Key Points
- TLS (Transport Layer Security) is a cryptographic protocol that protects data in transit by encrypting communications between a client and server, ensuring data privacy and integrity.
- TLS operates by authenticating the server using digital certificates and establishing an encrypted session through a handshake process. This guarantees the confidentiality of exchanged information and verifies the identities of both parties.
- Organizations can implement TLS encryption seamlessly using a Managed PKI solution like SecureW2’s Cloud RADIUS, which supports certificate-based EAP-TLS authentication for enhanced network security and real-time policy enforcement.
Transport Layer Security is a protocol that ensures privacy and data integrity between two communicating applications. It’s the most widely deployed security protocol used today and is incorporated into web browsers and other applications that require data to be securely exchanged over a network.
Organizations around the world have learned to utilize TLS encryption for increased network security. This article outlines TLS encryption, how it works, the role of keys and finally, compares it with SSL. We’ll also discuss how your organization can use TLS.
What is TLS and Why is it Important?
Transport Layer Security (TLS) stands as a crucial security protocol widely employed to establish secure communication between clients and servers on the internet, facilitating interactions like those between web pages and browsers. Serving a pivotal role, TLS ensures the encryption of data in transit while verifying the identities of both parties involved, assuring exclusive access to the intended recipient.
Designed with three specific functions in mind for comprehensive internet security, TLS offers flexibility in implementation, although leveraging all three features is highly recommended:
- Encryption: Safeguarding data from unauthorized access, ensuring privacy.
- Authentication: Rigorously verifying the identities of both the intended sender and recipient.
- Data Integrity: Shielding against tampering, guaranteeing data arrives unchanged to the intended recipient.
TLS seamlessly integrates these functions by encrypting data to shield it from the public eye, concurrently validating the identities of the sender and intended recipient. Its primary application is in creating secure environments for web browsing, email communications, and various data transfers. Websites, in particular, utilize TLS to secure all communications, employing TLS certificates to both confirm the site’s legitimacy and fortify transmitted data through robust encryption.
How Does TLS Work?
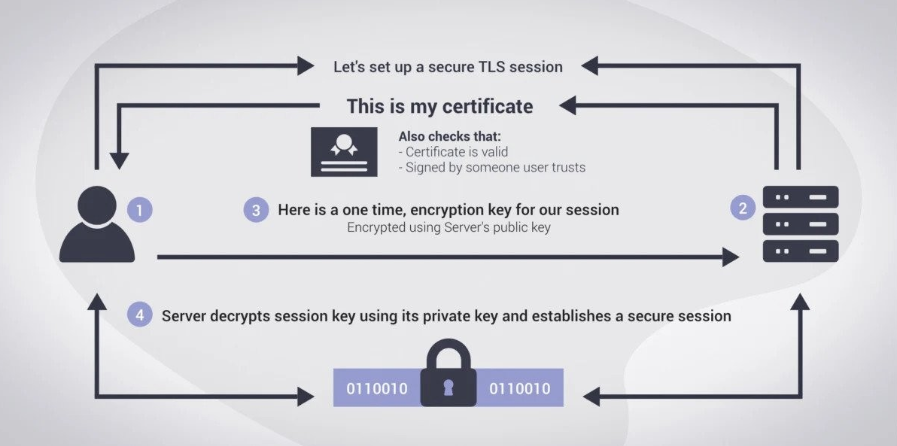
When you use the internet, your data traverses through various computer networks before reaching the intended destination. During this process, it’s vital to ensure your data doesn’t fall into the wrong hands. One of the reliable techniques to prevent this is the use of TLS encryption. Here, the TLS protocol negotiates encryption for the connections, and the server’s identity is authenticated using a digital signature in the TLS certificate. The TLS authentication process involves several steps:
Step 1: Client Hello
The TLS handshake begins with the client sending a “Client Hello” message to the server, indicating its intention to establish a secure connection and listing supported cryptographic algorithms.
Step 2: Server Hello
Upon receiving the “Client Hello,” the server responds with a “Server Hello” message, selecting the strongest cryptographic algorithms from the client’s list and providing its digital certificate, which includes its public key.
Step 3: Certificate Verification
The client verifies the authenticity of the server’s digital certificate. This involves checking if the certificate is signed by a trusted Certificate Authority (CA) and if it has not expired or been revoked. If the verification fails, the connection is terminated to prevent potential security risks.
Step 4: Key Exchange
Once the server’s identity is verified, the client generates a random session key and encrypts it using the server’s public key obtained from the digital certificate. This session key will be used for symmetric encryption during the data transmission.
Step 5: Server Key Exchange (Optional)
In some cases, the server may also send additional information, such as its own public key or parameters required for key exchange, depending on the chosen encryption algorithms and the server’s configuration.
By following this authentication process, TLS ensures not only the confidentiality and integrity of data but also verifies the identity of the communicating parties, thereby preventing unauthorized access and man-in-the-middle attacks.
What is a TLS certificate?
A TLS certificate is a digital document that plays a fundamental role in securing online communication. It is issued by a trusted third party called a Certificate Authority (CA) and serves to verify the authenticity of a website or server. TLS certificates enable encrypted connections between a user’s web browser and a server, ensuring the confidentiality and integrity of data during transmission.
The certificate contains key information, including the domain name of the website it is associated with, the public key of the server, information about the CA that issued the certificate, and the digital signature of the certificate to ensure its validity. When a user connects to a website secured with TLS, the browser checks the certificate to confirm the legitimacy of the site and establish a secure connection.
TLS certificates are crucial for preventing malicious actors from impersonating websites and conducting man-in-the-middle attacks. They are a foundational component of the TLS protocol, contributing to the overall security of online communication by providing a trusted means of verifying the identity of websites and servers.
How Does SSL/TLS Encryption Work?
SSL/TLS uses both symmetric and asymmetric encryption to protect the confidentiality and integrity of data-in-transit. Asymmetric encryption is used to establish a secure session between a client and a server, and symmetric encryption is used to exchange data within the secured session.
What is the Difference Between Secure Sockets Layer (SSL) and TLS?
Secure Sockets Layer (SSL) and TLS are both protocols used to protect sensitive data during electronic dissemination across the internet. SSL is the predecessor of TLS. When SSL v3.0 was found to be vulnerable to specific cryptographic attacks, TLS v1.0 was introduced as a replacement.
Is TLS Safer than SSL?
Yes, Transport Layer Security is generally considered safer than SSL. TLS is an evolved and more secure version of SSL, designed to address vulnerabilities and shortcomings identified in earlier SSL versions. While the terms are often used interchangeably, TLS has become the industry standard for securing internet communication.
One of the main reasons TLS is considered safer is that it has undergone significant improvements in cryptographic algorithms and protocols, providing stronger security measures. TLS offers better protection against various security threats, including attacks such as BEAST and POODLE that were identified in SSL protocols.
Additionally, TLS supports more secure cipher suites and has mechanisms for forward secrecy, which means that even if the long-term private keys are compromised, past communications remain secure. As a result, most modern web browsers and servers have transitioned to using TLS for encrypted connections.
TLS in the Transport Layer Security System
Transport Layer Security ensures the security of your data from one point to another through encryption. It uses the session keys to encrypt and decrypt the transmitted data, and the master secret is used to generate the session key.
What Do SSL and TLS Do?
SSL and TLS are cryptographic protocols designed to provide a secure connection between a client and a server over the internet. They work to protect data integrity and privacy, converting readable data into an indecipherable encrypted code during transmission. Once the intended recipient receives it, they can decrypt it back into its original form. For this process, both SSL and TLS use a combination of symmetric and asymmetric cryptography.
The TLS Handshake Process
The initiation of a TLS connection begins with the TLS handshake, an automated process that occurs before the actual data is transferred between the server and the browser. This handshake forms a secure connection to ensure the confidentiality and integrity of data. The exact steps within a TLS handshake will vary depending upon the kind of key exchange algorithm used and the cipher suites supported by both sides. The RSA key exchange algorithm, while now considered not secure, was used in versions of TLS before 1.3.
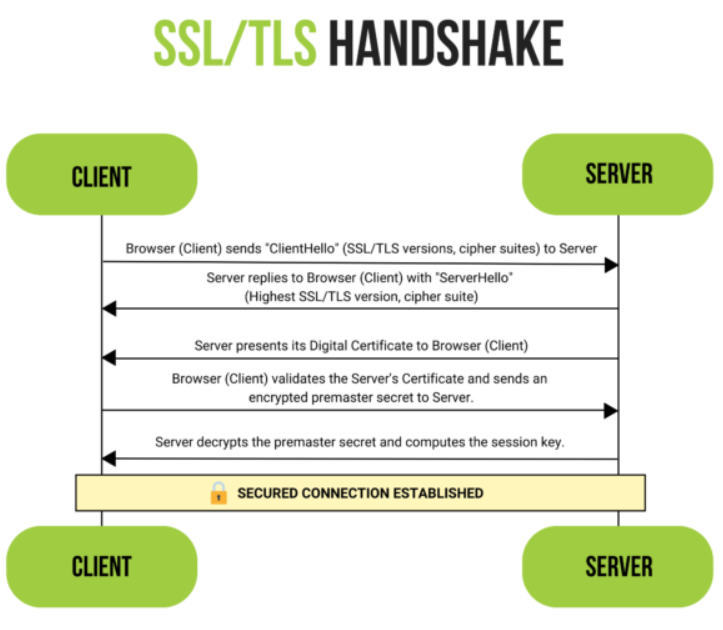
During the handshake, the server and client negotiate aspects of the secure connection, like the version of TLS they will use, the cipher suite, and other configurations. The server sends its SSL/TLS certificate containing its public key. The client verifies this certificate with the certificate authority (CA) and then uses the server’s public key to encrypt a pre-master secret and sends it to the server. The server decrypts the pre-master secret using its private key, and both sides then use this pre-master secret to generate the same session key for encrypting and decrypting data.
Does TLS Use a 3-Way Handshake?
Though it may sound similar, a 3-way handshake differs from the TLS handshake. In a 3-way handshake, used in establishing a TCP connection, the two parties exchange SYN (synchronization) and ACK (acknowledgment) packets before actual data communication begins. This process is not encrypted and hence can be vulnerable to certain attacks.
What is the Difference Between a TCP Handshake and a TLS Handshake?
Essentially, the TCP handshake sets up the connection between the client and the server, while the TLS handshake secures it. The TCP handshake ensures that both parties are ready for communication and that packets sent are received. The TLS handshake then provides encryption for those communications.
The Role of Keys in TLS Encryption
When it comes to TLS encryption, the role of keys (private key and session keys) is paramount in ensuring the confidentiality and integrity of data during transmission. Let’s look at the role of the private key and session keys in TLS encryption.
Private Key
In TLS encryption, a private key is part of a key pair system used for secure communication. During the TLS handshake, entities exchange public keys, enabling the derivation of a shared secret for encryption. The private key, kept confidential, decrypts data encrypted with the corresponding public key. This process ensures secure communication over the Internet. A digital certificate, signed by Certificate Authorities, associates public keys with trusted entities. Protection of the private key is crucial to prevent unauthorized access and maintain the integrity of the encryption process.
Session Key
In TLS encryption, session keys play a pivotal role in securing the actual data exchange between a client and a server. Once the TLS handshake establishes a shared secret derived from the public key and the private key, a session key is generated. The session key is symmetric, meaning the same key is used for both encryption and decryption of the transmitted data, providing efficiency in processing. Unlike the public-private key pair used during the handshake, session keys are ephemeral and unique to each session. Their temporary nature enhances security by limiting the exposure of a key to potential attacks. A session key is used exclusively for the duration of a session, reducing the risk associated with long-term key usage. This aspect of TLS ensures a dynamic and secure communication environment by constantly refreshing and regenerating a session key for each new connection.
What is TLS 1.2?
TLS 1.2, the third major iteration of the TLS protocol introduced in August 2008 through RFC 5246, marked a significant advancement over its predecessors. Notable improvements included the adoption of a more secure hash function, SHA-256, along with detailed specifications for cipher suites and the pseudorandom function (PRF). TLS 1.2 offered enhanced flexibility, enabling sophisticated key derivation, and introduced authenticated encryption ciphers that seamlessly combined encryption and data integrity verification in a single operation. These features collectively fortified the security and versatility of the TLS protocol suite, establishing it as a robust framework for secure online communication.
TLS 1.3: the Latest TLS Version
In August 2018, the Internet Engineering Task Force (IETF) unveiled TLS 1.3 (RFC 8446), the latest evolution of the TLS protocol. Purposefully designed for heightened efficiency and security, TLS 1.3 addressed vulnerabilities identified in previous versions. This iteration streamlined the TLS handshake process, requiring only a single round trip for the client to transmit application data to the server, significantly reducing connection times. Furthermore, TLS 1.3 abandoned support for older, insecure cryptographic features, resulting in a faster, more secure protocol compared to its predecessors.
What were the Key Upgrades in TLS 1.3 from TLS 1.2?
A pivotal distinction between TLS 1.2 and TLS 1.3 lies in the optimization of the TLS handshake process. Unlike TLS 1.2, which necessitates two complete round trips before the client can send application data, TLS 1.3 achieves the same with just one round trip, markedly enhancing connection speed. Moreover, TLS 1.3 enhances overall security by eliminating support for outdated cryptographic features prone to vulnerabilities. Its swifter and more secure handshake process, combined with a judicious abandonment of insecure elements, positions TLS 1.3 as a robust and modernized protocol, setting a new standard for secure online communication.
Implementing TLS Encryption: SSL/TLS Enabling
Enabling SSL/TLS is specific to the software and operating system you are using. Generally, it involves acquiring an SSL/TLS certificate from a certificate authority, installing it on your server, and configuring your server to use SSL/TLS for connections. Additionally, it’s important to ensure that you’re using a version of TLS that is secure and not vulnerable to attacks.
Is SSL/TLS Layer 4 or Layer 7?
SSL/TLS operates at both Layer 4 (the Transport Layer) and Layer 7 (the Application Layer) in the OSI model. It provides encryption services more closely aligned with Layer 4 but also includes application-level knowledge that classifies it as Layer 7.
TLS Encryption Use Cases
TLS Encryption is crucial for organizations and their clients because it protects them from data breaches and additional cyber attacks, like the infamous man-in-the-middle attack. HTTPS is an implementation of the TLS protocol and is used by all websites. HTTPS shows that the website is protected by a TLS/SSL certificate. Conducting business online is a standard in today’s environment, meaning things like passwords, social security numbers, debit/credit card information is all online and at risk of being stolen. TLS ensures your data will stay safe from outside threats and reach its intended destination.
Organizations can configure the TLS protocol with digital certificates and enable EAP-TLS, the most secure IEEE 802.1X protocol that leverages certificates and the TLS protocol. EAP-TLS combines the TLS protocol with the Extensible Authentication Protocol (EAP), virtually eliminating over-the-air credential theft. Network administrators can configure the highest level of network security with WPA2-Enterprise. WPA2-Enterprise can work with other 802.1X authentication protocols, but EAP-TLS is the only one that leverages the full capabilities of digital certificates.
Implementing TLS with a PKI
Network administrators can use EAP-TLS authentication with a private managed PKI solution, such as SecureW2. EAP-TLS is the only certificate-based authentication protocol, and SecureW2’s PKI allows admins to easily create and provision EAP-TLS certificates to every network user, device, and server. With SecureW2, a user will connect to the secure network and EAP-TLS confirms the identity of both the user and server in an EAP tunnel that prevents outsiders from infiltrating the connection.
Our PKI also comes with Cloud RADIUS, an improved, dynamic version of the RADIUS protocol. RADIUS is imperative for 802.1X authentication as it can be configured as the server to authenticate clients and authorize them for web access. Network admins can configure Cloud RADIUS with their organizations user policies and permissions. When a user is authenticated, Cloud RADIUS is the only certificate-based solution that can directly reference the organization’s directory and look up policies and permission ascribed to that user and determine access levels at the moment of authentication.
Implementing a PKI for your environment can be a difficult and expensive process, unless you choose a turnkey Managed PKI solution that integrates with all major vendors and can be set up in a matter of hours instead of weeks. Plus, our PKI comes at a much more affordable price than most PKI solutions.