Key Points
- FreeRADIUS and Google LDAP integration enables 802.1X network authentication, enhancing security with existing directory services.
- While FreeRADIUS is open-source, deploying an on-prem RADIUS server with Google LDAP incurs hardware, maintenance, and staff costs. This requires considerable technical knowledge, with limited documentation, increasing deployment time and complexity.
- Google Secure LDAP mitigates credential theft risks, but implementing a cloud RADIUS service offers better scalability and reduced infrastructure overhead.
- SecureW2’s Cloud RADIUS eliminates on-prem costs, simplifies deployment, and offers better security through certificate-based authentication.
When it comes to securing your network, one significant challenge faced by numerous organizations is keeping security investments within budget. These attempts to curb budget often lead to organizations turning to solutions that seem inexpensive at a glance, such as open-source options.
FreeRADIUS is an example of an extremely popular open-source RADIUS server that many turn to for their own network authentication. With the right technical expertise, businesses have even used FreeRADIUS with Google LDAP in an effort to keep security economical. But how does this setup work, and is it really worth the investment?
What is Google LDAP?
Lightweight Directory Access Protocol (LDAP) is a protocol that maintains data in a directory and makes it easy to search for. This data can be any information relevant to your organization’s directory, such as individual device and user information.
LDAP is also the protocol that communicates with on-premise directories. So, when someone says “Google LDAP”, they are likely talking about a Google LDAP server that serves as a directory using LDAP to search its information for the ultimate purpose of user or device authentication with Google identities.
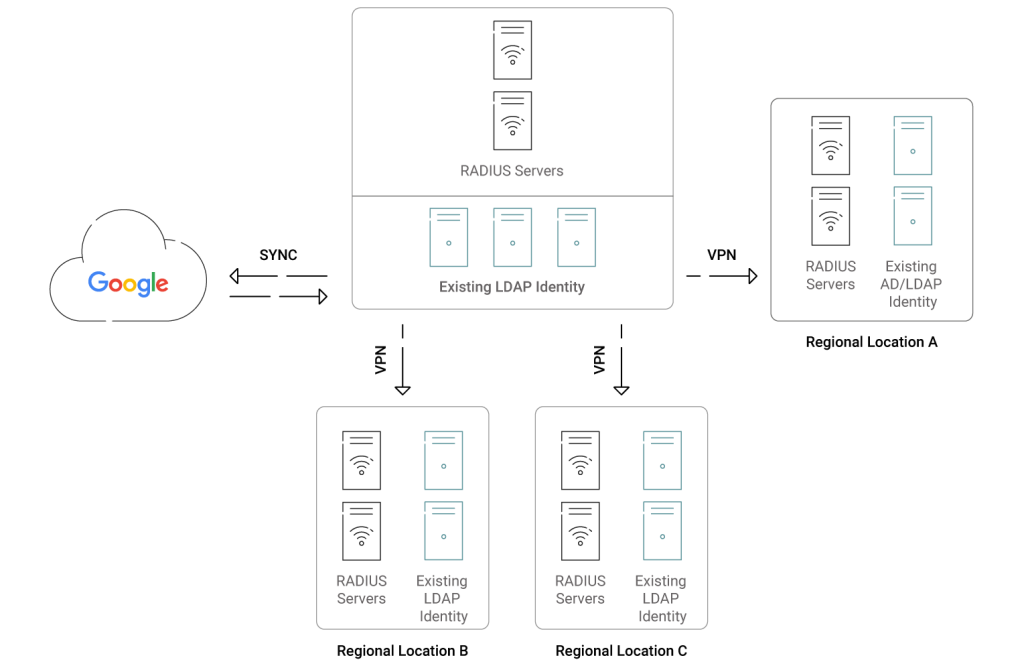
In this scenario, Google Identity still provides the directory service; the LDAP server is essentially an extra step in the equation that duplicates the information from your Google Identity services and converts it into a form compatible with on-premise services (like FreeRADIUS and LDAP itself). It looks something like the above-pictured diagram.
How does FreeRADIUS work with Google LDAP?
As we mentioned in the introduction to this post, FreeRADIUS is an open-source RADIUS server used all over the world. Like the name suggests, it’s a free tool that many have built their authentication processes around.
For an organization already using Google for its directory needs, it’s easy to see why FreeRADIUS is an attractive proposition. Configured correctly, it can leverage the policies you’ve established in Google already. To connect the two, some businesses will establish a FreeRADIUS server to communicate with their Google LDAP server.
This involves setting up an on-premise FreeRADIUS server and an on-premise Google server that uses LDAP. Then, FreeRADIUS will reference the Google LDAP server for authentication.
FreeRADIUS with Google LDAP Authentication Flow
At a high level, this type of authentication setup would work like this:
- A user logs into your network or an LDAP-compatible application by entering their credentials.
- The user’s device presents credentials to the RADIUS server.
- The RADIUS verifies that the credentials are correct by referencing the Google LDAP server.
- The Google LDAP server, in turn, forwards this request to the Google Identity Provider.
- The credentials are confirmed by the Identity Provider, and this information is sent back to FreeRADIUS, which sends an ACCESS_ACCEPT message to the user.
The Pros & Cons of FreeRADIUS with Google LDAP
Pros
Companies that are drawn to this infrastructure are generally drawn to it because, at least initially, it appears budget-friendly. After all, the RADIUS server is based on an open-source tool that anyone can access.
Additionally, if it’s configured correctly, this setup can indeed extend 802.1X authentication security to your Google environment, vastly increasing the security of your network. It’s important to keep in mind, however, that there’s a lot that goes into properly configuring FreeRADIUS with Google LDAP.
Cons
Although organizations building FreeRADIUS with Google LDAP likely did so to save money, they are often quickly shocked by mounting costs they didn’t anticipate. These costs are largely associated with what you need to establish a secure on-prem RADIUS server; physical components, on-site security measures, recurring licensing fees, and, of course, paying for the staff to maintain it all. There’s a reason why on-prem RADIUS servers are often so much more expensive than cloud-based ones.
Skyrocketing costs aren’t the only things that shock IT departments building this infrastructure – the sheer amount of effort it takes to deploy the newly secured network from scratch is also surprising. One issue with using open-source solutions, in general, is that you’re left essentially coding and configuring them all by yourself (and, in this case, without the benefit of a GUI). And if you don’t already have someone capable of doing this in your business, then you’ll need to hire someone who can do it (and then maintain it indefinitely) – which can be costly depending on market rates in your locality.
The lack of supporting documentation surrounding the construction of FreeRADIUS with Google LDAP servers is another problem. Without clear direction, security professionals attempting to configure this on their own may feel left in the dark, frustrating them and increasing the deployment time. FreeRADIUS fortunately does offer support for those in need of it, but this support comes at a monetary cost.
Last but certainly not least, there’s the vulnerability of LDAP itself to take into consideration. If you’re using credentials – usernames and passwords – as the authentication method with your LDAP server, that sensitive information is communicated in clear text, which means it can be intercepted in over-the-air attacks.
Google offers Secure LDAP to help protect against this possibility. Although it can integrate with LDAP-compatible applications that utilize credentials, it normally uses certificates, which requires a public key infrastructure (PKI) to manage. It also utilizes cloud-based LDAP servers, so your LDAP applications and infrastructure can be either on-prem or cloud-based while using Google Secure LDAP.
However, even though Google Secure LDAP can be used with certificates for added security, many LDAP clients will still require you to use both certificates and credentials. Credentials are demonstrably less secure.
Alternatives to Google LDAP
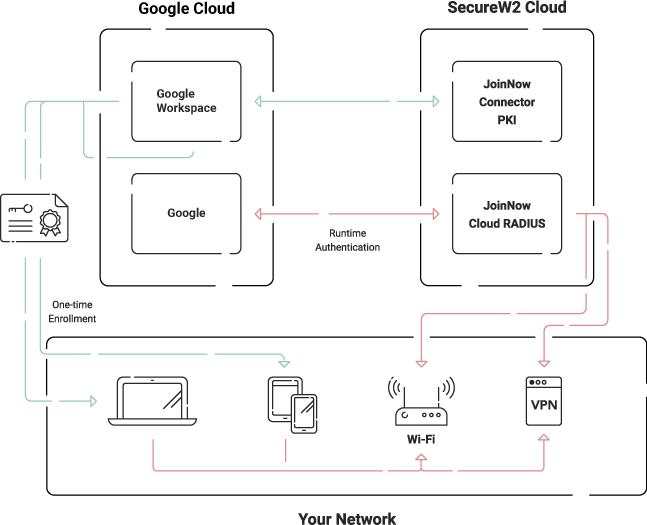
The good news is that you don’t need to pay for an additional LDAP server if you want to use your Google identity provider for authentication. In fact, you can tie your Google directly to your Wi-Fi and VPN authentication with the right solutions.
How? By cutting out the LDAP middleman entirely and using a cloud-based RADIUS service like Cloud RADIUS.
All the cons associated with on-premise infrastructure are removed when you use Cloud RADIUS. Because it is cloud-native, it can be used across multiple locations and users/devices can authenticate from anywhere. It’s also vendor-neutral, so it can integrate with your current infrastructure – including Google – without the addition of an LDAP server. Its Identity Lookup feature allows it to communicate directly with Google in real-time during authentication, applying the most current policies from Google to the authenticating user or device.
Unlike LDAP, Cloud RADIUS was designed for certificate-based authentication, which eliminates the possibility of credential theft. That means you’ll need a Public Key Infrastructure (PKI) with Cloud RADIUS, but that’s a service SecureW2 also provides. We even have the onboarding tools you need to effortlessly issue certificates to users and devices, whether it’s through our easy self-service onboarding application for BYODs or our auto-enrollment gateways for managed devices.
Replace On-Prem Google GLDAP with Cloud Google Authentication
On-premise infrastructure, like what would be required to build FreeRADIUS with Google LDAP, costs both time and money – oftentimes much more than what you would spend by simply going with a managed RADIUS service and PKI like SecureW2’s. In addition to helping you reduce expenses, Cloud RADIUS is easy to deploy and can integrate with your existing infrastructure. No need to maintain an outdated, on-premise LDAP server anymore.
And if you ever need technical support, our support team is composed of experts with experience deploying our solutions in organizations of all sizes. If you want to learn exactly how affordable and easy our solution can be, get in touch with us and we’ll customize a quote for your exact needs.