Key Points
- Access Control Lists (ACLs) regulate user and device permissions in Windows, with DACLs giving access and SACLs auditing access attempts.
- A Public Key Infrastructure (PKI) improves Windows access control by incorporating digital certificates for secure authentication and authorization, providing greater context about the devices and users accessing resources.
- PKIs can be difficult to set up on your own, but a managed PKI service such as JoinNow Connector PKI allows you to quickly deploy certificate-based authentication and manage the entire certificate lifecycle.
Controlling who has access to what, is a fundamental aspect of securing applications, data points, and network resources in an enterprise environment. In the realm of enterprise networks, access control is pivotal in restricting user and machine access solely to the necessary applications or data points required for their specific roles.
At the heart of access control lies the concept of security features designed to regulate who gains access to the resources in an operating system and the extent of their access. This concept, often referred to as network access control, lays the foundation for segmenting your network—a critical requirement in network security.
An Overview of Acess Control Lists (ACLS) and How They Work
At the core of Windows Access Control mechanisms are Access Control Lists (ACLs). Implementing ACLs involves delineating permissions for various users and devices, thus defining the level of access each has to specific network resources or objects. This process is central to securing an organization’s data and system integrity. A Public Key Infrastructure (PKI) can be used to enhance an organization’s network access control even further through the use of digital certificates.
In the broader context, PKIs, including those compatible with Microsoft environments, play a crucial role in establishing a secure environment for certificate management. Within such ecosystems, certificate authorities (CAs) are tasked with validating the identities of users and devices, ensuring that access is granted only to verified entities. This creates a layered security model that enhances the effectiveness of ACLs by integrating digital certificates, which are instrumental in establishing secure connections.
The components of ACLs, namely Discretionary Access Control Lists (DACLs) and System Access Control Lists (SACLs), along with Access Control Entries (ACEs), are fundamental in specifying access permissions in a granular manner. DACLs determine access permissions for users or groups to objects, while SACLs are focused on the auditing of access attempts, playing a vital role in security incident response and prevention.
The essence of using PKIs that are interoperable with Microsoft systems lies in leveraging the robust framework they provide for authenticating users and devices across both on-premises and cloud environments. Microsoft does offer its own PKI solutions, including Active Directory Certificate Services (AD CS) and its newer Microsoft Cloud PKI. However, neither of these are managed solutions, and a PKI can be difficult to set up and maintain on its own. Managed PKI services, such as SecureW2’s, can integrate with Microsoft environments and allow organizations to quickly implement the security of a PKI.
What Are Securable Objects & Security Descriptors?
Any object can be called a securable object if it has a security descriptor. Though all named Windows objects are securable, some unnamed objects, too, can have security descriptors. Some examples of named and unnamed objects are:
- Unnamed Objects — Processes and threads such as a huddle in Slack. They are not saved, and the process or thread ends the moment the activity stops.
- Named Objects — Files, directories, access tokens, network shares, devices, printers, desktops, Windows stations, and active directory objects such as users or user groups.
Security Descriptors hold the security information about securable objects, such as:
- Ownership details like security identifiers (SID) of the owner of an object and the group it belongs to.
- A list of the users and groups allowed or denied access and the degree of access they have to the securable object. This list is called the DACL.
- A list that contains the types of access attempts that are to be audited. This list is called the SACL.
In the context of Active Directory, all objects have security descriptors. You will find more information about DACL and SACL in the next section, where we’ll discuss the access control list and its components.
What Is an Access Control List?
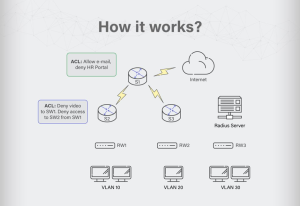
Access Control Lists in action
An ACL is a detailed data table that allows an operating system to discern the level of access granted to users and machines, thus embodying the principles of least privilege necessary for maintaining robust security. In the broader spectrum of PKI-enabled security ecosystems, ACLs facilitate a seamless mechanism for defining and administering access permissions. This is achieved through Access Control Entries (ACEs), which explicitly outline the permissions granted to individuals or groups for actions such as reading, writing, and executing.
The strategic application of ACLs, supported by a flexible and interoperable PKI framework, ensures that access to critical resources is restricted to authenticated and authorized entities. This not only enhances the security of an organization’s data and systems but also introduces a layer of adaptability for integrating cloud-based PKI solutions, thereby reinforcing the infrastructure against potential security threats and unauthorized access attempts. This approach underscores the importance of leveraging a versatile PKI that aligns with the ever-evolving needs of modern enterprise networks, including those utilizing Windows devices.
In cloud-based PKIs, ACLs extend their utility beyond traditional boundaries, such as enabling a seamless and secure interaction with Active Directory Certificate Services (AD CS). This integration empowers administrators to leverage CAs to authenticate and authorize access requests efficiently. Each entry in an ACL, the ACEs, specifies the permissions available to a user or group, including actions such as read, write, and execute.
How Does an Access Control List Work?
ACLs function by attaching a list of permissions, or ACEs, to each securable resource, such as files or directories. These ACEs dictate the specific actions that individual users or groups are permitted to perform, ranging from viewing to editing content. By consulting the ACL, the system can instantly determine whether a request for access by a user or device conforms to the established permissions. This process ensures that access decisions are made swiftly and accurately, aligning with predefined security policies and minimizing the risk of unauthorized access. Through their role in managing permissions effectively, ACLs serve as the backbone of a secure and efficiently governed digital environment.
Types of Access Control Lists
As discussed above, every object has a security descriptor, and two important ACLs that they have are as follows.
Discretionary Access Control List (DACL)
A DACL or discretionary access control list lists users and groups allowed or denied access to an object. A user or a member of a particular group that DACL does not identify will be denied access.
By default, a DACL is controlled by the user who created the object or the owner of the object that the DACL belongs to. Just like in the case of an ACL, each entry of the list is called an access control entry or ACE.
System Access Control List (SACL)
A SACL or system access control list is the list that defines the users or events that need auditing to be done when they are granted or denied access to the object. This is very useful in identifying security breaches and determining the exact location and degree of damage.
Just as in the case of a DACL, the system access control lists are controlled by default by the owner or creator of the object. The access control entries (ACEs) of an SACL determine whether recording has to be done for a failed attempt or a successful one at the time of a user trying to access the object.
Use Cases of Access Control Lists
Access Control Lists provide for the management of access rights across various scenarios. Among some use cases that illustrate the applicability and effectiveness of ACLs in enhancing security include:
- Network Security Segmentation: Leveraging ACLs enables organizations to segment their network effectively, creating barriers that restrict access based on user roles or device types. This segmentation is crucial for protecting sensitive data and systems from unauthorized access, aligning with compliance requirements.
- Resource Access Management in Active Directory: Utilizing ACLs in conjunction with Active Directory Certificate Services allows for granular control over who can access specific resources within an enterprise network. By defining precise access rights, organizations ensure that only authenticated and authorized users can interact with critical infrastructure components, hence mitigating the risk of data breaches.
- Regulatory Compliance and Audit Trails: The integration of SACLs with CAs facilitates the generation of audit trails for accessing sensitive data. This capability is essential for organizations needing to comply with regulatory standards that mandate monitoring and recording access to certain information.
- Remote Access Control: With the adoption of cloud-based PKIs, ACLs extend their utility to manage remote access permissions effectively. This ensures that remote workers or external devices connecting to the network are authenticated through a PKI, granting access only to resources necessary for their roles while maintaining strict security controls.
Implementing Access Control on Windows
Implementing Access Control in Windows environments, particularly those managed through a Windows server, fundamentally revolves around the utilization of Access Control Lists (ACLs). These ACLs ensure that only authorized individuals and systems can access certain data or operations, adhering to the principles of least privilege and role-based access control. The integration of Microsoft’s PKI significantly amplifies the security measures by facilitating the management and distribution of a public key, which, when paired with its corresponding private key, enables a secure authentication and encryption process.
How Windows Access Control Works
Windows Access Control operates on a sophisticated foundation that integrates with Active Directory to manage resources securely. The process is outlined as follows:
- Certificate Authority: Central to Microsoft PKI, the CA issues certificates to entities, verifying their identity using a combination of a public key (which is made publicly available) and a private key (which is kept secure by the user or organization).
- Certificate Templates: Predefined settings for issuing certificates. Windows Server administrators can configure these templates, tailoring the certification process to specific organizational needs, such as the level of access or the type of user.
- Certificate Enrollment: The process by which entities request and receive a certificate from a CA. Windows automates this process, easing the burden of manual certificate management.
- Active Directory: Integrates with PKI to assign and enforce access policies based on the issued certificates, ensuring that only entities with the correct credentials can access certain areas of the network.
This integration of components forms a robust system for managing access control, with the dual keys (public key and private key) playing a pivotal role in the authentication and authorization processes.
Challenges With Windows Access Control
While Windows access control systems, bolstered by Microsoft PKI, offer robust security features, they are not without challenges. These include:
- Complexity in Management: The intricate setup of certificate authorities, coupled with certificate enrollment and management, requires specialized knowledge, making it daunting for some organizations.
- Scalability Issues: As organizations grow, the task of managing an increasing number of certificates and access permissions can become cumbersome.
- Dependency on On-Premise Infrastructure: Traditional Windows Server-based PKI solutions rely heavily on on-premise infrastructure, which might not align well with the growing trend towards cloud-based solutions.
Cloud-Based Public Key Infrastructure Solutions
As organizations grapple with the intricacies of managing access control within Windows environments, the shift towards cloud-based PKI solutions emerges as a solution. The challenges associated with traditional Windows access control—ranging from the complex management of certificate authorities to scalability issues and the heavy dependency on on-premise infrastructure—underscore the necessity for more agile, scalable, and accessible solutions. Cloud-based PKIs represent a pivotal evolution in overcoming these hurdles, offering a streamlined, flexible, and cost-effective approach to securing digital assets and managing access rights.
The SecureW2 PKI exemplifies the next generation of access control solutions, providing a robust, vendor-neutral platform that effortlessly integrates with existing systems, including those operated on Microsoft environments. By leveraging the cloud, SecureW2 PKI eliminates the traditional complexities associated with PKI deployment and certificate management. Organizations can now facilitate secure access with unprecedented ease and efficiency, ensuring that only authenticated and authorized users can access critical resources, regardless of their location. This transition not only addresses the pressing challenges of traditional access control systems but also paves the way for enhanced security, scalability, and operational flexibility.
Access Control Lists With Other Solutions
The versatility and effectiveness of ACLs are not confined to Windows environments alone. They extend their utility to other platforms and solutions, broadening the scope of access control measures across different technological ecosystems.
Access Control Lists With RADIUS
The utilization of ACLs extends to network access control solutions such as Remote Authentication Dial-In User Service (RADIUS) servers, which act as a central authority for authenticating and authorizing network access requests. Integrating ACLs with RADIUS servers, alongside the deployment of Microsoft PKI, enhances the security of wireless and wired networks. This setup allows for the dynamic assignment of roles and access permissions based on certificate authentication, where certificates issued by a trusted certificate authority validate the identity and permissions of a user or device.
The RADIUS server, leveraging certificates authenticated by Microsoft PKI, can enforce access policies more securely and efficiently, ensuring that only authorized entities gain access to network resources. This approach significantly mitigates the risks associated with traditional password-based authentication methods, providing a more secure and manageable solution for network access control.
Cloud RADIUS for Network Access Control
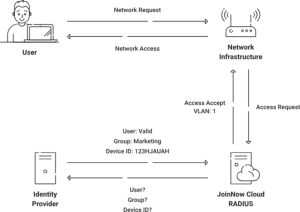
Cloud RADIUS can help mitigate the risks involved with password-based authentication and provides a well-rounded infrastructure for network access control. This is because Cloud RADIUS was designed with passwordless authentication in mind, integrating with a PKI for certificate-driven wired and wireless security.
Additionally, Cloud RADIUS is vendor-neutral, and capable of integrating with all major SAML Identity Providers (IDPs), including Azure AD/Entra ID, Okta, Google, OneLogin, and more. At the time of authentication, it communicates in real-time with your IDP, ensuring only the most current access policies are applied.
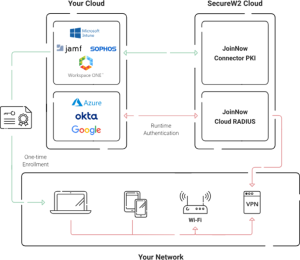
SecureW2 Cloud RADIUS
Implement Modern Cloud Access Control With SecureW2
Access control as a concept of network security is vast and has many facets that only one solution cannot cover. ACLs are crucial in implementing network access control. However, they alone cannot secure your information. There is a need for a comprehensive solution that covers all aspects of access control, authentication, authorization, and accounting.
SecureW2 offers end-to-end network access control solutions from onboarding to creating and implementing customized network access policies to monitoring network activity. Secure your network with SecureW2 solutions that are affordable and can be customized to best fit your organization’s needs. Click here to learn more about pricing.