Key Points
- Misconfigured RADIUS servers, certificate errors, or client supplicant issues often cause failed authentications and connectivity drops.
- Use RADIUS logs, supplicant diagnostics, and certificate validation checks to pinpoint where the authentication flow is breaking.
- SecureW2 simplifies 802.1X troubleshooting with Cloud RADIUS visibility, real-time logging, and Dynamic PKI automation, reducing downtime and IT overhead.
The technological landscape of the workplace has shifted dramatically – especially with the move towards hybrid remote/on-site work environments. Gone are the days when employees would only use company-owned devices for work; now, BYODs/unmanaged devices are an increasingly common part of your organization’s IT ecosystem.
But any security-conscious administrator will be wary of devices they don’t have direct control over. These devices can be security risks, and ensuring they’re properly configured for the organization’s network can be a strain.
For simplicity’s sake, some argue that an open SSID is the best solution in this scenario. However, rigorous network security standards – such as those demanded by 802.1X – don’t need to complicate access to necessary resources. In fact, 802.1X offers a range of benefits, including a much-improved ability to identify network and connectivity issues.
802.1X Components
One of the hurdles administrators face when trying to implement 802.1X is the complex configuration and architecture that needs to be established for it. What, exactly, do you need for 802.1X?
In a nutshell, 802.1X is just an authentication protocol that verifies the devices and users connecting to your network. You can secure your SSID with 802.1X for authentication. On the opposite end of the authentication spectrum, an open SSID requires no such authentication, like many public Wi-Fi networks without passwords that customers may use at businesses.
Contrary to what many may believe, however, 802.1X doesn’t necessarily need tons of complex components. In fact, all you really need to implement it are three things:
- Supplicants (most modern devices already have one in their network stack)
- Authenticators/access points
- Authentication server/RADIUS server
802.1X has a reputation for being difficult to build and maintain. While it’s true that it takes more time to set it up than merely establishing an open SSID, it doesn’t need to be complicated, and it offers inherent security and troubleshooting benefits.
Open SSID vs 802.1X for Network Authentication
The events that follow when a user connects to either an 802.1X network or an open SSID varies drastically. Let’s take a closer look at the authentication process for either option.
Open SSID Authentication
Chances are, you’ve encountered an open SSID before – likely in a business with a large number of daily guests, such as a restaurant or coffee shop. When you connect to one, all you need to do is find the network on your device and select it. Your device will submit an authentication request to the access point, and the access point will, in turn, automatically accept it.
In other words, no real authentication occurs. There is no need for you to submit anything attesting to your identity, whether it’s a password or a certificate.
This is, obviously, easy for the end-user. All they need to do is choose the correct network they want to connect to, and then they’re connected. That’s it.
However, simpler isn’t always better, and that’s certainly the case here. There are a lot of attacks that users are exposed to on open networks, such as packet sniffing or evil twin APs. If there are other open SSID issues, too, such as connectivity problems, it can be more difficult to troubleshoot – especially with the lack of accounting and authentication involved.
802.1X Authentication
What truly separates 802.1X from other network authentication protocols is the use of a RADIUS server; this allows every user/device to authenticate to the network with its own credentials. Here is a high-level overview of how the process works:
- The device attempts to connect to your network and presents credentials to the RADIUS server.
- The RADIUS checks that the device’s credentials are valid.
- If the credentials are valid, the RADIUS sends an ACCESS_ACCEPT packet. If the credentials are invalid, the RADIUS denies access.
The RADIUS itself does not contain user information, so it needs a database to check that the credentials provided to it are accurate. However, using passwords for credentials here exposes your network to a host of potential vulnerabilities – the more secure solution is to use digital certificates instead.
With digital certificates, the authentication process is a little different. Here is an overview:
- The device attempts to connect to your network and presents a certificate to the RADIUS server.
- The RADIUS checks that the device’s certificate is unexpired.
- If the certificate is unexpired, the RADIUS then checks to see if the certificate is on the Certificate Revocation List (CRL) to confirm whether or not it has been revoked.
- If the RADIUS supports Identity Lookup (such as our Cloud RADIUS), it will check your directory for additional user attributes to aid in policy enforcement.
Certificates are not just more secure than passwords, they also offer better UX to the end user by eliminating the need to remember and reset passwords. Admins appreciate certs because they provide vital identity context to every connection, facilitating more accurate and information-rich network monitoring and reporting.
Identifying Network Issues with 802.1X
The individual components of 802.1X, aside from the obvious benefit of security from rigorous authentication, offer the additional benefit of network visibility that makes troubleshooting simpler. If you are doing certificate-based authentication with onboarding technology, this is even more true.
Let’s look at how 802.1X can help you identify connectivity issues and resolve them more quickly.
Using RADIUS to Troubleshoot Network Issues
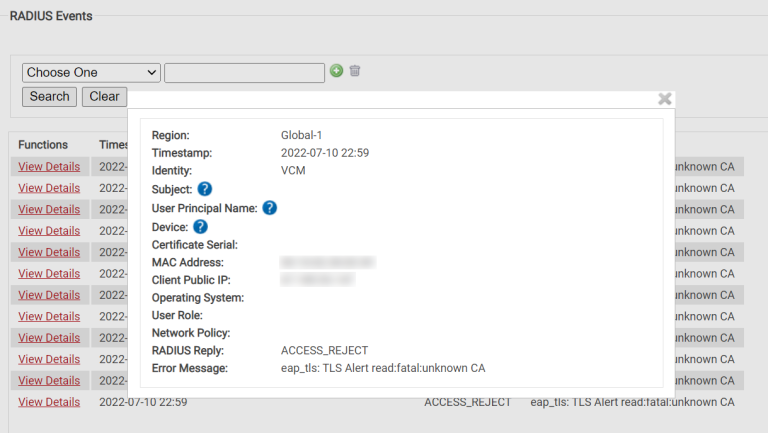
RADIUS servers are also known as AAA (authentication, authorization, and accounting) servers. The key to network troubleshooting lies in the last part of that phrase: accounting.
Users and devices authenticate to the network through the RADIUS server, and the server keeps a record of those authentication attempts, whether they are successes or failures. These records are called RADIUS event logs.
Just how much detail the event logs contain depends on the RADIUS in question; some RADIUS services may offer less detail than others. But with Cloud RADIUS, you get extremely detailed RADIUS event logs that provide a wealth of information beyond merely authentication failures or successes.
Whenever someone fails an authentication attempt, you’ll see the reason behind that failure. This can help you pinpoint what went wrong during authentication, and resolve it much more quickly as a result.
What’s more, you can search through the logs using a variety of filters. If one person, in particular, cannot get past authentication, you can search for their email address, for example, to see the error message the RADIUS recorded.
Onboarding Technology and Troubleshooting Network Issues
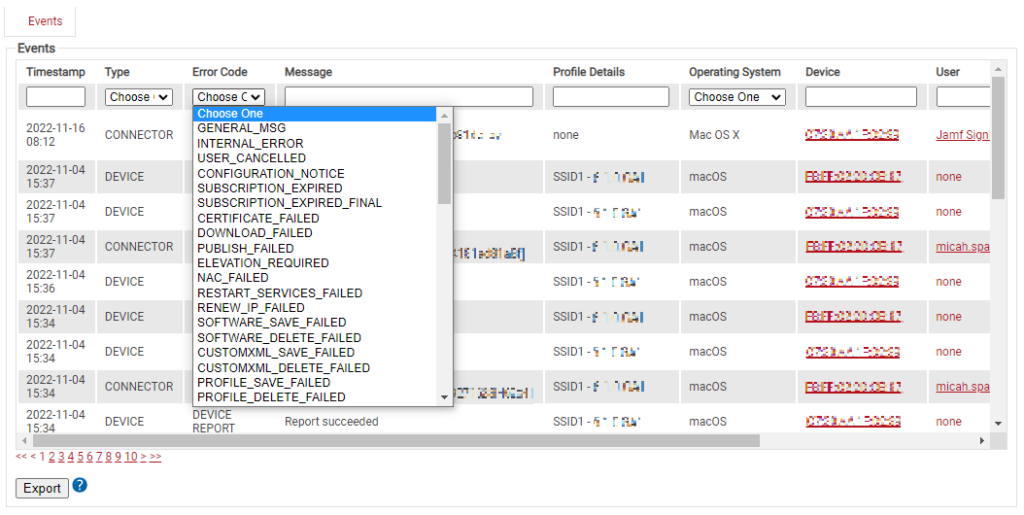
One of the biggest challenges to implementing 802.1X with certificates in the past has been getting those certificates onto all the devices that need them. With modern automation and onboarding technology, that’s no longer the case.
But onboarding tools aren’t just useful for equipping devices with certificates and configuring them for certificate-based authentication. The right one can also tell you so much more about the users’ devices – especially if a BYOD/unmanaged device is the device in question.
JoinNow MultiOS is a self-service onboarding application for BYODs. With its help, users can self-configure their own devices with just a couple of clicks. Beyond the simplicity of its configuration capabilities, however, it also offers a clear snapshot of what happens during that configuration. If it should fail for any reason, you’ll know why.
There are generally four types of messages that are recorded during the configuration process with JoinNow MultiOS: initial report, enrollment status, configuration status, and connection status. Each one can generate a range of error messages if there are any issues, allowing you to pinpoint exactly where in the process the user had a problem.
You’re also able to dictate a range of requirements for configuration. For instance, you can choose to only allow certain operating systems, devices that have the most recent OS updates, or devices with antivirus software. Should a device fail to meet any of your criteria, you’ll be able to instantly determine what the missing criterion was.
Foolproof Device Onboarding for 802.1X
If your main concern with 802.1X is that it’s hard to get everyone set up for it, the good news is that it doesn’t need to be. SecureW2’s JoinNow Suite contains everything you need to implement 802.1X – even the onboarding part.
Our self-configuration application, JoinNow MultiOS, guides users through the configuration process within two minutes. You can also create your own custom onboarding landing page with MultiOS, ensuring that each user knows they’re in the right place.
Of course, if you’re going to use certificates for authentication, you’ll want your own PKI, which is another service we provide. Our PKI is vendor-neutral and cloud-based, so it can integrate with your current infrastructure without the need for a network overhaul. We even have a powerful, cloud-native RADIUS service that all your locations and users can authenticate to from any location. These solutions don’t break the bank, either – check out our pricing to see just how affordable we can be.