Key Points
- FIDO2 lets users log in without passwords, using biometrics, PINs, or security keys, making access simpler and more secure.
- Deployment complexity, device compatibility issues, and user onboarding challenges can slow down FIDO2 adoption in organizations.
- SecureW2 makes FIDO2 easy with automated certificate management, secure network access, and smooth user onboarding for any device.
Security Keys are a method of authentication that is becoming increasingly more commonplace due to the additional layer of security they provide. They are a versatile security component that can be used to log in to Wi-Fi, desktops, websites, and applications.
Security Keys have actually been present for around a decade, but only recently have they been used in the mainstream. This is partially due to the innovations in technology from companies like Yubico, as well as IT professionals becoming more aware of the problems caused by insecure passwords. With 10 million attacks targeting usernames and passwords occur every day, organizations need to be doing everything in their power to avoid credentials. SecureW2 provides easy-to-use software that allows end-users to enroll their security keys for certificates, see how it is from one of our customers.
One relatively recent change Yubico (as well as other providers) have implemented is incorporating FIDO2 capabilities with their physical security keys. But what exactly is FIDO2, and how does it work to improve an already secure technology?
What is FIDO?
FIDO stands for “Fast Identity Online” and it was created in order to do just that – securely access online services without having to install new software and drivers. So instead of relying on a static piece of data you know (like a password) FIDO relies on physical tokens (Security Keys) to access data on a network.
These keys are capable of robust cryptography without any actions required from the end-users. When the key is registered, a Public and Private key pair is generated for the client-side and user-side respectively.
Each time a user sends data, it is encrypted by the shared public key and can only be decrypted by the receiver’s private key. The matched keys confirm the other party is the same entity that they registered with, which prevents any bad actor from accessing the data. The security key can’t communicate with any other device until it is unlocked physically by the user.
How Do FIDO2 Security Keys Work?
FIDO2 is the next generation in the FIDO family tree. It combines the capabilities of Web Authentication (WebAuthn) with Client-To-Authenticator-Protocol (CTAP) to expand the more advanced FIDO2 to more browsers and devices. The new and improved FIDO2 enables more methods of authentication to be verified by a single key.
FIDO2 is also an open standard that allows for flexibility in product choice. It’s designed for all existing phones and computers, many authentication modalities, and different communication methods including USB and NFC.
FIDO2 Specifications
WebAuthn
Developed by the World Wide Web Consortium (W3C), WebAuthn is a web-based API that enables FIDO-based authentication for web browsers and platforms. Users leverage common devices to easily authenticate to online services in both mobile and desktop environments. Web services and apps can – and should – turn on this functionality to give their users an easier login experience via biometrics, mobile devices, and/or FIDO security keys – and with much higher security over passwords alone.
CTAP2
The second specification of FIDO2, CTAP2 enables physical devices to connect to web browsers and platforms that support WebAuthn. CTAP2 is the second iteration of CTAP1, which is used by FIDO U2F, the predecessor of FIDO2.
When To Use FIDO2 Security Key
Security Keys are undoubtedly useful for anyone who wants to prioritize security. Whether you want to protect your bank account or your Twitter, a security key can help keep your information safe.
Anyone from Enterprise Level corporations to small business operations will find countless different ways to use them. They can integrate into most authentication processes you encounter:
- Log in to a user account on a laptop or desktop
- Log in to a VPN or proxy service
- Log in to social media
- Log in to web applications
- Regulate access to secure buildings, rooms, servers, etc.
- Control privileged account access
FIDO2 Security Keys add the benefit of authenticating quickly without needing to remember any passwords. These keys can simply be plugged in and clicked – voila, authentication made simple.
FIDO2: A Passwordless Version of FIDO U2F
FIDO’s Universal 2nd Factor (U2F) protocol was developed by Google and Yubico with the goal of strengthening credential-based login systems with a physical security key. The key owner must input their key in a laptop/computer and then enter their login credentials, creating a two-step verification process. While this is a better security measure, it introduces the concern of the security key falling into the wrong hands.
A vulnerability was discovered with the Google Titan security keys where the attacker could extract private keys from the Google Titan key and create duplicates. To be fair, in order to exploit the vulnerability a would-be hacker needs to physically have the Titan key, which is a rare security risk, but possible. Essentially, the vulnerabilities are caused by the human element. People can forget or share their login credentials or security keys can be stolen.
FIDO2 expands FIDO’s use case opportunities by extending FIDO capabilities to passwordless solutions while promoting the migration towards passwordless systems going forward. FIDO2 is based on the FIDO U2F model meaning U2F will still be compatible with platforms and browsers that support FIDO2.
The best FIDO2 deployment solution excludes login credentials as an authentication factor and encrypts information on the security key so it cannot be breached if the key is lost. That solution happens to be digital certificates.
Improving FIDO2 Security Keys With Digital Certificates
While FIDO U2F is still a strong authentication protocol for most organizations, it’s apparent that the ideal authentication solution has nothing to do with passwords. Fortunately, certificates can pick up where passwords falter. Certificates remove any possibility of user error by relying on rigorous security protocols, encrypted key pairs, and easy identification. Using certificates for facets of your network perimeter is the easiest way to significantly enhance the strength of your network security.
Security keys don’t protect you from more advanced over-the-air hacking techniques, such as the infamous man-in-the-middle attack. The credentials are securely passed to the device, but that’s as far as security key protection goes. They’re communicated over the same network as all of the other potentially insecure traffic. Certificates ensure that the authentication process is protected from start to finish. The private keys are invulnerable from the moment they’re generated on the security key until they are authenticated by the recipient application.
The Ultimate FIDO2 Solution: Yubikeys with Certificate Enrollment Software
SecureW2 has the industry’s only solution for using certificates with Yubikeys. With SecureW2, you can easily onboard users and have them configure security keys with certificates in minutes. This takes the burden away from IT departments who would traditionally have to manually enroll each Yubikey. Instead, end-users are fully capable of enrolling certificates themselves using our portal. Storing those certificates on a Yubikey adds an invaluable MFA element to your security, allowing you to be confident that you are protected from over-the-air attacks and phishing.
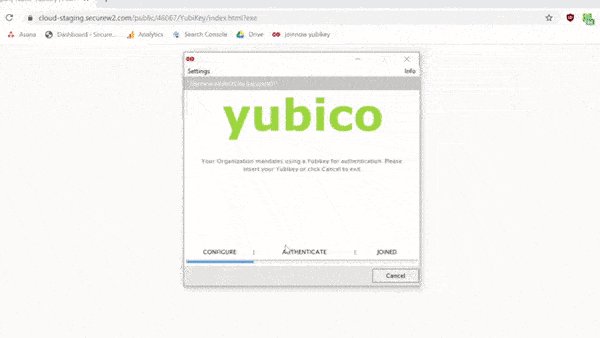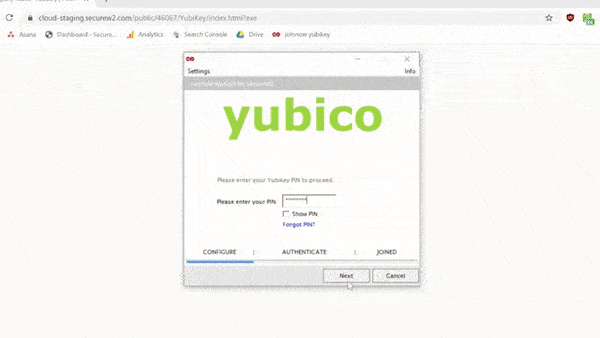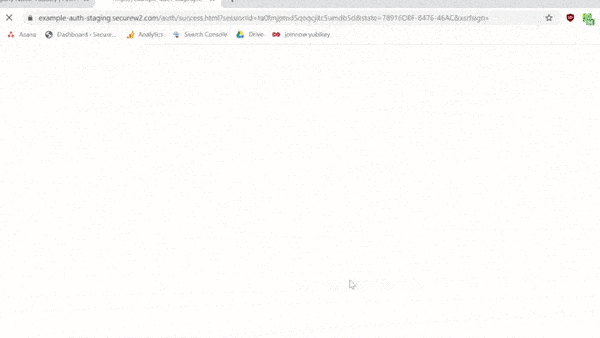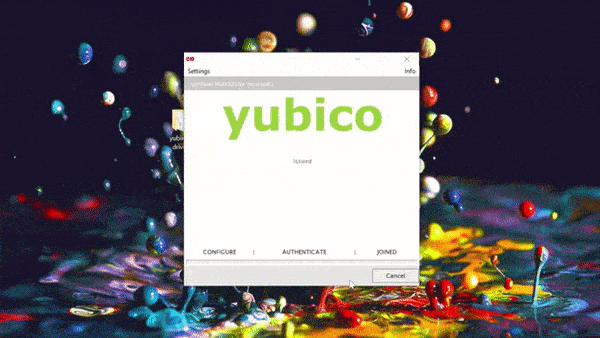
Enrolling Yubikeys for certificates is simple with SecureW2. With just a few clicks in our world-class management portal, you can create a custom client that will configure your Yubikey for certificate enrollment. Our #1 onboarding software comes with the Getting Started Wizard, providing everything you need to enroll a Yubikey for a certificate. Here’s a brief GIF of the process:
Configuring FIDO2 Keys for Microsoft
The best option to incorporate FIDO2 in Windows environments is by combing security keys, namely Yubikeys, and Azure Active Directory (AD). The current iteration of passwordless authentication for Azure AD (Microsoft Entra ID) is a big improvement over passwords, however, it has one major drawback: scalability.
Azure AD is valued because it can scale infinitely and remains easily manageable. Unfortunately, Yubikeys cannot claim the same thing. They’re a pain to set up because each one has to be manually configured via a command-line interface with the correct certificates to enable the Azure integration. That task is too complicated to be left to the end-user, which means that deploying pre-configured Yubikeys to an organization becomes a huge task for IT.
By pushing a payload that includes an automatic configuration package, Yubikeys can be induced to self-enroll for certificates upon the first-time setup. Our customizable onboarding client walks end-users through a foolproof setup process that ties their identity and existing Azure AD credentials to the Yubikey, with optional PIN/PUK complexity requirements.
If you’re interested in exploring the possibilities of certificate onboarding and simple self-enrollment, read about our Yubico integration here. If you want to know more about how our products work with Yubico, check out our solution page here.