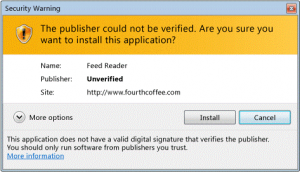
Imagine you’re installing an application and a pop-up like the screenshot above comes up. How can you be sure that the application you’re about to download is really safe?
The answer is code signing certificates, which attest that the software package has not been tampered with or replaced with a modified version. It’s a virtual tamper-proof seal that verifies the code is the authentic original version, preventing scenarios where a bad actor might upload an infected version of a common application.
In addition to protecting users from accidentally downloading viruses, code signing certificates prevent security warnings, like the one above, from stifling the user experience. SecureW2 offers a turnkey PKI solution with #1 rated certificate delivery so you can take advantage of code signing certificates. Learn from one of our customers how easy our PKI solution is to configure.
In this article, we’ll take a closer look at code signing certificates and explain how they work and why they are so important.
Understanding a Code Signing Certificate
Code signing is done by putting a digital signature on an executable, software update, or file. The certificate confirms that the program has not been tempered and the software is safe for download.
You can think of it as a wax seal on an envelope. If the seal is intact, you can be certain that the letter hasn’t been modified with or replaced by an outside source. Apple developers use code signing to prove, for instance, that your macOS update actually came from Apple, and not a hacker who is trying to compromise your computer.
All major operating systems and browsers and OSs support code-signing software.
How Does Code Signing Work?
In order to understand code signing, first, you need to understand what a PKI is.
The purpose of a Public Key Infrastructure (PKI) is to create and manage public-private key pairs (in the form of X.509 digital certificates) used by the network for identity management and access control.
A PKI allows users and systems to verify the legitimacy of certificate-holding entities and securely exchange information between them over the air. The introduction of a PKI enables the use of code signing certificates through public-key encryption.
The process for code signing is as follows:
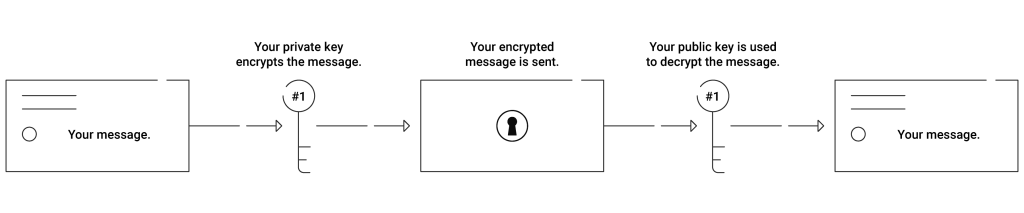
- A developer uses a PKI (like SecureW2) to add a digital signature to a code signing certificate.
- A user has a public key that is used to decode the signature. The user’s software or application decodes the signature using the key.
- Then software searches for a root certificate with a verified identity to validate the applied signature.
- The software system then applies a hash to the download of the application and another hash to sign the code.
- If the root and hashes match, the download continues.
- If the root and hashes do not match, the download will be interrupted and shows a warning.
Code signing is commonly used by app developers so that users downloading an application can rest assured that it’s safe. In fact, major app distribution platforms such as Apple’s App Store and the Google Play Store require apps on their platforms to be code signed.
However, the practice isn’t just limited to app development; code signing is also utilized by IoT manufacturers and by people working on operating systems. Really, any time you have an executable, you can use the code signing process to create a tamper-evident seal for your end users.
Benefits of Code Signing Certificates
Using code signing certificates is a must if you want to maximize user experience and security. The benefits are the following :
- Validating Code Integrity
- Enhancing Legitimacy
- Integration with All Major Operating Systems
Validates Code Integrity
Code signing provides an integrity check of the code by validating it with a hash function. The hash function is used at the source to sign the code and the same hash has to be matched at the destination. This provides the user with proof that the code has remained unchanged.
Enhancing Legitimacy
When users download a piece of software and are immediately issued a warning by their operating system, it can ruin the mood a little bit. Users need to be able to trust your software if you want them to continue to be your customer, and an untimely warning can damage that trust.
Code signing certificates indicate to an OS that the source is legitimate, bypassing security flags and facilitating a smooth user experience. allow your customers to trust in your software and bolster your public reputation.
Integration with All Major Operating Systems
Code signing processes are encouraged by all major platforms such as Apple iOS, Windows, Linux, Android, JAVA, Adobe AIR, etc. The partners, channels, and platforms that distribute your software expect you to safeguard their customers’ data. Signing software shows your commitment to their safety and is often a contractual requirement.
Best Practices with Code Signing Certificates
Implementing code signing certificates in your development process is a step in the right direction. However, there are additional considerations to make to enhance both your security and peace of mind, as well, such as the following:
- Protecting your keys with an HSM (hardware security module)
- Enforcing policies and up-to-date security practices
- Keeping and checking auditing logs regularly
Protect your keys with an HSM.
We’ve discussed briefly what a PKI is, and the merits of having one, but it’s important to mention that PKIs are even better when they’re protected with their own security measures. The gold standard for safeguarding your PKI is a hardware security module, also known as an HSM.
In a nutshell, an HSM is a secure physical device that can operate cryptographic functions. Because they have extremely limited network access and they are themselves protected by a firewall, HSMs are tamper-resistant, highly effective guardians for PKIs.
A wise practice is to host your root Certificate Authority offline, then protect that root CA with an HSM. If this sounds more trouble than it’s worth, the good news is that SecureW2’s managed PKI already comes backed with an ultra-secure HSM.
Enforce network policies and utilize up-to-date security practices.
Your security tools are only as good as the rules you frame them with. Even if you have a high-end lock, it’s only useful as a decoration if you leave it open all the time or hand out keys to everyone indiscriminately.
In other words, build and enforce strong policies around your certificate use. One excellent practice is to support authentication within your organization with a RADIUS server. RADIUS servers basically act as bouncers on your network, checking users’ identities at the “door” when they attempt to authenticate.
Some RADIUS services, including our own Cloud RADIUS, can interface directly with your identity provider (IDP) to verify information regarding different groups of users. For example, you could use Cloud RADIUS to authenticate certificates for users on your software development team, putting them on their own VLAN or prioritizing bandwidth for them. You could even accept or deny users based on the time of day.
This may not apply directly to code signing, but it’s important to consider, anyway. Your end users can trust your organization much more when they understand that you take security seriously.
Keep and check audit logs regularly.
Event logs are critical to any network’s security. Keeping them isn’t enough, though – you also need to check them regularly.
In the event a breach does occur in your organization, a detailed event log can help you pinpoint what caused it. Checking your logs frequently in advance can also help you prevent any security issues from worsening – much like treating an illness the moment symptoms appear.
This is why our Cloud RADIUS comes with detailed event logging. When users attempt to authenticate to your network, whether they’re granted or denied access is immediately logged for your network administrators. We strongly encourage our customers to reference these logs to ensure the health of their network.
How Do I Get a Code Signing Certificate?
There are a couple different ways you can go about acquiring a digital code signing certificate. The first method is to simply purchase the certificate directly from a reputable Certificate Authority. Unfortunately, these individual certificates can be expensive, so purchasing more than one isn’t the most economical plan.
If you want a much more scalable option, the alternative is to implement your own organizational PKI. As we’ve mentioned previously, however, building and maintaining your own PKI is a hassle. Without the proper expertise, the chances of misconfiguration are high, and hiring the expertise if you don’t already have it is costly.
This is where managed PKIs (MPKIs), like SecureW2’s JoinNow Connector PKI come into play. An MPKI takes all the frustration out of maintaining a PKI. You don’t need to build one from scratch, you eliminate the risk of misconfiguration, and the expertise required for maintenance is provided for you.
Once you’ve established a PKI, you can issue certificates as necessary without having to pay astronomical fees for each one. An important factor to keep in mind, however, is who the end-user is for the code you are signing.
The cornerstone of digital certificates and PKIs is trust. Trusting a certificate requires trusting its source first. If you use your own internal PKI to issue a code signing certificate to an app you have in the app store, the odds of a random end-user outside your organization trusting the Certificate Authority that issued your certificate are nonexistent.
Thus, using your own internal PKI to issue as many code signing certificates as you need is an excellent solution if you need to sign your code for others in your own organization. However, when it comes to creating applications that will be distributed externally, you’ll probably need to stick with using a certificate issued by a public CA that is more widely trusted outside your organization.
Do I Need a Code Signing Certificate?
While you don’t absolutely need a code signing certificate to code and release applications, being able to sign code is important to gaining the trust of your end users (and their devices!). Certificates simply present the best method for doing so.
With a certificate, the code signing process is simple. Additionally, the peace of mind end-users will gain is priceless.
Types of Code Signing Certificates
There are two types of code signing certificates — OV or standard code signing certificates and EV code signing certificates.
OV Certificates confirm the existence of the organization. To get an OV certificate, a company must complete the validation process. During validation, the certification center must ensure the legal and physical existence of the company.
EV Certificates offer the same solution as an OV certificate, but EV code signing keeps the private key secret using a hardware token whereas in regular code signing the private key is not provided in a separate external drive.
In general, both offer the same thing: signing software, scripts, drivers, or any other executable files using x.509 based certificates that are attached to a trusted root. EV certificates just have a more rigorous protocol behind them. A benefit of this is that an EV code signing certificate offers an immediate reputation with Microsoft SmartScreen, so your users will never have to click through a SmartScreen warning in Windows.
Can SSL Certificates Be Used for Code Signing?
An SSL certificate is a certificate that promotes secure, encrypted connections between servers hosting websites and the clients that visit those sites. The certificate verifies that the host server is valid, and then the end-user is able to safely connect through HTTPS.
At their core, certificates perform the same basic function: proving someone or something’s identity. Both code signing and SSL certificates do this, so does that mean they can be used interchangeably?
Unfortunately, the answer is no. Certificates are each designed for a specific use case and are encoded with attributes for that purpose. Attempting to use an SSL certificate for the code signing process will just result in an error.
What is the Difference Between a Signing and Encryption Certificate?
Understanding the difference between encryption and signing requires an understanding of some technical information security concepts. We’ll give you a quick runthrough.
Encryption is a process related to the concept of confidentiality. When a set of data is encrypted, it is basically protected from third party observation. There are two types of encryption: symmetric and asymmetric.
Digital certificates use asymmetric encryption, which is also known as public key cryptography. We could go on about public key cryptography at length, and we have existing guides on the topic if you want more detailed information. Put simply, however, public key cryptography uses a public key that is freely distributed and a private key kept secret by the holder.
This functionality makes it possible for these certificates to be used for signatures. Just as people can encrypt messages with the public key that can be decrypted by the private key, so can the private key’s holder encrypt messages that can only be decrypted with the public key. Because the public key can decrypt the message, it’s safe to assume that it can only have come from the appropriate private key.
In other words, digital certificates function as both encryption and signing mechanisms. As we mentioned previously, however, exactly what they are being used to encrypt or authenticate varies.
Do Code Signing Certificates Expire?
Generally, certificates are only good for a certain period of time, and that includes code signing certificates. A certificate wouldn’t be the best authentication method if it was valid indefinitely – just like using the same password forever isn’t exactly secure.
The exact lifespan of your code signing certificate will vary depending on how you acquired it. Different certificate authorities offer various life cycles for their certificates. These certificates tend to be valid for a couple of years.
The problem is that applications are often used for more than a couple of years. You can code-sign an application with a certificate that expires after two years, but people may still be downloading your application several years later. How do those people know that your code hasn’t been tampered with since the expiration of the certificate?
The answer to that question is timestamp counter signatures. If you’ve gotten your code-signing certificate from a public CA, you can also request a signed timestamp that includes the current date and time from that CA. In the future, when the end-user checks the signature, they can see the original certificate and the time stamp that confirms that the certificate was “in date” when the timestamp was administered.
If you’re using our JoinNow Connector PKI to generate code signing certificates, you’ll have the ability to choose the length of time the certificate is valid for. You can even designate a particular date for expiration if you choose. Remember, however, that as far as code-signing is concerned, this setup works only for internal use, where you can ensure that employees and devices in your organization trust your own CA.
Code Signing Certificates With SecureW2
Code signing certificates, as well as certificates for other use cases, are an essential part of software development and a way to prove your commitment to security to end-users, but making sure you have the proper tools to utilize them internally is paramount to success.
In the past, IT professionals have chosen to avoid implementing certificates because the thought of managing a PKI was too big a hassle. With SecureW2’s PKI solution, you get everything you need to secure your network, without any of the usual headaches like massive infrastructure changes or lengthy deployments.
Besides being vendor-neutral and able to integrate with your existing infrastructure, using our managed PKI service can save you the expenses involved with building your own PKI from scratch. We provide you the PKI with no need for costly on-prem infrastructure or the need to hire additional personnel with PKI experience. Take a look at our pricing yourself and see just how affordable our secure managed PKI can be.