Key Points
- Since RADIUS is also known as an AAA ( Authentication, Authorization, and Accounting) server, Accounting plays an important role in generating event logs that contain vital information such as connection requests, authentication success rates, and so on.
- RADIUS event logs play a vital role in audit compliance, troubleshooting authentication failures, Wi-Fi and VPN connectivity issues, tracking devices and users' access to your network, etc.
- You can easily view events with SecureW2's CloudRADIUS or stream Accounting logs to existing infrastructure.
RADIUS servers are often called AAA (authentication, authorization and accounting) servers because they perform each of those three functions. Accounting – which refers to the process of tracking events as they occur – is something a RADIUS server achieves by generating event logs.
RADIUS logs contain detailed information on the clients accessing your network. Checking here should be one of your first steps when determining what the cause of network connectivity issues is – or when you suspect unauthorized network access. In this blog, we’ll show you exactly where to find RADIUS event logs, and why they’re important.
What are RADIUS Event Logs?
RADIUS servers can be configured to perform event logging, an in-depth record of events related to connection requests from RADIUS clients. These event logs can vary in detail, but they will often show things such as the device, OS, user, whether the authentication was successful or failed, and error messages related to the authentication attempt.
Logs can be generated every time a RADIUS client attempts to authenticate to your network or VPN. They’re a great starting point for determining the root cause of Wi-Fi connectivity issues, or for meeting compliance requirements from auditing or regulatory authorities.
RADIUS Event Log Use Cases
Keeping event logs and regularly auditing them is necessary for modern cybersecurity. RADIUS event logs can be and are used for a variety of purposes, including the following:
- Compliance audits
- Troubleshooting authentication issues
- Troubleshooting Wi-Fi and VPN connectivity problems
- Tracking the devices accessing your network
- SIEM or Syslog alarms
Basically, event logs can be used anytime you need to troubleshoot connection issues for a particular user or device. They can also be imported to any Security Information and Event Management (SIEM) software you use, so you can be alerted right away when connection issues arise. In this way, they can potentially serve as the basis for the first notice you receive when there are problems with authentication to your network.
Finding Logs from Different RADIUS Servers
Network Policy Server (NPS) Logs
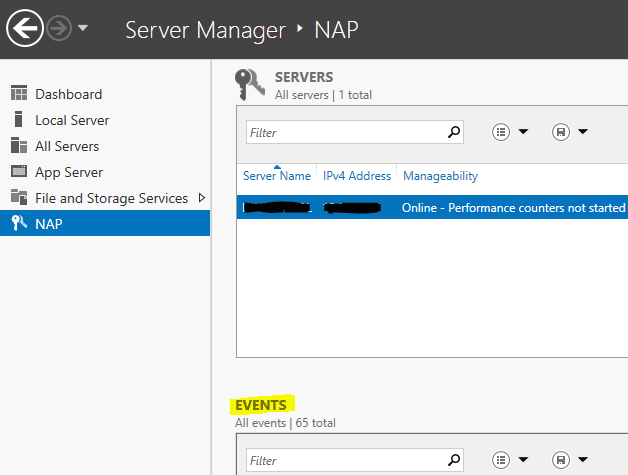
Network Policy Server (NPS) is Microsoft’s implementation of RADIUS. Network Policy Server logs can be viewed using Windows Server Manager or Windows Event Viewer UI (another system, part of the larger Windows Server package). You must decide whether you want to log RADIUS client authentication and accounting information to text log files stored on the local computer or to a SQL Server database on either the local computer or a remote computer. Like with other RADIUS servers, NPS event logs contain authentication results and the reason for any failed authentication attempts.
NPS is only suitable as an addition to an existing Windows Server in most environments. Its logs may not be as detailed as other RADIUS server logs, sometimes missing accurate reasons for connection failures like when users type in wrong passwords.
NPS and Active Directory (AD) are generally tied to on-premise infrastructure, as well. This means that NPS may not be a suitable choice for organizations looking for cloud-based identity management and access control solutions, such as Azure AD (Microsoft Entra ID) or similar.
FreeRADIUS Logs
FreeRADIUS is an open-source RADIUS server free for download and use. It can run on Unix-based platforms.
By default, Free RADIUS stores accounting information in /var/log/freeradius of the Unix platform, but accessing these logs takes some technical expertise.
Where Do I Find Cloud RADIUS Event Logs?
Cloud RADIUS, unlike an NPS server, is a managed and cloud-based platform that can be configured and deployed to any location. It also captures detailed logs for every network connection request and provides extensive information in addition to ACCESS_ACCEPT and ACCESS_REJECT responses.
This information can be easily found in the SecureW2 management portal by navigating to Data & Management, then selecting the RADIUS Events option.
Cloud RADIUS Event Log Fields and Meanings
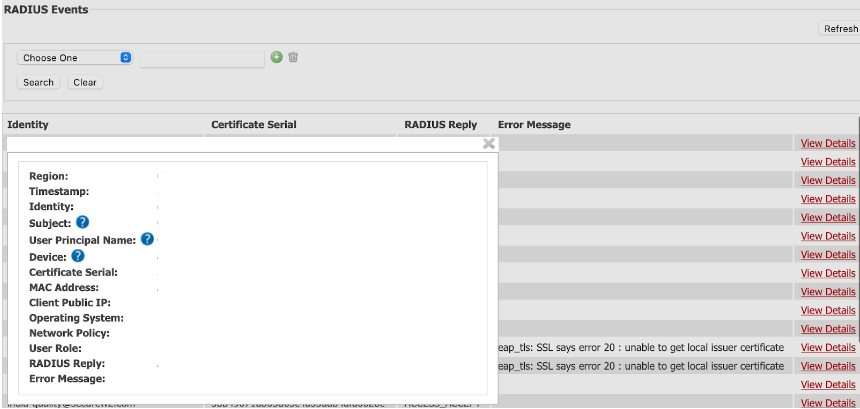
Cloud RADIUS event logs were designed to provide administrators a clear snapshot of each authentication attempt. As such, we’ve incorporated numerous fields in them, including the following:
⦁ Region – Origin of the connection request.
⦁ Timestamp – Recorded time of the connection request.
⦁ Identity – Username used during the authentication.
⦁ Subject/Common Name – Name of the user using the certificate or token.
⦁ User Principal Name – Email ID of the user trying to connect to the network.
⦁ Device – Information related to the device such as a serial number.
⦁ Certificate serial – Serial number of the device’s certificate trying to connect to the network.
⦁ MAC Address – Media Access Control Address of the device trying to connect to the network.
⦁ Client Public IP – IPv4 address of the device, needed for the network to reach the device.
⦁ Operating System – Software that supports the device trying to connect to the network.
⦁ User Role – The user role designated by the administrator that the user belongs to.
⦁ Network Policy – This shows the network policy that applies to the user.
⦁ RADIUS Reply – Status of the RADIUS Authentication (ACCESS_ACCEPT/ACCESS_REJECT)
⦁ Error Message – If applicable, the reason why the remote access authentication attempt failed.
Cloud RADIUS Event Log Search Filters
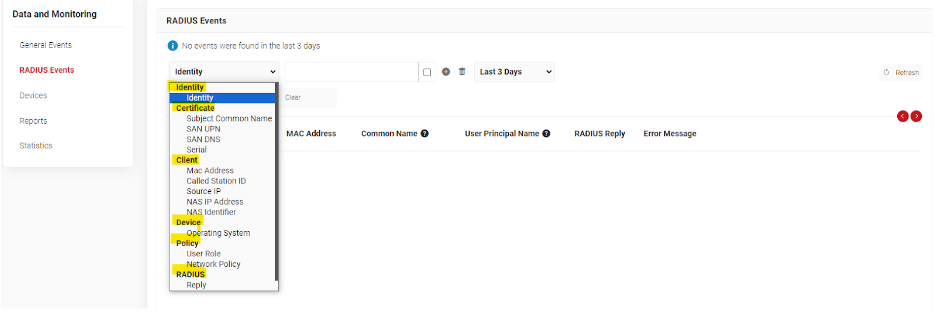
RADIUS logs are a great tool for troubleshooting when you start getting reports that users can’t connect to your network. Granular search filters make it simpler to access them, which is why Cloud RADIUS includes a range of search settings.
Narrow your search by checking a specific user, for example, when only a single person is experiencing connectivity issues. You can also search by operating system, MAC address, and more.
Detailed and Easily Accessible Logs with Cloud RADIUS
Event logs serve many purposes: they can be your first line of defense when an unauthorized party accesses your network, they can help you rapidly pinpoint the root cause of network connectivity problems, and they may be required for compliance reasons. Being able to quickly access and read RADIUS records is crucial.
Cloud RADIUS event logs streamline this process. Every authentication attempt is recorded in a detailed entry that provides administrators enhanced visibility. Additionally, granular search filters make it a simple matter to find the exact entry you need when you need it. Organizations using SecureW2’s Cloud RADIUS can not only view events from the management portal, but also export data to a SIEM provider to trigger an alarm and have notifications on the occurrence of connectivity issues.
We have affordable solutions for organizations of every size. Check out our pricing page here.
