Key Points
- Misconfigured or missing server certificate validation in WPA2-Enterprise makes networks vulnerable to man-in-the-middle (MITM) attacks, allowing credential interception.
- Proper client setup guarantees that devices authenticate RADIUS server certificates, which secures the EAP authentication process and prevents rogue SSID exploitation.
- SecureW2 provides advanced onboarding solutions that automate certificate-based authentication, enforce server validation, and safeguard against MITM vulnerabilities.
Your users have strong, unique passwords, your networks are protected with WPA2-Enterprise encryption, and you use 802.1x for authentication. WPA2-Enterprise is the gold standard when it comes to security, so you should be safe right? Think again.
Our experience helping all sorts of customers deploy WPA2-Enterprise in all sorts of environments has shown us that while many network administrators are eager to roll out a more secure wireless option, the process of manually enabling and configuring devices on the network can be a burden. Mishaps in the onboarding process are frequent and can lead to a variety of security concerns for both the user and the enterprise. Click here to learn more about our #1 rated WPA2-Enterprise onboarding client that works for any OS.
The diversity of client devices is growing every day, and the steps required to properly secure these devices can be very different. How can you ensure your users are protected completely? Configuring your device with a certificate that must authenticate to the RADIUS server prevents potential hackers from gaining access to your organization’s wireless network.
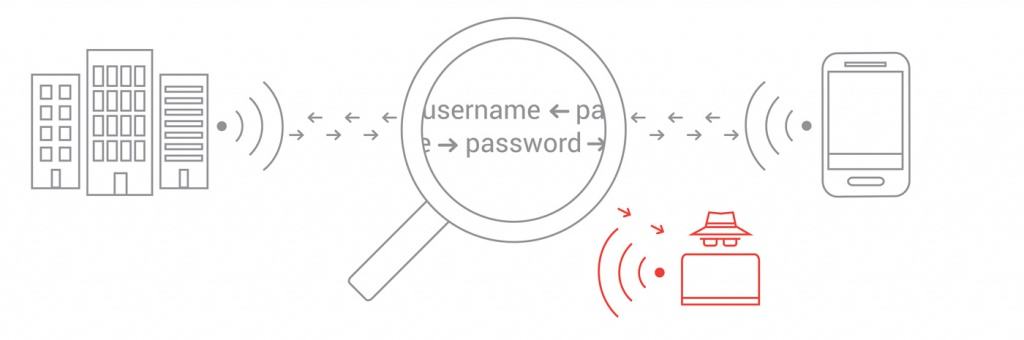
Misconfigured Certificate Validation Makes WPA2-Enterprise Vulnerable
What’s the danger in NOT correctly enabling server certificate validation? Through a man-in-the-middle attack (MITM), an attacker with malicious intent can easily set up a rogue network and mimic the SSID in order to steal personally identifiable information such as passwords and banking information. Server certificate validation is similar to a handshake between the server and the device, making it significantly more difficult to execute a MITM attack during the authentication phase.
The typical MITM attack is designed to trick a user into sending their credentials to an attacker rather than the authorized server. In WPA2-Enterprise, the first step of the authentication phase is the client-server handshake, which occurs when the client asks for the server certificate. If the certificate check passes, the client or supplicant will determine if the certificate is valid. The cached user credentials will be sent off, and the 802.1x authentication will proceed.
Certificate Verification for 802.1x Authentication
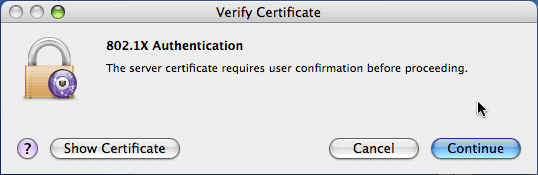
If the certificate is unknown to the client, you may be prompted (depending on the operating system) with a certificate warning. If the user opts to continue, their credentials, which in many cases is their Active Directory username and password hash, will be sent to the server, which in the case of a MITM, may be the attacker.
Use a Secure Onboarding Software for WPA2-Enterprise
Configuring clients and supplicants to check the server certificate before sending their credentials is the only reliable way to prevent MITM attacks. SecureW2 offers affordable options for organizations of all shapes and sizes. Click here to inquire about pricing.