Key Points
- VPNs are essential for remote work by providing encryption but are increasingly targeted by cybercriminals exploiting weak password-based authentication.
- End-to-end encryption is critical; without it, data can be intercepted at intermediate points—even services like Zoom may falsely claim full E2EE when only transport encryption is used.
- Replacing passwords with certificate-based authentication (EAP-TLS) for VPN access eliminates credential theft risk and simplifies administration for IT teams.
We have never been more connected with others than we are today. The workforce is quickly moving to mobile devices. Remote work has picked up dramatically due to the COVID-19 pandemic, so VPNs are needed more now than ever before. Unfortunately, Cyber Criminals have quickly begun to pray on remote workers who haven’t been configured properly to work remotely securely. In this article we will go over why you need a VPN, how criminals are targeting it, and how you can make sure your VPN security is locked down.
What is a VPN?
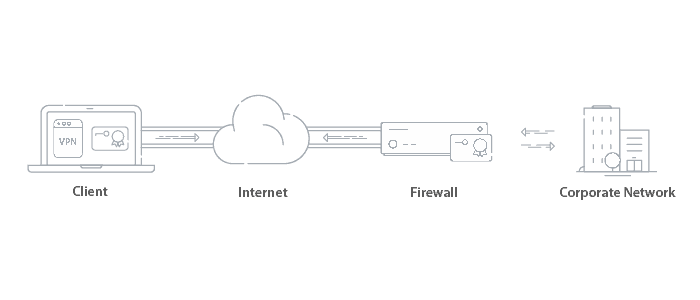
Virtual Private Networks (VPN) are designed to protect your online identity by connecting your device to a secure server rather than your typical ISP. The goal is keeping your private information private. VPNs encrypt web traffic so no one is able to see your data, whether it’s a hacker, corporation, or government.
VPNs were originally created to connect businesses securely online so they’ll be able to login from home. Now that 80% of Americans are required to stay home, VPNs are necessary for remote work.
Companies Need to Encrypt Their Networks for Remote Work
Since the pandemic took over, businesses are needing to find a way for their employees to access the company’s network from home. VPNs provide the most secure way for companies to access their networks and private resources.
Remote access is incredibly convenient but also relies on employees having access to company data at home. There are protocols in place, like Windows Remote Desktop Protocol, that allow users to access their company’s network from anywhere. The concern is that the protocols require the company’s network to be open to the internet, putting it at risk for cyber attacks.
While these protocols are secured by username-password methods, hackers have no trouble nowadays finding passwords and breaching networks. Credential-based networks are not strong enough to handle end-to-end encryption (E2EE).
VPN End-to-End Encryption is Critical for Secure Communication
E2EE is vital for remote work because even if a hacker is able to access the network and steal information, anything they get would be worthless. Without E2EE, your message will be able to be decrypted by a mid-point server, meaning your web traffic and IP is visible. E2EE ensures nobody outside your network can access you or your company’s data.
Zoom’s business has skyrocketed during the pandemic, quickly becoming the premier video conferencing platform for remote workers. The company has touted E2EE on their website and in their whitepapers. However, Zoom’s claims of E2EE may be false. As reported by the Intercept, Zoom actually uses transport encryption instead, meaning that your audio and visual connection will be encrypted, but not from Zoom.
Like Zoom, many services that provide E2EE don’t do enough to protect your networks. The encryption can be bypassed through backdoor attacks or the service might not encrypt backup data.
Configuring Secure VPN Authentication is Imperative
According to ISC SANS instructors, a program that monitors cyber attacks, VPN security should be a top priority since millions of people are working remotely. The CISA recently issued an alert that there will be an increase in malicious cyber actors phishing for VPN credentials. Many employees are now required to use VPNs to work remotely and might not understand them completely. That makes these users vulnerable to phishing attacks, especially ones that capitalize on the coronavirus.
Since VPNs are becoming more popular among business networks, they are increasingly targeted with cyber attacks. Microsoft recently came out warning hospitals attackers are taking advantage of VPN vulnerabilities and breaching networks.
ISC SANS instructors are recommending that companies examine the logs of their VPN authentications to ensure only authorized users have access, which is a monotonous task.
Luckily, digital certificates can provide secure authentication for VPNs, meaning VPNs stay protracted and IT admins don’t have to sift through all those logs. Certificates eliminate the need for password-based authentication because passwords just aren’t secure enough for networks anymore. Just like E2EE, certificates encrypt private data so a hacker wouldn’t be able to do anything if they get a hold of the certificate.
Secure Certificate-Encrypted VPN Authentication
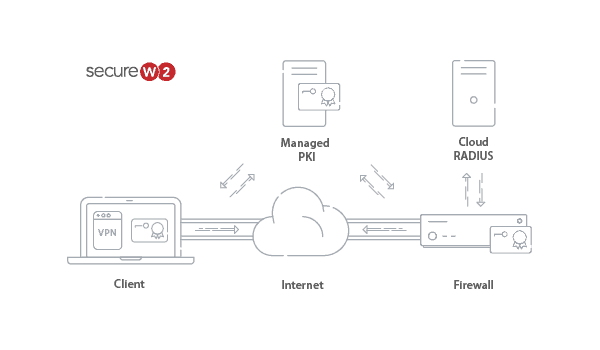
While certificates can prevent the rampant amount of credential theft that is being targeted against VPN users, many are unclear about how to implement them. One of the main reasons is that Public Key Infrastructures, which are required to implement certificates, were once incredibly complex systems to configure and manage. Luckily, there are simple managed PKI solutions in the cloud that make it incredibly simple to replace passwords with certificates for VPN, Wi-Fi, Web Apps… really just about anything.
To use certificates for VPN, you just need to do a couple things.
- Enroll end devices or security keys for Client Certificates
- Upload a Root or Intermediate CA on your Firewall, VPN Gateway, or RADIUS Server
Here’s a guide on how we integrate with a Palo Alto Gateway.
For some, that doesn’t sound like a simple or easy task. However, SecureW2’s PKI Services make it incredibly easy. Our #1 rated certificate enrollment software integrates with any SAML or LDAP directory and allows any end user to get authenticated and easily self-enroll their device for a certificate. We offer clients for every operating system that not only enroll for a certificate, but install them in the proper key store and ensure their private keys are not exportable from the device. They can also install certificates on to PIV-Backed Security Keys and attest to the location of private key generation, offering incredibly high assurance levels for access policies. Lastly, we offer a host of Gateway APIs to auto-enroll Managed Devices or devices that are in manufacturing for client certificates.
SecureW2 also makes it really easy to generate custom Root and Intermediate CA’s that can be uploaded to your Firewall/Gateway/RADIUS. You can also easily integrate Cloud RADIUS with your Gateway or Firewall to ensure strong authentication and implement identity-driven policies to further increase network security. Want to learn more about our solutions? Contact us today and we can get you setup with everything you need to make sure you and your users won’t fall victim to attacks when authenticating to their VPN.