Key Points
- 802.1X authentication uses supplicants, authenticators, and a RADIUS server to validate devices and users before granting access, improving network security.
- Set up a RADIUS server, create profiles, and secure wireless networks with WPA-2 enterprise to configure 802.1X on Ubiquiti UniFi devices for better control and security.
- SecureW2's Cloud RADIUS provides passwordless authentication for modern cloud-based networks, improving resilience and efficiency.
In an era where network infrastructures must run smoothly, protecting sensitive data and securing connections is crucial. Ubiquiti UniFi is a market leader in networking solutions, providing a dependable and scalable platform recognized for its strength and durability. Ubiquiti Networks makes the Ubiquiti UniFi a complete networking solution. This unified and easily controlled network infrastructure comprises various hardware devices, such as routers, switches, and Ubiquiti access points, which are the foundation of their connectivity. These access points are essential components of the well-known UniFi ecosystem from Ubiquiti, which is recognized for its scalability, dependability, and easy management. Ubiquiti UniFi systems are known for being reliable, scalable, and easy to control with the UniFi Controller software.
Click here to learn how SecureW2 provided a client with an 802.1X solution.
The UniFi ecosystem enables users to centrally create and administer their networks, making it popular in residential and commercial situations. The UniFi devices all work together with a single management interface. This makes it easy for network managers to handle and monitor everything. Using 802.1X authentication, discussed in the article, makes the network even safer by ensuring that only authorized devices and people can connect.
Understanding Ubiquiti 802.1X Authentication
802.1X is an IEEE standard that makes it easier for devices on a network to share data safely. 802.1X authentication is a key part of network security that is meant to control who can enter a network and keep people who aren’t supposed to be there from getting in. 802.1X’s main job is to verify the identity of people or devices before letting them connect to the network. This makes sure that only authorized entities can join. By stopping unauthorized access and possible security leaks, this authentication method improves the general integrity of the network, especially in places where private information is sent.
Key Components
Three main components make 802.1X authentication work:
⦁ Supplicants,
⦁ Authenticators, and
⦁ Authentication servers.
Supplicants are devices that want to connect, like computers or smartphones. Authenticators, on the other hand, control who can join the network. The authentication server, which usually uses RADIUS (Remote Authentication Dial In User Service), verifies the user’s information, which completes the three-way handshake.
RADIUS facilitates a safe and centralized authentication method by linking the authenticator and the supplicant. It manages the verification process to improve network security, serving as the guardian of user credentials. Organizations may track user access, enforce regulations, and keep a centralized database of user data by utilizing RADIUS. The main idea behind 802.1X is that supplicants, authenticators, and servers work together to make a strong authentication system that takes network security to a whole new level.
Benefits of Implementing 802.1X
There are many perks for network managers using 802.1X. First, it ensures that only verified and authorized devices can get in. This lowers the risk of security threats and unauthorized access. 802.1X makes things safe and gives administrators more control over who can access what. They can give different devices or groups of users different jobs and rights. This makes managing networks easier, and it is easier to follow the rules set by regulators. Also, 802.1X is a flexible and scalable security system that can adapt to new network technologies and protect the network from new dangers. As we look at how to set up Ubiquiti UniFi, these benefits show how important 802.1X security is for making modern network systems safer.
Prerequisites for Setting up Ubiquiti UniFi Network
Assessing Network Infrastructure Readiness
Before setting up your Ubiquiti UniFi network, ensure everything is ready. To do this, the hardware and software needs must be carefully examined. For hardware, ensure you have the UniFi Security Gateway (USG), the UniFi Switch, the UniFi Access Point (AP), Ethernet wires, and a power strip. Ensuring all the hardware listed works together and matches the requirements is important for a smooth setup process. Taking care of software requirements simultaneously requires making a Ubiquiti account, which is a key step in starting the UniFi network setup. This first evaluation sets the stage for a strong network setup, creating a safe and well-integrated UniFi environment.
Creating a Network Map
Once the necessary hardware and software are set up, the next step is to create a detailed network map. Finding important network access points, like the link between the AP and the Switch or the connection between the USG and the Switch, helps you understand how the network is set up physically. At the same time, looking into user roles and permissions shows how devices and users communicate in the UniFi ecosystem. By listing these roles, administrators can give different groups of users specific entry rights, creating a customized and safe network environment. This proactive approach to network planning speeds up the next steps in the setup process and makes the UniFi network more secure and efficient.
Setting Up RADIUS Server
RADIUS (Remote Authentication Dial-In User Service) is key to making networks safer because it centralizes authenticating and authorizing users. RADIUS is key to authenticating people or devices trying to connect to a network. It was created to make security settings stronger. Implementing RADIUS adds an extra layer of identity verification to Ubiquiti UniFi. This is especially helpful when improving security and connecting to centralized identity sources like Active Directory. This part will go over the basics of RADIUS, explaining how it works in the login process and showing how it can be used in Ubiquiti UniFi network setups.
Installing and Configuring RADIUS Server Software
Install and set up the RADIUS server software before using the Ubiquiti UniFi RADIUS login. There are different kinds of RADIUS servers, and Microsoft’s Network Policy Server (NPS) job is often one of the most famous. NPS is commonly used, yet it has downsides. These may include configuration and scalability issues.
Despite its popularity, administrators should consider other RADIUS servers that better meet network needs and avoid NPS constraints. Many complex steps must be taken to set up an on-premise RADIUS server like NPS. These include adding the role services needed on a Windows Server and agreeing to accept extra services during installation. Next, the UniFi Access Points (APs) must be configured for RADIUS clients. The shared secret between the clients and the RADIUS server is an important part of this setup that needs close attention to detail.
Establishing Communication Between Ubiquiti UniFi and RADIUS Server
Once the RADIUS server is configured, the next critical step is to ensure that Ubiquiti UniFi devices and the Cloud RADIUS service communicate effectively. This includes setting up RADIUS clients using the UniFi Network dashboard, a vital step in the authentication process. With SecureW2’s Cloud RADIUS, the entire process is simplified and user-friendly, giving simplicity and flexibility. Before configuring the UniFi devices, ensure they are correctly connected to the network and that the Cloud RADIUS server is operational and accessible. Additionally, ensure that the required authentication methods, such as EAP-TLS, are supported and set correctly on both ends. These criteria lay the groundwork for a seamless and secure connection of Ubiquiti UniFi with Cloud RADIUS, improving network authentication capabilities.
Steps to Configure 802.1x on Ubiquiti Unifi Access Point
Setting 802.1X on Ubiquiti UniFi Access Points is critical for strong network security. Ubiquiti UniFi Access Points are critical to your network infrastructure because of their reliability and scalability. These access points provide high-performance wireless connectivity to your network. Let’s look at how SecureW2 Cloud RADIUS works with configuring 802.1X on Ubiquiti UniFi Access Point.
Configure Unifi AP for Certificate-based RADIUS Authentication
You can enable EAP-TLS authentication on your existing ubiquiti infrastructure by creating a new RADIUS profile using SecureW2 cloud RADIUS service.
- Go to Settings > Profiles in your uniFi access point.
- Click Create New Radius Profile.
- For Profile Name, enter the relevant profile name.
- For VLAN Support, check the box for Enable RADIUS assigned VLAN for wireless network.
- Open a new browser tab/window, and log into your SecureW2 Management Portal.
- Go to RADIUS Management > RADIUS Configuration.
- Copy the information for Primary IP Address, Port, and Shared Secret (to your clipboard or somewhere handy), and paste respectively into the Create New Radius Profile form for IP Address, Port, and Password/Shared Secret.
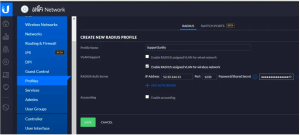
- Click Save.
Set Up an Open SSID on Unifi
With cloud RADIUS, we will set up an open onboarding SSID that helps user to redirect to BYOD self-enrollment portal. It helps to issue certificates automatically to the connected devices.
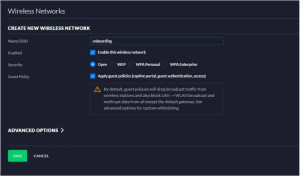
- Navigate to Settings > Wireless Networks > Create New Wireless Network.
- Enter the name of the SSID in the NAME/SSID section.
- Under Enabled, check the box to Enable this wireless network.
- Under Security, select the radio button for Open.
- Under Guest Policy, select the box “Apply guest policies (captive portal, guest authentication, access).”
- Click Save.
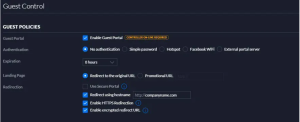
Ubiquite does not support the URL’s sub-domains, we would recommend you set up a local webserver with a rewritten URL that helps users to be directed to the SecureW2 landing page.
Add the webserver URL to “Redirect using hostname”:
- Navigate to Settings > Guest Control > Guest Policies.
- Check the Box “Enable Guest Portal”.
- Under Authentication –> Choose No Authentication.
- Check the Box “Redirect using hostname“.
- Click Save.
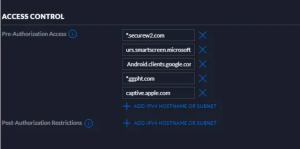
Add the ACL’s:
The User need to limit this SSID, it can be used only for self-service certificate enrollment and device network access configuration. For more information about SSID contact our expert support engineers.
- Navigate to Settings > Guest Control > Guest Policies.
- Check the Box “Enable Guest Portal“.
- Under Access Control → Pre-Authorization > add the ACLs (hostname or IPV4).
- Click on Apply.
Create a secure SSID
You must create a new wireless network connection in the UniFi network console and set the security to WPA-2 enterprise. After setting up the new RADIUS profile to the network, you can enjoy the benefits of the better security and enhanced user experience.
- From your UniFi Network console, go to Settings > Wireless Networks.
- Click Create New Wireless Network.
- For Name/SSID, enter the name of the SSID.
- For Enabled, check the box for Enable this wireless network.
- For Security, select the radio button for WPA Enterprise.
- For RADIUS Profile, click the dropdown and select the RADIUS profile you created.
- Click Save.
Modernizing Ubiquiti UniFi: Elevating Security With SecureW2’s Cloud RADIUS
The transition towards cloud-based identities is essential in the continuously growing network security domain. SecureW2’s Cloud RADIUS is a state-of-the-art solution specifically designed for modern cloud settings, effectively meeting the evolving network requirements of organizations. This section examines the mutually beneficial association between SecureW2’s Cloud RADIUS and Ubiquiti UniFi, highlighting a transformative change in network authentication. SecureW2’s Cloud RADIUS sets itself apart from the traditional RADIUS solutions. This innovative approach mitigates the risks associated with legacy authentication techniques, enhancing organizations’ resilience against credential theft.
Cloud RADIUS enhances network security by introducing a passwordless framework, freeing organizations from the limitations imposed by LDAP and AD servers. To prioritize cloud identities, his solution effectively interacts with Azure AD (Microsoft Entra ID), Okta, and Google environments, leveraging established policies to ensure highly secure network authentication.
The foundation of Cloud RADIUS is established through digital certificates, which play a crucial role in verifying the device and user context. This approach harmoniously aligns with the principles of Zero Trust Network Security. SecureW2’s Cloud RADIUS offers a solution that enhances network authentication by eliminating password requirements. This advancement contributes to a more secure, efficient, and user-friendly experience, particularly for organizations grappling with the intricate challenges of contemporary network security.
Navigating Ubiquiti Challenges with SecureW2’s Seamless Solutions
Users typically confront various issues, from security concerns to identity management challenges, while using Ubiquiti UniFi. Traditional setups might be exposed to security flaws in legacy protocols and credential theft. It becomes difficult to manage and secure identities, particularly in an era of remote work and cloud integration.
To solve these problems, SecureW2 presents a passwordless approach that easily aligns with today’s security standards. By removing LDAP and AD server requirements, SecureW2’s Cloud RADIUS frees organizations from the limitations of traditional password-based authentication. The simple integration with Azure AD, Okta, and Google environments makes the experience smooth by using current policies to provide strong network authentication. This innovative approach offers a safe, effective, and user-friendly substitute for standard Ubiquiti UniFi settings, addressing the complexities of identity management in the cloud era.
Deploying Ubiquiti 802.1X with Cloud RADIUS
As our review of configuring Ubiquiti UniFi networks draws to a close, it becomes apparent that SecureW2’s Cloud RADIUS can effectively mitigate the conventional obstacles in network security and identity management. We reviewed the details of setting up 802.1X security, installing RADIUS servers, and the problems that Ubiquiti UniFi users always have. SecureW2’s solution has the power to change things because it can usher in a time without passwords, protect organizations against identity theft, and work smoothly with modern cloud identities.
As you update your Ubiquiti UniFi network, SecureW2’s Cloud RADIUS will ensure the design is safe, efficient, and ready for the future. Take your Ubiquiti UniFi setup to the next level by learning to deal with today’s complicated security issues with SecureW2. Contact us today to start moving towards a cloud-integrated, password-free network environment that puts your organization’s safety first.