Key Points
- Certificate pinning locks an application or client to a specific server certificate or public key, ensuring that it only connects to trusted servers.
- However, certificate pinning is not scalable. With certificate rotation and limited validity, it isn’t a practical security approach in a network with BYOD and dynamic access policies.
- Device attestation verifies the identity, integrity, and compliance of a device before it’s granted access to the network. It is a scalable, verifiable technique for securing access at the device level, far beyond what pinning alone can offer.
Certificate pinning is widely used in networks to establish trust between client devices and servers. However, with enterprises shifting to dynamic BYOD and device trust policies, certificate pinning alone does not suffice to secure networks. Pinning merely validates the server, but fails to check if a genuine, untampered, and compliant device is connecting to the organizational network.
Device attestation ensures that a certificate and its corresponding private key are stored securely on the intended device. A certificate and private key embedded in a device cannot be tampered with, misused, or deployed on a compromised device. Private key attestation ensures that only genuine, untampered devices with securely stored private keys can establish trusted network connections.
Certificate pinning is not needed when devices are validated through MDM or IDP lookups and continuous monitoring. Rather than hardcoding trust to a single certificate, you can verify device identity and trust in real-time, delivering stronger security without the operational risks associated with pinning.
What Is Certificate Pinning?
Certificate pinning is a security technique that enhances SSL/TLS authentication by ensuring that a client only accepts a specific server certificate or public key during the TLS handshake. Certificate pinning operates at the application layer, where developers embed a list of authorized certificates or public keys within their applications. When a device connects to a server, it doesn’t just verify that the certificate is valid and signed by a trusted CA. It ensures that:
- The client certificate matches one of the pinned server certificates.
- The connection is terminated if no match is found, preventing unauthorized access.
How Certificate Pinning Works
Key Benefits Of Certificate Pinning
Certificate pinning blocks malicious actors from using compromised certificates to intercept network traffic. The attacker may have managed to obtain a CA-signed certificate, but if it doesn’t match the public key of the pinned certificate, they cannot establish a connection to the network.
This is particularly valuable in environments that handle sensitive data, like banking, healthcare, or government applications. Applications in these sectors often use pinning to ensure that data is transmitted only to verified, authorized servers, adding another layer of defense against eavesdropping or tampering.
The Problem with Certificate Pinning in Modern Environments
Certificate pinning is a common practice, but it is not foolproof. Some risks and disadvantages associated with it include:
Frequent Certificate Rotation
Certificate rotation replaces certificates periodically before they expire or become vulnerable, ensuring secure communication and minimizing the risk of MITM attacks. This is considered a best practice for maintaining security, but it comes with significant operational challenges.
With pinning, there should be an exact match between the server’s and the pinned certificate. If the pinned certificate isn’t updated on time, even a valid, CA-issued certificate will be rejected by the client. The result? Failed TLS handshakes and immediate service disruptions.
Shorter Certificate Lifespan
Certificates typically have shorter lifespans now. Usually, they are valid for up to one year. However, organizations like Google are pushing to reduce the validity of intermediate certificates to three months.
Limiting the lifespan of TLS certificates and private keys minimizes the window of opportunity for attackers in the event of a compromise. It also reduces dependency on certificate revocation mechanisms, which are inconsistently supported across clients, browsers, and CAs.
Short-lived certificates are designed to encourage automation and agility. Pinning, by contrast, locks systems into rigid certificate dependencies, making them incompatible with PKI best practices, such as automatic certificate revocation and renewals.
Pinning restricts flexible network connections, delays incident response during revocations, and isn’t scalable for a dynamic infrastructure. As a result, many organizations are moving toward more scalable, policy-driven trust models, such as private-key device attestation.
What Is Device Attestation?
Device attestation is a verification process to determine whether a device is genuine, untampered, and compliant with network access requirements. It uses hardware-backed checks and integrates with MDMs or device manufacturers to validate trust before issuing a digital certificate through a PKI.
This ensures that only verified, uncompromised devices can receive certificates and connect to enterprise resources.
How Does Device Attestation Work?
Device attestation is built on a secure hardware foundation called the Root of Trust (RoT) enclosed in a Secure Enclave or TPM. A secure enclave stores and handles cryptographic keys used for network security.
A device’s unique identity is established and provisioned through the RoT, either by generating keys directly on the device (via Onboard Key Generation) or injecting them from a trusted external source. In a managed environment, the keys form the basis for creating and storing credentials and authenticating devices.
Device attestation adds a critical layer of security by verifying that a device is genuine and uncompromised before it can access sensitive resources. In enterprise environments, it helps ensure both managed and BYOD devices meet trust standards.
Key Advantages of Device Attestation Over Pinning
Device attestation provides cryptographic proof of device integrity, rather than relying on static associations. While device pinning binds a server certificate to a client device, making it vulnerable to spoofing and MITM attacks, attestation verifies that the device is genuine, untampered, and compliant via hardware-backed TPMs or Secure Enclaves.
Differences between certificate pinning and device attestation:
| Feature | Certificate Pinning | Device Attestation |
| Security Scope | Server identity | Device identity + integrity |
| Trust Model | Static (hardcoded certificates) | Dynamic, policy-based trust |
| Certificate Rotation | Loses connectivity if not updated manually | Handled automatically via MDM/PKI workflows |
| Hardware Support | No hardware verification | TPM/Secure Enclave validation |
| Automation & Scale | Manual pinning is error-prone | API-driven, integrated with MDMs and IdPs |
| Certificate Lifecycle | Not supported | Automated issuance, renewal, and revocation through CRLs |
How SecureW2 Uses Attestation for iOS & Windows
Device attestation on iOS verifies firmware integrity, checks for tampering, and ensures the device runs a legitimate iOS version. Each Apple device is provisioned with a unique attestation key, which enables cryptographic proof of its authenticity during both the boot process and network access.
Additionally, SecureW2 supports private key attestation, ensuring that the certificate’s private key is securely generated and stored in the Secure Enclave or TPM, never exported or duplicated, thereby creating a hardware-bound trust anchor.
SecureW2 Automates Certificate Management in Managed iOS Devices
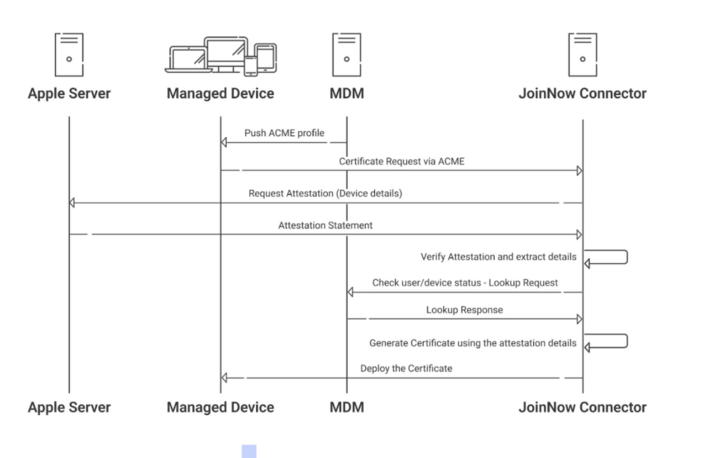
SecureW2’s Dynamic PKI uses the ACME protocol to automate certificate issuance for managed Apple devices. When a device requests a certificate, our PKI performs dual validation. First, it checks with the MDM, such as Jamf, to confirm enrollment and verifies the device’s legitimacy through Apple’s attestation server.
A certificate is issued to secure, trusted, and compliant devices upon successful checks and private key attestation. This eliminates the need for static pinning logic, enabling dynamic, posture-aware access with full certificate lifecycle automation.
SecureW2 Automates Certificate Management in Managed Windows Devices
Windows devices have a Trusted Platform Module (TPM) to secure private keys. Each TPM contains a unique Endorsement Key (EK) to verify the TPM’s authenticity. During certificate issuance, the device must possess the TPM-backed private key and validate its identity through the EK’s public key (EKPub). This process ensures the certificate is issued only to genuine, tamper-free hardware, creating a hardware-bound trust anchor.
SecureW2’s Dynamic PKI integrates with Microsoft Intune to automate this attestation-driven certificate issuance for both managed devices and BYODs. SecureW2’s Dynamic PKI verifies the TPM and device posture via Intune, ensuring that only compliant, trusted devices are granted access. This enables context-aware access control, eliminates credential-based risks, and strengthens Zero Trust security with minimal administrative overhead.
The Future of a Secure Network is Real-Time Trust
The future of secure access devices —trust-based access — lies in real-time, dynamic trust, not static pinning. Device attestation is scalable, API-driven, and hardware-backed, ensuring only verified, compliant devices receive network certificates.
By replacing certificate pinning techniques with automated attestation workflows, enterprises can reduce network outages, enforce policy-driven access, and dramatically strengthen their overall security posture. With native integration across identity providers and MDMs, device attestation is a foundation for secure, resilient network access.
SecureW2’s Dynamic PKI Verifies Trust With Device Attestation
Traditional certificate pinning binds a certificate to a device, but it lacks flexibility and fails to account for device posture or potential compromise. Our Dynamic PKI replaces this static approach with real-time device attestation, leveraging the ACME protocol to validate device authenticity before issuing certificates. For macOS and iOS, our Managed Gateway APIs ensure only genuine, compliant devices receive certificates, blocking unauthorized or tampered devices from accessing the network.
We integrate with Microsoft Intune for Windows and BYOD environments to automate the issuance of TPM-backed certificates based on verified device posture. This approach eliminates the operational burden of managing pinning logic, enabling context-aware, scalable access control aligned with Zero Trust principles.
Know more about our Dynamic PKI and how it helps secure managed devices.