Key Points
- Jamf Pro 11 supports ACME certificate payloads with MDA, enabling hardware-bound keys and attested device identity.
- Dynamic SCEP and ACME automation replace static shared secrets, ensuring per-device challenges, automatic renewals, and reduced downtime.
- SecureW2 integration enforces policy-driven issuance with device posture checks (FileVault, OS version, compliance state) and real-time revocation.
Digital certificates have become the backbone of safe access in Apple environments, and Jamf is still the top platform for managing Macs, iPhones, and iPads at scale. By integrating Jamf’s management capabilities with certificate-based authentication, organisations can replace weak, shared passwords with device-specific credentials. These certificates cannot be phished or reused, making them a considerably more secure basis for safeguarding Wi-Fi, VPN, and business-critical applications.
While Jamf has a built-in CA, it was created for simple use cases and lacks the automation, policy controls, and visibility required in prevailing deployments. Most companies rely on external PKIs to simplify enrollment, ensure compliance, and extend certificates beyond Wi-Fi authentication.
With the release of Jamf Pro 11, certificate enrollment has grown significantly New support for modern protocols such as ACME (Automated Certificate Management Environment) and MDA (Managed Device Attestation), as well as advancements in automation and compliance, enable IT teams to handle certificates with greater flexibility and assurance than ever before. These improvements represent a move from static, one-time enrollment to dynamic, policy-driven certificate lifecycles, paving the way for increased security and reduced costs in Apple-first enterprises.
What’s New in Jamf Pro 11 for Certificate Enrollment
Jamf Pro 11 has made certificate enrollment easier and less labor-intensive. The UI has been redesigned, with improved navigation for certificate payloads and configuration profiles. This small, but significant enhancement, allows administrators to easily discover the appropriate settings and standardize the experience throughout Jamf’s MDM tool set.
Beyond UI changes, the most important story is Jamf’s expanded support for modern certificate protocols. Admins can now utilize ACME with MDA, which provides greater device validation and avoids the vulnerabilities associated with the static secrets that SCEP(Simple Certificate Enrollment Protocol) relies on. This makes Jamf certificate management compatible with Zero Trust requirements.
Jamf Pro 11 also includes lifecycle enhancements that reduce the possibility of downtime. With automated redistribution of ACME certificates, certificates may be renewed on devices several days before they expire, avoiding connection gaps. Similarly, companies using DigiCert Trust Lifecycle Manager may enable automated seat creation when delivering certificates via SCEP, eliminating the need to create seats for each user or device manually.
These upgrades simplify certificate issuance, renewal, and integration, offering Jamf administrators reliable tools for managing secure authentication at scale.
SCEP Workflows in Jamf
The SCEP has been the standard technique for issuing certificates in Jamf-managed settings for many years. In a SCEP workflow, Jamf Pro is the MDM, delivering a configuration profile including the SCEP payload to devices. When a device receives the profile, it immediately seeks a certificate from an external Certificate Authority (CA) and uses a shared secret or challenge password to finish the registration process. Once granted, the certificate may be used for Wi-Fi, VPN, and other secure services with minimal end-user participation.
The most significant advantage of SCEP is its maturity. It is compatible with almost all Apple systems, interacts well with Jamf payloads, and is reasonably simple to configure. For administrators, this means simple deployments and a consistent user experience that eliminates the need to request or install certificates manually.
However, SCEP has limits. Relying on static shared secrets might pose security issues if not properly secured. Revocation is not tightly integrated, necessitating extra tools or manual processes to maintain certificates current. SCEP lacks advanced policy enforcement, making it less suitable for current Zero Trust needs.
To fill these gaps, SecureW2 provides Dynamic SCEP, which replaces static shared secrets with unique, per-device challenges and combines certificate issuance with policy checks. This technique considerably reduces the risk of traditional static SCEP while retaining its simplicity and wide compatibility.
With these advancements in mind, it’s evident why many organizations are transitioning to modern enrollment methods.
Modern Enrollment with ACME + MDA
What is ACME?
ACME is a modern protocol that automates the request and installation of certificates from a CA, removing the outdated requirement for static shared secrets, such as in SCEP. Jamf Pro 11 now supports the ACME Certificate payload (designated by com.apple.security.acme), allowing administrators to customize key settings such as the ACME server URL, client identity, hardware binding, key type/size, and optional attestation parameters.
What is MDA?
Apple announced Managed Device Attestation (MDA) as a security feature allowing a device to confirm its authenticity (for example, a genuine Apple hardware with particular device attributes and a hardware-bound private key) using the Secure Enclave and Apple’s attestation service. When combined with ACME, MDA guarantees certificates are only provided to verified, uncompromised devices.
How ACME + MDA addresses SCEP gaps
Short-lived, automated certificates: ACME supports automatic lifecycle management, including certificate rotation, without administrative involvement.
Stronger assurance: MDA guarantees that only trusted devices with proper attestation may receive certificates, thus even if a profile is hacked, the certificate cannot be misused.
Hardware-bound keys: Private keys are generated within the Secure Enclave and remain there, making extraction or replay attacks impossible.
Configuration in Jamf
Jamf Pro 11 now includes support for ACME Certificate payloads within configuration profiles. This payload describes how a device communicates with the ACME server, including certificate authority information and enrollment procedures. Administrators may activate Managed Device Attestation within this payload, ensuring that devices cryptographically establish their identity during registration. Jamf’s Network Relay payload may also use ACME-issued certificates for safe authentication, which extends certificate trust to relay communications.
Enrollment Process
Once Jamf MDM pushes the configuration profile:
- The device accepts the ACME and Network Relay payloads.
- It sends an ACME enrollment request with embedded attestation data.
- The ACME server checks the request against the device’s hardware and OS configuration.
- If successful, the server issues a certificate.
- The certificate can be instantly used for Wi-Fi, VPN, and relay authentication.
Benefits of ACME and MDA
This approach increases security by guaranteeing that only valid, trusted devices obtain certificates. Automation reduces renewal costs, and easier network access expands certificate usability across services. In particular, the MDA implements a Zero Trust policy, requiring devices to verify their authenticity rather than being trusted by default.
SecureW2 Integration with Jamf Pro 11
Integrating SecureW2 with Jamf Pro 11 expands Jamf’s device management capabilities by providing a comprehensive PKI and certificate lifecycle automation solution. This integration allows enterprises to offer certificates via SCEP or ACME effortlessly, enforce compliance requirements, and automate revocation events without requiring manual intervention.
Additionally, SecureW2 provides a Dynamic PKI model in which device metrics such as FileVault status, OS version, or enrollment state are verified before a certificate is granted and are continuously monitored after issuance. Administrators can automatically suspend or revoke a device’s certificate if it fails to comply or exceeds a certain threshold. This ongoing validation ensures that certificates are not static trust tokens, but rather live credentials linked to the device’s current security posture.
Setting up Certificate Enrollment via SCEP on Jamf
Setting up SCEP in Jamf requires configuring SecureW2’s Certificate Authority as an External Certificate Authority in Jamf. To configure an external CA in Jamf:
- Log in to the Jamf Pro console.
- Navigate to Settings > Global.
- Click PKI certificates.
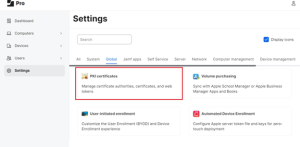
- Select the Management Certificate Template tab, select External CA, and click Edit.
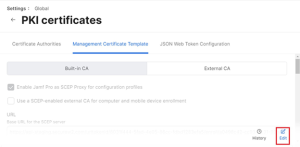
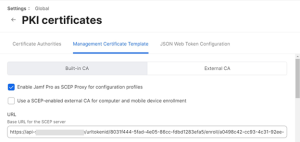
- Select the Enable Jamf Pro as SCEP Proxy for configuration profiles checkbox.
- In the URL field, enter the new SCEP URL you saved in the CSV file.
NOTE: You can also refer to the steps in Configuring API Tokens (SCEP
Enrollment Token) in the JoinNow MultiOS and Connector Configuration Guide available in the Management Portal.”
- In the Name field, enter the name of the certificate-issuing CA created in the JoinNow Management portal.
- In the Subject field, enter “CN=$DEVICENAME.”
- From the Subject Alternative Name Type drop-down list, select None.
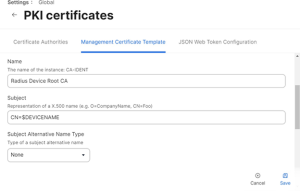
- From the Challenge Type drop-down list, select Dynamic.
- From the Key Size drop-down list, select 2048. SecureW2 does not recommend selecting 1024.
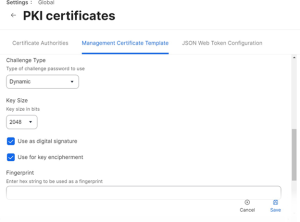
- Click Save.
- Under the Signing Certificate section, click Change Signing and CA Certificates to upload the signing certificate.
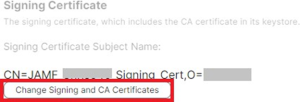
- On the Upload Keystore step, click Choose File and upload the PKCS12 file you downloaded in “Creating a Signing Certificate for Jamf.”

- Click Next.
- On the Enter Password step, enter the password you entered in the Password for private key prompt in the Creating a Signing Certificate for Jamf section when you created the certificate.
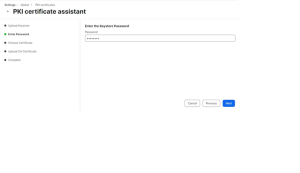
- Click Next.
- On the Choose Certificate step, verify that the correct CA certificate is selected from the Choose Certificate drop-down list and that the correct certificate chain is displayed.
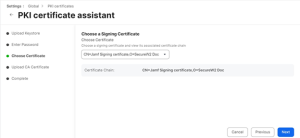
- Click Next.
- On the Upload CA Certificate step, click Next to skip the upload. The CA certificate is already present in PKCS12.
- On the Complete step, click Done.
Best Practices: Policy-based Certificate Issuance and Device Compliance
Digital certificates are a robust authentication technique, but without policy controls, even a hacked or outdated device could still use a valid credential. By integrating policy-driven certificate issuance with device compliance checks in Jamf Pro and Microsoft Intune, organizations may implement a dynamic trust architecture that adheres to Zero Trust principles.
Why Policy-Driven Issuance Matters
Certificates should only be issued to devices that adhere to corporate security standards. Best practices involve modifying certificate issuing based on:
- User role or group membership: Financial or engineering groups may demand greater certificate controls than contractors.
- Device posture: Policies that include checks for FileVault encryption, OS patch level, and Jamf enrollment.
- Ownership model: Certificates for BYOD endpoints are short-lived, whereas corporate-owned devices are long-lived.
- Compliance state: Certificates can be withheld or revoked if a device fails to comply with Intune compliance standards enforced via Jamf’s Cloud Connector.
This ensures that certificates reflect the device’s current status rather than being static “once trusted, always trusted” credentials.
Integration with Jamf and Intune
Jamf Pro’s integration with Microsoft Entra ID and Intune provides compliance with regulations for macOS, iOS, and iPadOS devices. Administrators may set compliance policies in Intune (for example, mandating FileVault or prohibiting obsolete OS versions) and enforce them using Jamf smart/static groups. Jamf then sends device posture data back to Intune, which can prevent non-compliant devices from accessing Microsoft 365 and other conditional access resources. Certificates associated with these compliance checks can be automatically revoked if a device exits the Jamf scope or fails to comply.
Example Policy Scenarios
- FileVault Enforcement: Certificates are only granted for macOS devices with FileVault enabled.
- BYOD vs. Corporate: BYOD users are given short-lived certificates (e.g., 7 days), but corporate-managed devices have longer lifespans (e.g., 1 year).
- Automatic Revocation: Devices unenrolled from Jamf or failing Intune compliance tests will automatically lose their certificates.
- System Integrity Protection (SIP) Monitoring: SIP is enabled on macOS devices to verify that core system files and processes remain protected from tampering.
Building Towards Zero Trust
By incorporating certificate issuance into Jamf + Intune compliance workflows, enterprises can ensure that devices are healthy, compliant, and authorized before accessing resources. This method eliminates reliance on static trust, bridges revocation gaps, and guarantees that certificate-based access remains an active component of the organization’s Zero Trust strategy.
Testing and Validation in Jamf Pro 11
Before deploying workflows on a large scale, ensure that certificate enrollment works correctly. Jamf Pro 11 has various tools and logging features to assist administrators in verifying deployments and enforcing compliance requirements.
Verifying the deployment of the certificate payload
Administrators should verify Jamf Pro logs after deploying a configuration profile, including certificate payloads, to ensure that the payload was received and deployed correctly. Administrators may access certificate data such as the topic, serial number, issuing CA, expiration, and revocation state under Settings > PKI Certificates. Jamf Pro displays the configuration profiles for third-party CAs. Exports to CSV, TXT, or XML enable large-scale study of fleet data.
Testing SCEP vs. ACME Enrollments
Jamf offers the Certificate SDK Sample App for testing certificate procedures.
SCEP Enrollments: These may be confirmed using the “Actual” test type, which sends actual calls to Jamf Pro and the CA to ensure communication is established and secrets are correctly configured.
ACME Enrollments: Administrators may test hardware-based attestation scenarios using Jamf Pro 11’s ACME payload support. Administrators may use the “Simulated” test type in the Sample App to simulate certificate requests, sluggish networks, and error states without requiring a Jamf Pro instance. Logs in the Sample App contain complete information on success, error codes, and certificate issuance behavior.
Validating Compliance Enforcement
Certificate testing is not complete without validating device compliance workflows. In Jamf Cloud-integrated setups, Intune compliance standards (such as FileVault, OS version, and patch levels) may be checked by moving a device into a Jamf smart group and seeing whether certificate issuance or revocation happens as expected. Non-compliant devices should be denied access to conditional-access-protected resources, demonstrating that policy enforcement works correctly.
Conclusion
Modern certificate enrollment in Jamf has advanced well beyond standard SCEP procedures. Organizations benefit from ACME and MDA by improving identity assurance, automating lifecycle management, and providing seamless user experiences. When combined with policy-based issuance and compliance checks, certificates become more than simply a connection facilitator; they also serve as an essential layer of enterprise security. This approach complies with Zero Trust concepts, forcing devices to continually establish their credibility before accessing resources.
SecureW2 extends Jamf’s capabilities with cloud-based PKI services, improved policy enforcement, and real-time revocation logic.
Ready to update your certificate enrollment with Jamf? Contact us today.