Key Points
- Manually issuing certificates for a large number of Chromebooks is time-consuming and inefficient.
- A more efficient approach is to use a simplified SCEP-like mechanism that allows Chromebooks to automatically enroll for certificates without any user intervention.
- SecureW2 automates certificate management by integrating a SCEP Gateway with Google's Cloud Certificate Connector, allowing for effortless, secure, and passwordless authentication on Chromebook
Certificates are far superior to credentials and mitigate many vulnerabilities associated with pre-shared keys. They enhance the user experience by facilitating network access and removing password-related friction induced by password reset and complexity policies. Certificates also grant identity context by associating identities with devices, allowing administrators to decode SSL encryption and monitor device behavior.
One of the most significant challenges enterprises experience when configuring certificate-based authentication (CBA) is the smooth issuance of these certificates, especially when there are many devices to account for. To streamline this process, we at SecureW2 have developed a mechanism allowing Chromebooks to automatically enroll for certificates without requiring end-user intervention, leveraging JSON to achieve SCEP-like capability.
But before discussing the technical procedure involved in the process, we want the reader’s users to have a general understanding of the SCEP certificate lifecycle as it affects the Google Cloud Certificate Connector.
What is SCEP?
SCEP (Simple Certificate Enrollment Protocol) is a protocol that enables devices to quickly enroll for a certificate by communicating with a PKI through a URL and a shared secret. MDM software generally uses SCEP for devices by transmitting a payload to managed devices, including the SCEP URL and shared secret. This can save an admin significant time compared to manually enrolling managed devices for certificates.
Essentially, SCEP instructs devices on how to connect with the PKI using a Gateway API URL. SecureW2 customers may build their own SCEP Gateway API URL using our software. They may then add this URL to their MDM so that it can send a payload to devices that need to enroll for client certificates.
SCEP Shared Secret
A Shared Secret is a case-sensitive passcode shared between the SCEP server and the Certificate Authority (CA). This shared secret links the CA to the relevant server for certificate signing. The device submits the shared secret to our Managed PKI via SecureW2’s solution, and then the certificate enrolling occurs on the device.
SCEP Certificate Request
After configuring the SCEP gateway and communicating the Shared Secret between the SCEP server and the CA, you can generate and distribute a configuration profile allowing managed devices to auto-enroll for certificates. The device will send a certificate enrollment request to the CA via the SCEP gateway. After authentication, a signed certificate will be installed onto the device.
SCEP Signing Certificate
Most MDMs need you to upload a SCEP signing certificate that covers the entire certificate chain and is signed by the CA issuing certificates (signing certificate, Intermediate CA, Root CA). With In SecureW2, you pick the CA issuing certificates, and a PKCS12 file will be created for you to upload into your MDM.
Setting up the SecureW2 Management Portal
First, contact SecureW2 Support to create an Identity Provider (IDP) in the SecureW2 Management Portal for Google Verified Access. Then, log in to the SecureW2 Management Portal and perform the following steps:
If you have yet to configure the default configurations in the Management Portal, use the Getting Started Wizard.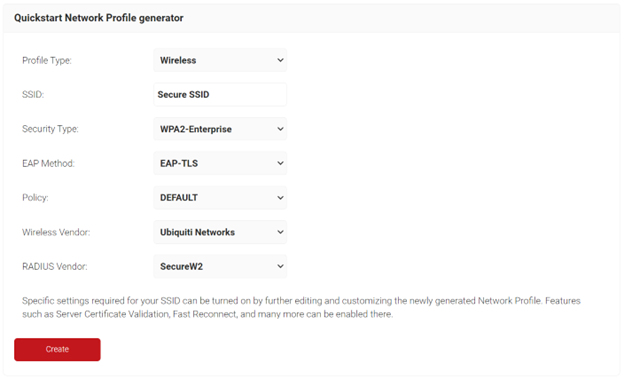
The Getting Started Wizard will create the configurations required for 802.1x authentication. For further configurations on the Getting Started wizard, refer to the “Getting Started” section in the JoinNow MultiOS Configuration Guide.
NOTE: The Getting Started wizard typically takes 60-90 seconds to create the profile.
Creating an Intermediate CA for Google SCEP Gateway Integration
SecureW2 recommends having a new intermediate CA for JoinNow SCEP Gateway integration with Google SCEP-based Chromebook enrollment as a best practice. To create a new intermediate CA:
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to PKI > Certificate Authorities.
- Click Add Certificate Authority.
- In the Basic section, from the Generate CA For drop-down list, select the Device and User Authentication option to authenticate devices and users.
- From the Type drop-down list, select Intermediate CA.
- From the Certificate Authority drop-down list, select the default Root CA that comes with your organization.
- In the Common Name field, enter a common name for the CA certificate. SecureW2 recommends a name that includes “SCEP.”
- From the Key Size drop-down list, select 2048 for the CA certificate key pair.
- From the Signature Algorithm drop-down list, select the signature algorithm for the certificate signing request. The option available is SHA-256.
- In the Validity Period (in years) field, enter the validity period of the CA certificate.
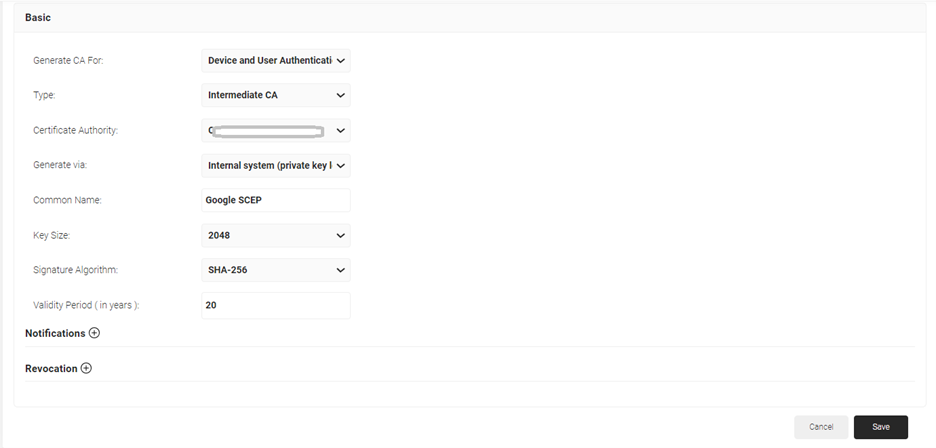
- Click Save. The new intermediate CA is generated.
Creating a Google Certificate Template
To create an Google Certificate Template:
- Navigate to PKI > Certificate Authorities.
- Click Add Certificate Template.
- In the Basic section, for the Name field, enter the name of the certificate template.
- In the Subject field, enter CN=${/auth/displayName:/device/identity:/csr/subject/commonname}
- In the Display Description field, enter a suitable description for the certificate template.
- In the Validity Period field, type the validity period of the certificate (based on the requirement).
- From the Signature Algorithm drop-down list, select the signature algorithm for the certificate signing request. The option available is SHA-256.
- In the SAN section:
- In the Other Name field, enter ${/auth/upn:/device/identity:/csr/san/othername}
- In the RFC822 field, enter ${/auth/email:/device/identity:/csr/san/rfc822name.
- In the DNS field, enter ${/device/computerIdentity:/device/buildModel:/csr/san/dnsname}
- In the Extended Key Usage section, from the Use Certificate For list, select Client Authentication.
- Click Save.
Generating a SCEP URL and Secret
To generate the SCEP URL and secret:
- From your JoinNow MultiOS Management Portal, go to Identity Management > API Gateways.
- Click Add API Gateway.
- Under the Basic section, in the Name field, enter the name of the API token.
- In the Description field, enter a suitable description for the API token.
- From the Type drop-down list, select SCEP Enrollment Token.
- From the SCEP Vendor drop-down list, select Other.
- In the Vendor Name field, enter “Google”
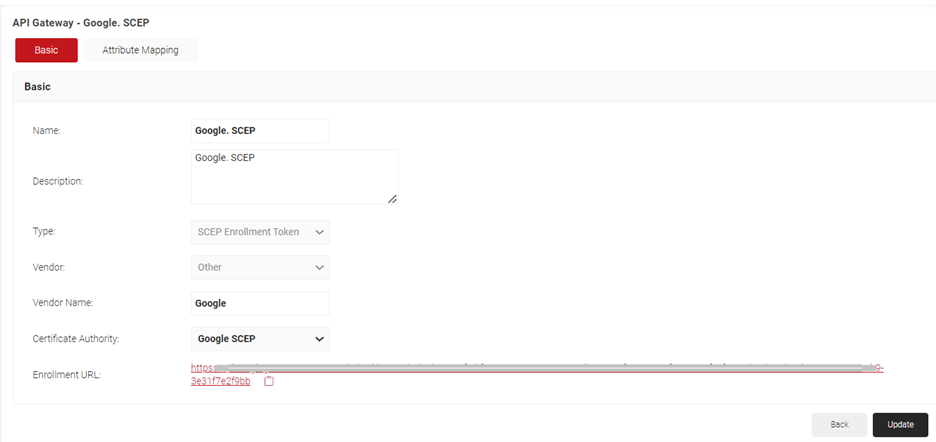
- From the Certificate Authority drop-down list, select the Intermediate CA created in Creating an Intermediate CA for Google SCEP Gateway Integration. If you do not select a CA, by default, the organization CA is chosen.
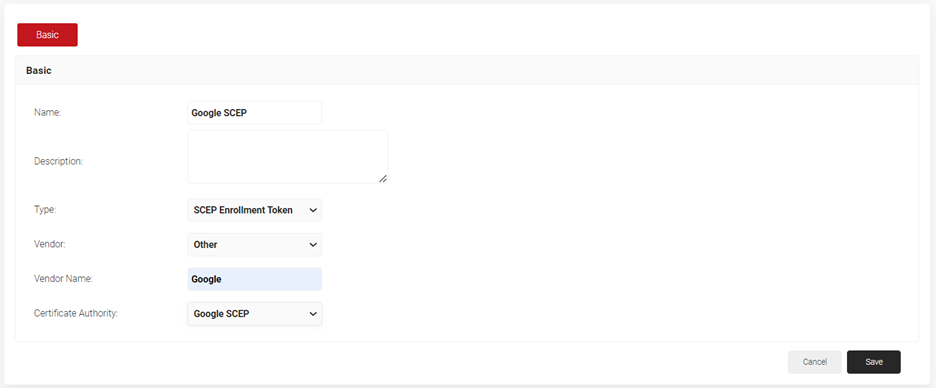
- Click Save. A .csv file containing the API Secret and URL is downloaded. In addition, the Enrollment URL is displayed on the page.
Configuring a Policy Engine Workflow
To configure a Policy Engine Workflow:
- Navigate to Policy Management > Policy Engine Workflows.
- Click Add Policy Engine Workflow.
- In the Basic section, enter the name of the role policy in the Name field.
- In the Display Description field, enter a suitable description for the role policy.
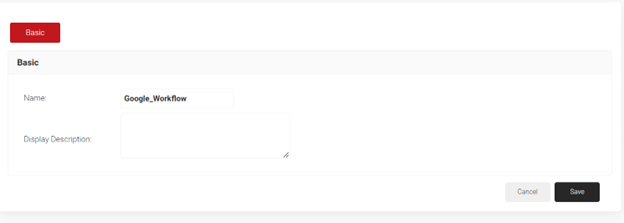
- Click Save.
- The page refreshes, and the Conditions tab is displayed. Select the Conditions tab.
- IFrom the Identity Provider drop-down list, select the API token you created earlier.
- In the Attributes/Groups section, for the Attribute field, retain ANY.
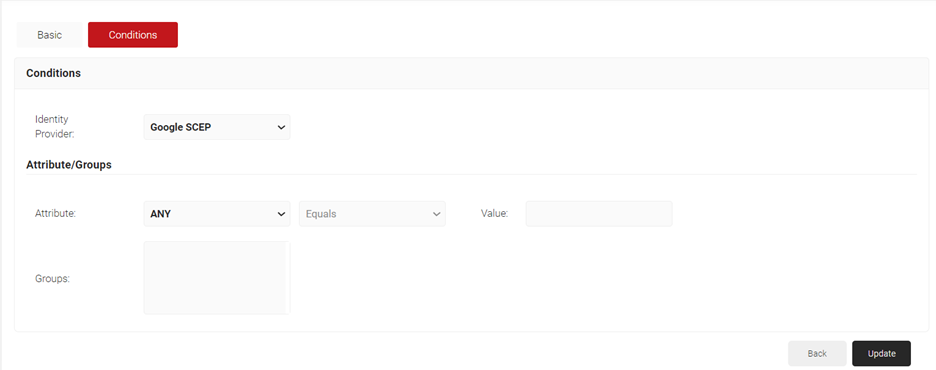
- Click Update.
Creating Enrollment Policy
To add an Enrollment Policy, perform the following steps:
- Navigate to Policy Management > Enrollment Policies.
- Click Add Enrollment Policy.
- Under the Basic section, enter the name of the enrollment policy in the Name field.
- In the Display Description field, enter a suitable description for the enrollment policy.
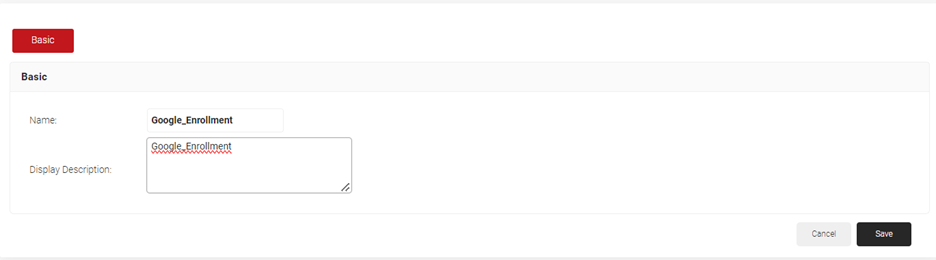
- Click Save.
- The page refreshes, and the Conditions and Settings tabs are displayed.
- Select the Conditions tab.
- In the Conditions section, from the Role drop-down list, select the role policy you created earlier ).
- From the Device Role drop-down list, select DEFAULT DEVICE ROLE POLICY.
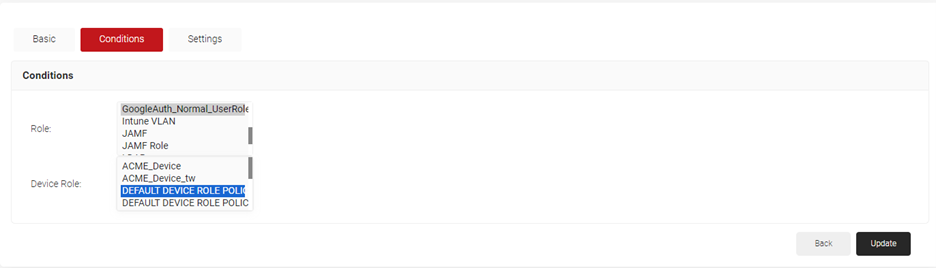
- Select the Settings tab.
- In the Settings section, from the Use Certificate Authority drop-down list, select the intermediate CA you created earlier.
- From the Use Certificate Template drop-down list, select the template you created earlier.
- In the other settings, the default values are retained.
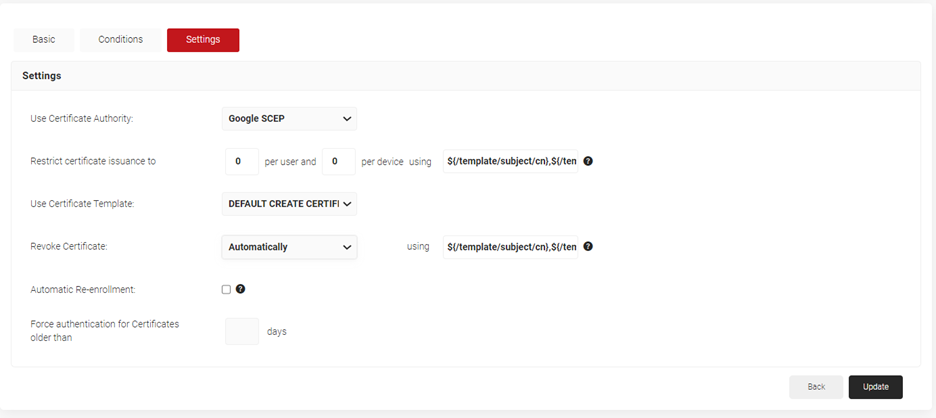
- Click Update.
Configuring Network Policy
To configure network policy:
- Go to Policy Management > Network Policies.
- Click Add Network Policy.
- In the Basic section, enter the name of the network policy in the Name field.
- In the Display Description field, enter a suitable description for the network policy.
- Click Save.
- Select the Conditions tab.
- Select Match All or Match Any based on your requirements to set authentication criteria.
- Click Add rule.
- Expand Identity and click Select adjacent to the Role option.
- Click Save.
- The Role option appears under the Conditions tab.
- From the Role Equals drop-down list, select the role policy you created earlier.
- Select the Settings tab.
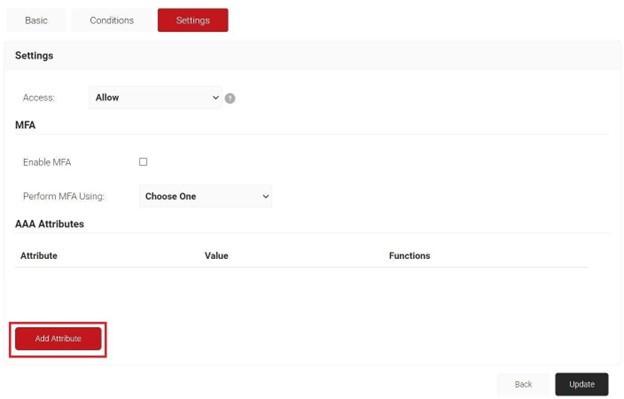
- Click Add Attribute.
- From the Dictionary drop-down list, select Radius:IETF or Custom.
- From the Attribute drop-down list, select an option.
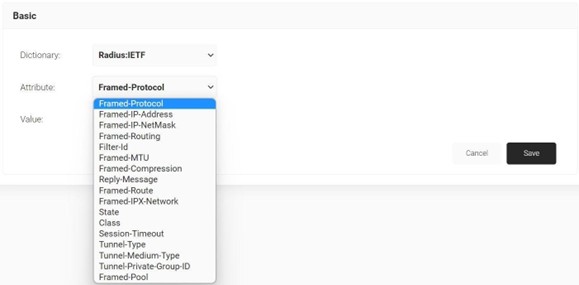
- In the Value text box, enter a value for the attribute.
- Click Save.
Configuring Google Cloud Certificate Connector
- Log in to the Google Admin console.
- Navigate to Devices> Networks > Secure SCEP.
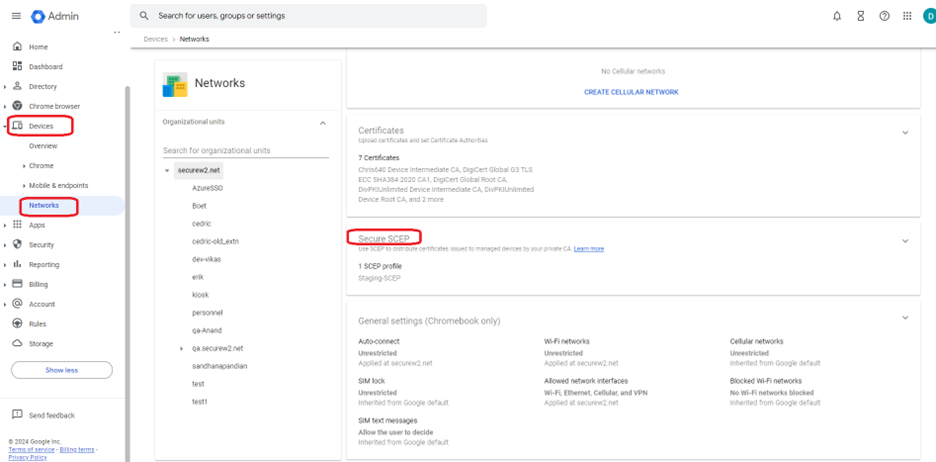 Click on Download Connector.
Click on Download Connector.
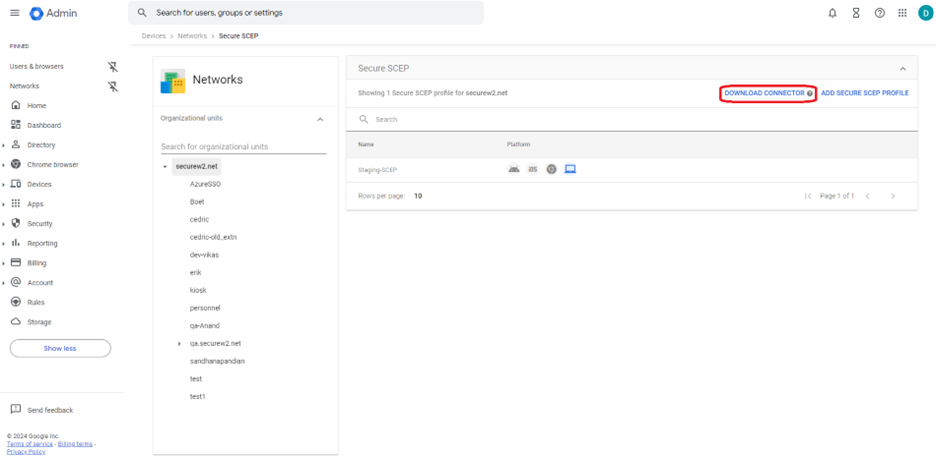
- Click Download in the Install Google Cloud certificate connector section. The .exe file downloads.
- Run the downloaded connector file (google-cloud-certificate-connector-setup.exe). The Google Cloud Certificate Connector Installer wizard will open.
Note: If the Microsoft Defender Dialog-box displays an Unknown publisher warning, click on the Run Anyway button.
- In the Welcome screen of the Cloud Certificate Connector wizard, click on the Next button.
- In the License agreement screen, select the I accept the terms of the license agreement radio button and click the Next button.
- In the Installation type screen, click the Anyone who uses this computer radio button and then click the Next button.
- In the Destination folder screen, retain the default destination folder under “C” drive and click Next.
- Click the Next button in the Program Folder screen.
- In the Windows services screen, enter the user credentials (username and password) to run the service. Click Next.NOTE: Enter the username in the computer\user or domain\user format.
- In the Start installation screen, click Next.
- Once the Installation is finished, the Installation Completed screen is displayed. Click Finish.
- Click Download in the Download connector configuration file section. The “config.json” file downloads.
- Navigate to the Get a Service Account key section, and click on the Generate key. The “key.json” file downloads.
NOTE: Place the key files and configuration (config.json and key.json) into the Google Cloud Certificate Connector folder, typically: C:\Program Files\Google Cloud Certificate Connector.
- Launch the Windows Services application. Right-click the Google Cloud Certificate Connector service and select the Start option.
Trusted Certificate Profile for RADIUS Server CA
You should configure the Trusted Certificate Profile with the certificate of your RADIUS server certificate’s issuing authority. This will make the devices trust your RADIUS server by validating the RADIUS server certificate. You can achieve this server validation in the profile configuration by adding the Root and/or Intermediate Certificate Authority (CA) certificates that issued the RADIUS server certificate. When you assign this profile, the Chromebooks receive the trusted certificates.
Exporting the SecureW2 Intermediate CA
Follow the steps to export the SecureW2 Root and Intermediate CAs from the JoinNow MultiOS Management Portal.
- Log in to the JoinNow MultiOS Management Portal.
- Go to PKI > Certificate Authorities.
- In the Certificate Authorities section, click the Download link for the Intermediate CA created earlier This certificate is imported when you set up the trusted certificate profile described in the following section.
Uploading Intermediate CA in Google Console
- Navigate to the Certificates section in the Google Admin console.
- Click ADD CERTIFICATE.
- In the Name field, enter a name for the certificate authority.
- Click Upload. Choose the Intermediate CA certificate downloaded earlier and click Open.
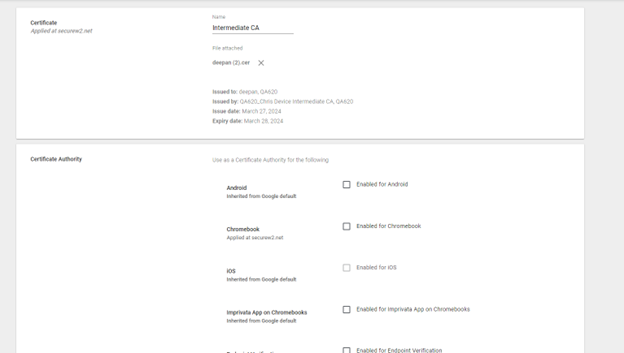
- Select the Enabled for Chromebook option.
- Click ADD.
Exporting the Trusted RADIUS Server Root CA Certificate
This section lists the steps to export the RADIUS server Root CA certificate from the JoinNow MultiOS Management Portal.
- Log in to the JoinNow MultiOS Management Portal.
- Navigate to Device Onboarding > Network Profiles.
- Click the Edit link of the network profile configured earlier.
- In the Certificates section, click Add/Remove Certificate.
- Check the checkbox next to DigiCert Global Root CA (Mon Nov 10 00:00:00 UTC 2031) as shown in the following screen.
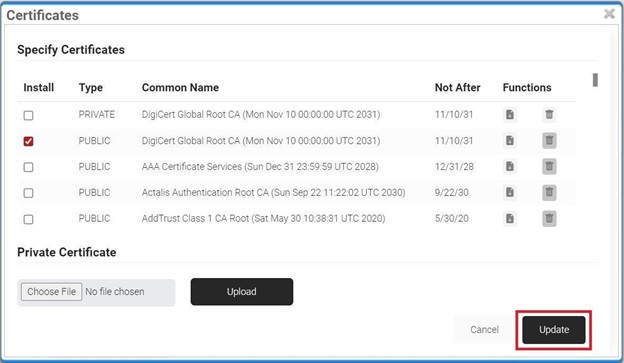
- Click Update.
- The CA appears in the Certificates section.
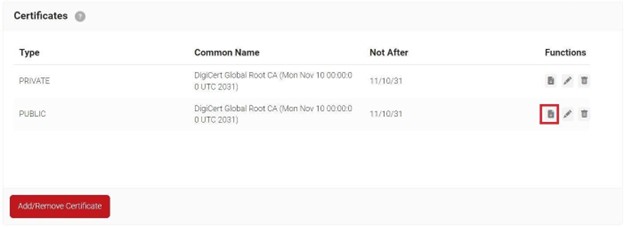
- Click Download.
Uploading RADIUS Server CA in Google Console
- Navigate to the Certificates section in Google Admin console.
- Click ADD CERTIFICATE.
- In the Name field, enter a name for the certificate authority.
- Click Upload. Choose the Intermediate CA certificate downloaded earlier and click Open.
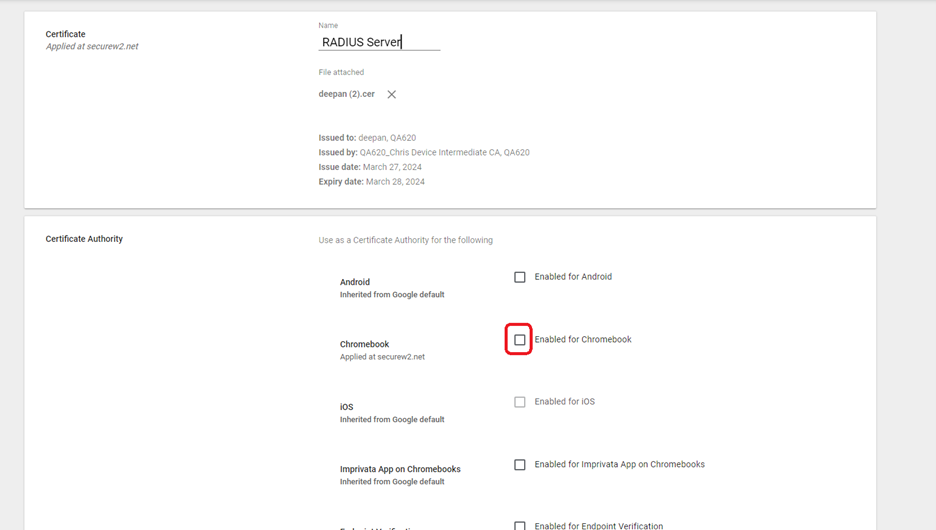
- Select the Enabled for Chromebook option.
- Click ADD.
Configuring SCEP Profile in Google Console
- Log in to the Google Admin console.
- Navigate to Devices > Networks.
NOTE: Leave the top organizational unit chosen to apply the setting to everyone. Choose a child organizational unit instead. Due to a known problem, we recommend that you configure the SCEP profile for each organizational unit to which you wish the profile to apply.
- Click Create SCEP Profile after selecting the organization.
- Click Add Secure SCEP Profile.
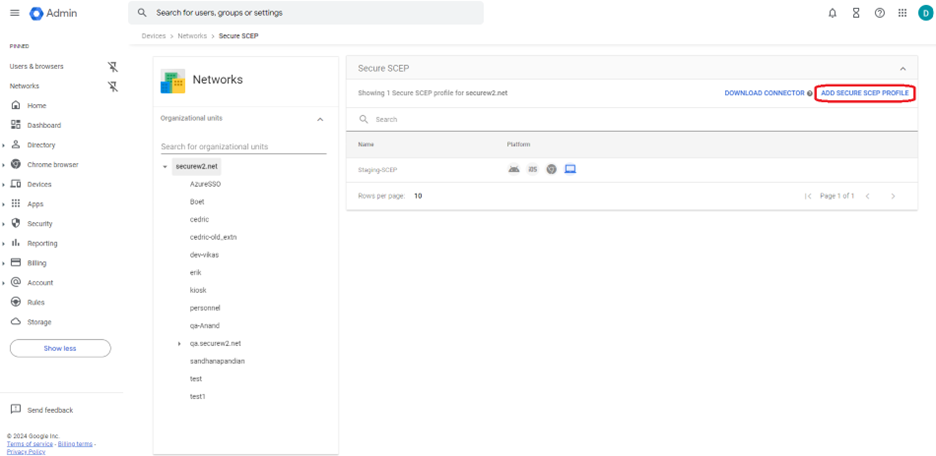
- In the Device Platforms section, select Chromebook (Device).
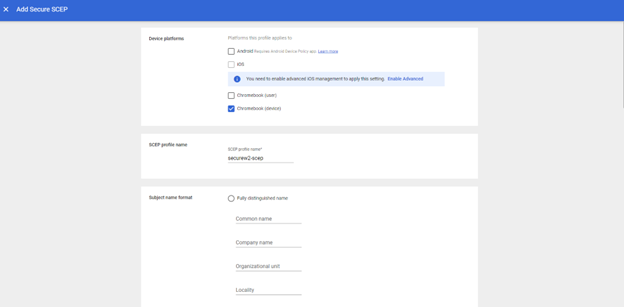
- In the Subject name format section, click on Fully distinguished name radio button.
- In the Common name field, enter ${DEVICE_SERIAL_NUMBER}
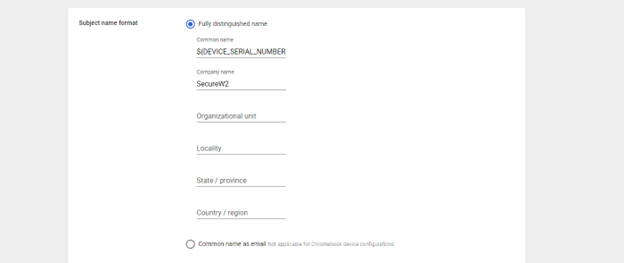
- In the Subject alternative name field, choose Custom.
- From the Subject alternative name type drop-down, select RFC822. In the adjacent field, enter ${DEVICE_SERIAL_NUMBER}.
- In the Key usage field, select Key Encipherment.
- In the Key size (bits), select 2048.
- In the Security section, select Strict.
- In the SCEP server URL field, copy paste the URL from the .csv file created in Generate a SCEP URL and Secret section.
- In the Extended key usage field, select Client authentication.
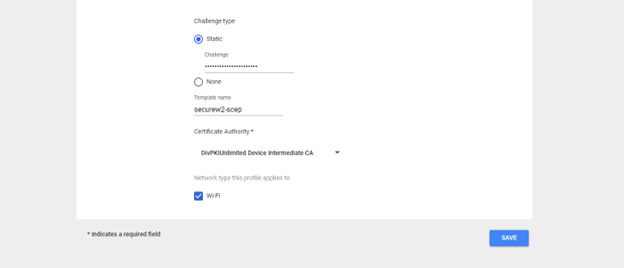
- In the Challenge type, select Static. In the field for challenge, copy and paste the API Secret from the .csv file.
- In the Template name field, enter a name for the SCEP template.
- From the Certificate Authority drop-down, select the certificate authority created for this SCEP organization.
- Click Save.
Configure 802.1X Wi-Fi for Certificate-Based Authentication on Chromebook
The last thing we need to do is configure the network settings that will be pushed to our Chromebooks so that they will authenticate to our SSID using SecureW2 for certificate-based Wi-Fi authentication.
- Navigate to Devices > Networks > Wi-Fi > Add Wi-Fi
- Under Platform access, select Enabled for Chromebooks (by device)
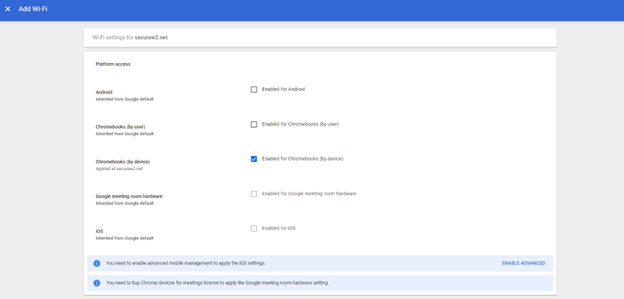
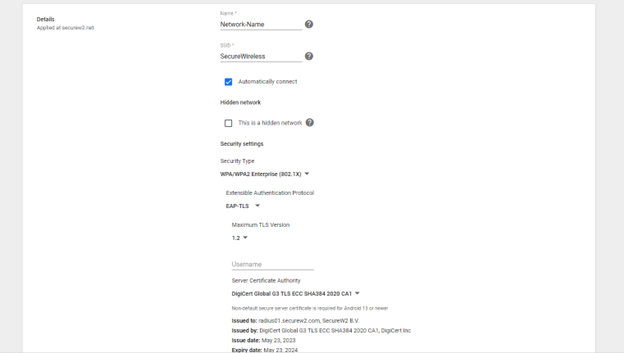
- In the Name field, enter a name for your Wifi.
- In the SSID field, enter a name for your broadcasting SSID.
- Enable the Automatically connect
- From the Security type drop-down, select WPA/WPA2-Enterprise (802.1X).
- Set the Extensible Authentication Protocol to EAP-TLS. Select Maximum TLS Version as 2.
- For the Username field, enter ${CERT_SAN_EMAIL} or ${CERT_SAN_UPN}.
- From the Server Certificate Authority drop-down, select the RADIUS Server Certificate’s Issuer CA chain you uploaded earlier.
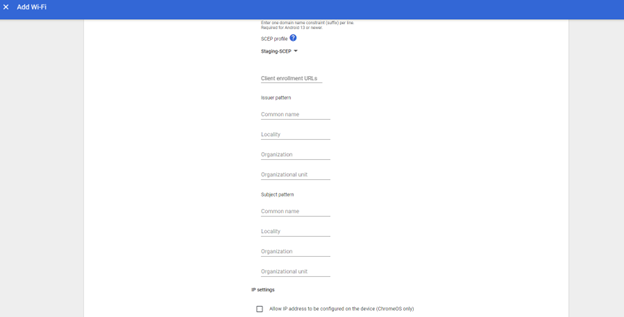
- From the SCEP profile drop-down, select the SCEP profile created in the earlier step.
- Under the DNS settings section, select Automatic Name Servers.
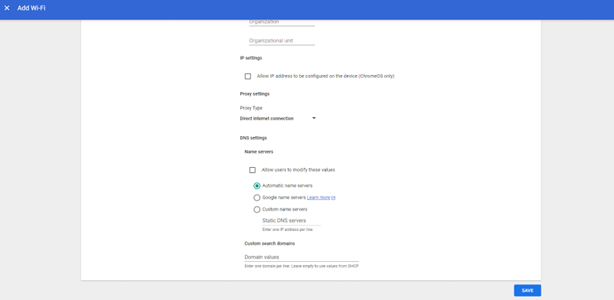
- Click Save.
Chromebooks for your organization can now be enrolled via the SCEP protocol. For assistance in case of queries/enrollment failures, contact support@securew2.com
Superior Google Chromebook SCEP Certificate Auto-Enrollment
With the last save, your network is now certificate-ready. The company may then complete any network configurations that will be delivered to the managed Chromebooks and begin the registration process. Managed Chromebooks will be enrolled for X.509 digital certificates, and all devices will be appropriately set up for secure 802.1X network access.
Support for uniquely identifying and reporting Chromebook devices has been introduced to SecureW2’s Management Portal. You can also auto-enroll for certificates and utilize powerful identification and device monitoring features for each network connection using a sophisticated Chrome Extension with Google-approved communications.
Are you ready to begin onboarding your own managed Chromebooks? We believe in constantly upgrading ourselves to keep our ever-expanding customer base ahead of the curve. If you’re keen to expand your cybersecurity horizons, here’s our pricing to learn more.