Key Points
- SecureW2 enables you to use Google identities for EAP-TLS 802.1x authentication, issuing unique X.509 certificates to users and devices via Google Cloud, streamlining enterprise-grade network access
- The process involves creating a SAML app in Google Admin Console, uploading its metadata into SecureW2, and configuring ACS URL with Entity ID to establish the identity provider integration.
- SecureW2’s JoinNow Connector allows rapid deployment of certificate-based Wi-Fi security—getting devices connected with strong, passwordless authentication in just a few clicks.
Organizations are making the much-needed transition to cloud-based network solutions and Google is a forerunner in getting people’s devices and networks in the cloud.
However, for some, getting your devices configured and ready for WPA2-Enterprise Wi-Fi can be tricky and the process isn’t always straightforward. Luckily, SecureW2 can easily get your devices connected and ready for 802.1x authentication with a RADIUS server in just a few clicks with our JoinNow Connector and allow you to safely and effortlessly use certificate based security with Google.
How to Use Google Identities for 802.1x EAP-TLS Authentication
In this article, we will walk you through how to set up 802.1x authentication using Google Cloud as your identity provider. If you want to pursue passwordless authentication with X.509 certificates, you will need to configure Google with EAP-TLS authentication (as well as onboarding devices such as Chromebooks for certificate-based authentication).
This process will utilize your existing Google identities to issue users and devices a unique X.509 certificate encoded with attributes used for policy enforcement.
Creating a SAML Application in Google for 802.1x Enrollment
To create a SAML application in Google:
- From your Google Admin Console, click Apps, and then click SAML apps
- At the bottom-right of the screen, mouse over the yellow circle and click Enable SSO for a SAML Application
Click SETUP MY OWN CUSTOM APP -
- Under Option 2, for IDP metadata, click DOWNLOAD. Save the metadata file (.XML) to your computer
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers
- Click Edit for the IDP you created (GoogleSAML)
- Select the Configuration tab
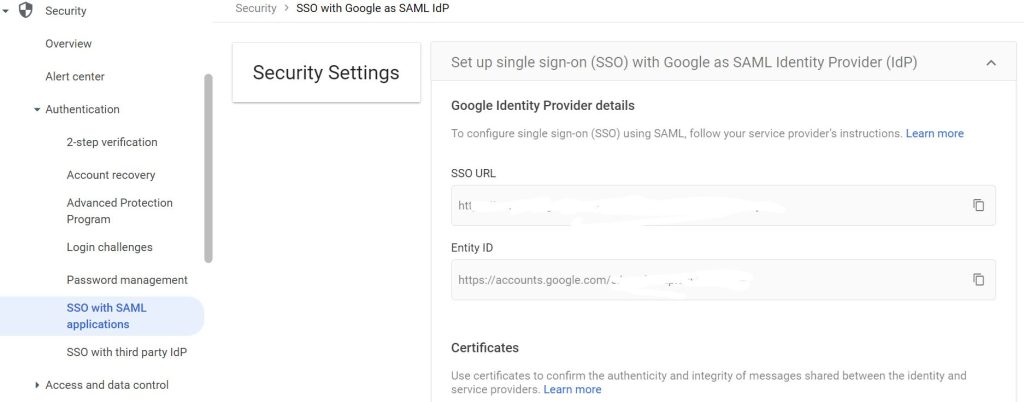
- NOTE: Note the ACS URL and EntityId — you will need these for step 11.
- Under Identity Provider (IDP) Info, for Metadata, click Choose File
- In the prompt that appears, select the metadata file you saved to your computer. Click Upload
- Then, click Update
- Copy the ACS URL and EntityId to your clipboard or somewhere handy
- Return to your Google SAML App setup
- On the Basic information for your Custom App page, enter the Application Name and Description
- Click Next
- On the Service Provider Details page, paste the ACS URL and the Entity ID
- Select the Signed Response check-box, and then click Next
- On the Attribute Mapping page, click Finish
NOTE: LDAP can be configured to communicate with Google using SecureW2.
Enrolling for an EAP-TLS Certificate with Google
Credential-based authentication is an outdated security measure when it comes to maintaining your network integrity. The EAP-TTLS/PAP protocol leaves your network open to potential threats as it sends your credentials in clear text, making it susceptible to over-the-air credential theft.
These threats can easily be deflected with the power and security of 802.1x digital certificates. Certificates are impossible to decrypt and eliminate the need to remember passwords, which is a win-win for end users and IT alike.
Fortunately, setting up passwordless certificate-based 802.1X authentication for Google is easier than you might think. Here’s a high-level overview of the steps to enroll for EAP-TLS certificates with SecureW2:
- Set up CAs in SW2 Management Portal
- CAs serve as the central authority for certificates and as the hub where admins can determine what roles and policies will apply for their network.
- Add Google as IDP in SecureW2
- Google can be configured as the IDP in SecureW2’s management portal.
- Google can be configured as the IDP in SecureW2’s management portal.
- Go to Google Admin Console to Configure the SAML IDP
- Once complete, the RADIUS server will be able to authenticate devices against Google.
- Configure Attribute Mapping
- Admins can map attributes to certificates so they’ll have an easier time seeing who’s on the network.
- Configure network policies to be distributed
- Once devices are properly configured, they can start requesting certificates.
Google RADIUS WiFi Setup
Certificate-based authentication (EAP-TLS) is the industry gold standard for secure Google Wi-Fi due to the protection it provides against the growing risks of credential theft. However, setting up the necessary PKI can be a daunting task, and some may think it might not be worth implementing just for Wi-Fi.
SecureW2’s Cloud RADIUS and Managed Cloud PKI are a turnkey solution that can get your organization set up, into the cloud, and ready for EAP-TLS authentication in only a couple of hours. We can even integrate with your existing infrastructure to hasten the process.
Traditionally, RADIUS authentication using the EAP-TLS protocol talks to the Certificate Revocation List (CRL) to deny access to users who have a revoked certificate. However, this can lead to a brief moment of vulnerability. Say an IT admin forgets to revoke a certificate? Or maybe the CRL has a longer update interval. The revoked certificate may still be valid, and the user will still have free reign to connect to your network and become a potential threat to your network security.
Our new Dynamic Cloud RADIUS addresses this issue by using industry-first technology that allows the RADIUS to dynamically communicate with your directory (Google, in this case) as well as the CRL to make sure that only approved users can be authenticated and gain access to your network.
Cloud 802.1X for Google WiFi
SecureW2 can get your Google WPA2-Enterprise network configured and ready in only a few hours with our world-class support team ready to assist you with any problems that arise. In addition, we are the only 802.1X vendor that offers EAP-TLS onboarding software for BYOD devices. For your managed devices, our SCEP gateways can automatically configure Chromebooks and other devices for 802.1X authentication (or Google WiFi VPN authentication).
Check out our pricing here and see how affordable our solutions are for all organizations of any size.