Chances are, your work requires you to have logins and passwords for multiple resources. On top of that, you probably have to update your password regularly, ensuring that each new password is compliant with rigorous security standards. Now, repeat this several times or more across the board for each user account you need to access, and it’s easy to see how frustrating maintaining credentials can be.
Smart card authentication seeks to rectify this prevalent issue by providing employees with a physical card that contains identifying information, authenticating users and providing them access. Microsoft admins can configure smart card software using Microsoft Windows Active Directory, but the security of a smart card is improved even further when it’s equipped with a digital x.509 certificate. You can click here to learn more about how switching to certificate-based authentication boosted this SecureW2 customer’s network security.
What is Smart Card PIV Authentication?
Smart card PIV authentication, or smart card logon, is the process of authenticating users by administering smart cards with digital x.509 certificates approved by a trusted Certification Authority (CA). Admins can input user information and policies onto a certificate it will serve as the user’s authentication identity. This certificate can be kept on many devices, but using a smart card to store digital certificates is becoming increasingly common.
Smart Card Certificate-Based Smart Card Authentication
Implementing a PKI is a complicated, labor-intensive, and expensive task that requires a team of trained professionals to manage (and compensation matching their expertise). Luckily, SecureW2 provides a turnkey managed cloud PKI solution that can be set up in under an hour and doesn’t require PKI expertise.
Microsoft admins are able to configure AD with our services and administer digital certificates to all network users containing their specific user credentials. Our certificate onboarding solutions allow smart card users to easily self-configure their cards with a digital certificate that will verify their identities.
SecureW2’s Managed PKI software ties an issued certificate to its respective smart card, unlike passwords that can be shared or stolen. Users can easily self-configure their smart cards using SecureW2’s JoinNow MultiOS onboarding software, simplifying their entire process. By providing identity context and their AD credentials, users can be enrolled for certificates that will verify authentication going forward. Completely passwordless authentication.
Benefits of Certificate-Based Authentication with Smart Cards for Active Directory Users
At the beginning of this post, we briefly touched on the frustration of credential-based authentication. While it may be true that accessing your user account with a username and password is generally simple – even for those with more limited technical skills – the inconveniences of the authentication method quickly add up. Those weaknesses are also the strengths of smart card logon.
For example, consider the hassle of having to repeatedly enter in credentials whenever you are timed out of a user account. Imagine if, rather than having to type in your information over and over again, you could simply plug a smart card into your device instead.
Aside from making logging in faster, a smart card simplifies the process. A smart card makes it possible for a single user to log into various applications and resources without needing to use separate, highly customized credentials for each one. This cuts down on the risk of password mismanagement that often occurs as a result of frustration, such as employees writing down their passwords, sharing passwords, or getting locked out of accounts if they forget a password.
The convenience and security of a smart card are undeniable. However, they get even more secure when you implement digital certificates in tandem with your smart cards. X.509 certificates take you closer to eliminating credentials entirely and can be tied to users in your Active Directory so you have complete control over who can access your network.
Issuing and Revoking Certificates on Smart Cards
In the past, digital certificates have had a reputation for being tricky to implement. Frankly, setting up a Public Key Infrastructure (PKI) and issuing user certificates to each device or smart card on your network does take a degree of technical knowledge and experience. Active Directory Certificate Services (AD CS) was created by Microsoft to allow administrators to oversee the construction of their own in-network PKI.
Keep in mind, however, that there’s a lot that goes into PKI implementation. You’ll need to create a Certification Authority (CA), likely even multiple. You’ll also need to create a Certificate Revocation List (CRL) so that you can ensure that a smart card user who’s no longer active in the company couldn’t log into anything if they accidentally held onto the smart card. There are numerous options of misconfiguration, which can render your in-house PKI ineffective.
The good news is that you don’t necessarily have to do all these things yourself to implement smart card authentication with certificates. Using a Managed PKI (MPKI) like SecureW2’s MPKI, all the complex legwork we described above can be taken care of for you.
Our powerful MPKI is equipped with a full suite of features designed to make managing certificates headache-free. Our CRL can be set up to automatically revoke user certificates on certain dates or after a specific period of time has elapsed, saving you and your IT team time spent on manually updating your own list.
Additionally, our MPKI is cloud-based. It can be accessed from anywhere, so it scales with businesses spread across multiple locations. You don’t have to deal with setting up a PKI in a physical Windows server that is naturally vulnerable to on-site security risks, such as power outages.
Requirements for Smart Card Authentication Deployment
If you’ve made the decision to move to smart cards with Active Directory, you’ll want to ensure you have several components ready. More than a few requirements will need to be met before you can start issuing a smart card to each employee. Here’s what you’ll need to start:
- An Active Directory Windows server
- Smart card-compatible workstations (smart card reader)
- Active Directory Domain Controller(s)
- A PKI
It’s important to note here that your domain controller and workstations will also need to be equipped with properly configured certificates. Assuming you have all these things, you’re ready to deploy smart cards.
Enabling Smart Card Logon Using Active Directory
The process for setting up smart card authentication by configuring AD can be simple. This article by Microsoft covers an in-depth overview of configuring smart card authentication with third-party CAs.
Here’s a quick overview of the configuration process:
- Download the certificate chain from the CA that issues certificates to smart cards.
- Import the CA into SecureW2 and configure AD as the Identity Provider.
- Admins will be able to customize certificates specific to users by inputting their credentials and policies from AD.
- Add the SecureW2 root CA to the trusted roots in AD and configure a Group Policy Object (GPO) to distribute the CA to all domain computers.
- Add SecureW2’s CA to NTauth store in AD.
- The logon process will not work unless the CA issuing the smart card certificate is added to the NTauth store.
- Install certificates onto the domain controllers that will authenticate smart cards.
- Admins can customize and install certificates on both devices and servers, ensuring they only connect with each other because they can verify one another with their certificates.
- Request a smart card certificate from the CA.
- Smart card logon certificates must have a Key Exchange private key for the process to work.
- Integrate smart card software with PKI infrastructure.
- Equip all network smart cards with an appropriate smart card certificate.
From now on, smart cards will automatically access the network.
Smart Card Deployment with the SecureW2 PKI
Implementing smart card certificate-based authentication doesn’t need to be as complicated as one might think. SecureW2 provides you with many of the pieces to the puzzle, so you can roll smart cards out efficiently, unlike just about any other cryptographic service provider out there.
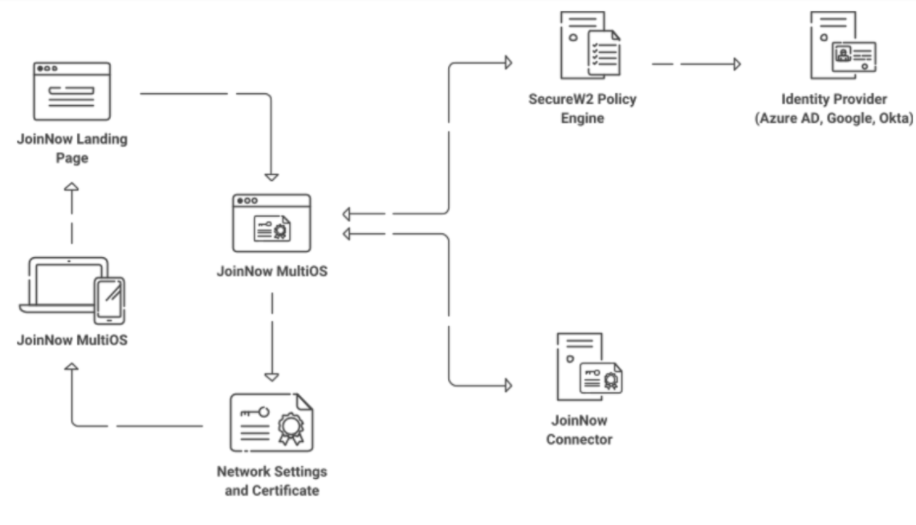
The first tool we offer to our customers is an easy-to-use PKI. Our Cloud-based PKI, as we mentioned above, gives you the powerful components you need to issue, manage, and revoke certificates. It works with our cloud Policy Engine to communicate effectively with your Active Directory and ensure that each smart card belongs to an authorized individual.
To roll out certificates, we have our ultra-simple JoinNow MultiOS application. JoinNow MultiOS makes it possible for each smart card user to enroll themselves for certificates in a matter of seconds. It allows everyone to self-configure their smart card, smoothing the way for all parts of your infrastructure to communicate with one another.
Improving Smart Card Security Further
SecureW2 doesn’t just make certificate-based authentication on smart cards easy – we work hard to make it even more secure. It comes down to how the security keys on smart cards work.
A traditional Yubikey has two main components: the PIN and the Management key. The PIN is what users enter to actively authenticate with, while the the management key is a sort of master key that can be used for administrative tasks like creating new private keys.
In the past, the management key was mathematically linked to the PIN and could be derived from it. The problem with this was that a malicious actor who knew the PIN could then determine what the management key was. Similarly, the reverse is true – if someone knew a Yubikey’s management key, they could calculate what the PIN was.
To protect the PIN and management key, SecureW2 uses a feature where the management key is completely randomized. The PIN is required to unlock the Yubikey itself first, and once the Yubikey is unlocked, we can verify with it what the management key is for any maintenance features.
Make Smart Card Logon Easy with Active Directory and SecureW2
A smart card is a tantalizing proposition for businesses – not to mention end users. Smart card deployment can help eliminate many of the frustrations that come with traditional credentials. No more having to repeatedly enter in your credentials or having to get creative with new passwords for each user account. This undeniable convenience and security get even better when you add digital certificates to the mix.
AD-domain environments can offer far better wireless network security and user experience with certificate-based authentication. Passwords are obsolete and incredibly vulnerable, while certificates eliminate over-the-air credential theft and prevent a user’s credentials from being compromised. By integrating your environments with SecureW2’s PKI and configuring AD as the Identity Provider, admins can input user attributes and policies into certificates and distribute them to end user devices automatically. All this comes at a fraction of the cost on an on-prem solution for AD and smart cards.