate policies and settings that are sent to Intune devices so they are automatically enrolled for 802.1x digital certificates. This makes things substantially easier for IT administrators who no longer need to stress about configuring managed devices. Click here for our Intune integration guide.
Certificate Authentication with Okta and SecureW2
With SecureW2, your organization can have a top of the line, certificate-backed network that is fully functional in a matter of hours. We provide you with an amazing support team that is ready to assist with any help you may need with the process.
SecureW2 works with all SAML-based Cloud Identity Providers so you don’t have to worry about any headaches associated with the integration process. If you’re ready to make the transition to secure and easy-to-use certificates, check out our Okta solutions page here to see if we can be of service.