As cloud-based solutions are gaining popularity, many organizations are having trouble transitioning to their on-prem servers. To help alleviate some stress, Microsoft created Azure AD (Microsoft Entra ID) to aid clients in moving their AD instance to the cloud. However, Azure AD is limited compared to AD when it comes to support for VPN and other key network features your organization might find necessary. Luckily, if you are using Azure as your SAML provider, you can easily set up a network equipped with Cloud RADIUS using SecureW2.
Even as quarantine protocols worldwide relax, the demand for VPN remains 22% higher than the demand before the pandemic started. Cloud RADIUS is the only RADIUS Server that comes with an industry-exclusive Dynamic Policy Engine that integrates natively with Azure and Intune and empowers organizations with certificate-based authentication for ultra-secure Wi-Fi and VPN authentication. Our RADIUS supports token-based VPN and can create and configure devices with VPN network profiles, read from one of our customers how easy it was to switch to certificates.
What Is VPN?
Virtual Private Networks (VPN) are designed to protect your online identity by connecting your device to a secure server rather than your typical ISP. VPNs encrypt web traffic so no one is able to see your data, whether it’s a hacker, corporation, or government.
VPNs were originally created to connect people working from home to their organization’s data online. Now that 80% of American’s are required to work from home, VPNs are the best way to make that possible.
How To Use Azure AD (Microsoft Entra ID) for 802.1x Authentication
SecureW2’s PKI Services allow certificates to be installed, while a client certificate can simultaneously be enrolled and configured for VPN or Web-Application Authentication
Digital certificates can provide secure authentication for VPNs, meaning VPNs stay protected and IT admins don’t have to be bogged down by looking through all the logs. Certificates encrypt private data so a hacker wouldn’t be able to do anything even on the off chance they get a hold of the certificate.
Below, we’ll outline how you can set up Azure as an SSO for Certificate Enrollment and 802.1x Onboarding, so your end users can easily self-service themselves for certificate-hardened 802.1x with their Azure credentials.
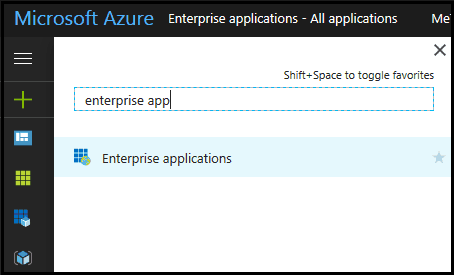
Creating a SAML Application in Azure for 802.1x Enrollment
To create a SAML application in Microsoft Azure:
- From your Microsoft Azure Portal, use the search feature to go to Enterprise applications.
- In the main panel, click New application.
In the Add an application panel, under Add from the gallery, enter ‘SecureW2‘ in the search field.
-
- If the SecureW2 JoinNow Connector application appears:
- Select it.
- In the Add your own application panel, click Add
- If the SecureW2 JoinNow Connector application does not appear:
- Click Non-gallery application.
- In the Add your own application panel, for Name, enter a name.
- Click Add
- If the SecureW2 JoinNow Connector application appears:
Enrolling for an EAP-TLS Certificate with Azure AD
We’ve seen some Azure customers using credential-based authentication using the EAP-TTLS/PAP protocol. We strongly recommend clients against this as it sends credentials in cleartext and puts organizations at serious risk for over-the-air credential theft.
You can get rid of the security threats that come from password authentication through the use of secure EAP-TLS certificates. They can eliminate over-the-air credential theft because certificates are nearly impossible to decrypt. They also eliminate the hassle of passwords and allow for easy migration to the cloud.
To enroll EAP-TLS certificates using SecureW2:
- Set up CA’s in SW2 Management Portal
- CA’s serve as the central authority for certificates and as the hub where admins can determine what roles and policies will apply to their network.
- Add Azure as IDP in SecureW2
- Azure can be configured as the IDP in SecureW2’s management portal.
- Go to Azure Management Portal to Configure the SAML IDP
- Once complete, the RADIUS server will be able to authenticate devices against Azure AD.
- Configure Attribute Mapping
- Admins can map attributes to certificates so they’ll have an easier time seeing who’s on the network.
- Configure network policies to be distributed
- Once devices are properly configured, they can start requesting certificates.
Certificate-Encrypted VPN Authentication With Azure
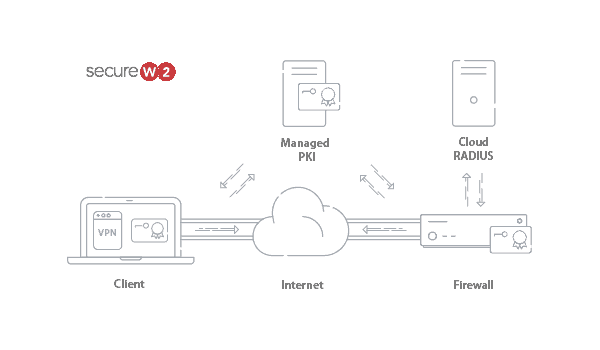
With both Azure AD and SecureW2 configured for certificate authentication, the last step is to upload a Root or Intermediate CA on your Firewall, VPN Gateway, or RADIUS Server. SecureW2’s PKI Services makes setting up a certificate-backed VPN incredibly easy. Our #1 rated certificate enrollment software integrates with any SAML or LDAP directory and allows any end-user to get authenticated and easily self-enroll their device for a certificate.
SecureW2 also offers a host of Gateway APIs to auto-enroll Managed Devices or devices that are in manufacturing for client certificates. Check out our Azure VPN solutions page to see how to equip yourself with a VPN that has the highest level of security possible.