Since most transactions and communication are done over networks today, the security of these networks can’t be overlooked. Securing your network connections has never been more critical, as the data traversing these networks is often sensitive and personal.
The Protected Extensible Authentication Protocol (PEAP) is a foundational component for creating secure network environments. It is a method that ensures data transmitted over a network is done so securely, making it significantly harder for unauthorized parties to access. This article looks at everything you need to know about PEAP.
What is the Protected Extensible Authentication Protocol (PEAP) Protocol?
PEAP, or Protected Extensible Authentication Protocol, is an authentication protocol that enhances security by creating a secure channel between the client and the server. This protocol encapsulates the Extensible Authentication Protocol (EAP) within an encrypted and authenticated Transport Layer Security (TLS) tunnel. Simply put, it’s like adding a protective layer around your network connection, ensuring that only authorized users can access it.
Core Principles of PEAP
PEAP operates within the framework of the IEEE 802.1X standard, enhancing security by employing strong encryption methods to protect the exchange of authentication information. The key principles that form the foundation of PEAP include:
EAP Encapsulation over Transport Layer Security (EAP-TLS)
At its heart, PEAP uses Transport Layer Security (TLS) to create a secure channel between the client and the authentication server. This encrypted channel protects the identity of the user and the credentials being exchanged by encapsulating the EAP conversation within a TLS tunnel.
Server Authentication
An essential principle of PEAP is the mandatory authentication of the server to the client. This is achieved by using a digital certificate on the authentication server, often a RADIUS server, which the client verifies before proceeding. This step ensures that the client communicates with a legitimate server, protecting against man-in-the-middle attacks.
Optional Client Authentication
While server authentication is mandatory, client authentication under PEAP is flexible. Clients may authenticate using a variety of methods, such as secure passwords (MSCHAPv2), digital certificates, or other mechanisms supported by EAP. This flexibility allows for different levels of security and deployment scenarios.
Dynamic Key Generation
Upon successful authentication, PEAP generates dynamic encryption keys, which are used to secure communications over the airwaves in wireless networks or over the physical medium in wired networks. This dynamic key generation adds an additional layer of security by ensuring that keys are not static and are difficult for attackers to compromise.
Protection of Credentials
By encapsulating the authentication process within a secure TLS tunnel, PEAP ensures that the user’s credentials are not transmitted in clear text. This protects sensitive information from being intercepted during the authentication process.
Integration with Existing Authentication Systems
PEAP is designed to work with existing authentication infrastructures, such as RADIUS servers. This allows for relatively easy implementation and integration into existing network environments, leveraging the security benefits of PEAP without requiring significant changes to the infrastructure.
Scalability and Flexibility
The design of PEAP allows it to be scalable to enterprise environments and flexible enough to accommodate various authentication methods and configurations. This scalability ensures that PEAP can be deployed in networks of varying sizes and complexities, from small businesses to large corporations with diverse security needs.
Mutual Authentication
Although client authentication is optional, PEAP supports mutual authentication. When implemented, this ensures that not only the client authenticates the server (to ensure it’s not connecting to a rogue server), but the server also authenticates the client, ensuring that only authorized users can access the network. This two-way authentication adds an additional layer of security.
Session Resumption
PEAP supports session resumption, which allows clients to reconnect to the network more quickly without needing to perform a full TLS handshake again. This feature is especially beneficial in environments where devices frequently disconnect and reconnect to the network, as it reduces the authentication time and improves the user experience.
Compatibility with Legacy Systems
Despite its advanced security features, PEAP has been designed to be backward compatible with older systems and software. This ensures that organizations can upgrade their network security without having to replace all of their existing hardware and software, making PEAP a cost-effective solution for enhancing network security.
How Does PEAP Work?
PEAP operates through a detailed, multi-phase process that combines TLS for secure channel establishment and EAP for user or client authentication following these steps:
- Establishment of TLS Tunnel: Initially, the client and server engage in a TLS handshake. The server presents its digital certificate for client validation, establishing a secure TLS tunnel. This phase ensures encryption and integrity of the subsequent authentication exchange.
- Authentication via EAP: Within the established TLS tunnel, the client then authenticates to the server using one of the supported EAP methods (e.g., EAP-MSCHAPv2, EAP-TLS, or EAP-GTC). This process involves transmitting encrypted authentication credentials from the client to the authentication server.
- Key Material Generation: Upon successful authentication, key material is generated for use in encrypting subsequent communications, ensuring data protection beyond the initial login phase.
- Optional Client Certificate Authentication (for PEAP-TLS): If using PEAP-TLS, client certificate verification occurs, further strengthening the authentication process by providing mutual authentication.
Does PEAP Require a Certificate?
Yes, PEAP requires a server-side certificate to establish a TLS tunnel. This certificate is crucial for the authentication process, as it allows the client to verify the server’s identity. Trust is established when the client validates the authentication server’s certificate. This verification process ensures that the server is legitimate, paving the way for a secure exchange of authentication information.
PEAP Authentication Types
PEAP supports several authentication methods, offering versatility to meet diverse network security needs. The most commonly used types include:
- PEAP-MSCHAPv2: This method is widely adopted due to its compatibility with Windows environments. It uses a two-phase process where the password is first hashed and then sent over the encrypted tunnel.
- PEAP-TLS: This method requires a client certificate, providing a higher security level by using certificate-based user authentication.
- PEAP-GTC: The Generic Token Card (GTC) method, designed to support token-based authentication and other non-password-based methods, offering flexibility especially in systems that require alternative forms of user credentials.
Each of these PEAP authentication types caters to specific security and implementation scenarios, giving network administrators the flexibility to choose the most appropriate method for their network architecture.
It important to note, however, that PEAP-MSCHAPv2 has an increasing number of vulnerabilities due to its reliance on credential-based authentication and compromised hashing algorithm. Many experts, including Microsoft, recommend moving past PEAP-MSCHAPv2 and considering certificate-based authentication.
Setting Up PEAP Authentication
Configuring PEAP authentication within an enterprise network involves several key steps, including:
- Obtain a Server Certificate: Secure a certificate from a trusted CA. This certificate will be used to establish the TLS tunnel that PEAP depends on.
- Configure Your Authentication Server: Install the server certificate on your authentication server. This server will handle user credential verification.
- Select Your PEAP Authentication Method: Decide between PEAP-MSCHAPv2, PEAP-TLS, or PEAP-GTC based on your network security requirements and user credential types.
- Configure Your Network Access Server (NAS): Update your NAS settings to support PEAP. This involves pointing it to your authentication server.
- Set Up Client Devices: Ensure that client devices are configured to trust the CA that issued your server’s certificate, and set them up to use PEAP with your chosen authentication method.
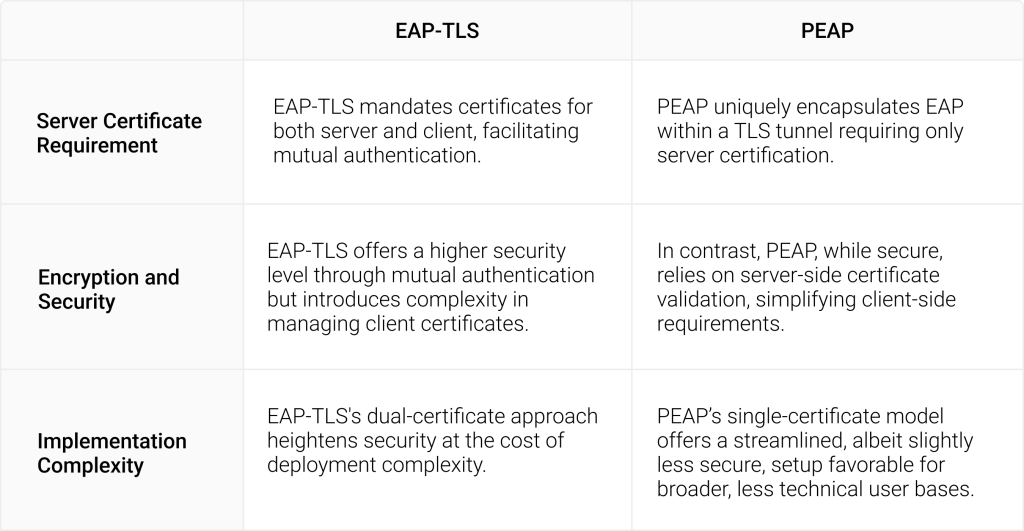
PEAP vs. EAP-TLS
While PEAP and EAP-TLS both aim to provide secure authentication, they go about it in slightly different ways.
Alternatives to PEAP
As network security technologies evolve, so do the alternatives to PEAP. Each alternative comes with its set of features, benefits, and potential drawbacks:
- EAP-TTLS (Tunneled Transport Layer Security): Similar to PEAP, EAP-TTLS creates a secure tunnel for transmitting credentials. However, it allows for the secure transmission of a wider range of credential types, not just those suitable for EAP methods.
- EAP-FAST (Flexible Authentication via Secure Tunneling): Developed by Cisco, EAP-FAST addresses some of the vulnerabilities associated with PEAP and EAP-TTLS by not requiring a certificate for the authentication server, thus simplifying deployment and reducing cost.
Advance Your Network Security with PEAP and EAP-TLS through SecureW2’s Managed PKI and RADIUS Server
PEAP and EAP-TLS form the cornerstone of secure network access, each serving distinct security and implementation needs. Central to these protocols is the role of certificate-based authentication, a domain where SecureW2 excels with its innovative solutions. The platform’s adeptness at leveraging the strengths of EAP-TLS facilitates the seamless issuance, management, and integration of digital certificates.
SecureW2’s Managed PKI offers a robust solution that demystifies the complexity of deploying and managing digital certificates. It leverages the distinct advantages of EAP-TLS, offering a streamlined path toward adopting certificate-based security. For organizations inclined towards the simplicity and broad compatibility of PEAP, SecureW2 simplifies server certificate management, ensuring robust encryption without the overhead of client certificates. Conversely, for entities prioritizing the heightened security that EAP-TLS affords through mutual authentication, SecureW2 aids in the efficient deployment and lifecycle management of client and server certificates.
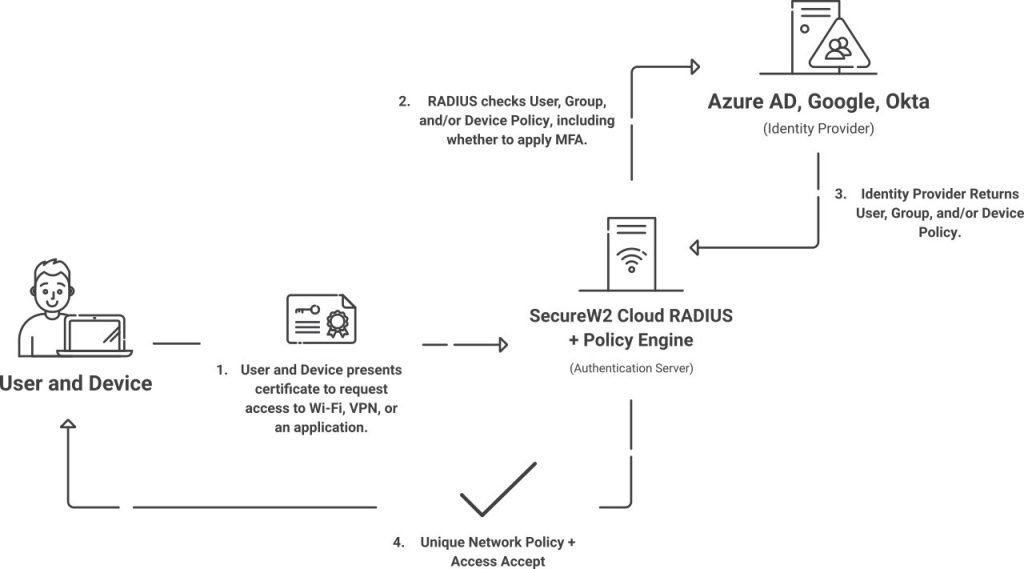
SecureW2 also extends a RADIUS server platform adept at championing passwordless authentication. This platform is not just about authenticating network access requests; it’s about ensuring adherence to the latest network policies through dynamic communication with leading cloud identity providers including Entra ID (Azure AD), Google, Okta, and OneLogin.
SecureW2 is an invaluable asset for organizations keen on harnessing the power of PEAP through streamlined certificate-based authentication. Check out our pricing page to see if our certificate solutions suit your organization.
