Key Points
- OAuth is a secure authorization protocol that allows applications to access user resources without exposing passwords or credentials.
- OpenID Connect is an authentication protocol built on OAuth, enabling apps to verify user identities while granting secure access.
- With SecureW2, organizations can combine OAuth and OpenID Connect with certificate-based authentication for streamlined, secure, and passwordless access management.
Authorization and authentication processes need to be more solid and safe than ever. OAuth and OpenID are two well-known names in this field. Before we get into the OAuth vs. OpenID debate, it’s essential to know what OAuth and OpenID are, how they work, and why they’re essential in current applications.
OAuth, which stands for “Open Authorization,” is a framework for authorization. Its primary goal is to let third-party apps access resources on behalf of a user with the user’s permission. OpenID, on the other hand, is primarily concerned with authentication. It enables users to authenticate their identity across several websites or applications in a standardized manner. The primary point in the OAuth vs. OpenID debate is when and how to employ these protocols in various applications. While OAuth is concerned with issuing rights and authorizations, OpenID is concerned with user authentication. Choosing amongst them entails considering elements including the application’s use case, security needs, and user experience.
In this article, we will delve deeper into the workings of OAuth and OpenID, examine their strengths and weaknesses, and ultimately provide insights to help you decide which protocol best meets your specific authentication and authorization needs.
Click Hereto read how SecureW2 helped manage the guest network of a Florida County School District.
Understanding OAuth
OAuth is an open standard procedure that lets applications safely access resources on behalf of a user without revealing the user’s credentials. Its main goal is to allow third-party apps, with the user’s permission, restricted access to a user’s protected resources on a resource server. This method improves security by making it harder for people to share private login credentials. It also makes it easier for different web services and apps to work together smoothly.
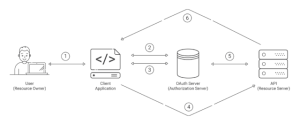
Key Components
Client: The term “client” refers to the software requesting authorization to use a restricted resource, such as a web service or mobile app.
Resource Owner: The owner of the information or system that the client is attempting to access.
Authorization Server: The authorization Server is in charge of user authentication and client authorization. It is responsible for issuing authentication tokens.
Resource Server: It refers to the server where the encrypted data resides. It verifies client access tokens and makes authorization decisions.
Pros and Cons of OAuth
Pros
Widely adopted and supported: OAuth is an industry standard that is known and used all over the world. It is used by some of the biggest tech companies, which makes it a good choice for safe entry control.
Fine-grained access control: With OAuth, you can be very specific about what a client can do. This level of detail improves security by limiting access to only the necessary tools and acts.
Cons
Complexity: Implementing OAuth can be challenging, especially for coders who have not worked with the system. It can take a lot of work to keep track of all the different flows and security concerns.
Limited User Information: OAuth is mostly about giving permission, so it doesn’t tell much about the person. It verifies that the user has given permission to access but doesn’t give specific information about the user. This can be a problem in some situations, like personalization, where you want to know more about the user.
OAuth is a powerful system that allows current applications to access resources safely. However, because it is complicated and focuses on permissions, you must consider whether it will work for your unique use case and needs.
OpenID Explained
OpenID is an authentication protocol that has been specifically developed to streamline the user authentication procedure across a multitude of websites and apps. Its main objective is to let users log in to many websites or online services using a single set of credentials issued by an identity provider. OpenID mitigates users’ need to generate and recall several usernames and passwords, augmenting the overall user experience and bolstering security measures.
Think about how you use social media sites like Facebook or Google. You can often use your Facebook or Google account to access third-party websites or apps through these services. Here is where OpenID is essential.
OpenID is used when you sign in with your Facebook account on a trip planning website. The booking site is the Relying Party (RP), while Facebook is the OpenID Provider (OP).
In this situation:
OpenID Provider (Facebook):
The online travel agency can rest easy knowing you are who you say you are since Facebook verifies your identity and sends a unique token to prove it.
Relying Party (Travel Booking Website):
The online booking service for vacations recognizes your Facebook login and allows you to sign in without entering any further information.
The authentication procedure is made easier for users in this manner. Use your current Facebook login information rather than establishing a new one only for the trip booking website. By consolidating your identity management with a reliable provider, OpenID reduces the number of login credentials you need to remember and increases your online safety.
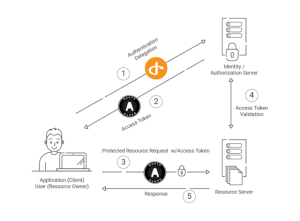
Key Components
OpenID Provider: This entity is the authentication service and confirms the user’s identity. The system generates identification tokens.
Relying Party: The website or application that depends on the OpenID Provider for user authentication. Access is granted based on the identity tokens supplied by the OpenID Provider.
User: The one who is requesting access to a Relying Party. The user employs their OpenID credentials as a means of verifying their identity.
Pros and Cons of OpenID
Pros
Simplifies User Authentication: OpenID makes it much easier for users to log in, making it easier for them and lowering the risk of security problems caused by passwords.
Allows users to control their identity: With OpenID, users have more power over their digital identity because they can choose their identity provider and handle their accounts there.
Cons
Limited support: Although OpenID is useful for identification, it may not be as widely supported and used as OAuth. In environments where OAuth is already familiar, this could be a problem.
Less fine-grained authorization: OpenID is mostly about identification, and its permission features may not be as advanced as OAuth’s, especially in situations needing fine-grained access control.
OpenID focuses on the user when it comes to authentication. This makes logging in more manageable and gives users power over their digital IDs. However, because it only focuses on authentication, it may need to be combined with OAuth or other methods for fine-grained authorization, based on your needs.
OAuth vs. OpenID: A Detailed Comparison
OAuth is primarily concerned with issuing rights to apps and services. It does not handle user authentication but assures authorized entities may act on the user’s behalf.
OpenID focuses on user authentication. It enables users to authenticate their identity across numerous websites or applications in a standardized manner.
When to use OAuth?
When your application requires third-party access to user data or you need to safeguard APIs, OAuth is the way to go. OAuth shines in instances involving social media connections by allowing external apps to access user data without disclosing sensitive user credentials. This allows for easy connection with significant platforms such as Facebook, Twitter, and Google, delivering a pleasant user experience while protecting user data.
Furthermore, OAuth excels at safeguarding APIs by offering effective access control techniques. OAuth allows you to govern who may access your resources, whether you’re constructing a web service, a mobile app, or any application that provides data over the internet. It allows you to set particular permission scopes, guaranteeing that only authorized entities have access, improving security and privacy.
When to use OpenID?
OpenID comes into play when you have Single Sign-On (SSO) needs or need to build federated identities across several domains or organizations. OpenID is an excellent tool for SSO systems since it simplifies user authentication across numerous sites or apps. Users may access diverse services using a single set of credentials from their preferred identity provider, minimizing the difficulty of managing multiple usernames and passwords.
Furthermore, OpenID thrives where trust must be established and user identities must be shared across domains or organizations. OpenID allows federated identity in circumstances requiring seamless user authentication and identity verification across organizational boundaries, improving user experiences and establishing confidence between domains. In such cases, it becomes an excellent tool for improving cooperation and user comfort.
Security Considerations
With access tokens, token termination, and scope-based access control, OAuth ensures that only authorized entities can access protected resources. OpenID Connect takes these security measures from OAuth and adds identity tokens, UserInfo APIs, and ID tokens to strengthen user registration and identity verification.
Scalability and Performance
Even though using OAuth to protect APIs may add some extra work because you have to get and confirm access tokens, its effects on speed are usually manageable with the right optimization. OpenID’s primary focus is authentication, so it usually has little effect on a system’s general performance when used correctly. When you understand these things, you can choose the correct protocol or a mix of protocols to meet your application’s security and authorization needs.
Final Verdict: OAuth or OpenID?
Factors to Consider
Several important things come into play when deciding whether OAuth or OpenID is better for your application. First of all, think about your unique use case and needs. OpenID is great for identity and Single Sign-On (SSO), while OAuth is great for situations that need permission and API security. Check your current system to see how each protocol fits your technology stack and integration ability. Also, put user experience and privacy at the top of your list. Figure out which protocol best fits your user authentication and data safety needs.
Making an Informed Decision
Start by picking the right tool for the job if you want to make a good choice. Choose the protocol that best fits your primary goals, whether to secure APIs, make user registration easier, or both. Sometimes, you may need to use OAuth and OpenID to find the right mix between authentication and authorization. Both methods can help build a strong and complete security and identity system when it makes sense.
Choosing Your Path to Secure Authentication: OAuth, OpenID, and Beyond
The debate between OAuth and OpenID shows the importance of choosing the right tool for your application needs. We looked at the main differences between OAuth and OpenID, paying particular attention to their strengths and how they can be used. OAuth is great at authorizing and securing APIs, while OpenID makes user registration easier and supports shared identity solutions. Your choice should be based on the needs of your project, the resources you already have, and the user experience. As you move through the constantly changing world of digital security and user identity, remember that these rules don’t contradict each other; they can work together when necessary.
SecureW2 is a reliable partner for those who want expert advice and custom identification and identity management solutions.JoinNow NetAuthis an example of one of our cutting-edge solutions that can help you set up safe, easy-to-use login and authorization options for your business. JoinNow NetAuth makes it easier to handle guest access by giving you a robust and flexible way to offer scalable guest wifi, whether secured or not. It makes it easier for users to invite guests, works smoothly with your directory system, puts security first, and simultaneously improves the user experience.
Contact usto take the next step towards protecting your digital identities.