Key Points
- Automate threat remediation & notifications with Adaptive Defense
- ACME for server certificate enrollment is now supported.
- Detect potential certificate spoofing with CertIQ ML Anomaly Detection.
Trust rules how the world works. It’s the foundation of personal relationships, how we choose who to do business with, and how we grant people (and now non-human identities) access to critical systems and information. Despite how important it is, there is a shockingly low amount of education around trust.
What does it actually mean? How do you earn it? How should it be defined in different scenarios?
These are the kinds of questions we ask ourselves that inspired our goals for the 8.0 version of the JoinNow Platform. We wanted to give you better systems and processes that help define when a user or device, and the scenarios they are in, should be trusted. If improving the way you trust and validate identity is something you are interested in, join us as we break down some of the key enhancements we made in our most recent update.
Adaptive Defense
Adaptive Defense is a new capability added to the JoinNow Policy Engine designed to improve an organization’s ability to respond to events that occur in identity, device management, and security systems.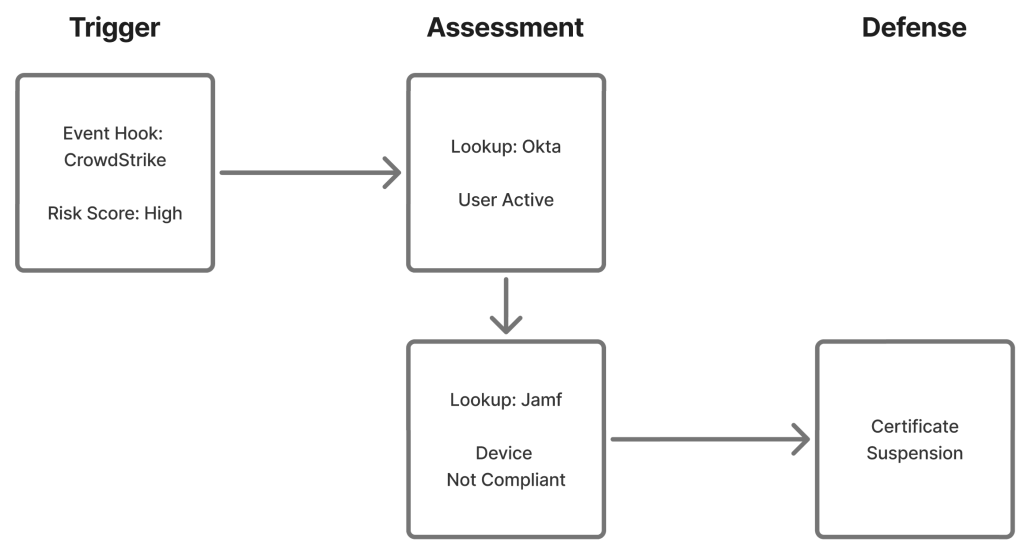
It works by taking Security Signals, performing an assessment of the trustworthiness of a user/device, and then implementing remediating action. It’s a major new feature that improves the way you can validate the trust behind your active certificates and network access.
Auto-remediation actions include:
- Reactivation of a user certificate when the user account is reactivated.
- Temporary removal of access by suspending a device’s certificate.
- Email alerts when certificate requests or network access are anomalous.
- Certificate revocation and network deactivation due to a critical risk score.
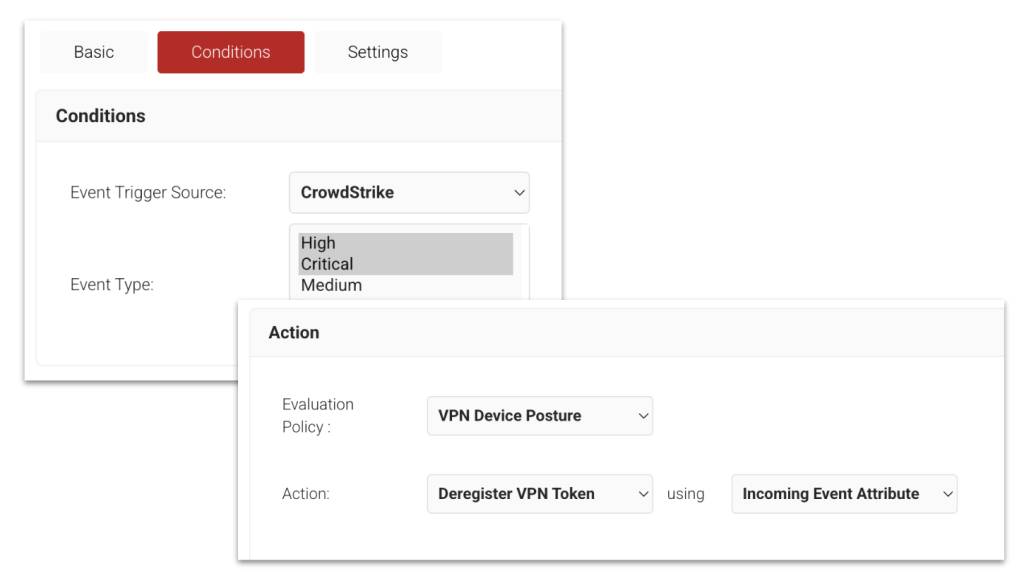 Adaptive Defense also supports the ingestion of even more events from your tech stack, including the following:
Adaptive Defense also supports the ingestion of even more events from your tech stack, including the following:
- Okta: User added/removed from group, user lock/unlock, and other events.
- OneLogin: User lock/unlock, deactivated/reactivated, and deleted events.
- Azure: Deactivated, reactivated, and deleted events.
- Jamf: Computer/mobile device added/removed from a smart group.
- EDR/XDR Vendors: Actions are triggered based on composite risk exposure levels.
With this new capability, you can aggregate signals from your entire IT and security stack, across multiple domains and vendors, before taking remediating action. We believe trust needs context, and Adaptive Defense is there to help you make automated, context-driven decisions.
Intelligence Briefs
Intelligence Briefs is a combination of comprehensive dashboards and notification/alarm capabilities that are aimed at helping improve the resolution/troubleshooting of enrollment/authentication issues, as well as identify potential security vulnerabilities. They are divided into two categories, one for RADIUS and the other for PKI.
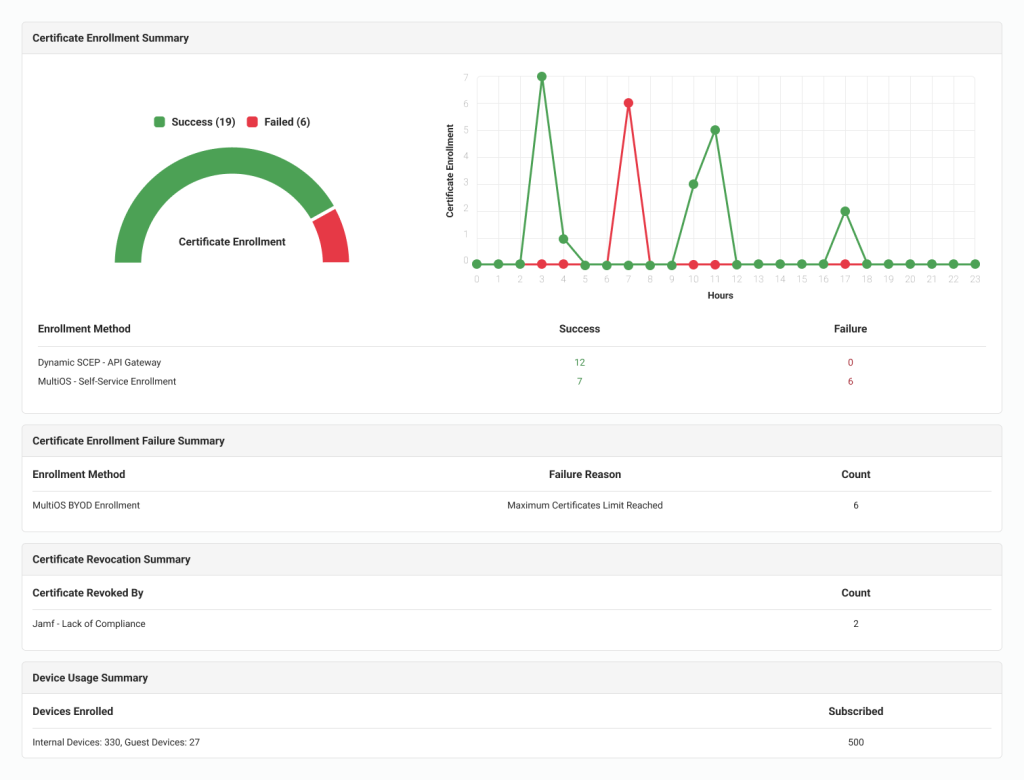
The Intelligence Brief email notifications aggregate key metrics so SecureW2 admins can more easily monitor authentication and authorization. The Intelligence Brief dashboard provides detailed metrics, such as Authentication status and device MAC address. Users/admins can double-click a device that shows unusual activity to view its full history and associated data.
Instant Alerts with CertIQ ML Anomaly Detection
Instant Alerts allow for the configuration of dynamic notifications triggered by specific criteria or anomalous behavior detected by SecureW2. These customizable notifications include thresholds for authentication rejects, anomalous certificate usage, and counts for successful/failed certificate enrollments and revocations.
CertIQML serves as a post-issuance monitoring layer, actively detecting anomalies, like certificate duplication or reuse. This is to help prevent certificate spoofing attacks, quickly alerting you when something out of the ordinary is taking place.
ACME Server Certificate Support
That’s right, we are excited that we now support the use of ACME for server certificates! You can now use SecureW2 Certificate Authorities to issue certificates with your ACME Clients.
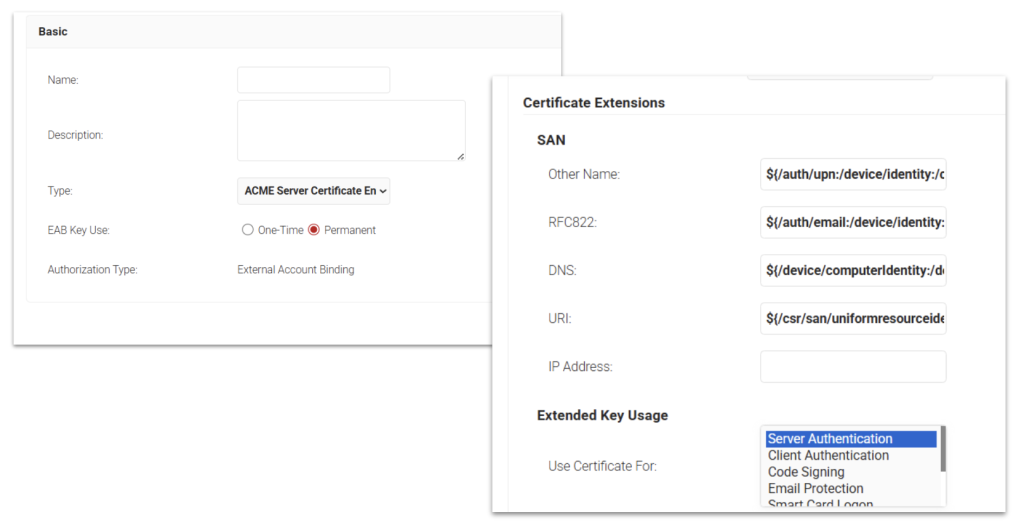
Windows IIS, Linux, and Apache Tomcat servers can now be automatically enrolled with certificates using the ACME protocol, with win-acme and acme.sh being the first supported ACME clients.
For the 8.0 release, External Account Binding (EAB) is supported to verify if the certificate enrollment request is from a trusted server. HTTP / Domain Validation will be supported in a future release.
Enhanced Dashboards & Event Views
The main JoinNow Dashboard has been improved, providing better context for troubleshooting and threat remediation. All events are now expandable by default, allowing you to click anywhere on an event row to view all the details you need to take action effectively.
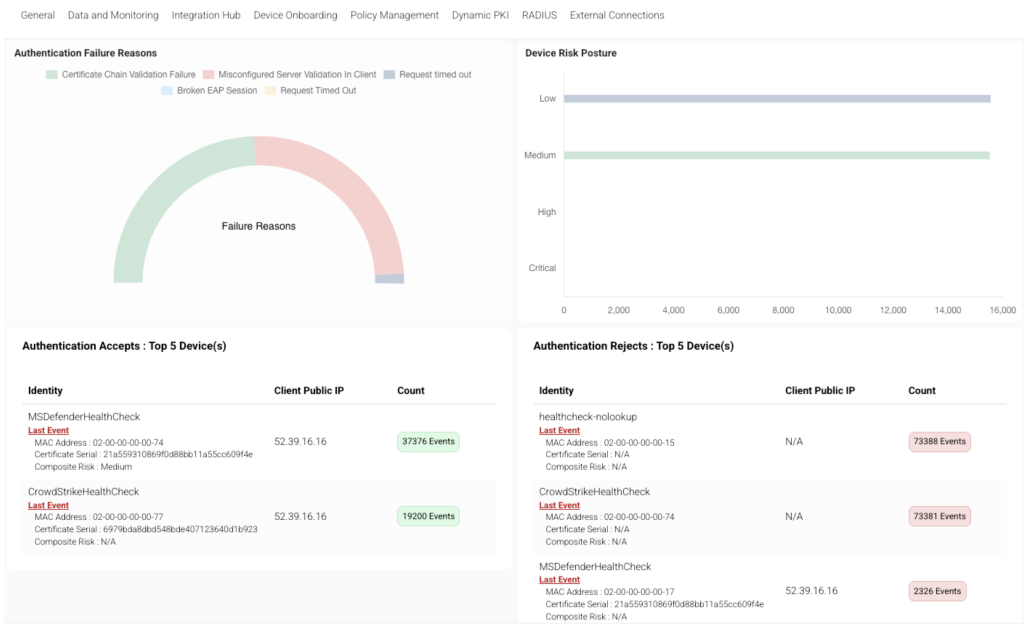
Dashboards will also display statistics for the last seven days (with future plans to increase the time ranges). Since the Intelligence Briefs will cover the previous day’s data, improvements to the JoinNow Dashboard give you a better understanding of your security posture at a higher level.
Working Towards Continuous Trust
Our ultimate goal is to replace static and short-lived certificate models by making certificates dynamic, self-adjusting trust objects that reflect current conditions in real time.
This live, condition-aware approach ensures continuous trust enforcement by aligning certificate validity to real-time conditions, enabling automated suspension, reactivation, revocation, or reissuance without manual tracking or renewal workflows, thereby operationalizing zero trust’s principle across network, SSO, cloud, and workload access.
Trust isn’t a checkbox you tick once, it’s a living, ongoing commitment.
We believe your business and your network deserve security that works as hard as you do. That’s why we’ve built a framework that validates, adapts, and enforces trust every time it’s needed, not just the first time. Because today, continuous trust isn’t optional. It’s essential.