What is a Certificate Authority?
A certificate authority (CA) is an entity that distributes digital certificates to devices. These certificates cryptographically tie an identity to a public key, ensuring that individuals online are who they say they are.
Certificate authorities play an integral role in a PKI and are essential to having a secure network. In this article we will highlight the benefits of a private CA and how to create one for internal use.
What is a Private Certificate Authority?
Private CAs, also known as Enterprise CAs, are self-hosted certificate authorities usually meant for internal use only, such as at a large company or university and for applications such as Wi-Fi, VPN, or Web Application authentication.
While there is little benefit from a software perspective, the benefit that comes from using a private CA is that it limits trust to devices within a given organization. This reduces the potential for a breach as with fewer devices comes fewer failure points.
One downside to a private CA compared to a public CA, is that the infrastructure management and cost fall unto you instead of the usual public CA vendors. Another factor to weigh is only internal devices will trust these CA’s. While this is the entire point of a private CA, it’s important to remember that this is the reason it’s only good for internal applications, and wouldn’t be of much use for external applications like sending an email to someone outside your organization.
Generating Certificate Authorities
While it’s possible to create your own certificate authorities without the assistance of a management system, the process can be a bit convoluted. The process is also different depending on the OS you are using. For example, for MacOS:
- Open a Command Console
- Enter openssl genrsa -des3 -out myCA.key 2048
- When prompted, enter your passphrase
- Generate a Root CA by entering openssl req -x509 -new -nodes -key myCA.key -sha256 -days 1825 -out myCA.pem
- Enter in answers regarding Name, Location, State, Organization, etc.
After completing the steps, you need to install your Root CA on all devices that access your network. To add the Root CA for a MacOS:
- Open the macOS Keychain app
- Go to File > Import Items…
- Select your root certificate file
- Search for whatever your CA name
- Double click on your root certificate in the list
- Expand the Trust section
- Change the When using this certificate: select box to “Always Trust”
- Close the certificate window
- Enter your password.
Following these steps for every device can be overwhelming, especially considering the variety of operating systems potentially in use. It also offers no mechanisms for certificate revocation and management.
Luckily, SecureW2 offers an alternative solution that you can use to create a private CA in minutes. SecureW2’s system also allows you to manage and customize your CA ensuring all your security needs are met.
Generating Certificate Authorities Easily with SecureW2
Many organizations find generating and managing certificates to be a major hassle, however SecureW2’s PKI comes with an easy to use management system that allows certificates to be handled simply and efficiently. Here’s how to create certificate authorities with SecureW2:
Root CA:
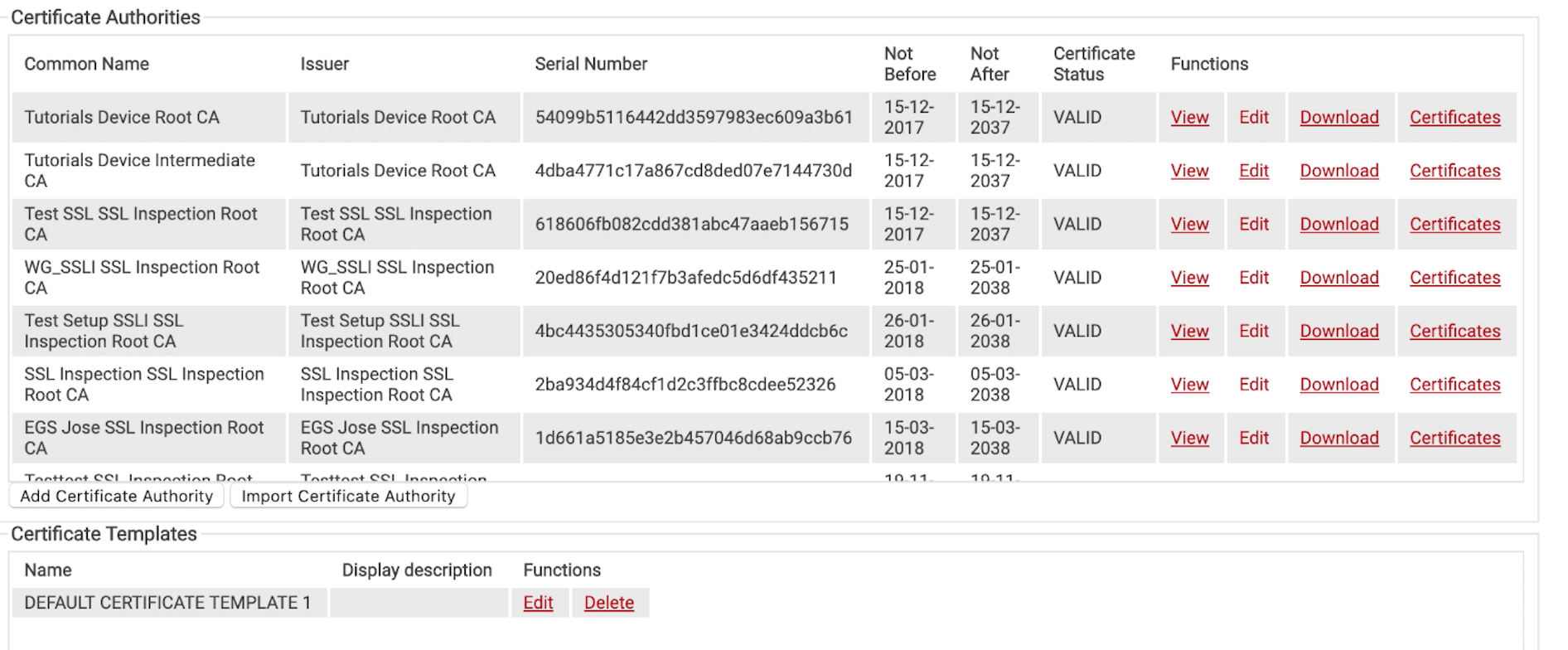
- Under PKI Management select Certificate Authorities
- Select Add Certificate Authority
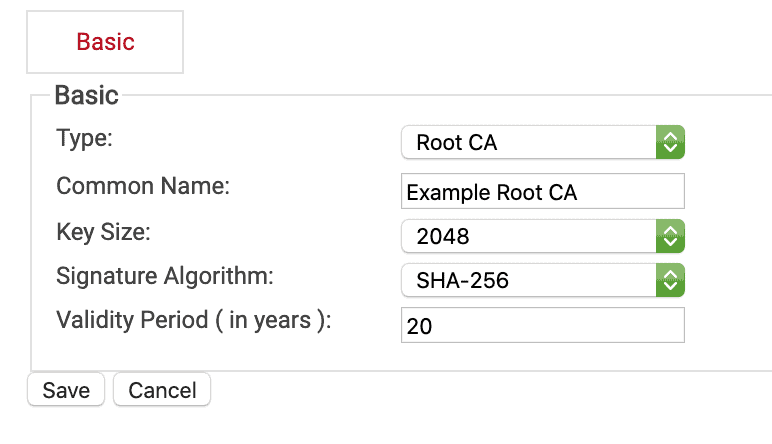
- Choose Root CA under Type
- Choose a name and Save
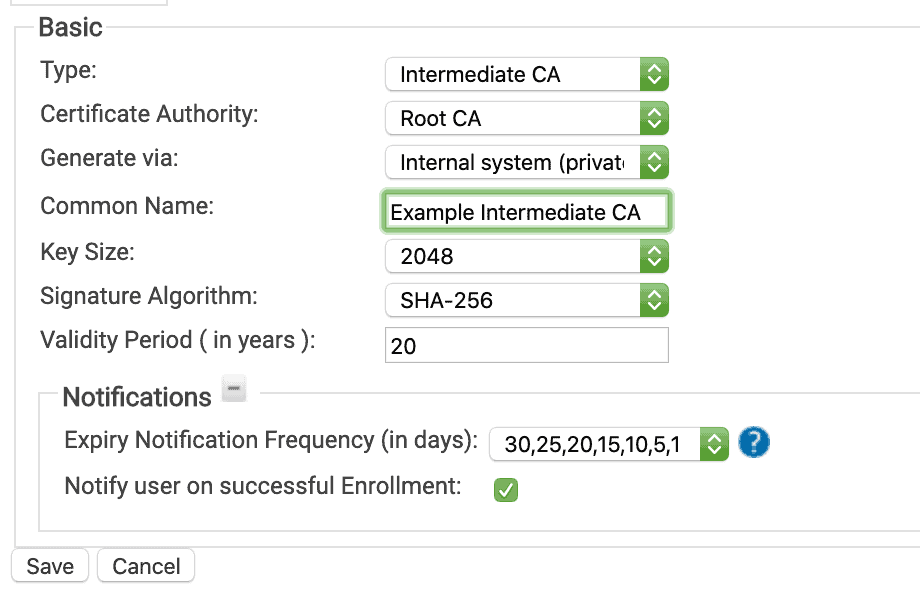
Intermediate CA:
- Under PKI Management select Certificate Authorities
- Select Add Certificate Authority
- Choose Intermediate CA under Type
- Select the corresponding Root CA under Certificate Authority
- Choose your desired setting under Generate Via
- Internal System: The intermediate CA private key and certificate is stored in the cloud. This CA can then be used in the Enrollment policy to sign client certificates
- Certificate Signing Request: Allows administrators to upload a Certificate Signing Request and then get it signed by the Root CA
- Browser: The intermediate CA private key and certificate are not stored in the cloud portal, and are allowed to be downloaded. This CA cannot be used for device enrollment and will be used for SSL inspection
- Choose a name and expiration date then save
Managing your Private CAs and Client Certificates
Using a Managed PKI like SecureW2 also makes it incredibly simple and easy to manage your CAs, and the client certificates generated by them. Not only do you get an easy to use GUI, but many of the management features required for certificate management are already set up for you.
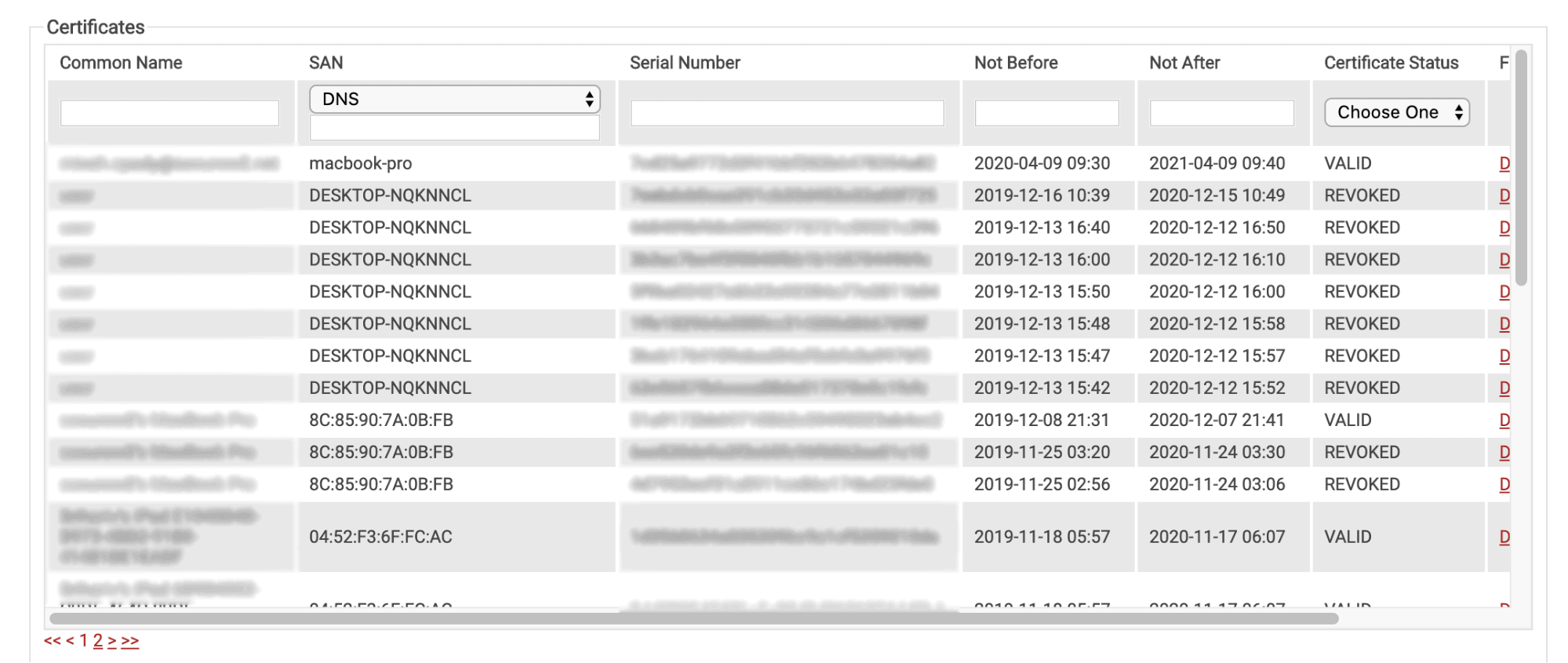
- You can easily sort & search, and individually revoke certificates with SecureW2.
Every CA you generate with SecureW2, automatically generates a Base & Delta Certificate Revocation List (CRL). Every certificate you revoke in the management portal, will be appended to the CRL so you can ensure your network stays safe.
Configuring proper enrollment notifications (shown above in the Intermediate CA settings) is also an essential management tool, especially if your security policies require you to keep certificate validity to a short period!
SecureW2 also allows you to integrate any SAML/LDAP Identity Provider with your Private CA, which makes it really simple to issue certificates. Create robust policies and issue custom certificate templates based on user groups that already exist in your directory. Our Cloud RADIUS can even perform Identity Lookup with Identity Providers, providing another security measure in those critical moments before you know you need to revoke a certificate.
Get Started With Your Own Private Certificate Authority
The process is much more straightforward with SecureW2’s PKI and allows for full customization tailored to your needs. The ability to create and manage certificate authorities is essential for some companies, SecureW2 offers affordable options to meet the needs of any organization, so click here to inquire about pricing.