Key Points
- Certificate Authorities (CAs) offer digital certificates that provide trust and security for online transactions, including SSL certificates, VPNs, and application security.
- CAs provide a chain of trust, providing safe communications and avoiding fraudulent activities by authenticating the legitimacy of the enterprises requesting certificates.
- SecureW2's cloud-based PKI solution simplifies digital certificate management for various security requirements.
Imagine walking into a vast library, seeking a single book among millions. Without a librarian or a catalog system, you’d be lost. In many ways, the internet is that library, and a certificate authority is the librarian guiding us to the websites and services we can trust. They are the cornerstone upon which the edifice of digital security is built.
In this article, we’ll explore the concept of certificate authorities, what they do, and how your organization can leverage them to improve the security of your network and resources.
What is a Certificate Authority?
A Certificate Authority is an entity responsible for issuing SSL certificates and other types of certificates, such as those used for client authentication or code signing. These certificates authenticate the identity of websites and other entities on the internet or on private networks, much like how a passport or driver’s license authenticates your identity in the real world.
But there’s more to CAs than just issuing certificates. They play a crucial role in creating a secure and trustworthy online environment. When you enter your personal or financial information on a website, you’re trusting that site to safeguard your data. A certificate authority acts as a trusted third party, by verifying the identities of these websites. If a site has a certificate issued by a recognized CA, it’s like having a seal of approval, assuring users that their data is in safe hands. The versatility of digital certificates issued by CAs extends beyond secure web browsing, playing a critical role in Wi-Fi authentication, VPN access, application security, code-signing, and even facilitating secure desktop logins with smart cards.
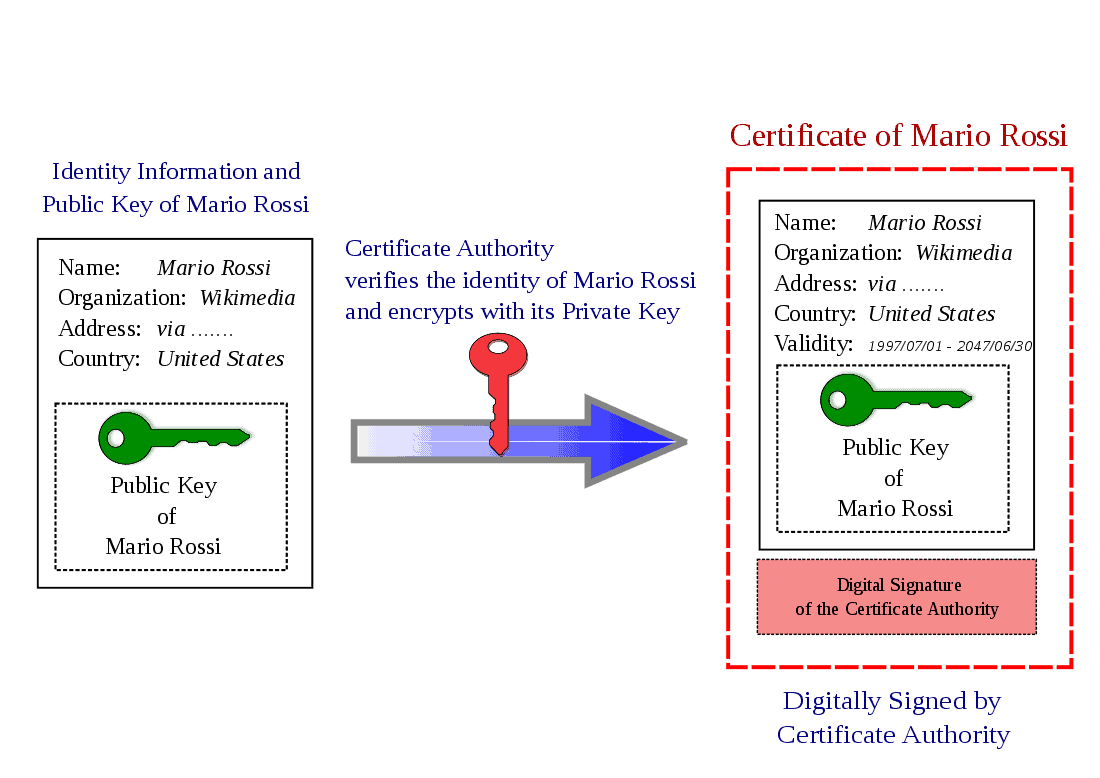
- Source: en.wikipedia.org/wiki/Certificate_authority
How do Certificate Authorities Work?
Certificate Authorities uphold the trustworthiness and ensure the safe exchange of information by providing the critical functions of verifying identities, issuing digital certificates, and managing these certificates’ lifecycles. By validating the authenticity of entities seeking digital certificates, CAs act as trusted third parties, ensuring that only credible and legitimate entities receive certificates. This verification and authentication process is vital in establishing a secure digital environment, effectively minimizing the risks of impersonation and fraud.
CAs are responsible for issuing various types of certificates, including SSL/TLS certificates for secure web browsing and code signing certificates that affirm the authenticity of software. Beyond issuance, CAs also oversee the entire lifecycle of a certificate—encompassing renewal, suspension, and revocation—thereby maintaining the ongoing integrity and reliability of encrypted communications.
Why Do We Need a Certificate Authority?
Imagine a world without any form of identification. Chaos, right? Without CAs, the internet would be a wild west of security threats, with rampant phishing attacks and data breaches. CAs instill a level of trust and confidence, essential for secure online transactions and communications.
Digital Certificate Use Cases and Versatility
The Trust Hierarchy
While SSL certificates are well-known for establishing secure web connections, digital certificates extend their utility far beyond, providing security solutions for a variety of platforms and purposes. Apart from the SSL certificates, digital certificates are essential for:
- Wi-Fi Authentication: Certificates secure Wi-Fi connections, ensuring that access is granted only to authenticated users or devices.
- VPN Authentication: They provide a secure method for validating user access to Virtual Private Networks, enabling remote work with confidence.
- Application Security: Digital certificates authenticate software and applications, guaranteeing their integrity and origin.
- Code-signing: This use case ensures that the code has not been tampered with since being signed, fostering trust in software distribution.
- Desktop Logins with Smart Cards: A digital certificate stored on a smart card can authenticate a user to a system, offering a higher security level than traditional passwords.
Types of Certificate Authorities
Certificate Authorities are responsible for issuing various types of digital certificates, including SSL certificates, which are critical for secure internet browsing. There are several types of Certificate Authorities, each serving specific roles within the digital security ecosystem:
Root Certificate Authorities
Root CAs are at the top of the digital certificate hierarchy. They are trusted entities that issue digital certificates to Intermediate CAs or, less commonly, directly to end entities. Root CAs have their self-signed certificates that are embedded in web browsers and operating systems, establishing a chain of trust. When a web browser or device recognizes a root CA’s certificate, it trusts all certificates issued by that CA.
Intermediate Certificate Authorities
Intermediate CAs serve as a bridge between the root CA and the end entities (such as websites). They are issued certificates by the root CA, which they use to sign the certificates of end entities. This multi-layered approach enhances security by minimizing the risk associated with directly exposing root CAs to the public internet and by allowing for revocation of compromised intermediate certificates without affecting the root CA.
Public Certificate Authorities
Public CAs are entities that issue certificates to the public. They can either be root CAs or operate under the authority of a root CA as intermediaries. Companies like Let’s Encrypt, Comodo, Symantec, and DigiCert are examples. They offer a range of certificates catering to different levels of authentication, including:
- Domain Validation (DV)
- Organization Validation (OV)
- Extended Validation (EV)
Private Certificate Authorities
Private CAs are internal to an organization and not trusted by devices and browsers outside the organization’s domain. They are used to issue certificates for internal servers, user authentication, email encryption, and secure communication within an organization. Because they operate within a controlled environment, private CAs allow organizations to manage their security policies and certificate lifecycle closely.
There are many private Certificate Authority companies and services available today that make it simple to deploy your own CA. SecureW2 is a private Certificate Authority service that empowers organizations to create as many CAs and manage the entire certificate lifecycle from a single pane of glass.
Self-Signed Certificate Authorities
While not formally CAs, entities can issue self-signed certificates, where the certificate’s issuer is also the certificate’s subject. Primarily used for testing, development, or internal applications, self-signed certificates are not verified by an external CA and, therefore, not inherently trusted by web browsers or operating systems. Users often have to manually accept or install the certificates to bypass security warnings. Self-signed certificates provide a basic level of security for internal communications but are not suitable for public-facing applications where trust and authentication are critical.
Specialized Certificate Authorities
Some CAs serve specific niches or industries. For example, government or military organizations may have their dedicated CAs for internal and secure communications. Healthcare industries might also rely on specialized CAs that comply with industry-specific security standards and regulations. These CAs provide tailored services and certificates that meet the unique requirements and trust models of these sectors.
Cross-Certified Certificate Authorities
Cross-certification is a process where two or more CAs exchange certificates with each other, thereby extending trust among themselves. This method allows entities that hold certificates from one CA to be trusted by another CA without needing direct certification from the latter. This practice is useful in environments where interoperability between different security domains or trust networks is necessary.
Cloud-Based Certificate Authorities
As organizations move more services to the cloud, some CAs have begun offering cloud-based certificate management services. These CAs provide a scalable, flexible, and often automated environment for managing the lifecycle of digital certificates. They cater to organizations that prefer cloud-first strategies, providing seamless integration with other cloud services and ensuring secure communications across cloud-based resources.
All these Certificate Authority providers can be public or private. SecureW2, for example, offers a cloud-based private Certificate Authority platform. However, regardless of the type, the underlying principle of CAs—establishing trust through verification—remains constant across various applications, from securing internet transactions to authenticating internal networks and software within organizations.
What is a Certificate Chain of Trust?
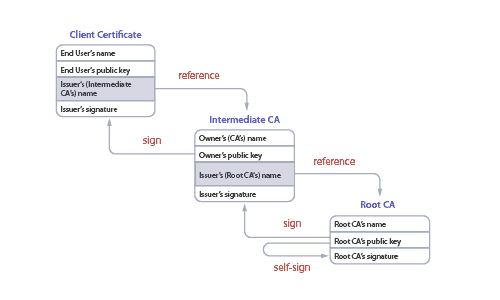
A certificate chain, often referred to as a trust chain, is a sequence of certificates that enables a recipient to verify the trustworthiness of a digital certificate presented to them. Imagine it as a linked chain where each link represents a certificate, starting from a trusted root certificate authority, through one or more intermediate CAs, and ending with the end-entity (or leaf) certificate used in secure communications. The root CA is the most trusted link in this chain, installed and pre-trusted in web browsers and operating systems. Intermediate CAs, authorized by the root CA, extend this trust to end-entity certificates, which websites use to establish secure connections with users.
The certificate chain’s purpose is to establish a path of trust from a known, trusted entity to an unknown entity, ensuring that each certificate is signed by the entity directly above it in the chain. When a user’s device checks this chain, if each certificate is valid and correctly linked back to a trusted root CA, the end-entity certificate is considered trustworthy. This intricate system underpins secure communications on the internet, ensuring users can trust the authenticity of websites and services they interact with.
The Hierarchical Structure of the Certificate Chain
The certificate chain is structured hierarchically, ensuring that each link in the chain is trustworthy. The hierarchy typically includes:
- End-Entity Certificate: This is the certificate used by the website or service you connect to. It contains the public key and identity information of the entity and is signed by an Intermediate CA.
- Intermediate Certificates: These certificates act as a bridge between the trusted root CA and the end-entity certificates. There can be one or more intermediate certificates in the chain, forming layers of trust. Each intermediate certificate is signed by the authority above it in the chain.
- Root Certificate: The topmost certificate in the chain is the root certificate. It is self-signed by the root CA, which means it is its own issuer. Root certificates are included and trusted by web browsers, operating systems, and applications.
How Does a Certificate Chain Work?
The process of verifying a certificate chain is akin to connecting the dots back to a source you trust. Here’s how it works:
- Starting at the End-Entity Certificate: When you visit a secure website (https), the site presents its end-entity certificate to your browser.
- Verification of the Issuer: The browser checks if the end-entity certificate was issued by a trusted CA. It does this by looking at who signed the certificate (the issuer) and then attempting to locate the issuer’s certificate on your device or in its own store of trusted certificates.
- Walking Up the Chain: If the issuer’s certificate is an intermediate certificate, the browser then looks for who signed the intermediate certificate, moving up a level in the chain. This process continues until the browser reaches a root certificate.
- Root Certificate Recognition: The final step is the recognition of the root certificate. Root certificates are pre-installed in web browsers, operating systems, and mobile devices. If the browser recognizes the root CA as trusted, then the entire chain is trusted, ensuring that the website or service you are interacting with is verified and trustworthy.
This trust model ensures multiple layers of security. Requiring the endorsement of a root CA—via intermediate CAs—for an end-entity certificate adds depth to the verification process, making it more challenging for malicious actors to impersonate or create fraudulent sites. Moreover, the certificate chain mechanism enables the flexibility of trust. Since root CAs are universally recognized and trusted entities, having a chain that connects an end-entity certificate to a root CA allows for widespread trust. However, if an intermediate certificate is compromised, it can be revoked without undermining the integrity of the root CA or other chains that share the same root.
The verification process, while complex, is primarily transparent to the user. Web browsers automate this process, providing users with a seamless and secure browsing experience. When there’s an issue with the certificate chain—such as an expired certificate, a missing intermediate CA, or a break in the chain—the browser will warn the user, indicating that the site may not be secure. The verification of SSL certificates is part of this trust model, ensuring that when you visit a secure site, the SSL certificate presented is trustworthy.
The Connection Between Certificate Authorities and PKI
Public Key Infrastructure (PKI) serves as the framework for managing encryption keys and digital certificates, ensuring secure communications and transactions over the internet. At the heart of PKI are Certificate Authorities, which play a pivotal role in the ecosystem. The relationship between CAs and PKI is foundational, with CAs ensuring the integrity and trustworthiness of the PKI through:
- Issuance and Management: CAs are responsible for issuing digital certificates to entities after verifying their identities. This process involves generating a public-private key pair, where the private key is kept secret by the entity, and the public key is embedded in the digital certificate issued by the CA. Within the PKI framework, Certificate Authorities’ issuance and management of SSL certificates are key to enabling secure electronic communications over the internet.
- Trust Anchors: In PKI, root CAs act as trust anchors. Their self-signed certificates are pre-installed in web browsers and operating systems, establishing a baseline of trust for all other certificates issued within their hierarchy.
- Revocation: CAs maintain certificate revocation lists (CRLs) or use the Online Certificate Status Protocol (OCSP) to disseminate information about revoked certificates. This ensures that compromised or invalid certificates can be quickly identified and no longer trusted.
SecureW2 Cloud-Based PKI for Your Organization’s Passwordless Security Needs
SecureW2’s Cloud-based Public Key Infrastructure (PKI) is designed to address a wide range of security needs effectively. From ensuring Wi-Fi and VPN authentication to bolstering application security, facilitating code-signing processes, and enabling secure desktop logins via smart cards, SecureW2 simplifies the management and deployment of digital certificates across various use cases. This versatility is important to address diverse and intricate security needs.
Leveraging cloud technology, SecureW2’s solution offers a scalable and flexible platform that integrates seamlessly with existing IT infrastructures. Organizations can deploy a fully functional PKI without the need for extensive in-house expertise or the hardware necessary for traditional setups. This approach not only reduces operational costs but also accelerates the deployment of secure and trusted digital certificates for a myriad of applications beyond traditional web security.
While SecureW2 is adept at managing SSL certificates for web server security, its cloud-based PKI and RADIUS solution encompasses a far broader spectrum of digital security needs. SecureW2 manages the entire lifecycle of certificates—from issuance to renewal and revocation—ensuring that encryption keys and digital certificates remain secure and up-to-date. Its ability to integrate with existing directory services for automatic certificate enrollment, along with support for a wide range of devices and applications, underscores its effectiveness in enhancing digital security across the board.
Schedule a free demo today and see how SecureW2’s offerings can empower your organization’s diverse security needs with its comprehensive, cloud-based PKI solution.