Key Points
- The EAP method requirements for WPA3-Enterprise vary based on whether we are using 192-bit mode or 128-bit mode.
- WPA3-Enterprise’s 192-bit mode exclusively supports EAP-TLS, which requires certificate-based authentication on both the client and the RADIUS server.
- Not all devices or network equipment fully support WPA3-Enterprise. Mostly, Windows and Linux often lack true 192-bit mode support.
- WPA2-Enterprise remains a reliable and widely supported alternative, particularly when combined with certificate-based EAP-TLS.
The only EAP method allowed in WPA3-Enterprise 192-bit mode is EAP-TLS, which uses X.509 certificates for client and server-side authentication. No other EAP authentication types are permitted, since they lack the cryptographic strength or mutual authentication required for the same. As WPA3-Enterprise becomes more prevalent in enterprise environments, it’s essential to understand which EAP methods it supports and why they are crucial for maintaining robust Wi-Fi security. Learn more about EAP-TLS authentication and how it works.
From WPA2-Enterprise to WPA3: A Security Evolution
WPA2-Enterprise is the gold standard for secure enterprise Wi-Fi. It uses the 802.1x authentication protocol and AES-CCMP 128-bit encryption. However, with growing threats and the increasing complexity of attacks, there have been some developments in enterprise protocols to further improve security parameters. WPA3-Enterprise introduces a more resilient framework, particularly with its optional 192-bit security mode.
WPA3-Enterprise comes in three modes:
- Standard Mode: It uses AES-CCMP with a 128-bit key, which is the same as WPA2 but with stricter authentication method requirements.
- Enterprise Transition Mode: WPA3-Enterprise Transition Mode is a feature that allows organizations to support both WPA2-Enterprise and WPA3-Enterprise devices on the same Wi-Fi network, during a gradual upgrade to WPA3.
- 192-bit Mode: Built for high-security environments like government and finance, using GCMP-256 encryption and requiring Suite B-compliant EAP methods.
What Are EAP Methods and Why Do They Matter?
Extensible Authentication Protocol (EAP) is a network authentication protocol often used alongside the 802.1X framework that enables identity-based authentication between the client device, access points, and RADIUS server. EAP allows secure transmission of credentials, or certificates, over encrypted networks and is not limited to a particular form of authentication. It is compatible with several authentication methods like public key encryption, digital certificates, smart cards, one-time passwords, and token-based systems, making it highly versatile.
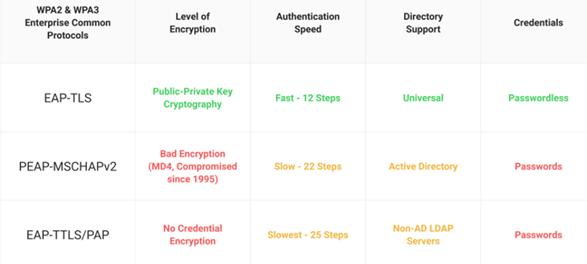
EAP-TLS is superior to other major credentials-based authentication protocols. It uses digital certificates, which reduces the risk surface that inherently comes with using credentials in PEAP-MSCHAPv2 and PAP. EAP-TLS offers relatively faster authentication compared to other protocols, and it integrates with most cloud-based directories by using certificates for both client and server authentication.
EAP Requirements for WPA3-Enterprise (192-bit Mode).
EAP-TLS authentication protocol is a must for WPA3-Enterprise 192-bit mode.
To comply with 192-bit mode, the network must also meet Suite B/Commercial National Security Algorithm Suite standards, including:
- Support TLS 1.2 or 1.3.
- AES-GCM-256 encryption.
- Implement only Suite B-aligned cipher suites:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- Ensure both client and server are certificate-enabled.
Can Your Environment Support WPA3-Enterprise?
Despite WPA3-Enterprise being the most advanced authentication protocol, you must consider a few things:.
- Few operating systems appear to support it, and fall short in real-time deployments.
- Not all network infrastructure fully supports WPA3 Enterprise, or it might only work with select operating systems. For example, Windows 11 may require tuning to work properly with WPA3.
- Some access points and RADIUS servers don’t support the required cipher suites.
To help clarify what works and what doesn’t, take a look at what we’ve learned from testing WPA3-Enterprise across different platforms and environments.
| OS Support | Aruba | Meraki | Ubiquiti | Mist | Ruckus |
| Android 11 and Below | Poor Support | Poor Support | Poor Support | Poor Support | Poor Support |
| Android 12 and Above | Reasonable Support | Reasonable Support | Reasonable Support | Reasonable Support | Reasonable Support |
| iOS | Yes, but not 256-bit | Yes | Yes | Yes | Yes |
| macOS | Yes, but not 256-bit | Yes | Yes | Yes | Yes |
| ChromeOS | Yes, but not 256-bit | Yes | Yes | Yes | Yes |
| Windows (WPA3 Transition Mode*) | Yes, but not 256-bit | Yes | Yes | Yes | Yes |
| Linux | No | No | No | No | No |
We tested the three common WPA2/3-Enterprise authentication methods: EAP-TLS, PEAP-MSCHAPv2, and EAP-TTLS/PAP. These protocols worked well for all network infrastructures that supported WPA3-Enterprise. Passpoint was available for our Unifi and Mist testing infrastructure, though Mist did not support WPA3-Enterprise with Passpoint. Also, hidden SSIDs had no impact on the functionality of WPA3-Enterprise.
Windows and Linux don’t fully support “true” WPA3-Enterprise, so neither OS is included in the compatibility table. Windows devices, for instance, only support what’s known as “transitional WPA3,” essentially WPA2 with enhancements like Management Frame Protection (MFP), CCMP, and EAP-SHA256. However, Linux’s Wi-Fi UI doesn’t show WPA3-Enterprise, as it is still using the WPA/WPA2 EAP cipher with no MFP.
WPA2-Enterprise is Still the Smart Choice
If you are planning to upgrade to WPA3-Enterprise, it is essential to thoroughly test all your devices and network infrastructure beforehand. Since WPA-3 is not universally supported across platforms, understanding how your environment shall respond is a critical first step before moving forward. WPA3-Enterprise is a step forward, but it’s not always practical to immediately overhaul your entire wireless ecosystem.
WPA3 Enterprise represents a meaningful step forward in wireless security. However, given the current limitations in OSs and network infrastructure support, widespread adoption may take time. Still, WPA2-Enterprise combined with EAP-TLS certificate-based authentication offers a secure and scalable alternative that can immensely help secure your enterprise infrastructure. Click to learn more about configuring WPA-2 enterprise.