Companies and governments around the world are finding more and more uses for PKI smart cards – especially for identity management. These tiny chips can be found in a multitude of applications ranging from ID cards, credit/debit cards, SIM cards, security keys, and more.
One of the most useful applications of smart cards is in physical security tokens (otherwise known as “security keys”) like the Yubikey. Enterprises can use them to render their networks impervious to over-the-air attacks and totally eliminate phishing.
For the purposes of this article, our references to smart cards will primarily be in regards to security keys. They’re a common choice for organizations that want to deploy supplementary cyber security measures.
What is a PKI Smart Card?
The first thing to clarify is that there is no difference between a smart card and a PKI smart card. Just about every smart card is capable of being integrated with a public key infrastructure (PKI) because they all share the same fundamental component – a secure cryptoprocessor chip.
In fact, smart cards often have the capacity to perform some of the basic functions of a PKI by themselves (creating private keys, attesting digital certificates, etc.). They don’t, however, natively have a convenient graphical user interface or the capacity to be managed at scale.
To overcome that obstacle, organizations use a smart card management system (SCMS) like SecureW2’s. SCMSs offer the ability to integrate smart cards into your PKI so that you can simultaneously configure multiple devices and enroll them for x.509 digital certificates.
Why Use a PKI Smart Card?
The primary purpose of a smart card is identity authentication. The smart card in a credit card confirms that the card is unique and legitimate just as the smart card in a government PIV access card confirms that the bearer is authorized for access to restricted areas.
All authentication methods are greatly strengthened by having multiple factors of authentication (MFA). Simply swiping your debit card isn’t enough; you have to also put in a PIN for a second factor of authentication to make purchases.
Some smart card devices, like the Yubikey security key, can perform multiple factors of authentication themselves. Using private keys or one-time-passwords, requiring physical touch to send the authentication request, and biometric scanning of fingerprints are three different factors of authentication Yubikey is capable of. The device is incredibly effective for preventing unauthorized access.
How to Configure a PKI Smart Card for 802.1x Authentication
There’s no single process that can configure every smart card for 802.1x authentication since there are many manufacturers and many different devices that smart cards can be found in. For this section, we use Yubico’s titular Yubikey as an archetypal example of configuring security keys.
Yubikeys have a predefined list of applications they can integrate with, though they can be coaxed into working with many other services either directly through API or indirectly through integration with a PKI. By loading the Yubikey with x.509 certificates tied to an external identity provider, the Yubikeys can be used to authenticate most any web-based service.
In our capacity as an official Yubico Partner, SecureW2 has engineered a solution that massively enhances the potential integrations of a Yubikey. Instead of having to manually configure each key via command line interface, our software allows you to push automatic configuration profiles to each device for self-enrollment of certificates and integration into our enterprise cloud PKI solution.
Here’s a short video that illustrates how easy it is for the end user to set up their Yubikey. The guided onboarding process prompts the user to set up a PIN and PUK (with customizable complexity requirements).
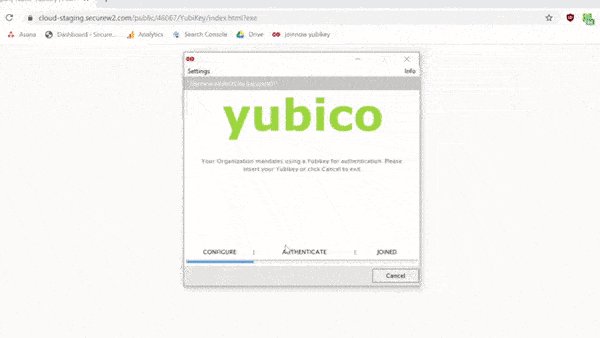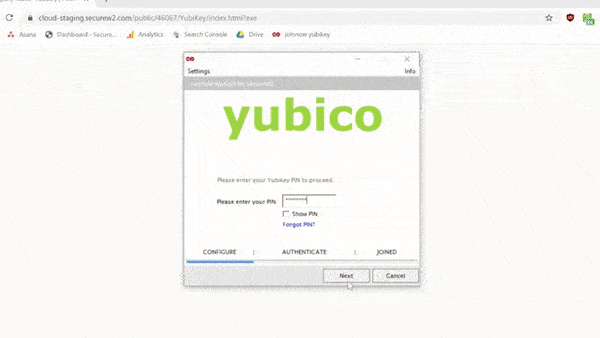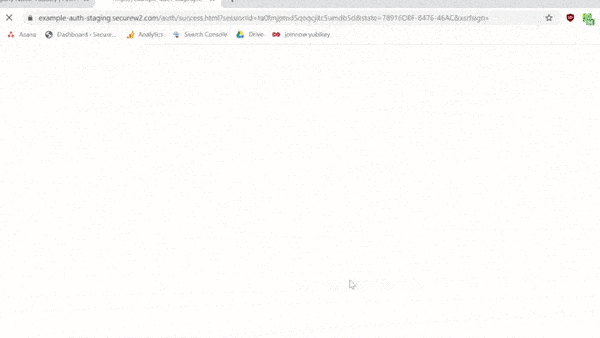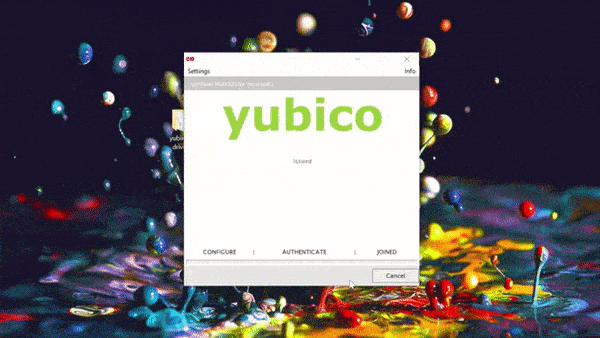
Once tied into your PKI via SecureW2, Yubikeys can be used for 802.1x authentication for access to Wi-Fi, VPN, desktop login, and virtually any web app with support for certificates (and you can continue using the intrinsic private key generator for services that don’t support certificates).
The Best Enterprise PKI Smart Card Management System
Despite being geared towards enterprise cybersecurity, PKI smart cards rarely have the capacity to be managed at scale. Insufficient smart card management can lead to vulnerabilities more dangerous than simply not using the cards at all, which is why a robust SCMS is vital.
Fortunately, the SecureW2 SCMS can be integrated into your existing network infrastructure or be included as part of our larger Cloud PKI solution. We help organizations of all types secure their network perimeter with digital certificates and MFA provided by security keys. Click here to check out our pricing page and see how affordable peace of mind can be.