Key Points
- AITM attacks are a dangerous evolution of MITM attacks, specifically designed to defeat multi-factor authentication (MFA) by hijacking live authentication sessions
- Standard MFA methods, like one-time passwords and push notifications, are still vulnerable to AITM phishing because attackers can easily spoof the login pages where users enter their credentials or approve access
- Phishing-resistant certificate-based authentication (CBA) is a strong defense against AITM attacks because certificates are tied to the device, and only the public key is shared, leaving attackers nothing useful to steal
A traditional Man-in-the-Middle (MITM) attack primarily involves an attacker passively intercepting a communication channel to eavesdrop or steal static credentials, such as passwords. The Adversary-in-the-Middle (AITM) attack takes this a step further. Instead of just listening, the attacker actively sets up a proxy server to hijack a live, authenticated session, stealing the session cookie to gain access after the user has successfully authenticated with multi-factor authentication (MFA).
What Is an MITM Attack?
A MITM attack is a cyberattack that occurs when an attacker inserts themselves between two communicating parties, such as a user and a website, or two systems, without their knowledge. From this position, the attacker can eavesdrop, manipulate, or inject malicious data into the communication stream.
Common MITM attack methods include:
- Unsecured Wi-Fi networks: Attackers set up rogue hotspots to intercept user traffic..
- ARP Spoofing: Attackers forge Address Resolution Protocol (ARP) messages to reroute traffic within local networks.
- DNS Spoofing: Malicious actors tamper with DNS responses to redirect users to fraudulent websites.
MITM attacks often exploit unsecured or outdated protocols and target environments where data is transmitted in plaintext or with weak encryption. They rely heavily on gaps in user awareness and misconfigured network infrastructure.
MITM Attacks Workflow:
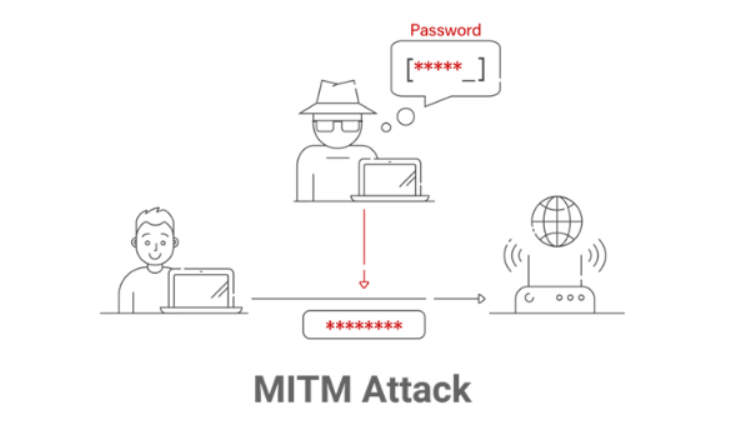
In MITM attacks, attackers position themselves between two entities to intercept data. They decrypt it using methods such as SSL stripping or social engineering to obtain valuable information, including login credentials and other sensitive data. They then modify the data or inject fraudulent responses. With stolen data, attackers can impersonate legitimate users to gain unauthorized access and deploy backdoors or rootkits to maintain control over the system.
What Is an AITM Attack?
An AITM attack is a far more advanced and targeted form of MITM, often deployed as part of a phishing campaign. Attackers specifically engineer it to defeat modern authentication methods, including MFA. AITM attacks typically leverage phishing kits or phishing-as-a-service (PhaaS) platforms like:
- EvilProxy
- Greatness
- Nighthawk
- Modlishka
These kits clone legitimate login pages (like Microsoft 365 or Okta), trick users into entering their credentials and MFA codes, and then instantly replay them. This allows the attacker to bypass MFA and gain session-based access to enterprise accounts without needing the victim’s password again.
AITM Attack Workflow:
- Phishing E-mail: A victim receives a legitimate-looking e-mail with a malicious link (commonly appearing as Microsoft 365, Google, or a financial service).
- Reverse Proxy: The user clicks through, landing on a phishing site that perfectly mimics the real login page but is an attacker’s proxy.
- Session Hijack: Credentials and MFA tokens entered are relayed directly to the real site, and any session cookies returned are intercepted and stolen.
- Account Compromise: Attackers immediately use the stolen cookies to access victim accounts, bypassing MFA even if the victim used OTP or app-based approval.
The user does receive their expected MFA prompt. The attacker is simply replaying it, in the background, to create a live, authenticated session for themselves.
Key Differences Between MITM and AITM
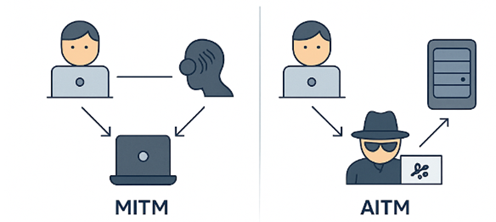
MITM attacks occur when an attacker covertly intercepts communication between a user and a server, typically by exploiting insecure networks( like public Wi-Fi) or using methods like ARP or DNS spoofing. The attacker’s primary goal is to steal sensitive data, like credentials, often by eavesdropping or altering information in transit. Traditional MITM attacks rely on intercepting unsecured data and generally cannot bypass strong MFA.
In contrast, AITM attackers use phishing sites and automated reverse proxy kits (such as EvilProxy) to intercept credentials and real-time MFA tokens. They lure victims to lookalike login pages, proxy every authentication step, capture session cookies after login, and gain full account access even when MFA is enabled.
| Feature | MITM | AITM |
| Attack vector | Network-level | Browser/session-level |
| Passive or active | Mostly passive | Always active and real-time |
| MFA-aware | No | Yes (explicitly designed to bypass MFA |
| Phishing involved | Sometimes | Almost always |
| Tools used | ARP spoofing, SSL stripping | EvilProxy, Modlishka, reverse proxies |
| Detection difficulty | Moderate | High (uses valid sessions) |
Eliminate AITM Attacks with Certificate-Based Authentication
Certificate-Based Authentication (CBA), powered by Public Key Infrastructure (PKI), is one of the most effective defenses against AITM attacks. CBA uses digital certificates and cryptographic keys. When a user logs in, their device proves its identity to the server using a securely stored private key that it never shares with anyone. Only the device with the correct private key can complete the authentication process.
Devices keep the private key secure by never sending it across the network or exposing it to the user, preventing phishing attacks. Authentication involves the server sending a unique challenge, which can only be correctly answered by the device holding the corresponding private key. An attacker in the middle cannot replicate this response.
CBA heavily relies on the EAP-TLS authentication protocol for wired and wireless VPN authentication, which utilizes certificates to enable both the client and the server to verify each other’s identity. This prevents users from connecting to malicious servers (like in an “Evil Twin” Wi-Fi attack) and ensures the server only accepts connections from trusted, authorized devices.