Wireless security is crucial now that most sensitive data can be accessed online. It’s imperative for network administrators to dictate who can access the network and how much they’re allowed to access. Organizations need a system that authenticates users to ensure only approved users will be able to access the network.
Active Directory (AD) is the most popular online directory and many organizations use AD credentials to authenticate their users. However, AD is a legacy on-premise service, which doesn’t fit with the rapid industry-wide move to the cloud. Cloud-based services offer more versatility and better security with WPA2-Enterprise and 802.1x authentication.
Migrating AD to the Cloud

AD has cornered the market in online directories, but with the adoption of cloud-base solutions AD’s on-prem infrastructure has become a hindrance for many organizations trying to migrate to the cloud.
According to our sales team, dozens of Windows network administrators are looking to effectively migrate their AD to the cloud and leave their on-premise infrastructure behind. Microsoft does offer Azure AD, which seems like the cloud version of AD, but that’s not necessarily the case. Implementing Azure AD had led to some issues for Windows admins, particularly around network authentication.
A common problem Windows admins face is the fact that Azure AD doesn’t natively support LDAP or Group Policy, unless you sync it up with on-prem AD. Instead of a seamless migration to the cloud, admins will have to create new accounts for all their users, plus create and enforce their access levels. This is a major headache for network admins and can be annoying for end users to need multiple logins.
Securing Your Azure Network
During the Covid-19 pandemic, cyber attacks have seen a 400% increase with the FBI’s Cyber Division reporting an average of 4,000 attacks per day. Now more than ever, it’s imperative for organizations to take network security seriously. Unfortunately, and as many Windows admins are finding out, moving on-premise legacy infrastructure to the cloud seriously impacts network authentication security infrastructure. Below are some simple solutions we’ve seen work really well in the field:
Ditch Credential-based Authentication
Authenticating network users with credentials has been the standard for some time, but as the industry moves towards the cloud, there’s a need for more secure authentication methods.
Passwords can be shared, forgotten, and stolen, making them a weak form of security in an environment where a cyber attack can bankrupt your business. Many Azure and AD networks authenticate users with PEAP-MSCHAPv2, which unfortunately contains a major vulnerability in it’s encryption.
Invest in Certificate-based Authentication
Digital certificates provide a better security standard because they themselves are encrypted entities that can be individually issued to every verified user, serving as an identifier instead of asking the user to create a password.
The only certificate-based authentication protocol is EAP-TLS, which also happens to be the most secure protocol. With EAP-TLS, both the client and server are equipped with certificates and can verify each other with said certificates. Authenticating users based on certificates eliminates over-the-air credential theft and ensures that only verified users will be granted network access. It’s also easy to map user attributes to certificates based on the user’s standing in the organization.
Using Digital Certificates / PKI for Azure AD Network Authentication

Public Key Infrastructures (PKI) come with a multitude of components and can be difficult to deploy, which is why many organizations have steered clear before. Nowadays, there are Managed PKIs that offload the implementation and management to third parties rather than the IT department. Admins don’t need to build their own from scratch with open-source software, instead installing a turnkey PKI solution.
The best way for Azure customers to deploy certificates is with onboarding software for BYODs and Gateway APIs, such as SCEP, for managed devices. It’s really easy by integrating your environment with SecureW2’s PKI and configuring Azure as an IDP.
Many admins have turned away from using certificates because they seemed too difficult to program and issue to every device. That’s only the case if you manually configure devices for certificates. Gateway APIs and onboarding software provide automatic certificate enrollment, lightening the load for IT admins.
In order to deploy certificates, admins need a PKI. Microsoft’s AD CS allows admins to build an on-premise PKI, and it may seem like the obvious choice for Azure customers. Unfortunately, on-prem PKIs are incredibly expensive, labor-intensive, and take months to set up. Azure enterprises have to pay for hardware and software implementation, licensing fees, infrastructure, eventual replacement and much more. Plus, on-prem AD CS PKIs require a team of professionals to manage, meaning Azure enterprises have to dedicate time and resources to either train their IT department or find new employees.
None of this is necessary with a managed PKI service, which has no infrastructure costs because it’s all on the cloud, can be set up in a few hours, and costs a fraction of the price of on-prem PKIs. Enterprises only need one part-time PKI manager, no expensive team of experts required.
With SecureW2’s PKI, admins will be able to map user attributes to digital certificates and administer them to each user. By integrating our PKI with Azure AD, admins will be able to transfer over group policies to the cloud.
Cloud RADIUS and Dynamic Policy Engine for Azure
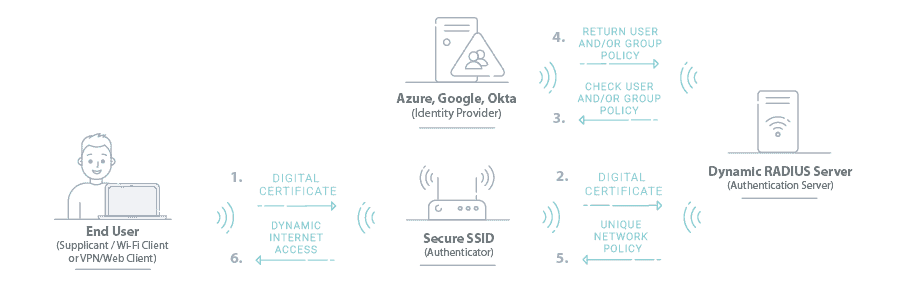
RADIUS is an important part of 802.1x authentication because something needs to serve as the barrier for network entry. Deploying a RADIUS server can vastly improve your network by allowing you to securely authenticate verified users for any application, including Wi-Fi, VPN, web apps, desktop logon, and much more.
Windows admins probably already have a RADIUS setup through an on-prem NPS, but as we’ve discussed, on-premise solutions are not as secure or versatile as cloud-based solutions.
Another option for implementing RADIUS is configuring a virtual FreeRADIUS server. FreeRADIUS is an open-source software program that is the most popular RADIUS server in the world. The reason being that it’s a no-cost solution because there are no license expenses. It’s multithreaded, meaning it can process more than one transaction at a time. The problem is that FreeRADIUS can be incredibly difficult to set up because it’s all up to you to make it work. There are consulting services at reasonable prices to help admins construct a FreeRADIUS server. However, the best solution is one that is turnkey and doesn’t require much setup time.
SecureW2’s PKI comes paired with a Cloud RADIUS solution that can fit into any Azure environment and doesn’t require any forklift upgrades to do so. Cloud RADIUS also comes with Industry’s First Dynamic Policy Engine to natively support Cloud IDPs like Azure, Okta and Google. Cloud RADIUS revolutionizes network security by allowing admins to enforce runtime-level policy decisions at the moment of authentication.
Now, everytime a user is authenticated for network access, admins can enforce network policies in real time. Cloud RADIUS automatically checks user status, what groups they’re in, if they’ve changed departments, and ties them to custom network policies created in SecureW2. All the benefits of historic LDAP authentication, with none of the risks associated with credential-based authentication.
Configure Cloud RADIUS with Azure
Increase your organization’s wireless security by replacing credentials and credential-based authentication with SecureW2’s turnkey PKI and secure certificate-based authentication. With our services, Windows admins can easily implement WPA2-Enterprise, 802.1x, and migrate to the cloud using Azure AD without needing to create new accounts. Our services come at an affordable price so they’re available for businesses of all sizes.