The standard method of thinking about network security is long overdue for an update. The usual “perimeter protection” approach consists of defining, and then controlling, a virtual boundary to make it airtight against the outside. This introduces a fallacy; the outside is considered hostile, while the interior is considered trusted.
This method can be compared to a castle border wall protecting against invaders.
Consider the narrative in which residents of the castle (reasonably upset at the antiquated form of government) plan to assassinate the king. The border wall immediately becomes obsolete as the conspirators are already inside. It’s fair to say that the king made the wrong decision in trusting his walls.
While it’s not exactly fair to compare employees to murderous villagers, the truth is 20% of security breaches are caused by employee negligence. This analogy draws parallels to the philosophy behind a Zero Trust network. In a Zero Trust network, all network traffic is untrusted, including and especially internal traffic.
SecureW2’s turnkey Cloud PKI and RADIUS services are an optimal zero trust solution for Azure AD because they provide the cryptographic infrastructure required to verify the identity behind every network connection and properly create Zero Trust access policies. Just see how easy it was for one of our customers to configure SecureW2 PKI.
So, how exactly can you implement Zero Trust policies in Azure AD? In this article, we’ll answer that question.
Using Azure AD(Microsoft Entra ID) Conditional Access for Authentication
Managing and verifying identities is the first step in protecting your environment. Provisioning user identities through Azure AD (Microsoft Entra ID), and connecting your on-premises Active Directory service if necessary, allows you to centralize identities for each user in order to then be able to establish policies based on devices, groups, and applications.
The more individuals with access to an element of a network the less secure that network becomes. If a locksmith prints a key to your home and distributes the key to everyone they know, the likelihood of that key falling into the wrong hands increases exponentially.
Azure AD’s Conditional Access aims to tackle this problem by allowing individuals, groups, or devices to be sorted into different access categories depending on configurable attributes. This level of granular policy enforcement ensures users are only given access to things they need access to.
Conditional access in Azure AD allows enforcing security policies that are triggered automatically when certain conditions are met. You can block access if the context data suggests that the user has been compromised, or if it is very unlikely that the user should log in under their specific conditions. You can apply additional authentication requirements when the system detects a risk based on connection conditions.
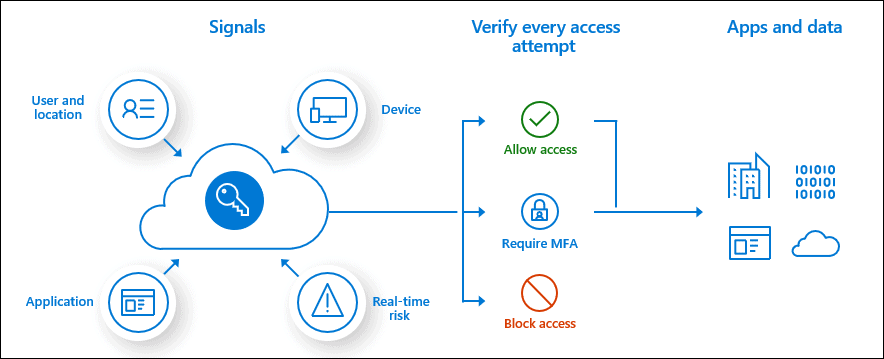
Some common conditions that Azure AD can take into account when making a policy decision include:
- User membership or group membership
- Policies can be targeted to specific users and groups, giving administrators more precise control over access.
- IP location information
- Organizations can create trusted IP address ranges that can be used to make policy decisions.
- Administrators can specify IP address ranges for entire countries/regions to block or allow traffic from them.
- Apparatus
- Users with devices from specific platforms or marked with a specific status can be used when enforcing conditional access policies.
For a complete list of conditions, you can visit Microsoft’s website.
Azure AD + SecureW2 For A Stronger Zero Trust Environment
Given the frequency of stolen credentials, a truly secure Zero Trust network shouldn’t rely on them at all. That’s where 802.1X comes in.
An 802.1X network is different from home networks in one major way; it has an authentication server called a RADIUS Server. RADIUS is a standard protocol to accept authentication requests and to process those requests. If you use certificate-based Wi-Fi authentication (EAP-TLS) with Azure AD, you can set up Azure AD with any RADIUS server. Digital X.509 certificates should be mandatory for zero trust network authentication because they are inextricably tied to the identity of a user or device, allowing you to positively verify the client with much greater accuracy than credentials.
SecureW2 provides both an easy-to-use Managed PKI and a Cloud RADIUS, giving organizations everything they need to set up 802.1X on their network. Along with our Cloud RADIUS, SecureW2 grants access to industry-first dynamic technology that allows Cloud RADIUS to talk to any IDP to dynamically update your users and policies. You can easily use the dynamic functionality with the Azure AD directory for user lookup to assist with access control in your zero trust environment.
Using our Cloud RADIUS also significantly reduces the costs associated with an on-prem RADIUS server by requiring significantly less time and money needed for maintenance and general upkeep.
SecureW2 Can Make Azure Integration Easy
Combining 802.1X policies with a Zero Trust framework is a surefire way to ensure safety for your network. With SecureW2 you can have your secure network set up in a matter of hours and have a support team ready to assist you with any of your questions. You can set up MFA protocols, access a dynamic policy engine, and still use Azure AD’s Conditional Access for airtight security.
We have affordable solutions for organizations of all sizes, check out how we work with Azure on our solutions page here.


