Device attestation is used to verify a device’s authenticity and ensure that only genuine, untampered devices with approved, uncompromised software are given access to systems. It provides cryptographic evidence through digital certificates signed by a trusted certificate authority (CA). A server can authenticate the certificates and check against policies for granular control.
What Is Device Trust In a Network?
Device trust consists of rules and processes that ensure only authorized devices can connect to the network, systems, data, and other resources. It also establishes specific policies for privilege-based access at network endpoints, helping to prevent unauthorized access, especially when employees use their devices to connect to the network.
The Role Of Device Attestation In Device Trust
Attackers can perform various attacks, such as MAC spoofing, Address Resolution Protocol (ARP) spoofing, and Dynamic Host Configuration Protocol (DHCP) spoofing, which allows them to impersonate a device and gain access to the network. Once they gain access to the network, they insert malicious code into the hardware via supply-chain attacks that can’t be detected through anti-virus or anti-malware software
However, with hardware-backed device attestation, digital certificates are used to communicate to systems that a device is trustworthy in a way that can’t be tampered with. It involves the use of a Public Key Infrastructure (PKI) that issues digital certificates to all end users, but only after validating device trust through communication with device-management platforms or a manufacturer, such as Apple. A PKI like SecureW2 validates device trust at the point of issuance and continuously monitors device trust using APIs and webhooks.
These checks ensure a device is genuine and untampered, and the results are passed to risk evaluation systems. Device attestation ensures that only uncompromised, safe devices can access company resources and the network.
How Does Device Attestation Work?
Device attestation relies on a secure foundation known as the Root of Trust (RoT), commonly referred to as a Secure Enclave or TPM, which ensures the authenticity and integrity of the device. It is responsible for storing and processing cryptographic keys to secure a device in a network. A device’s unique identity is established and securely provisioned, often through the RoT. Then, cryptographic keys linked to this identity are generated using Onboard Key Generation (OBKG) or injected from an external source. This identity is then used in attestation processes.
The keys are essential for generating credentials, storing them, and using them to authenticate devices within a managed device solution.
Use Cases for Device Attestation in a Network Environment
Device attestation prevents device-based threats by adding a layer of security and ensuring that a device is trustworthy. In an enterprise organization, device attestation ensures that managed devices and BYODs are secure and have not been tampered with before they can access critical resources.
Device Attestation in Apple Devices
Apple devices have hardened hardware and software integration, relying on the secure enclave of iOS devices. The secure enclave is a processor that helps manage cryptographic keys and biometric information to generate a unique attestation key for every device. Device attestation in Apple verifies the firmware, runs tamper checks, and ensures every device runs the original iOS version during the boot process.
Our PKI uses the ACME protocol to automate certificate issuance for managed Apple devices. The MDM communicates with our PKI via an API, and our PKI instructs the MDM to use a predefined ACME payload when a managed device requests a certificate. Once the device initiates the request, our PKI performs two validations: it checks with the MDM to confirm the device is enrolled and managed, and it verifies the device’s legitimacy through Apple’s attestation server. Only after both checks are successfully completed is a certificate issued.
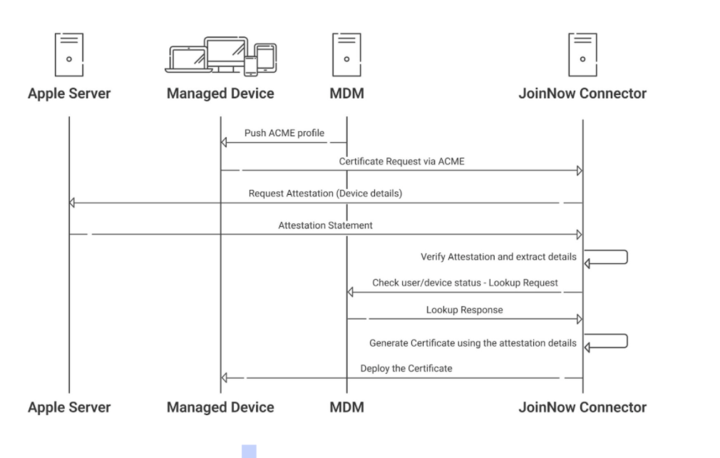
Device Attestation In Windows Devices
With Windows devices, a Trusted Platform Module (TPM) secures a device’s private key. Every TPM is populated with a unique asymmetric key called the Endorsement Key (EK) and cannot be changed or removed. It is used to verify that a TPM is genuine and manufactured by Microsoft. The device’s public key is known as the EKPub.
A CA establishes trust with a TPM through an EKPub. When a user requests a certificate, they must prove to the CA that it is needed for a device with the private key and verified with EkPub. Upon verification, the CA issues a digital certificate that is attested by the private key within the TPM. User devices with TPM-backed digital certificates can have access policies set, allowing administrators to enforce a higher-assurance device trust required for system access.
Leverage SecureW2’s PKI For Device Attestation In Managed Devices
Organizations adopt managed device attestation through digital certificates via a PKI provider. Our Managed Gateway APIs validate device authenticity using ACME before issuing certificates, preventing unauthorized or compromised macOS and iOS devices from accessing your network.
We integrate with Microsoft Intune to enable seamless, secure, and automated certificate-based authentication for managed devices. Our Dynamic PKI works with Intune to ensure that only trusted devices are issued digital certificates for network access, thereby restricting unauthorized access and enhancing context-based device trust. For BYODs, we integrate with your IDPs to provide SAML-backed authentication at the time of certificate issuance and ensure keys are generated on hardware.
Explore our Dynamic PKI solutions to build a secure network for managed device attestation.