Mutual TLS, or mTLS, is a trending talk of the town, especially regarding cryptographic encryption in general. Since you’re here, there’s a good chance you’re concerned about the network at your business’s security and want to look into more robust protections; even if you aren’t, we think it’s time you did.
In this article, we will understand the ins and outs of mutual TLS – how it provides security to sensitive data in a zero-trust security framework via two-way authentication, how it compares with other authentication methods, and some considerations to make when implementing mutual TLS.
What is Transport Layer Security?
Transport Layer Security (TLS), or Secure Sockets Layer (SSL), is a cryptographic protocol designed to provide secure communication over a network. It works by setting up a secure encrypted channel that protects the information transmitted from eavesdropping, data manipulation, and attacks. When browsers want to connect to a secure web server, they use TLS to provide privacy and data integrity for communications between applications.
In TLS, when a client initiates a secure connection with a server, they perform a handshake to establish the identity of the server and to generate and share a public/private key pair. Thereafter, session keys will be used for symmetric encryption of the subsequent messages during the established session.
Without TLS, sensitive information like credit card numbers, personal information, and passwords would risk being intercepted and exploited. TLS-based authentication offers a way to ensure that the data is being shared with the intended recipient and not an imposter. Here, the user is authenticated by presenting a valid certificate, which is verified by the web server at the other end.
So, What Is Mutual Transport Layer Security?
Mutual TLS is an advanced form of a standard TLS connection designed to enhance the security of data transmissions over the internet. Attackers can attempt to spoof a web server to a user or vice versa. Spoofing attacks are far more complicated when both sides have to authenticate with TLS certificates mutually.
In mutual TLS authentication, a client sends its public key and certificate to the server. Then, the server verifies this client’s public key to identify that the request is coming from a known client and has the corresponding private key that the client shared. The opposite also happens, where the client verifies the key sent from the server. In simple terms, mutual TLS is used to securely verify users, devices, and servers within a network. This article provides an in-depth exploration of mutual TLS and how it works to secure your data.
TLS Versus mTLS
While TLS and mTLS provide encrypted communication, the primary difference lies in the authentication process. In TLS, only the server’s identity is authenticated by the client, whereas in mTLS, both client and server identities are authenticated mutually. mTLS offers a higher level of security than standard TLS because it requires both client and server to authenticate each other. In other words, mTLS provides a post-handshake client authentication. By confirming the identities of both parties involved in the data transmission, mTLS significantly mitigates the risk of a data breach.
Instances Where TLS or mTLS are Applicable
Both TLS and mTLS are helpful in different scenarios. For instance, TLS is commonly used in basic web browsing, where the user only needs to confirm the server’s identity. On the other hand, mTLS comes in handy when both parties need to validate each other’s identities – this is especially important in business-to-business (B2B) data transmissions, connecting cloud services, and high-security applications.
How Does Mutual Authentication in mTLS Work?
Mutual TLS is a form of authentication where both parties in a data transmission process authenticate each other by exchanging and verifying digital certificates, which are used to confirm the identities of both the client and the server. In a typical mTLS authentication process, both the client certificate and the server certificate are presented to each other. Each entity then verifies the other party’s certificate to confirm its identity before the data transmission occurs.
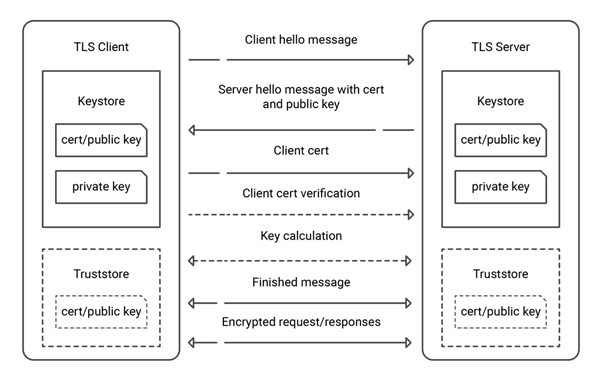
At the start of an mTLS session, the server responds by presenting its certificate to the client. Then, the client verifies this certificate against a list of trusted certificate authorities. If the server’s certificate is valid, the client responds by sending its client certificate, which the server likewise verifies. Only after a successful certificate exchange, called a mutual authentication step, does the data transmission occur.
The key benefit of mTLS is the added layer of security it provides. It makes it much more difficult for attackers to impersonate either party. This makes mTLS highly beneficial for securing sensitive communications.
How does mTLS Establish an Encrypted TLS Connection?
Mutual TLS establishes an encrypted TLS connection using a cryptographic protocol once the mutual authentication process between the client and the server is completed. A secure, encrypted channel is established where all data is transmitted. This encryption process ensures that any information sent over this channel remains private and immune to unauthorized access or eavesdropping, thereby ensuring the integrity and confidentiality of the data in transit.
Public Key and Private Key in mTLS
In an mTLS connection, a public key and a private key play crucial roles in the authentication process. The public key certificates are freely shared and used by others to encrypt messages intended for the certificate’s owner. Conversely, the private key is kept secret and is used by the certificate owner to decrypt received messages. Thus, the interplay between the public and private keys ensures two-way authentication and secure communication in an mTLS setup.
What is a Mutual TLS Certificate?
A mutual TLS certificate is a digital certificate that verifies the identity of an entity in an mTLS data transmission. A trusted certificate authority issues this certificate and contains the entity’s public key and other identifying information. mTLS certificates serve as proof of identity in an mTLS handshake. They are critical in establishing trust between the two communicating entities. mTLS certificates help ensure that only authenticated entities can communicate data, preventing unauthorized access and data breaches.
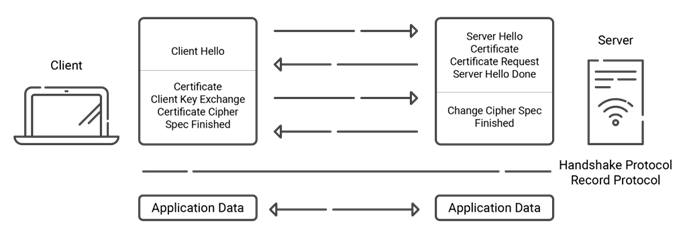
TLS Handshake
What is the Role of a Certificate Authority in mTLS?
Generating an mTLS certificate typically involves making a certificate signing request to a trusted certificate authority (CA). Certificate authorities then issue digital certificates to entities in a data transmission. These certificates, which contain the entity’s public key and identifying information, are used to verify the entity’s identity on the other end of the communication. Thus, CAs are instrumental in establishing and maintaining trust in an mTLS environment, ensuring that only authenticated entities can communicate and preventing unauthorized access and potential data breaches.
Mutual TLS Versus Various Authentication Methods
Let’s now dive into a comparative analysis of mTLS with other authentication mechanisms to highlight its unique strengths and applications.
What is the Difference between JWT and mTLS Authentication?
JSON Web Tokens (JWT) and mTLS are robust authentication methods, but they operate at different levels and serve different purposes. JWT is essentially a token-based authentication method. It allows secure transmission of information between parties in the form of a compact JSON object. The information, or ‘claims’ contained in the JWT, are digitally signed, ensuring the integrity of the data. The key selling point of JWT is that it is self-contained, carrying all the necessary information in the token itself, which makes it an excellent choice for decentralized or distributed systems.
On the flip side, mTLS provides double authentication at the transport layer. Unlike JWT, which primarily focuses on the application layer, mTLS operates at a lower level, securing the entire transmission channel between the client and the server. It requires both parties to authenticate each other using digital certificates before any data exchange takes place, offering a significant boost in data security.
In sum, while JWT provides a mechanism for conveying user authentication and authorization data between parties, mTLS safeguards the entire communication channel from potential intrusions.
Oauth2 vs. mTLS
OAuth2 is an authorization framework that allows third-party applications to obtain limited access to user accounts on an HTTP service. It provides clients a ‘secure delegated access’ to server resources on behalf of a resource owner. It’s commonly used to allow users to log into third-party websites using their credentials from a website like Google or Facebook.
Contrastingly, mTLS is neither about authorization nor about third-party access. Instead, it’s about verifying identities (of both client and server) and then creating an encrypted communication channel for data transmission. While OAuth2 relies on bearer tokens to prove an identity, mTLS uses digital certificates. This fundamental difference makes mTLS more suitable for scenarios where both communication endpoints need to be validated and secure and not merely for delegated access.
Should You Enable IEEE 802.1X Authentication?
Implementing IEEE 802.1X authentication can be an excellent decision for organizations seeking to amplify their network security. Essentially, 802.1X provides a framework for authenticating and controlling user traffic to a protected network based on a particular standard. It effectively prevents unauthorized access to network resources, which can be critical in a corporate or enterprise setting.
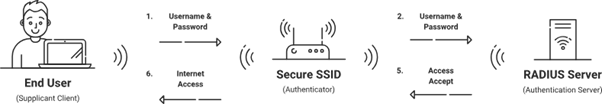
However, while 802.1X provides strong user authentication, it doesn’t necessarily secure the communication between the client and server, especially in a non-enterprise context over a wide area network (WAN). That’s where mTLS works best. mTLS not only provides mutual authentication at the start but also maintains encrypted communication during the session’s entirety. It ensures that the data in transit is safe from eavesdropping or tampering. Hence, in situations where both robust authentication and data security are paramount, combining 802.1X for access control with mTLS for data security could be a formidable solution.
Does 802.1X use TLS in its Operation?
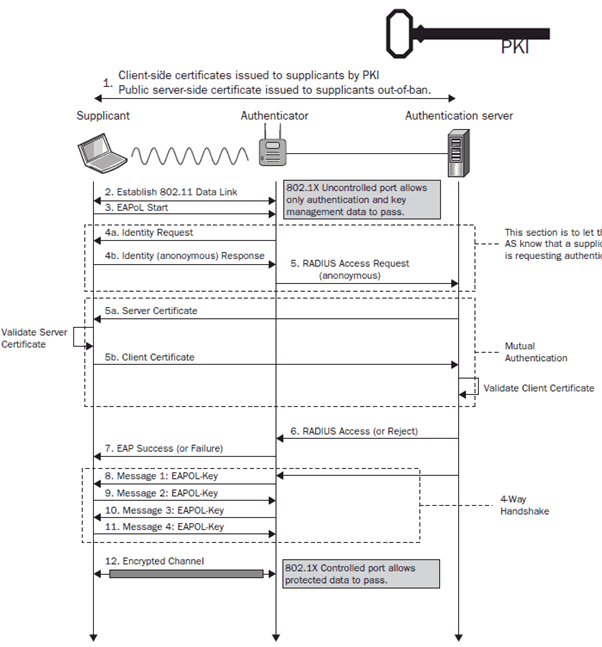
Indeed, 802.1X does employ TLS in its operation. Specifically, it uses Extensible Authentication Protocol (EAP) over LAN (EAPoL) protocol, with EAP being flexible enough to support several authentication methods, including EAP-TLS. EAP-TLS is an IETF open standard that uses the TLS protocol to secure the authentication process.
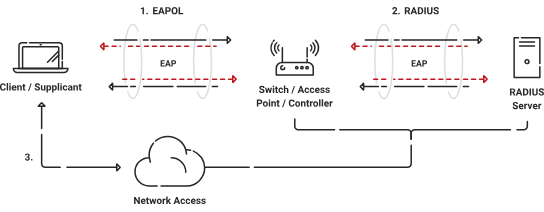
Like mTLS, EAP-TLS uses certificate-based authentication, but these two protocols operate at different levels. While EAP-TLS is typically used in a LAN environment for network access control (like Wi-Fi authentication), mTLS is more common in protecting application-level communication over a WAN, such as securing HTTP traffic between a web browser and a server. Thus, while there is a similarity in using TLS, the context in which 802.1X (with EAP-TLS) and mTLS are used differs, each serving its unique purpose.
RADIUS for Authentication
Remote Authentication Dial-In User Service (RADIUS) is a client/server communication protocol often used by ISPs and large enterprises. It’s a centralized system providing secure connection authentication, authorization, and accounting for users. In a RADIUS setup, user credentials are authenticated against a central server, and access policies are downloaded to the network access server. RADIUS is especially useful in large-scale operations due to its ability to handle a significant volume of authentication requests simultaneously.
What is the Difference between 802.1X Authentication and RADIUS?
While 802.1X and RADIUS protocols have overlapping functionalities, they are different. 802.1X is an IEEE standard for port-based Network Access Control (PNAC), defining the encapsulation of the Extensible Authentication Protocol (EAP) over IEEE 802 networks. RADIUS, on the other hand, is a centralized client-server system that manages network access by authenticating and authorizing users and tracking their activities. In many cases, a RADIUS server is used in conjunction with 802.1X to handle the actual authentication and authorization processes.
EAP TTLS and TLS
EAP TTLS (Tunneled Transport Layer Security) and EAP TLS are types of Extensible Authentication Protocols used in securing communications. EAP-TLS provides strong, certificate-based authentication, where users and servers must authenticate each other using digital certificates.
EAP-TTLS, however, allows legacy password-based authentication methods to be used within a TLS-secure tunnel. Thus, while both provide secure communication channels, EAP-TLS is generally seen as more secure due to its dual-side certificate authentication. In contrast, EAP-TTLS provides a balance between security and ease of use.
SecureW2’s Commitment to Advanced Security
mTLS provides an advanced level of security for data transmissions by implementing a mutual authentication process between the client and the server. In line with the industry’s increasing focus on advanced security, SecureW2 provides pioneering solutions integrating mTLS. With a robust toolkit that includes PKI (Public Key Infrastructure) services, 802.1X Authentication, and certificate management, SecureW2 is positioned at the cutting edge of network security.
SecureW2’s PKI Services simplify the process of generating, distributing, and managing digital certificates – a crucial part of mTLS authentication. This service ensures businesses have the right tools to implement and maintain an advanced mTLS system properly.
SecureW2’s 802.1X authentication solution provides secure network access control, ensuring only authorized users can access the network – a crucial feature to complement mTLS to create end-to-end secure networks. Our approach integrates seamlessly with existing infrastructure, resulting in a cost-effective solution that doesn’t compromise security. Check out SecureW2’s pricing to see if our certificate solutions can provide TLS security for your organization.
