Key Points
- The authentication strengths framework enables organizations to enforce different authentication assurance levels from basic MFA to phishing-resistant methods.
- Phishing-resistant methods like CBA and FIDO2 offer cryptographic, device-bound security that protects against credential phishing and session hijacking, making them ideal for securing high-privilege access.
- SecureW2 simplifies CBA by integrating with Entra ID and Intune for automated certificate provisioning and policy enforcement, enabling phishing-resistant access controls without disrupting user experience
As cyberattacks become more targeted and identity becomes the core of security strategy, IT administrators are rethinking how users authenticate to sensitive resources. Organizations widely adopt Multi-Factor Authentication (MFA) to mitigate the risks of compromised passwords; however, increasingly sophisticated phishing techniques expose the limitations of traditional MFA.
In response, Microsoft Entra ID introduced a more nuanced approach called Authentication Strengths, allowing Conditional Access policies to enforce stronger, more reliable forms of authentication based on the level of risk and sensitivity of the resource.
In this article, we’ll break down what authentication strengths are, how they differ from traditional MFA, how they integrate into Conditional Access policies, and why certificate-based authentication (CBA) is one of the most practical ways to implement phishing-resistant security at scale.
What Are Authentication Strengths?
Admins use authentication strength as a Conditional Access control to define which combinations of authentication methods users must use to access an app or resource. This will enable administrators to select stronger authentication methods for more critical resources or weaker authentication methods for non-sensitive applications.
Microsoft currently defines authentication strengths in three tiers:
- MFA strength
- Passwordless MFA strength
- Phishing-resistant MFA strength
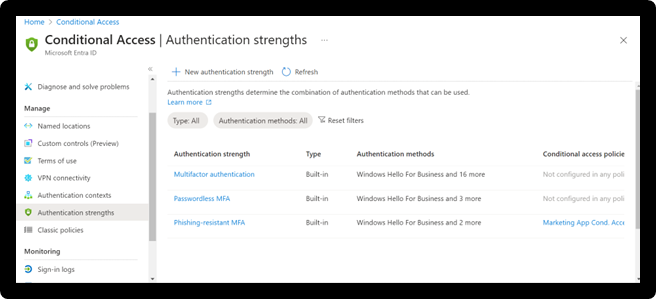 Authentication strengths available by default
Authentication strengths available by default
MFA Strength
This is the baseline level of secure access. It requires at least two factors from the classic trio: something you know (a password), something you have (a phone or OTP), or something you are (biometrics). It also gives your users the freedom to choose how they authenticate to a given resource, as it supports the broadest authentication options.
The supported authentication options are the following:
- FIDO2 security keys
- Windows Hello for Business
- Certificate-based authentication (CBA, MFA)
- Microsoft Authenticator app
- Temporary access pass
- Password + something you have
- Federated single-factor + something you have
- Federated multi-factor
Passwordless MFA Strength
Passwordless MFA is the middle tier in terms of strength, and can be used to eliminate the insecurity posed by passwords. Organizations use methods like Windows Hello for Business and hardware-tied biometrics or PINs for authentication. These approaches typically offer stronger security and better user experience, but their reliability varies based on device compliance. It supports the following authentication methods:
- FIDO2 security keys
- Windows Hello for Business
- Certificate-based authentication (Multi-factor)
- Microsoft Authenticator application
Phishing-Resistant MFA Strength
The highest tier, phishing-resistant MFA strength, comprises authentication methods designed to prevent all known forms of phishing attacks. It only supports the following authentication methods:
- FIDO2 Security key
- Windows Hello for Business
- Certificate-based authentication (Multi-factor)
The phishing-resistant method is the preferred way of authentication, especially if you have a high security requirement. The table below lists the pros and cons of adopting each level of authentication strength.
Why Basic MFA Is No Longer Enough
Basic MFA was once considered secure enough for securing identity. However, its weaknesses have become increasingly apparent. Attackers increasingly exploit human behavior by tricking users into approving malicious requests or stealing session tokens post-authentication. Real-time phishing kits can intercept MFA codes, making traditional methods vulnerable and reinforcing the need for phishing-resistant authentication. As a result, basic MFA is no longer sufficient for users with access to sensitive data or administrative privileges.
Phishing-resistant authentication, which binds credentials to devices and uses asymmetric cryptography, makes these attack methods virtually impossible. Credentials never leave the device and cannot be phished, guessed, or replayed. This is why organizations, including federal agencies like CISA, are being urged to adopt phishing-resistant methods, especially for high-value targets.
How Authentication Strengths Work with Conditional Access
In Microsoft Entra ID, Conditional Access policies now offer enhanced control over MFA. Beyond simply requiring MFA, these policies can dictate the specific strength of the MFA method, thanks to the integration of authentication strengths.
For example, IT administrators can configure a Conditional Access policy to permit access to internal productivity apps using basic MFA, while enforcing phishing-resistant authentication for financial systems or admin portals. This enables tiered access strategies that match the application’s sensitivity with the authentication method’s assurance level.
Organizations can define custom authentication strength policies in Entra ID, then assign those policies to Conditional Access rules. This level of granularity helps enforce Zero Trust principles by ensuring that only users who authenticate using approved, secure methods can access sensitive data.
Phishing-Resistant Authentication: FIDO2 vs Certificate-Based
FIDO 2 Security Keys
FIDO2 security keys are hardware devices that contain cryptographic keys for authentication. The devices are typically USB but could also use Bluetooth or NFC.
To authenticate, users register their device with the online service by performing gestures, such as pressing a button or providing a fingerprint. This action transmits their public key to the service, then registers it under the user’s name.
Drawbacks of FIDO2 Security Keys
FIDO2 security keys appear straightforward on paper, but they also come with their share of security concerns. To begin with, they require completely separate hardware for storing the user’s cryptographic keys. This requirement for additional hardware creates its plethora of complications.
For example, if a user’s hardware is lost, they would need to re-registrater. This not only takes a lot of valuable administrative time but also requires the organization to procure new hardware for each user.
Administrators can require users to register a spare key to prevent costly hardware loss. However, this also incurs another monetary cost. Imagine having to pay to duplicate every single key?!
The effectiveness of a security key hinges entirely on the end-user. If a user misplaces or forgets their key, they face a choice: retrieve it, or lose access to essential resources. Both scenarios inevitably lead to decreased productivity.
Furthermore, Entra ID cannot link specific security key serial numbers to individual users. Entra ID can only identify the make and model of the key used for authentication. This limitation means keys could be improperly shared among employees, potentially compromising access and authorization levels.
Certificate-Based Authentication
Certificate-Based Authentication (CBA) offers a robust and highly secure method for verifying user identities, contrasting with less secure methods such as password-based authentication. This approach relies on X.509 digital certificates installed on a user’s device, issued by a trusted Certificate Authority (CA). CA is responsible for verifying the identity of the certificate applicant and digitally signing the certificate to confirm its authenticity.
When users attempt to access a resource or application, their device presents its X.509 certificate to the authentication server. The server then validates the certificate by checking its digital signature against the public key of the issuing CA, ensuring the certificate hasn’t been tampered with and was indeed issued by a trusted source. The system validates the certificate by checking its validity period and confirming it hasn’t been revoked.
The use of strong cryptographic principles within CBA makes it highly resistant to common cyberattacks such as phishing, man-in-the-middle attacks, and credential stuffing, significantly enhancing the overall security posture of an organization.
FIDO2 is ideal for targeted, high-assurance use cases where strong, device-bound authentication is necessary. However,CBA offers a more flexible and cost-effective solution for securing access across the entire organization, especially when automated systems handle certificate management without requiring user involvement.
Drawbacks of Certificate-Based Authentication
Deploying Certificate-Based Authentication often presents a significant hurdle: constructing and maintaining a Public Key Infrastructure (PKI). Operating a PKI independently is challenging, requiring specialized knowledge and practical expertise in cryptography. However, it’s not necessary to establish a PKI from scratch. Dynamic PKI services enable you to leverage the robust security of certificates, without any of the hassle or expense that comes with building your own PKI.
In CBA, end-users may inadvertently select incorrect certificates or cancel the certificate prompt during authentication. Users can close and reopen their browser windows for that specific profile if this occurs. For example, if you encounter these issues while working on the “AA profile” in Google Chrome, you’ll need to close all browser windows associated with the “AA profile.”
| Feature | FIDO2 Keys | Certificate-Based Authentication |
| Device Support | Mostly modern OS, browsers | Works on all OS platforms, including legacy |
| Deployment Complexity | Requires physical key distribution | Can be automated via Intune, Jamf, GPO |
| Identity Mapping | Directly tied to user/device | Leverages existing PKI and identity records |
| Use Case Fit | Best for privileged users | Best for organization-wide zero trust policies |
How SecureW2 Simplifies Phishing-Resistant Access with CBA
CBA stands out as a highly secure authentication method, and is easily one of the most secure authentication methods supported by Entra ID’s Authentication Strength requirements. This method, leveraging digital certificates for identity verification, offers the strongest defense against common attack vectors, like phishing and credential theft.
However, implementing a certificate-driven security infrastructure, while seemingly complex, can be streamlined and simplified with the right tools. SecureW2 offers a comprehensive solution through its managed Dynamic PKI, designed to provide organizations with everything necessary to deploy and manage digital certificates seamlessly.
Our complete certificate lifecycle automation platform gives administrators the technology they need to manage the entire certificate lifecycle from distribution to revocation. Plus, we designed our PKI to integrate seamlessly with Microsoft ecosystems, enabling you to apply the policies and groups you already manage in Entra ID or Intune.
Want to learn more about what your network looks like with SecureW2? Contact us today for a free demo.
Frequently Asked Questions (FAQ)
Q1: What exactly are authentication strengths in Conditional Access, and why are they important?
Authentication strengths in Conditional Access enable administrators to define specific combinations of authentication methods that users must use to access particular resources. They are a crucial security enhancement, allowing for a more granular and adaptable approach to access control beyond simply requiring multi-factor authentication (MFA).
Authentication strengths are crucial for enforcing higher security, mitigating attacks, meeting compliance, improving user experience, and providing flexibility.
Q2: How do authentication strengths interact with existing Conditional Access policies?
Conditional Access policies use authentication strengths as a grant control. When a user attempts to access a resource and meets the policy conditions, the system evaluates whether the authentication method used satisfies the required strength. If the process meets or exceeds the required strength, the system grants access. If it doesn’t, the system either prompts the user to authenticate with a stronger method or blocks access entirely.
When a user attempts to access a resource, and Conditional Access policy conditions are met, the policy evaluates the required authentication strength. The user’s authentication method is compared to this requirement. If it meets or exceeds the strength, access is granted; otherwise, access is denied, prompting the user for a stronger method or blocking access.
Remembering authentication strengths doesn’t replace other Conditional Access controls like device compliance or approved client apps; they work together to provide a layered security approach.
Q3: Can I create custom authentication strengths, or am I limited to predefined options?
Yes, you can absolutely create custom authentication strengths. Microsoft Entra provides several built-in authentication strengths (e.g., “MFA Strength,” “Passwordless MFA Strength”), but the true power lies in the ability to define your own.
Custom authentication strengths offer flexibility in tailoring security. You can select, combine, name, and describe specific authentication methods (e.g., FIDO2, Microsoft Authenticator, certificate-based, Windows Hello for Business) to meet organizational needs and apply appropriate authentication levels to resources.
Q4: What are the best practices for deploying authentication strengths in my organization?
Deploying authentication strengths effectively requires careful planning and a phased approach. Here are some best practices:
- Audit current methods: Understand existing user methods and critical applications.
- Identify sensitive resources: Prioritize applications, data, and roles needing strong authentication.
- Communicate clearly: Inform users about changes and provide instructions/training.
- Phased rollout: Begin with a pilot group or less critical application, then expand.
- Monitor and adjust: Regularly review reports and refine policies based on feedback.
- Leverage built-in strengths: Use them for common scenarios.
- Document policies: Maintain clear records of authentication strengths and rationale.