Key Points
- Azure AD (Microsoft Entra ID) attributes are user and device data fields used to manage identity, access, and policies efficiently.
- Without proper attribute mapping, certificate deployment can be inconsistent, error-prone, and difficult to scale across users and devices.
- Configure AD attributes to automate certificate issuance, enforce group policies, and ensure consistent, secure authentication.
Attribute mapping in Azure AD (Microsoft Entra ID) is easier than you might think. With a simple SAML application, you can use customizable Azure attributes to enforce dynamic policy options on your 802.1X network.
What are Azure AD (Microsoft Entra ID) Attributes?
When a new object (such as a user or device) is provisioned to Azure AD it comes preconfigured with a number of default attributes based on the Azure AD Schema. The values of those attributes are determined by Azure’s synchronization rules.
Customizable attributes and schemas allow you to create “templates” for new objects that streamline the provisioning process. For example, a user assigned the “Marketing” department value can automatically be assigned new properties according to the synchronization rules when they are reassigned to the “Sales” department to reflect their new permissions.
Note: Azure documentation refers to “attributes” and “properties” interchangeably. “Claims” are also related, though they have a slightly different format.
Why use Attributes for Certificate Authentication?
Attributes are a powerful addition to 802.1X authentication because they make it possible to automate group policy and user segmentation.
Using a VLAN to segment your organization into multiple networks of varying permissions is a vital part of the Zero Trust paradigm. There’s no reason that a developer should need access to payroll, nor would an HR employee need to access the organization’s software code. Restricting resources to only the necessary parties limits the amount of damage an intruder can cause if they breach your perimeter.
Below we provided a short video on how easy it can be to attach attributes to your users.
How to Configure Azure Attributes on Digital Certificates
Configuring an X.509 digital certificate to use attributes from your Azure directory can be much simpler than you think. It just requires you to configure a SAML app on Azure and then integrate it into your PKI. For this article, we’ll use SecureW2’s Managed Cloud PKI to illustrate the process.
To configure Azure for attributes on digital certificates via SAML, you will require:
- Azure AD account
- SecureW2 PKI
- Admin privileges for both of the above
- Preconfigured SAML application for Azure
The following is a brief technical overview:
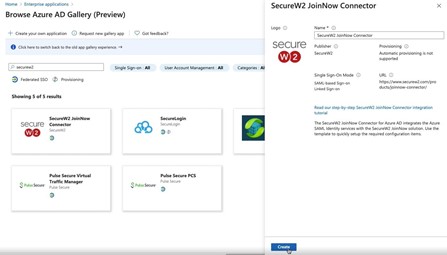
- Integrate Azure IDP with SecureW2 via SAML. In the SecureW2 Management Portal, go to Identity Management > Identity Providers and select “Add Identity Provider”. From the Type dropdown, choose SAML.
- Create Custom Attributes in Azure. Sign into the Azure portal as an admin and navigate to Azure Active Directory under the Azure services menu. Select “External Identities” in the leftmost menu and then choose “Custom user attributes (Preview)”. You can simply push the “Add” button to create a custom attribute.
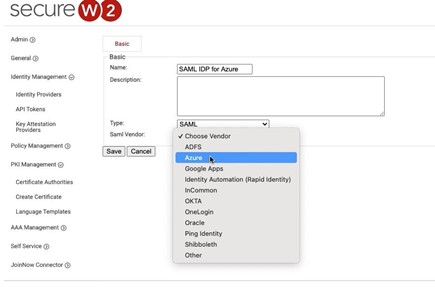
- Recreate Custom Attributes in SecureW2 Management Portal. In the Identity Provider tab, select the SAML IDP for Azure you configured in the first step. Choose the “Attribute Mapping” tab and fill out the fields so that they are identical the the attributes you created in Azure.
What Attributes are Required for RADIUS Authentication?
At minimum, to authenticate to a RADIUS server you will need a Short Alternative Name (SAN) attribute attached to your certificates. For most users, it’s a User Principal Name (UPN), which is usually an email address. Machines just use a Domain Name System (DNS) attribute.
In practice, of course, an object will have many more attributes attached to it. This single-attribute configuration is useful for troubleshooting RADIUS connectivity issues, however.
What Attributes are Required for Wi-Fi Authentication?
The simplest Wi-Fi authentication configuration only requires 3 attributes:
- UPN / DNS
- DisplayName
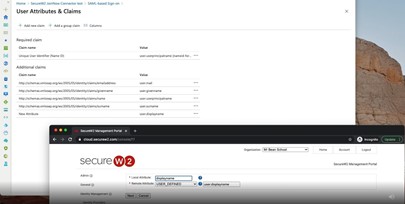
Here’s an excerpt from our documentation that illustrates these Azure attributes configured properly in the SecureW2 Management Portal.
 Implement True Passwordless Azure Authentication with Attributes
Implement True Passwordless Azure Authentication with Attributes
SecureW2’s Azure integration is the industry’s first solution for totally passwordless authentication with cloud directories. Digital certificates equipped with comprehensive attributes and a robust security policy create a network that is both more secure and a better user experience, all while being easier to manage.
Utilize your Azure environment to the fullest extent with Azure attributes for policy enforcement. We have affordable solutions for organizations of all sizes. Click here to see pricing.