Key Points
- WPA-Personal's dependence on TKIP encryption and shared passwords makes it susceptible to various attacks.
- Certificate-based authentication with EAP-TLS provides a secure, password-free alternative to Wi-Fi security.
- Secure your Wi-Fi network using SecureW2's cloud PKI and RADIUS solutions for reliable security.
In the continuous effort to strengthen wireless network security, Wi-Fi Protected Access (WPA) represents a significant turning point. Data transmission over airwaves is becoming increasingly common in the ever-expanding digital connection landscape, making transmission security critical. WPA was created in response to the flaws discovered in its predecessor, Wired Equivalent Privacy (WEP). With its strong encryption and authentication methods, WPA brought much-needed upgrades to Wi-Fi networks, ushering in a new age of improved security.
An essential subject of interest in WPA is WPA-Personal, sometimes referred to as WPA-PSK (Pre-Shared Key). Knowing the nuances of WPA-Personal and how it affects contemporary network security is crucial as people and organizations attempt to protect their Wi-Fi networks from ever-changing threats. In this article, we explore the depths of WPA-Personal, dissecting its internal mechanisms, examining its weaknesses, and considering how to improve Wi-Fi security.
Evolution of WPA (Wi-Fi Protected Access)
WPA was designed by the Wi-Fi Alliance to serve as a stand-in for WEP while the whole IEEE 802.11i standard was made available. WPA might be deployed by upgrading the firmware of wireless network interface cards built for WEP, which began arriving in 1999. Unfortunately, most pre-2003 APs (Access Points) could not be modified to enable WPA because the modifications needed in the wireless access points were more comprehensive than those on the network cards.
The WPA protocol uses the Temporal Key Integrity Protocol (TKIP). On wireless access points and devices, WEP uses a 64-bit or 128-bit encryption key that needs to be manually inputted and never changed. Because TKIP uses a per-packet key, it prevents attacks that undermine WEP by dynamically generating a new 128-bit key for every packet.
A Message Integrity Check is another feature of WPA that keeps an attacker from changing and resending data packets. This replaces the WEP’s standard’s cyclic redundancy check (CRC). The primary shortcoming of CRC was that it did not offer a robust enough data integrity guarantee for the packets it processed. There were tried and tested message authentication codes to address these issues, but they were too complex to utilize with outdated network devices. WPA checks the integrity of the packets using a message integrity check method known as TKIP. While TKIP is not as robust as the WPA2 algorithm, it is still far better than a CRC. Since then, researchers have found a flaw in WPA that depends on earlier WEP vulnerabilities and the limits of the Michael hash function. This function recovers the keystream from short packets for spoofing and re-injection.
Understanding WPA Personal (WPA-Pre Shared Key)
This mode is suitable for most home networks. Users must input a password specified on a wireless router or access point (AP) to join the network.
All users share a single password, which must be manually updated on each wireless client once it has been manually altered on the initial wireless router or access point. The wireless clients then save the password. As a result, everyone using the computer can access the password and join the network.
Misconceptions about WPA-Personal’s efficacy in protecting Wi-Fi networks are common. A frequent misperception is that employing a complicated passphrase guarantees security. Strong passphrases improve security but don’t completely fix WPA-Personal’s weaknesses, especially regarding advanced hacking methods. Furthermore, some users mistakenly think that WPA-Personal defends against brute force attacks, failing to recognize that skilled attackers might undermine network security by taking advantage of WPA protocol flaws. Recognizing these myths is essential to properly evaluating WPA-Personal’s security posture and implementing safeguards to reduce risks.
Security Vulnerabilities of WPA-Personal
While WPA-Personal brought about some early improvements in wireless security, its intrinsic flaws allow malicious people to exploit it. A significant weakness exists in the encryption technique that WPA-Personal uses, known as TKIP (Temporal Key Integrity technique). Although TKIP is a step forward over the infamously unsafe WEP (Wired Equivalent Privacy), its efficacy has been compromised by cryptographic flaws. The security of sensitive data transferred across the network may be jeopardized if attackers use these vulnerabilities to intercept and decode data packets.
Moreover, the pre-shared passphrase or key used for authentication in WPA-Personal is vulnerable to brute-force attacks. Even though it’s advised to create long, difficult passphrases, many users use simple, widely known words instead, giving hackers a head start on brute force operations. Adversaries can methodically guess or crack passwords using specialized tools and processing power, allowing them to access the Wi-Fi network without authorization.
Real-world examples highlight the risks of depending entirely on WPA-Personal for wireless security. WPA-Personal is based on the WPA2 protocol, which has a serious issue that researchers detected in one prominent instance known as the “KRACK” (Key Reinstallation Attack) vulnerability. Due to a flaw in the four-way handshake procedure used to create a secure connection, attackers could intercept and alter data flow, possibly jeopardizing the confidentiality and integrity of conversations. The KRACK vulnerability was a clear reminder of the continuous challenges of protecting wireless networks and the requirement for strong wireless security protocols, other than WPA-Personal.
WPA Personal Vs WPA2
Overview of WPA2
WPA2 (WiFi Protected Access 2) is an encrypted security protocol that secures internet communication over wireless networks. The second iteration fixes previous issues and provides stronger encryption. Since its launch in 2004, it has established itself as the industry standard for wireless network security.
How Does WPA2 Work?
All security protocols use cryptographic keys to encrypt data and make it indecipherable. The data is decrypted using the same key.
However, not all security protocols make use of the same technology. WPA2’s advanced data encryption techniques have made it the industry standard for networking security today. You may also select particular WPA2 parameters to maximize security based on your needs.
WPA2 – PSK
When configuring your router for WPA2, you may choose whether your security is for business or domestic usage. WPA2-personal (WPA2-PSK) is more suitable for home networks or small enterprises, while WPA2-enterprise is designed for larger organizations.
Routers are secured using encryption keys, which jumble your data and keep it safe from hackers. WPA2 employs dynamic key encryption, which changes the key often and increases its difficulty of cracking.
When a client provides a pre-shared key, the network’s clients in a WPA2-personal network are assigned unique encryption keys. The pre-shared key is an 8–63 character passphrase written in simple English.
How Secure is WPA2?
WPA2 has been the accepted security procedure for many years for a reason, which is due to the AES (Advanced Encryption Standard) encryption technique.
Every security protocol seeks to rectify the shortcomings of its forerunners. Therefore, WPA2 addressed security flaws that were found in WPA and WEP. Because skilled hackers could quickly crack these earlier security protocols’ encryption methods, they turned out to be inferior. Even the most advanced supercomputer would take billions of years to crack the AES encryption employed by WPA2.
Differences Between WPA-personal and WPA2-personal
Encryption Algorithm
WPA-Personal employs the Temporal Key Integrity Protocol (TKIP) for encryption, whereas WPA2-Personal uses the Advanced Encryption Standard (AES). AES is intrinsically more secure than TKIP due to its well-known robustness and resilience to cryptographic attacks. WPA2-Personal’s use of AES greatly improves the security and integrity of data transferred over the wireless network.
Key Management
Users usually provide a pre-shared passphrase or key when using WPA-Personal, and this information is used to generate encryption keys. On the other hand, WPA2-Personal decreases the possibility of key-related vulnerabilities by using AES and dynamically generating encryption keys. This dynamic key management strategy improves security because key compromise and unauthorized access are less likely.
Authentication Mechanisms
Pre-shared keys are used for authentication in both WPA-Personal and WPA2-Personal. However, WPA2-Personal has more robust authentication methods. WPA2-Personal supports the Extensible Authentication Protocol (EAP), which allows for more robust authentication processes and improves network security. By utilizing EAP, WPA2-Personal improves authentication and lowers the possibility of unwanted access.
Security Features Analysis
Encryption Strength
WPA2-Personal only uses AES encryption, which is stronger cryptographically than the TKIP utilized in WPA-Personal. Because AES uses a 128-bit encryption key, it is far more resistant to cryptographic vulnerabilities and brute force assaults. The security and integrity of data transferred via WPA2-Personal networks are guaranteed due to the strong encryption offered by AES.
Resistance to Attacks
AES encryption and dynamic key management, which are features of WPA2-Personal, reduce typical attack vectors that are frequent in WPA-Personal networks. When combined with dynamic key generation, AES’s defense against cryptographic assaults lessens the vulnerability of WPA2-Personal networks to exploits such as brute force attacks and key-related flaws. WPA2-Personal, therefore, provides better security against illegal access and data intrusions.
Industry Adoption and Standards Compliance
With extensive use in many industries, WPA2-Personal has become the industry standard for Wi-Fi security. Its compatibility and interoperability with various devices and network infrastructures are guaranteed by its adherence to accepted cryptography standards and best practices. WPA2-Personal is a commonly used wireless network security protocol by people and organizations who strive to maintain the highest levels of security for their networks.
Passwordless Wireless Network Security
There has never been a greater pressing need for strong security measures. Traditional password-based authentication techniques are becoming increasingly susceptible to cyberattacks, which increases the need to regularly reset passwords and raise security issues. But there’s a better option out there: certificate-based authentication. With certificates, every connection has a complete identity context, offering unmatched security in various authentication circumstances. The Managed Cloud PKI as a Service from SecureW2 provides an easy switch from password-based authentication to certificate-based authentication, eliminating the hassles involved.
Our Managed Cloud PKI platform enables organizations of all sizes to easily use the security benefits of digital certificates. Organizations may expedite issuing and deploying certificates for network authentication, S/MIME, desktop logins, code signing, and other purposes by centralizing certificate administration into a user-friendly interface. In contrast with standard on-premise PKI systems, SecureW2’s managed PKI leverages contemporary automation technologies to streamline the certificate lifecycle management process, providing the ideal balance of security and convenience. Organizations may benefit from the peace of mind that comes with a secure, passwordless authentication solution without breaking the bank by having no upfront infrastructure or software expenses.
Role of RADIUS in Wi-Fi Security
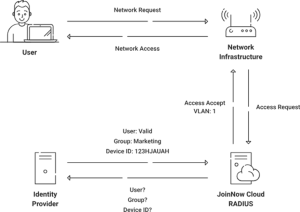
RADIUS (Remote Authentication Dial-In User Service) improves Wi-Fi security by providing a centralized authentication and authorization framework. Implementing a RADIUS server allows organizations to exercise granular control over network access and guarantees that only authorized users and devices are allowed access. With its dynamic policy enforcement features and passwordless authentication, SecureW2’s RADIUS platform raises the bar for Wi-Fi security.
Cloud RADIUS connects user’s and other devices’ identities to each connection through strong certificate-driven security mechanisms, allowing in-depth tracking and segmentation. Say goodbyeto interruptions on your network caused by expired and reset passwords, and greatly reduce the possibility of stolen credentials. Our verbose event recording and AI-powered anomaly detection enable enterprises to react quickly to security incidents.
Safeguarding Your Wi-Fi with Secure Authentication
In conclusion, WPA-Personal’s inherent flaws highlight how urgently organizations must switch to more secure authentication techniques. The increased vulnerability of password-based systems, such as WPA-Personal, to cyberattacks makes a transition to certificate-based authentication necessary for improved security. SecureW2 provides easy-to-use solutions that strengthen Wi-Fi networks against unwanted access by enabling the adoption of secure authentication methods.
Contact us now to take the first step toward a secure wireless environment.