Key Points
- Equifax’s 2017 breach exposed sensitive data of approximately 148 million Americans, and could have been prevented with timely patching
- Plaintext credentials and web shells in Equifax’s systems allowed attackers to escalate access and extract personal data with ease.
- Expired SSL inspection certificates blinded Equifax to the ongoing data exfiltration—highlighting the critical need for automated certificate expiration alerts.
On July 29th, 2017, Equifax discovered that data was leaking out of the credit bureau’s databases and had been since approximately mid-May of that year. They publicly reported the incident on September 7th, and it quickly became known as one of the most damaging data breaches in US history.
Information was stolen on approximately 148 million Americans, nearly half the population. The data stolen in the breach includes, Social Security numbers, passport and driver’s license numbers, individual’s names, home addresses and phone numbers, individual’s date of birth, credit card information, tax ID numbers, and many more pieces of vital, personal information.
While the damage from the loss of some of this information can be mitigated, other pieces, such as Social Security numbers, do not change and are particularly dangerous to individuals. The impact of this data breach can potentially affect millions of individuals for their lifetime, and Equifax could have easily avoided this catastrophe if they had followed diligent oversight practices and utilized modern security protocols.
Here we will break down what exactly happened and how you can learn from Equifax’s mistakes.
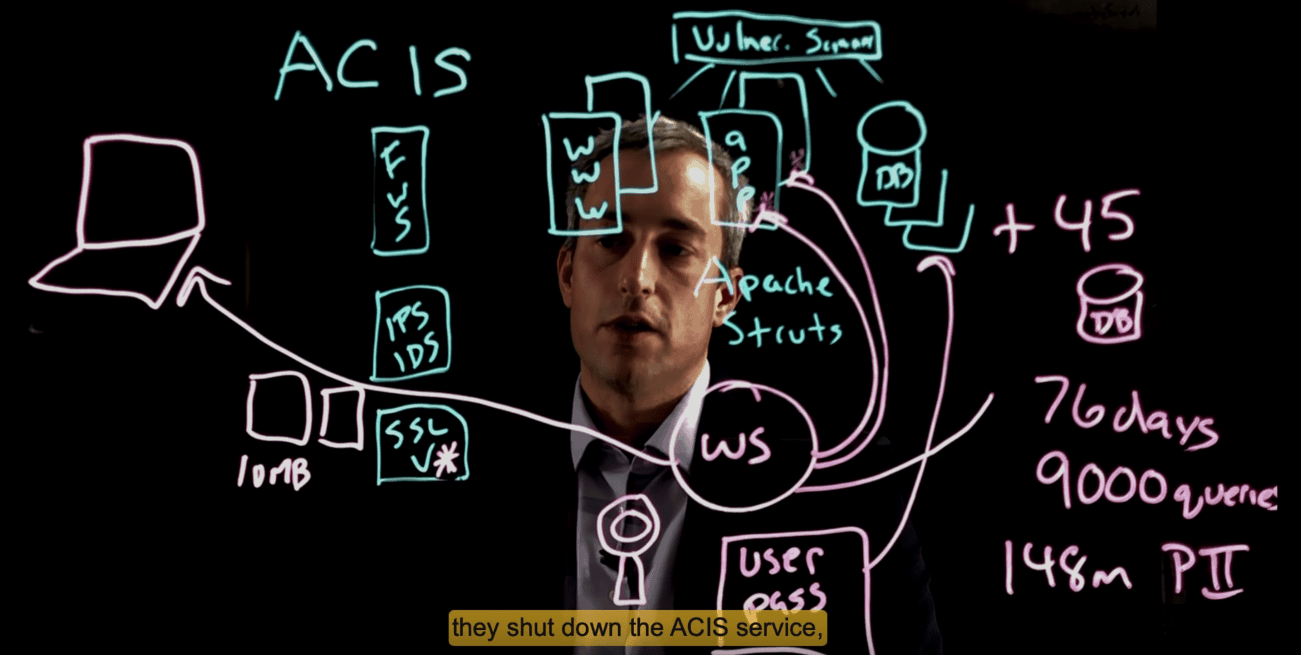
A visual breakdown of the process applied by outside users to access Equifax’s servers and leak citizens’ private information from the Jazz Networks’ video.
Missing Security Patches and Effective Penetration Testing
The attackers were initially able to gain access to Equifax’s network through a vulnerability in Apache Struts. Apache had released patches for this vulnerability they were made aware of in their security system, but Equifax failed to update their servers. The team was made aware of a vulnerability in Apache, but their penetration testing told them this vulnerability was not found on their network.
One of the key tenants of security technology is to diligently watch for patch releases. Patches are vital when released; to fill a hole in the security system that could be a potential avenue for outside users to gain access to your network. They are not optional and any organization utilizing security technology must continually upgrade to experience the benefits they expect.
Additionally, effective penetration testing should be done routinely throughout the organization. Firms such as Digital Silence can be contracted to attempt to penetrate an organization’s network through the same means as an attacker to offer insight and security recommendations to better protect a network. Had their penetration testing been executed properly, they would have realized the urgency there was to update their servers.
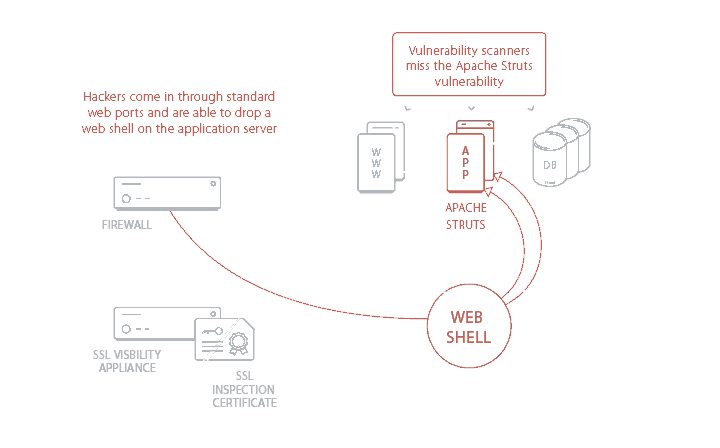
By failing to implement the Apache Struts update, the Equifax team was unaware of an exploitable hole in their cybersecurity.
Common Sense Security
Once the attackers had entered the network, they dropped a web shell (a script that enables remote administration of the machine) and went to work. With the web shell in place, they essentially had full control of the application and used it to locate a file system of usernames and passwords.
The credentials are used to access various servers around the organization and were stored in CLEARTEXT. Cleartext credentials means the information was stored without encryption and could be read as plainly as you are reading this article.
This is the opposite of security. No credentials should be stored in cleartext, especially not credentials used to access the most vital information kept on every American citizen. In the case of a system failure or an unauthorized breach (which happened here) the credentials are easily stolen and immediately usable for malicious purposes.
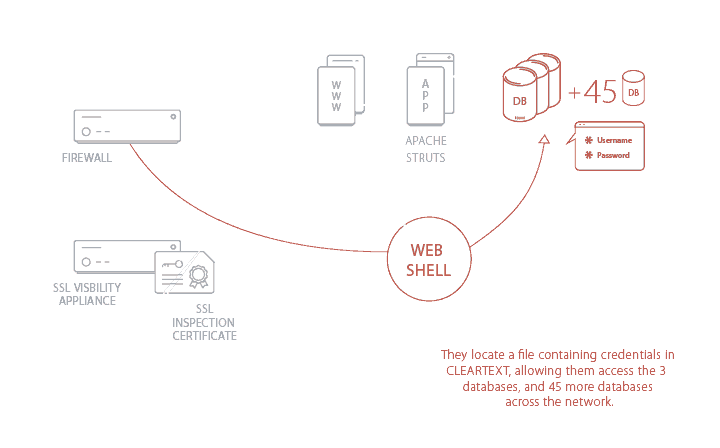
When the attackers uploaded a Web Shell, they discovered a database of Cleartext credentials that allowed them unlimited access to servers containing citizens’ data.
Protecting the Databases
The attackers used the cleartext credentials to access databases containing all the data they would later steal. By protecting their databases with a credential authentication wall, Equifax demonstrated that they deemed the information within the databases sensitive enough to warrant an extra layer of security.
While most organizations do not store as much sensitive data as Equifax, all organizations to contain data that is valuable to attackers. Data such as credit card numbers, personnel information, and financial information is valuable on black markets and a target for outside attackers. If your organization possesses information such as this, stronger security measures should be considered to protect databases.
The Leak, Importance of Certificate Expiration Notifications
Once they had established access to the databases, the attackers slowly began leaking the information out of the network in 10 MB packages. Over 76 days, the information of 148 million Americans was leaked undetected by Equifax.
How did this go undetected? Equifax had SSL inspection certificates which, under normal circumstances, provide visibility that’s required to monitor all the traffic coming in and out of their network. However, their certificates had expired and so they were not performing SSL Inspection. This would have detected the leak very early on and significantly reduced the amount of data leaked. It cannot be said exactly how many Americans would have had their records exposed, but it would have been nowhere near 148 million.
In July, Equifax discovered their SSL inspection certificates had expired and they replaced them, but it was far too late. The new certificate resumed regular SSL inspection and immediately discovered that there was unauthorized leaking of data. Equifax went into breach mode to prevent any more data from being released, but the damage had already been done.
Once again, this highlights the lack of oversight at Equifax and how poorly their security management system performed. There’s no excuse to not diligently check or set alerts of expired certificates. SecureW2 provides a notification system that automatically notifies users and administration when certificates are set to expire. If Equifax had such a system, their SSL Inspection certificate would have been up to date and they would have discovered the data leak immediately.
What Will Change?
In the wake of this massive and damaging breach, many American’s wondered what would happen as a result. New security regulations? Punitive damages against Equifax? Compensation for those whose data was stolen? Unfortunately, meaningful action does not seem to be a likely result at this time.
The Consumer Financial Protection Bureau (CFPB) was tasked with investigating the breach. Initially, the CFPB was moving forward with a thorough investigation, but the new administration brought a change in CFPB leadership in November of 2017. The acting director quickly narrowed the investigation and didn’t seem to be seeking answers. No subpoenas were ordered, no sworn testimony from executives was sought, and on-the-ground tests of Equifax’s security systems were pulled back. A new director has been confirmed by the Senate and took the post in December of 2018, and it is yet unclear if the director will continue with the relaxed nature of the investigation into Equifax or change course and pursue a thorough investigation.
Luckily, the CFPB is not the only ongoing investigator in this case. The Equifax breach is also being investigated by the FTC, the SEC, the DOJ, 48 state Attorneys General, and many class action lawsuits. But nearly 2 years after the leak was discovered, no meaningful results have been produced. There have been no fines levied against Equifax and no changes in regulation of credit bureaus. Equifax CEO Richard Smith retired in the wake of the breach and received a $90 million retirement package. Equifax stock price has nearly recovered to reach pre-breach levels. At its present course, it does not seem likely that meaningful change will result from this breach.
What Can We do to Protect Ourselves?
On an individual level, there are steps you can take to try and mitigate the potential damage if you are concerned that your information was stolen. A short term solution is to freeze your credit and prevent your information from being used to open a new credit account. This is considered a drastic move because it prevents yourself from opening new lines of credit, but it is successful for preventing false credit accounts.
A credit freeze is a short term fix, as you cannot freeze your credit forever. To offer some peace of mind over time, you can practice the following strategies. Credit bureaus offer fraud alerts that monitor and notify you if they detect suspicious behavior, such as setting up a line of credit in a new state. Individuals can request regular credit reports from all three major bureaus and check them for activity that you do not recognize. And lastly, it’s important to scrutinize your monthly credit statements, as credit card information is one of the most commonly sold stolen data on the black market.
Unfortunately, these precautions are all reactionary. You wouldn’t have to scour your statements or freeze your credit if you were confident that your most valuable and basic information was properly protected. But in the online age, politics is rapidly outpaced by technology. New technologies appear at a never-ending pace, especially in the criminal sector. Security patches are released at frequent intervals because people find new ways to exploit systems. In the case of the Equifax leak, the government’s security regulations for credit bureaus was far behind the technology of data thieves. They used un-encrypted credential systems to protect our most valuable data and were not mandated to perform rigorous security checks.
Security professionals are the most well-informed on the risks that weak security systems and poor network management can have on an organization. For a small to midsize business, a data leak frequently leads to substantial financial loss or even the closure of the organization.
Based on the response by the CFPB, it does not seem likely that governments will legislate stronger practices of their own fruition. It’s up to consumers to demand that their information be more secure. Activities such as demanding government officials improve regulations and boycotting companies that do not properly protect your data are steps in the right direction. Your personal information is much more valuable to you than to the credit bureau that maintains databases containing millions of them, it’s vital to remind them that they are not just numbers, but people’s lives.
Protect yourself and your organization form data breaches by laying a good foundation. Click here to learn more about WPA2-Enterprise and how it can keep you safe.