Password breaches have impacted nearly every industry, from telecommunications to healthcare. As threat actors refine their attack methods, securing networks solely with passwords has become increasingly challenging. Organizations are transitioning to stronger authentication methods, such as digital certificates, to enhance their network security.
Digital certificates use asymmetric encryption to secure communication and authenticate identities between clients and servers. Asymmetric cryptography—also known as public-private key cryptography—relies on a pair of mathematically linked keys: a public key, which can be shared openly, and a private key, which must be kept secret. For example, if a sender wants to send a confidential message, they encrypt it using the receiver’s public key. Only the receiver’s matching private key can decrypt it.
In certificate-based authentication, this cryptographic process proves the identity of devices or users without relying on passwords. Since asymmetric encryption is based on complex mathematical algorithms, it’s nearly impossible to brute-force or replicate, making it far more secure than traditional credentials. However, to manage and verify digital certificates at scale, organizations require a Public Key Infrastructure (PKI) to issue, distribute, and revoke certificates securely.
What is a PKI in a Network Environment
A PKI uses digital certificates to secure a network environment and is built of many components that establish a Root of Trust (RoT). Without a RoT structure, certificate-based authentication would be impractical, as self-configured certificates can leave networks vulnerable to phishing, man-in-the-middle (MitM) attacks, and credential theft.
So what exactly makes a PKI work in a networked environment? The components of a PKI are:
- Certificate Authorities consisting of
- Root CA
- Intermediate CA
- Digital Certificates & Certificate Templates
- Certificate Revocation Methods
- Certificate Revocation List (CRL)
- Online Certificate Status Protocol (OCSP)
- Certificate lifecycle
- Hardware Security Modules (HSM)
Certificate Authority (CA)
In a PKI, a client device generates a public-private key pair. The public key and identifying information are sent to a trusted Certificate Authority (CA), which verifies the device’s identity and issues a digitally signed certificate. This certificate binds the public key to the device and is signed using the CA’s private key.
When the device attempts to access the network, it proves its identity by signing a challenge with its private key. A server validates this signature using the public key in the certificate and confirms the certificate’s authenticity by verifying the CA’s signature. This process ensures that only trusted devices with corresponding private keys can access the network.
A CA also facilitates encrypted web traffic between the web server and your web browsers. Certificates used for internet encryption are often referred to as “SSL certificates”.
Root Certificate Authority
A Root CA is the core of a PKI; it signs the certificates issued to CAs, essentially granting them the “authority” to issue certificates to users and devices. It’s a critical resource and should be handled with utmost care. A compromised Root CA could compromise the entire network and render all certificates in the network untrustworthy. Root CAs do not typically issue end-user certificates. The Intermediate CAs issue the client certificates. Root CAs, since they are sensitive, are almost always securely stored away from the public internet.
Intermediate Certificate Authority
An Intermediate CA is also a trusted CA and serves as a link between the Root CA and the client certificate. The Root CA signs the Intermediate CA, granting the Intermediate CA the authority to issue certificates to end-users and devices.
Certificate Templates
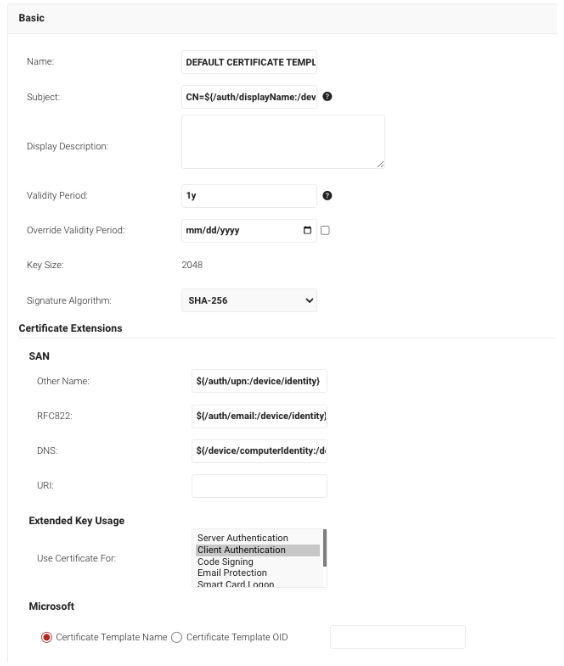
Certificate templates determine the structure and intended use of a certificate. Here is an example of a Default Certificate Template with attributes such as validity period, Signature Algorithm, and Extended Key Usage (EKU), which specifies the purpose for which the certificate will be used. A misconfigured certificate is a common exploit in a PKI and can leave your network vulnerable to attacks.
Certificate Lifecycle Management
Certificate lifecycle management encompasses all phases of the certificate lifecycle:.
- Certificate Enrollment: A user or device submits a request for a certificate to the CA.
- Certificate Issuance: The CA validates the applicant’s identity through credentials or by trusting another CA that has already validated the applicant.
- Certificate Validation: Every time the certificate is used to authenticate, the RADIUS server checks with the Certificate Revocation List to confirm that it is still valid and has not expired or been revoked.
- Certificate Revocation: Certificates have an expiration date specified when they are first issued, usually for several years. When a certificate expires instead of being manually revoked, it’s not on the CRL – it’s technically still on the device, just unusable for authentication. The expired certificate will automatically be considered invalid for any authentication attempt.
- Certificate Renewal: Instead of automatically being shunted to a CRL, some CAs have settings that renew certificates upon their expiration date, although they typically re-verify identity. Now, you can choose whether or not to generate a new key pair, effectively making it a new certificate.
A certificate management tool with effective IdP integration and a certificate database helps automate certificate management.
Certificate Policies
Certificate policies determine when to revoke or replace certificates in an MDM. This might be triggered by a non-compliant device, a change in authorization, a user leaving an organization, or misconfiguration. In general, certificate policies should be closely aligned with the existing policies in your Identity Provider or MDM. This is what makes APIs, like the Intune CA Partner API, so great. They’re just an extension of all the policies that exist in Intune.
Methods of Certificate Revocation
Large organizations issue certificates for thousands of their employees, and it’s a significant liability if they are in the hands of users or devices that shouldn’t otherwise have them. Certificate lifecycle management and automation solutions have quickly gained popularity, since legacy PKIs require a lot of manual work to ensure certificates were revoked promptly.
Certificate Revocation List (CRL)
A Certificate Revocation List (CRL) is a list of the serial numbers of certificates revoked before their expiration date. Certificate revocation lists are downloaded and cached into a service to authenticate certificates, allowing the service to check efficiently for revoked certificates.
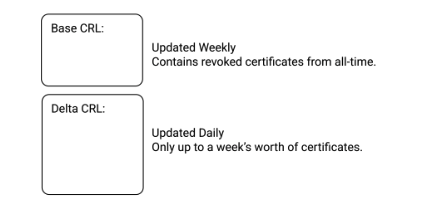
Base CRL vs Delta CRL
CRLs are incredibly resilient by design. They can be downloaded and cached efficiently because they are broken down into Base and Delta CRLs. A Base CRL lists all the revoked certificates from all time, and is typically updated weekly. A Delta CRL is usually updated daily and contains only up to a week’s worth of certificates.
Online Certificate Status Protocol (OCSP)
OCSP is a longstanding protocol used by clients, such as web servers, to check the certificate revocation status. Whenever authentication occurs, the OCSP server verifies whether the certificate requesting authentication is still valid. The OCSP server checks the certificate’s status against a Certificate Revocation List (CRL) or other revocation database maintained by the CA.
OCSP raises privacy concerns because it reveals which certificate a client is using for validation. It returns the status of individual certificates, not a list of certificates. OCSP Stapling, used by servers, helps reduce lookup costs and enhance privacy. OCSP is also vulnerable to MITM and replay attacks if not properly configured.
Hardware Security Module (HSM)
An HSM enhances the device by protecting and managing digital keys, laying the groundwork for building a secure enterprise PKI infrastructure. The HSM contributes to managing the complete cryptographic key lifecycle, including creation, rotation, deletion, auditing, and support for APIs to integrate with various applications.
RADIUS Server
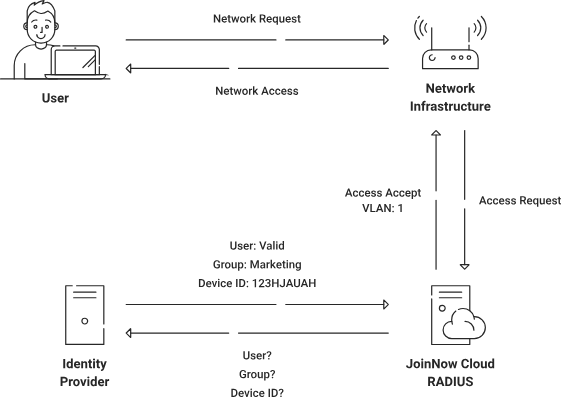
A RADIUS server authenticates users and devices securely to the network using digital certificates with EAP-TLS in a WPA-2 Enterprise network. It uses the 802.1X framework to enable network access control and authentication for remote users to access a server.
A Cloud RADIUS communicates with an IdP and MDM during authentication to verify user roles, device compliance, and risk posture. Based on this context, it can revoke access, prompt certificate renewal, and segment users or devices into VLANs based on certificate type or trust level for adaptive access control with digital certificates.
There are two CAs in PKI-based authentication. The first one validates digital certificates presented by users or devices during access requests, ensuring only trusted users and devices can authenticate and access the network.
Second, the client and the RADIUS server must possess a server certificate issued by a trusted CA. This certificate enables the client to authenticate to a RADIUS server, and the RADIUS server to authenticate its identity to the client, thereby establishing a secure TLS tunnel. This mutual server-certificate validation enables stronger trust and eliminates credential theft.
Use Cases of PKI in Enterprise Security
A PKI enables robust security via trusted identities, access-based controls, and encryption-based authentication for network users and devices. It prioritizes identity and continuous authentication, making it a powerful tool for modern network security.
Secure Wi-Fi, Wired, And VPN For 802.1X Authentication
Wi-Fi Security
A PKI can be used for Wi-Fi authentication by leveraging the EAP-TLS protocol. This is often done on WPA2-Enterprise networks where individual users each log in using their own certificates rather than sharing a single credential. A user or device presents their digital certificate to a RADIUS server, which checks the certificate’s validity and issues the CA. If the certificate is valid, the user or device is allowed or denied access.
With EAP-TLS, the connecting device validates the RADIUS server’s certificate before presenting its certificate, a process known as mutual authentication or server certificate validation. Mutual server authentication enhances Wi-Fi security by verifying the identities of both the client and the server and preventing unauthorized access through attacks.
A PKI also ties access decisions to a user or a device. It is linked to the user’s identity, device, and organizational role. For example, an employee in the finance department is issued a digital certificate with VLAN access. Their roles and access levels are decided, and then they are segregated into separate VLANs in a network. A finance employee would then have access to only resources and applications specific to their network, and would not be able to access any other VLANs.
VLAN segregation also enforces device trust since certificate policies can adapt to real-time changes, such as device health updates, role changes, and access rules, ensuring continuous trust based on an organization’s context.
Wired Security
PKI secures wired connections for 802.1X port-based authentication via digital certificates. When a device tries to connect to a port, the network switch blocks the connection till the authentication. To connect to a wired network, the device must be connected to an Ethernet and authenticated via an 802.1X switch.
The device certificate is forwarded to the server via an 802.1X-enabled switch. The server checks the certificates’ validity against a trusted CA. A PKI prevents devices from accessing rogue networks by preventing unauthorized access to LAN ports in a network.
VPN Security
VPNs provide secure remote access to internal applications and data. Compared to passwords, certificate-based VPN authentication is more secure and typically preferred since it reduces the risk of credential theft, enables automated management, and strengthens trust between users and systems. The Root/Intermediate CA is stored on the Firewall in a certificate-based VPN network. Once the user is authenticated, a secure tunnel is established to enable access to the network.
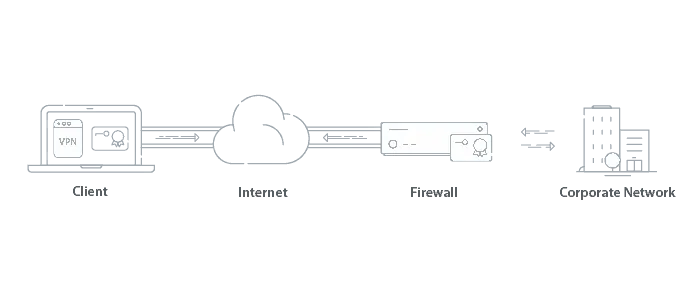 Benefits of a PKI In a Network Environment
Benefits of a PKI In a Network Environment
Improve End-User Experience
Passwords require repeated input and constant resets. When combined with multi-factor authentication (MFA), the user experience becomes frustrating, since the user is now burdened with passwords plus an additional device or factor for authentication. As complexity increases, users tend to bypass the MFA requirement, thus leaving the network vulnerable to attacks. MFA is also susceptible to fatigue attacks, where an attacker bombards the end user with multiple notifications, hoping the user will accept one and fall prey.
As more organizations strive to adopt passwordless authentication methods, digital certificates with a Public Key Infrastructure (PKI) are becoming the preferred choice. The National Institute of Standards and Technology (NIST) prescribes specific frameworks to secure critical data in an enterprise network. It strongly recommends using digital certificates with a Public Key Infrastructure (PKI) for Wi-Fi and VPN authentication to identify and ensure that only trusted devices can access the network.
Prevent breaches due to stolen credentials
Implementing a PKI with digital certificates eliminates the security risks that arise with stolen credentials. Digital certificates are tied to public-private key pairs, where the private key is securely stored on devices. When a device attempts to connect to the network, it must prove possession of its private key, which cannot be phished or reused like a password.
Even if a malicious actor intercepts the certificate or gains access to the network traffic, they cannot authenticate without the corresponding private key, which remains securely stored and inaccessible. This cryptographic identity verification ensures that only authorized users and trusted devices can access network resources, effectively blocking attackers who rely on stolen credentials.
Reduce Password-Related Support Tickets
By switching to digital certificates, an organization can reduce overheads by minimizing the volume of password-related support tickets. Since digital certificates replace passwords for authentication, users no longer need to remember, reset, or frequently change credentials.
This eliminates routine password resets and lockout requests, significantly easing the burden on IT teams. Automated certificate issuance and renewal also streamline onboarding and access management, reducing manual intervention and support costs.
Greater Visibility Over Network Access
With a PKI, authentication events are tied to cryptographically verified identities. Unlike passwords, which can be shared or stolen, digital certificates are device-bound and traceable. Detailed RADIUS logs show who and what connected or accessed the network when a device authenticates using a certificate.
How Does A PKI Secure Networks in an Organization
A PKI operates on identities as a source of truth, validating every user and device on a network via digital certificates, which provide enhanced security compared to passwords and pre-shared keys. Here is how a PKI enhances network security in an organization:
Trustworthy Validation for Users & Devices
By using digital certificates and cryptographic keys, a PKI provides trustworthy validation for users and devices. Each user or device is issued a certificate by a trusted CA, which confirms their identity. When they attempt to access the network, they prove their identity by securely responding to a challenge from the rightful owner only. This process ensures that access is granted only to verified, trusted users and devices, making it much harder for attackers to impersonate someone or use stolen credentials.
Leverages EAP-TLS In WPA2-Enterprise Network
Digital certificates provide enhanced security for EAP-TLS 802.1X authentication on a WPA2-Enterprise network. They provide the framework for the EAP-TLS protocol, which enables faster and more secure authentication through mutual authentication between clients and servers.
Protecting Remote Cloud Environment
With certificate-based 802.1X authentication, users and devices can connect to a remote server without the risk of stolen or leaked passwords that could compromise the entire network.
A certificate management system tied to a PKI automates the certificate lifecycle for managed, BYOD and guest devices. This allows administrators to continuously monitor who has access to the network, whether it is wired or wireless. This ensures that only authorized personnel can access specific data and applications, thereby preventing unauthorized access to confidential information.
Here’s why a PKI-based network is better than a password-based one.
| Features | Password-Based Network | PKI-Based Network |
| Security Risk | Due to shared keys, there is a high risk of phishing, brute force, and MITM attacks. | Lower risk as there are no pre-shared keys. |
| Authentication Factor | Weaker trust- passwords can be stolen or duplicated. | Stronger continuous device trust with Certificate-based authentication |
| UserExperience | Clunky and needs multiple resets, reset-based disconnects. | Certificates can be used till their validity or revocation. |
| Context-Based Trust | Limited, static device trust. | Identity and access-based granular trust model. |
Best Practices for a Strong PKI Implementation For Your Network
PKI implementation needs a strategy and a far-sighted approach to build a secure network. With digital certificates, your network will be ready for secure communication through identity and context-based device trust. However, a PKI alone won’t address security needs unless properly implemented.
Here are some best practices:
Use an Intermediate CA For Certificate Issuance
The Root CA is the main anchor of trust in a PKI and should never be compromised. Compromising the Root CA would mean that all certificates in the PKI have been compromised, and a complete overhaul would be required. An Intermediate CA rises from a Root CA and is considered the best way to issue certificates on a cloud PKI.
An Intermediate CA can be established under an organization’s central CA and then separated based on geographical locations, departments, etc. The Root CA would remain separate and well-guarded, maintaining trust throughout. An Intermediate CA reduces the exposure risk to the certificates it issues alone and can be contained more easily compared to the entire network. They can also segregate users/devices based on roles, locations, departments, and third-party-issued certificates to simplify policy enforcement.
Intermediate CAs can integrate with IdPs and MDMs to validate user identity before certificate issuance and revoke certificates for devices as they become uncompliant, thus enforcing context-based device trust in a network.
Automate Certificate Lifecycle Management
A certificate lifecycle typically includes enrollment, issuance, renewal, revocation, and ongoing maintenance. Manual configuration is not only tedious but also prone to misconfiguration. A misconfigured network is an open platform for hackers to launch MITM and brute-force attacks.
As an organization, you should automate certificate management through a managed PKI that streamlines the certificate lifecycle. This would prevent the risk of network outages due to certificate expiration and subsequent renewal. With a managed PKI, an organization can implement granular visibility and access policies and continuously monitor users and devices.
Failure to manage certificates can lead to attacks and data leaks. A managed PKI would prevent this by keeping track of all certificates and setting alerts to renew them before expiration. You can also set specific revocation policies to avoid devices with rogue certificates, certificates that need renewal due to certificate policy changes, and misconfigured certificates from accessing the network.
Regular Audits and Compliance Checks
A PKI should maintain an audit trail for all certificates issued, renewed, revoked, and stored in the network. Security teams should regularly monitor these logs to respond quickly to incidents and detect unusual activities. If any unusual incident is detected, an automated alert should be set up to alert and prevent further access.
Integration with a Security Information and Identity Management (SIEM) tool provides real-time alerts from all access points, firewalls, servers, and cloud platforms in a network environment. With an SIEM tool, you can detect certificate-based anomalies and use them to troubleshoot, audit, and ensure compliance, thereby maintaining a secure network perimeter.
Integrate PKI With Identity and Access Management Tools
By integrating PKI with IdPs and MDMs, organizations link users and devices to certificate-based authentication for IAM. They use EAP-TLS to strengthen security and replace passwords with a more reliable method. An IIAM system allows administrators to automate certificate issuance, revocation, and renewal as users or devices are added or removed from an organization.
Identity and access management tools ensure that people can access resources within a network through context-based, granular policies, achieved through the real-time integration of Identity Providers (IdPs) with a Public Key Infrastructure (PKI). Context-based policies ensure that only trusted users and devices can access resources and applications in accordance with established policies and rules.
Protect Private Keys Using HSMs
The private key is the central pillar of a PKI security framework. It requires the most stringent security measures to protect it from theft and misuse.
To secure a private key, an organization should ensure that the secure keys, i.e., the root and intermediate keys, never leave the HSM. All keys must be generated with the HSM to avoid exposure during creation. Any key stored in an HSM should be used solely for cryptographic functions, such as developing new keys, signing, and decryption. There should be limited access and restrictions on viewing and exporting cryptographic keys.
In a managed PKI, an HSM can integrate with CAs to automate key usage, ensuring that private keys are never exposed to administrators within the network and maintaining complete integrity.
Onboarding Software to Authenticate Managed and BYODs to a Network
Digital certificates are a better option than passwords, as they are resilient to theft, over-the-air credential theft, and phishing attacks. However, managing certificates with a self-made PKI can do more harm than good. Misconfiguring a PKI can leave your network compromised and vulnerable to MITM and brute force attacks.
Onboarding software automates certificate issuance to managed devices using protocols such as the Dynamic Simple Certificate Enrollment Protocol (SCEP) and Automated Certificate Management Environment (ACME). It also helps BYOD and guest devices self-enroll for certificates and authenticate safely to a network with limited access, preventing unauthorized access.
Future-Proof Your Network With SecureW2’s Dynamic PKI
Credential-based network authentication often fails to secure networks effectively today. Moving away from passwords to a more resilient security model, such as digital certificates, will provide bulletproof network security as they are almost phishing-resistant and hard to steal or duplicate.
Certificate-based authentication with a Public Key Infrastructure (PKI) enables organizations to transition from a static, one-time trust approach to an adaptive security model, where trust is continually verified and updated.
SecureW2’s Dynamic PKI integrates with your existing IdPs and device management systems, ensuring continuous trust management. This ensures that only trusted users and devices can access the network. Dynamic authentication verifies trust throughout a session, enabling context-based authentication for managed, BYOD, guest, and IoT devices.
Explore more about our Dynamic PKI here.