Key Points
- The SolarWinds compromise exploited trusted software updates, inserting malicious code into thousands of enterprise networks.
- Supply-chain attacks like SolarWinds highlight how fragile trust in third-party software and certificates can undermine security.
- Strong certificate management and Zero Trust principles help detect compromised identities and prevent attackers from exploiting blind trust.
Earlier this month, SolarWinds was breached by (who experts theorize to be) the hacker Russian organization, Cozy Bear. This attack has left 18,000 organizations potentially compromised with 250 of which were confirmed to have data stolen; many were Fortune 500 companies as well as a number of US government agencies.
According to reports from Reuters, The Washington Post and The Wall Street Journal, the hack affected the US Homeland Security, State, Commerce and Treasury Departments, as well as the National Institutes of Health. Politico reported on Thursday that nuclear programs run by the US Department of Energy and the National Nuclear Security Administration were also targeted. However, it is not exactly known what information was compromised.
The attack on SolarWinds Orion is an example of how important cybersecurity is going to be in the future of an increasingly technologically dependent world. It’s apparent that the days of espionage from James Bond-like secret agents is over; now governments and organizations need to be aware of the much more real threat of sophisticated computer hackers.
What Is SolarWinds Orion?
SolarWinds was founded in 1999 by former Walmart executive Donald Yonce and his brother, David. SolarWinds Orion is an analytical software that allows IT professionals to monitor, analyze and manage the devices on their network all in one application. Almost all Fortune 500 companies are reported to use SolarWinds products to scan their networks, including major defense contractors such as Boeing, according to the New York Times.
Because of the high number of companies in both the private and public sector that use a SolarWinds product, they were, in hindsight, the perfect target for an attack. But how exactly did such a powerful organization become compromised?
What was the Compromise?
Although there has been some controversy over SolarWinds password to the update server hilariously being “SolarWinds123,” this was not where the compromise occurred, nor was it a compromised user-identity. The attackers compromised the signing certificate server and made changes to it to allow them access to files and get their malware into the update package.
What is a Supply Chain Attack?
The compromise, in essence, was a supply chain attack. A supply chain attack is a cyber attack that moves through the supply chain. The attackers made their move by infiltrating SolarWinds and hiding nefarious code inside the dll file for SolarWinds update package that would go unseen and downloaded by clients.
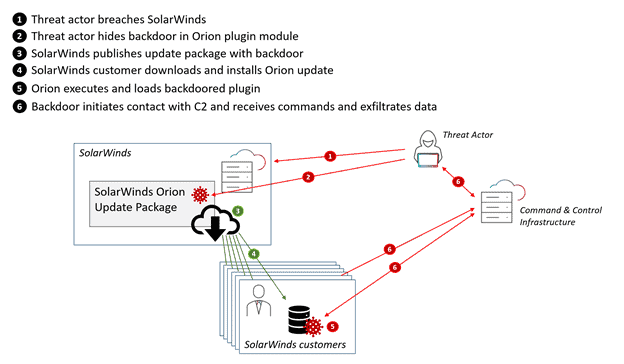
Once the update was downloaded from SolarWinds and onto customers networks, SolarWinds was found to have too many permissions available for admins, which allowed the malware to access sensitive data from their database by using a backdoor.
Supply Chain Attacks are Incredibly Hard to Defend
The core reason why Supply Chain attacks are hard to do is that the hacker is already inside. Historically, organizations focused on keeping potential hackers outside of the network by focusing on a secure perimeter. Today, many organizations have been implementing the philosophy of Zero Trust, and assuming that they’ve already been breached.
In the case of the SolarWinds breach, the malware was hard to detect as the trojan mimicked the actual SolarWinds Orion tool hiding in small bits of xml files to hide from anti-virus programs and extracts information at the same time and being sent out masquerading as analytic data using the backdoor. If a Zero Trust philosophy was implemented here, SolarWinds would have been actively searching for anomalies in their production build on a regular basis.
How Does the Backdoor Work?
The backdoor receives very standard instructions from the C2 server, executes those instructions and sends back the information. A C2 or command-and-control server is a server used by the attacker to maintain communications with the compromised system within a target network. The first step involves creating a connection from the backdoor to the C2 server to report some basic information about the compromised system to be able to receive it’s first commands.
The backdoor then creates a JSON document that can be read by the attacker to the C2 server. If the connection is successful, then an encoded connection that contains commands for the backdoor to execute are sent over. Attackers can run commands like CollectSystemDescription that sends over an array of information that includes sensitive information like Administrator Account SID and System Directory.
How Did this Affect SolarWind Customers?
Users are affected by the SolarWinds breach by having their sensitive information from their networks compromised. The malware is known tohave beenfor around 8-9 months. Once the SolarWinds Orion update package was downloaded and installed, SolarWinds was granted permissions to the network, causing the bad actor to access all the sensitive information on the customers network. Things like emails, financial information, and other classified data can all be presumed to have been compromised.
How To Prevent Supply Chain Attacks
Supply chain attacks, like we saw with SolarWind, seek to damage an organization by targeting the least secure elements within its supply network. These attacks deliberately go after third-party providers to access the networks of those further down the supply chain.
A great strategy is to employ a Zero Trust philosophy, and configure your environment accordingly. Zero trust is a security philosophy that can be boiled down to “never trust, always verify”. In a Zero Trust network, all network traffic is untrusted. This means that security professionals must ensure that all resources are accessed securely, adopt a least privilege strategy, strictly enforce access control, and inspect and log all traffic.
Another strategy to execute comes from securing IoT (Internet of Things) devices. The diverse environment of IoT devices means there is a huge disparity between security levels offered by different IoT manufacturers. Many buyers are not properly evaluating the security of the devices they’re purchasing and it puts their organization at significant risk. Any one of these devices, if left unchecked, can be a potential entry point for a supply chain attack.
Lastly, using a cloud-based environment is a great way to prevent a supply chain attack and keep your network safe. If the SolarWinds compromise has taught us anything, it’s that on-premise environments are not as secure as they were previously thought to be. Hopefully, this comes as a wake up call for organizations and we see more transitions to cloud environments in the future.
Why Cloud-Based Networks Are More Secure
The main reason why cloud-based network infrastructure is more secure than on-premise, is simply economies of scale. Having a secure network is incredibly difficult, and resource intensive. Every major cloud provider has insanely secure facilities, which are much easier and more secure to rely on than our own networks.
In the SolarWinds scenario, customers downloaded the malware through an infected update onto their on-premise environment, SolarWinds had too many permissions and configured their networks such that the attackers had access to all the sensitive data they wanted.
If a SolarWinds customer was using cloud-based network infrastructure, the compromised update package would have been downloaded to the cloud instead of onto their network directly. SolarWinds also would not have the authority to configure their network and gain access to places it shouldn’t be allowed, ostensibly making sure the malware would never have reached the network itself.
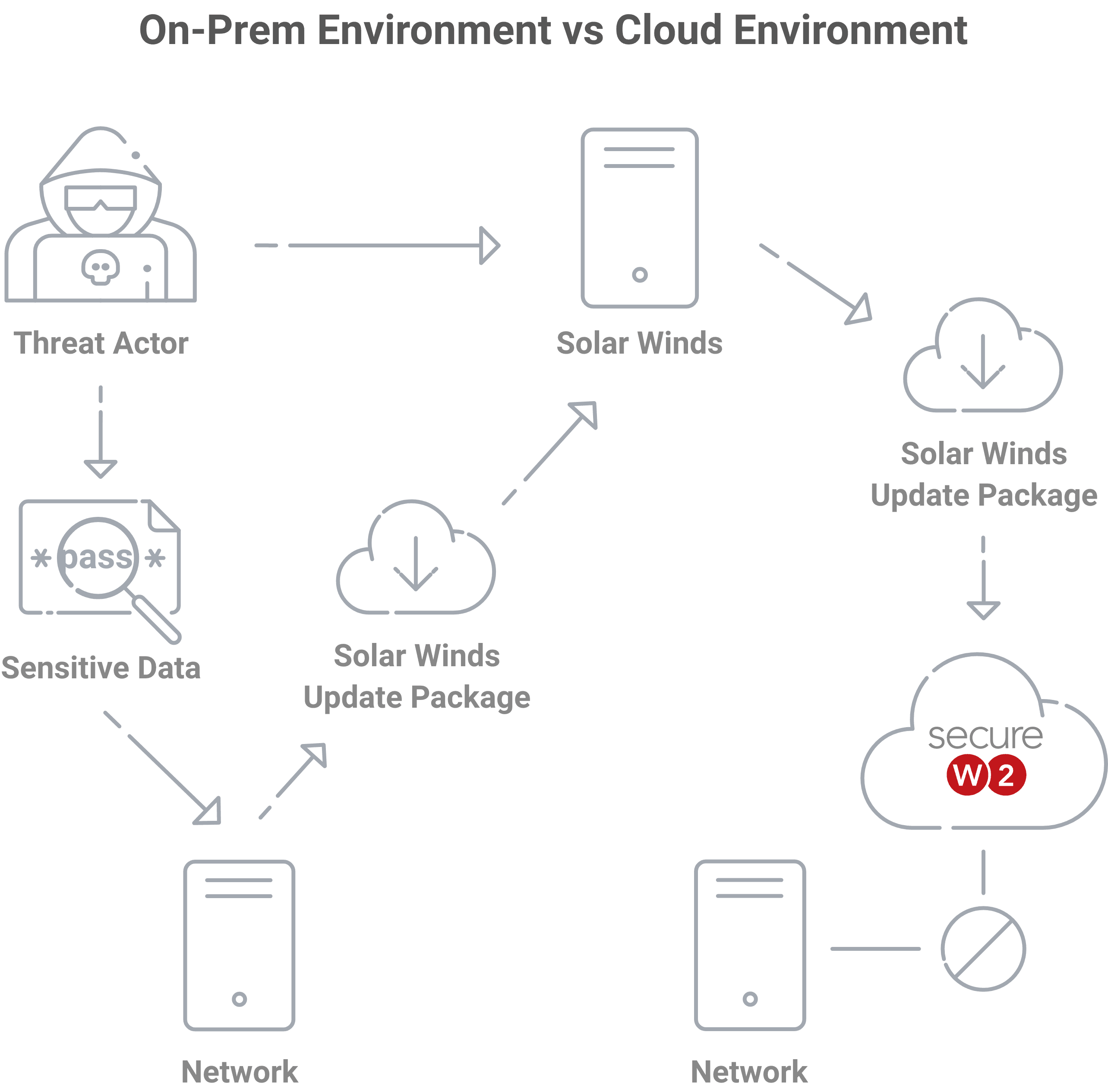
The difference in security can be explained by looking at where data is stored. On-premise software is installed locally, on an organization’s computers and devices, where cloud software is hosted on the vendor’s server and accessed via a web browser.
We at SecureW2 understand the importance of cloud migration and have developed technology that can help any organization successfully create a cloud-based environment. Our #1 rated cloud PKI, Cloud RADIUS and onboarding software can get you started in no time, all with amazing technical support that’s ready to answer any question you may have. Click here to get started on securing your network and keeping your information safe.