Yubikeys are an all-in-one MFA device. In addition to serving as a physical authentication token, they can generate one-time-passwords (OTP) and require users to input a PIN.
It’s quite difficult to enable all of these methods of authentication and have a device that can be securely reset and reconfigured without compromising your vulnerable private keys. To facilitate the key management of Yubikeys, Yubico has created a system of 3 “passwords” for each device.
Yubikey PIN Configuration
Yubikey PINs are different from most other PINs you’ll meet because they aren’t limited to numbers. They’re actually byte-limited to 8 bytes per PIN, which means that you can use any 8 ASCII characters (upper and lower case letters, numbers, and non-alphanumeric characters too).
The default PIN length requirement is just 6 characters of your choice, there are no restrictions. The default PIN is configured to “123456”, which sounds like something an idiot would put on their luggage.
The PIN is used for most actions on the Yubikey, such as authenticating to a service or creating a digital signature. If entered incorrectly 3 consecutive times, the Yubikey will lock.
Yubikey PUK (Personal Unlocking Key) Configuration
PUKs are a backup mechanism for recovering and resetting a locked Yubikey. After the PIN has been entered incorrectly 3 times, you’ll have 3 opportunities to put in the correct PUK. If the user fails that too, then the device will be permanently locked and will need to be restored to factory conditions before it can be used again.
PUKs inherit the same complexity requirements as the PIN, but their default setting is a much more secure “12345678”. Note that setting a PUK is optional.
Yubikey Management Key
The Management Key is a 24-byte key specifically for use with the PIV Manager tool – the Yubico tool that allows you to customize your Yubikey. The PIV Manager tool will generate one on request, or you can opt to simply use your PIN in place of a dedicated Management Key. The tool will derive a full 24-byte Management Key using your PIN as a seed.
You shouldn’t use your PIN as the Management Key for a few reasons:
- If the Management Key is derived from the PIN, it changes whenever your PIN does (such as if you get locked out). It effectively removes your backup recovery option because…
- Using the PIN as a Management Key disables the PUK for technical reasons.
- Since the PIV Manager derives the Management Key from the PIN, if your PIN is changed by any tool that isn’t the PIV Management tool, it fails to correctly derive the new Management Key.
Configure Custom Yubikey PIN/PUK Requirements
That third point is important because it precludes you from managing Yubikeys at scale, which is a big detriment for organizations that want to deploy and manage security keys in a timely and efficient manner.
Although the primary role of a security key is the physical touch component, your security perimeter is only as strong as the weakest link – that’s why we advocate for strong PINs on Yubikeys. Certainly the default PIN and PUK need to be changed before the key reaches the end user, otherwise half the keys in an organization would be protected by the default PINs.
You can use the PIV Manager tool to set new PINs and PUKs and Manager Keys, as well as to enforce complexity requirements, but the tool is clunky to say the least. You have to manually configure each Yubikey in a command line interface when using the native PIV Manager tool.
Enterprise Yubikey Management Solutions
Manual Yubikey configuration is simply not feasible for any organization that has more than a dozen or so Yubikeys. Fortunately, we have a solution for scaling Yubikey management.
SecureW2 is an official Yubico Partner, and with their help, we have developed solutions to integrate Yubikeys into a WPA2-Enterprise network environment for 802.1x authentication via x.509 digital certificates. Our tech allows you to use Yubikeys for more than authenticating to web apps – you can use them for desktop login, Wi-Fi, VPN, and more.
To accomplish this, we integrate Yubikeys into a cloud PKI and enroll the security keys for the same device certificates you would use for regular EAP-TLS authentication. Since Yubikeys already come equipped with certificate slots and attestation, it’s simply a matter of reconfiguring the key with your own certificate authority and deploying new certificates.
Our enterprise Yubikey management solution allows you to configure the keys for foolproof self-enrollment by the end user, guiding them through the process of setting a PIN and PUK according to the complexity requirements that you can prescribe on an organizational-level. Don’t believe us? Here’s a .gif of the process:
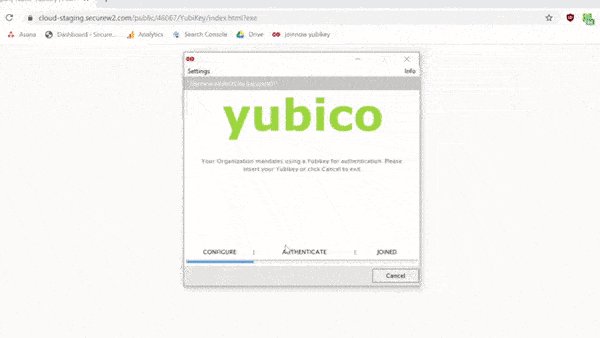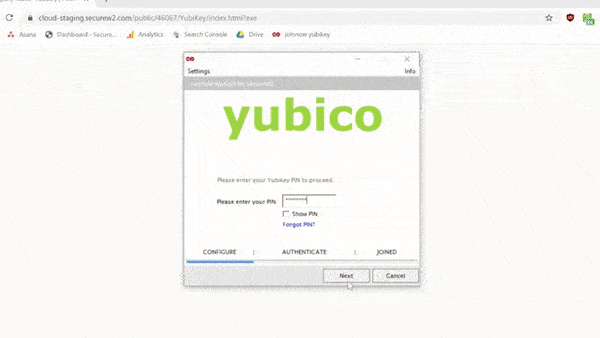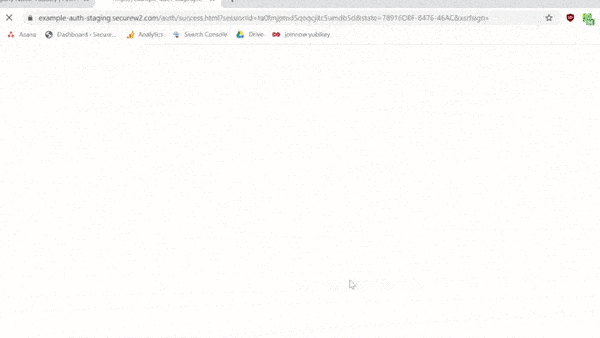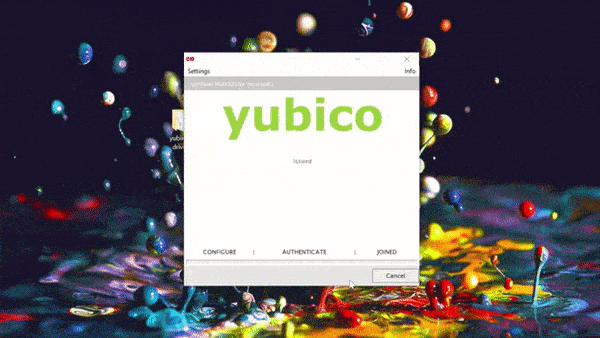
Your Yubikeys can do so much more. Unlock the full potential of security keys with the SecureW2 Smart Card Management System. We have affordable options for organizations of every size. Check our prices here.
