Key Points
- Group Policy Object (GPO) is a Windows feature that automates configuration management across connected devices in a domain.
- AD CS works with GPO to issue certificates to managed devices, but it has limitations, such as the inability to search for individual certificates.
- SecureW2's PKI integrates seamlessly with Microsoft GPO and modern platforms like Intune, offering enhanced functionality and flexibility.
Enterprises that use Public Key Infrastructures (PKI) will have to issue and manage tens or even hundreds of thousands of digital certificates. Keeping track of all those certificates may seem overwhelming, which is why many smaller organizations with limited IT resources use a handful of SSL certificates. However, there is another solution that is often overlooked.
Windows environments can use Active Directory Certificate Services (AD CS), combined with Group Policy (GPO), to implement auto-enrollment and allow all networks users and devices to enroll for a certificate. AD CS provides the foundation for Microsoft admins to build a PKI and manage certificates. Including auto-enrollment in the PKI plan is a must for any network.
The Benefits of Certificate Auto-Enrollment
When an organization is dealing with a massive amount of certificates, it’s easy to overlook minor security gaps which can fester if not dealt with immediately. For starters, every certificate will expire. Organizations that manage thousands of workstations each with their own certificate can easily miss a certificate failing to renew within their GPO-defined renewal threshold. The effect could range from a minor impact like a user not being able to log in to a major issue like not being able to access mission-critical resources. In order to fix this, admins will have to dig through thousands of certificates to find the ones on the brink of expiration, kind of like finding a needle in a haystack.
A certificate auto-enrollment solution takes away the workload from the admin so they no longer have to manually search for certificates that failed to renew. With certificate auto-enrollment and GPO, admins have a much easier time finding certificates that are about to expire or even out of compliance, as GPO updates regularly. Auto-enrolled certificates that fail to renew can be hard to catch, until it negatively affects your network. Implementing certificate auto-enrollment is a best security practice, although there are some areas where AD CS falls short.
The Drawbacks of using AD CS with GPO
AD CS provides a foundation for Windows admins to build a PKI and is widely used due to the industry’s reliance on Microsoft legacy systems, like GPO, NPS, and AD. There’s a solution to provision certificates to AD-domain managed devices, but not anything for non-Windows devices. On top of that, AD CS is not compatible with macOS devices.
AD CS is also a legacy system, requiring an on-premise connection. That makes it difficult for Microsoft environments to fully transition their networks to the cloud. Admins would have to further entrench their networks on-prem and find workarounds to implement cloud capabilities. As the industry is rapidly moving towards cloud solutions, AD CS environments are stuck with outdated legacy systems that won’t be compatible with new technologies.
As with on-prem PKIs, they take an entire team of PKI experts for implementation and regular management. This ends up costing organizations a hefty price in licensing fees, infrastructure costs, and disaster recovery. Luckily, there is a more cost-effective PKI solution that can integrate with AD CS and GPO for seamless certificate auto-enrollment on all network devices, SecureW2’s Managed PKI.
Certificate Auto-Enrollment for Non-Windows Managed Devices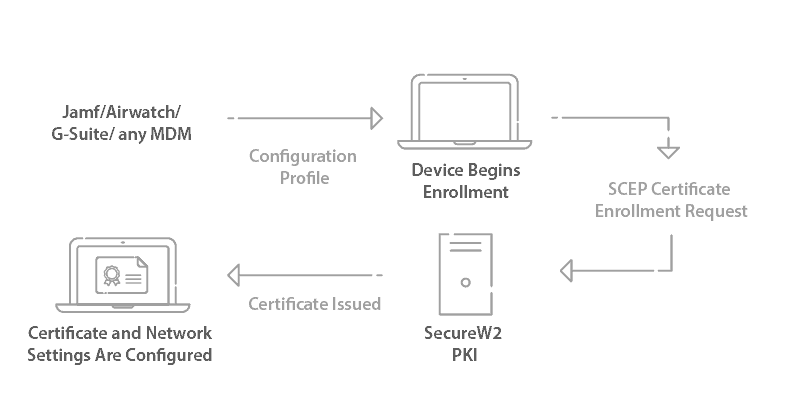
SecureW2’s PKI comes with JoinNow onboarding software that streamlines the wireless network onboarding for users via a self-service method. Admins can set up powerful SCEP Gateway APIs to send configuration payloads containing 802.1X settings and distribute certificates to all managed devices, including non-Windows devices.
Instead of complicated configuration instructions that only confuse end users and increase the amount of help-desk tickets, JoinNow allows network administrators to completely streamline their network connectivity. End-users download the institution’s configuration package (either from an on-premise web server or the cloud), follow a few simple on-screen prompts, and get connected in no time.
Certificate Auto-Enrollment for AD Domain Managed Devices
For AD domain-managed devices, admins can integrate SecureW2 with Microsoft Intune to build powerful WSTEP gateway APIs and configure GPO to send out a configuration profile to their domain-joined devices that will automatically enroll the device for a certificate and configure it for certificate-based EAP-TLS authentication, the most secure authentication protocol around.
With SecureW2’s PKI, JoinNow onboarding software, and Gateway APIs, admins can set up seamless certificate auto-enrollment and not have to worry about a misconfigured device or expired certificate negatively impacting their network. Plus, our software comes at an affordable price.