Introduction
SecureW2 provides Dynamic PKI services that enable seamless certificate enrollment and management through the use of integrations with Identity and Device management systems.
A key benefit of this interoperability is the ability to combine multiple sources of truth, to make sure the presence of a certificate means a user/device is truly trustworthy.
In this integration guide, we will show you how to issue certificates using an API integration with Jamf, so we can validate device trust. But we will also validate that the certificate belongs to a trusted user in Okta. This will be achieved by including the user’s email address in our certificate templates, which is used as the key identifier during authentication.
This will enable SecureW2’s Cloud RADIUS to validate users in Okta during network authentication, as well as to validate any other attribute you might want to check, like Group Membership. Based on this validation, Cloud RADIUS either grants or denies network access and assigns the appropriate VLAN to the user’s device.
Prerequisites
The following are the prerequisites for integrating SecureW2’s PKI and Cloud RADIUS services with Jamf and Okta, respectively, for certificate enrollment and RADIUS authentication:
- An active account in JoinNow with an Ultimate subscription.
- An active subscription in Okta with admin privileges
- An active subscription in Jamf with admin privileges
Integrating JoinNow with Jamf for Certificate Enrollment
The following are the high-level steps to configure certificate enrollment with JoinNow:
Creating an Intermediate CA for SCEP Gateway Integration
As a best practice, SecureW2 recommends having a new intermediate CA for JoinNow SCEP Gateway integration with Jamf. The CA that issues certificates to BYOD devices should be separate from the CA that issues certificates to managed devices because managed devices do not require email notifications. You can disable email notifications for the dedicated CA issuing certificates to Jamf-managed devices.
To create a new intermediate CA:
- Log in to the JoinNow Management Portal.
- Navigate to Dynamic PKI > Certificate Authorities.
- Click Add Certificate Authority.
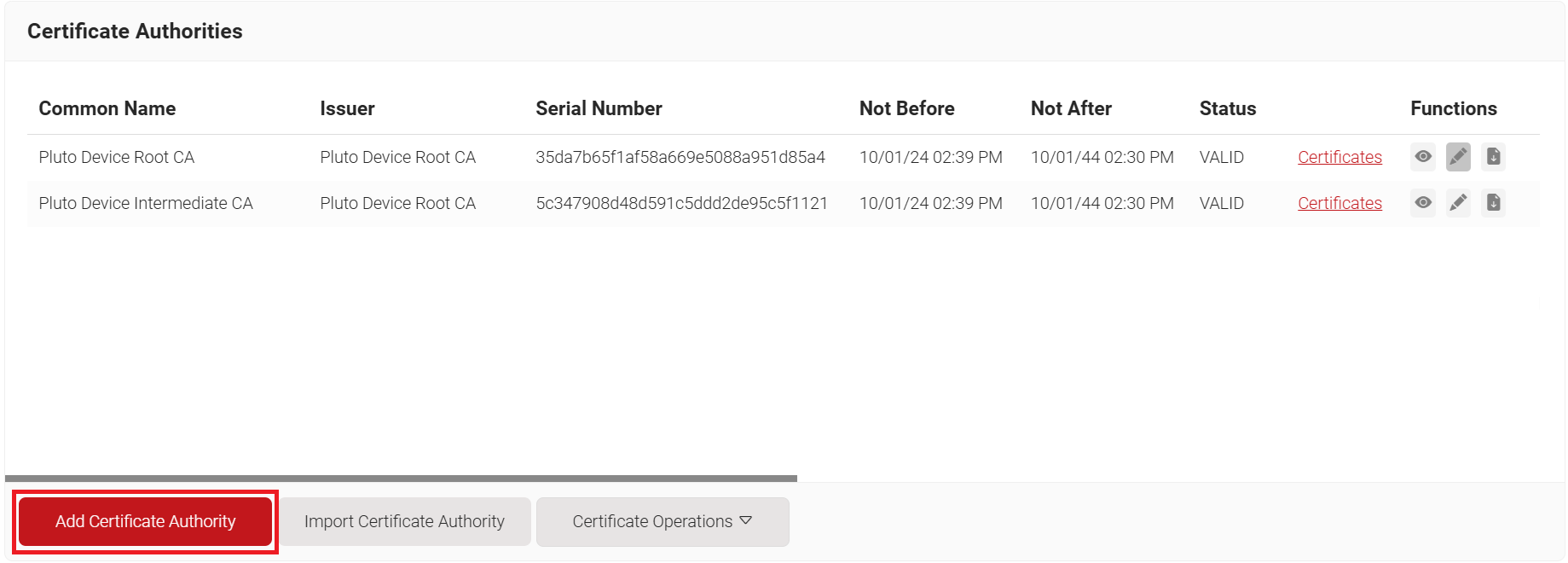
- In the Basic section, from the Generate CA For drop-down list, select the Device and User Authentication option to authenticate devices and users.
- From the Type drop-down list, select Intermediate CA.
- From the Certificate Authority drop-down list, select the default Root CA that comes with your organization.
- For the Common Name field, enter a name. Recommended name format for easy identification – “myOrgName jamf Intermediate CA”.
- From the Key Size drop-down list, select 2048 for the CA certificate key pair.
- From the Signature Algorithm drop-down list, select the signature algorithm for the certificate signing request. The option available is SHA-256.
- In the Validity Period field, enter the validity period for the Intermediate CA in terms of the number of years.
- In the Notifications section:
- From the Expiry Notification Frequency (in days) drop-down list, select the frequency interval for which a certificate expiration notification should be sent to users.
- Select the Notify user on the successful Enrollment checkbox to notify users after a successful enrollment.
- If the RFC has a valid email address, the user will receive the certificate-issued or expired notification; otherwise, they will not receive the notification.
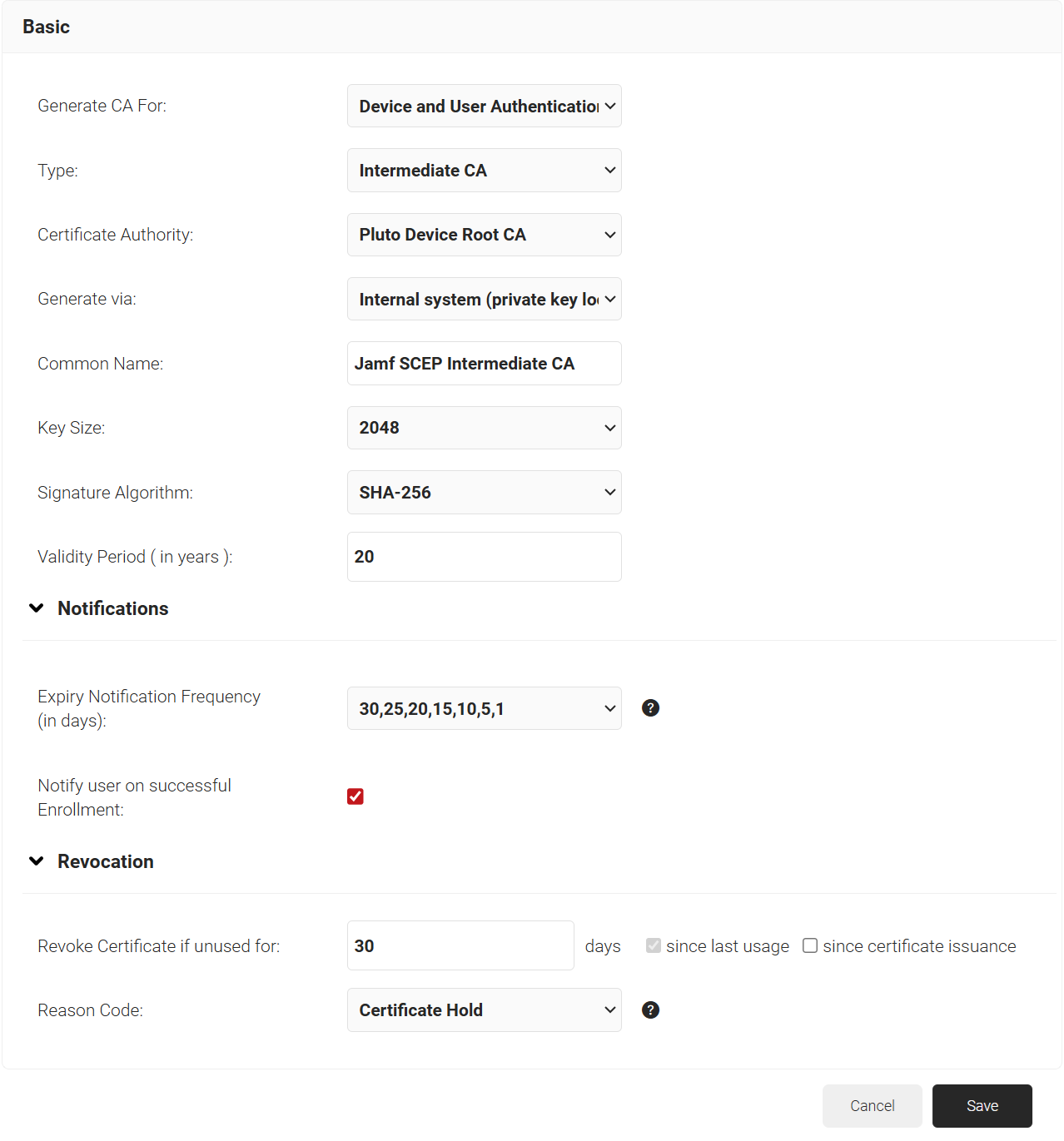
- In the Revocation section:
- In the Revoke Certificate if unused for field, select the number of days after which an unused certificate can be revoked.
- Since last usage – Select this checkbox to revoke the certificate after a specified number of days if it remains unused.
- Since certificate issuance – Select this checkbox to revoke the certificate after a specified number of days after it is issued.
- From the Reason Code drop-down list, select any one of the following reasons for which the certificate is revoked.
- Certificate Hold
- AA Compromise
- Privilege Withdrawn
- Unspecified
- In the Revoke Certificate if unused for field, select the number of days after which an unused certificate can be revoked.
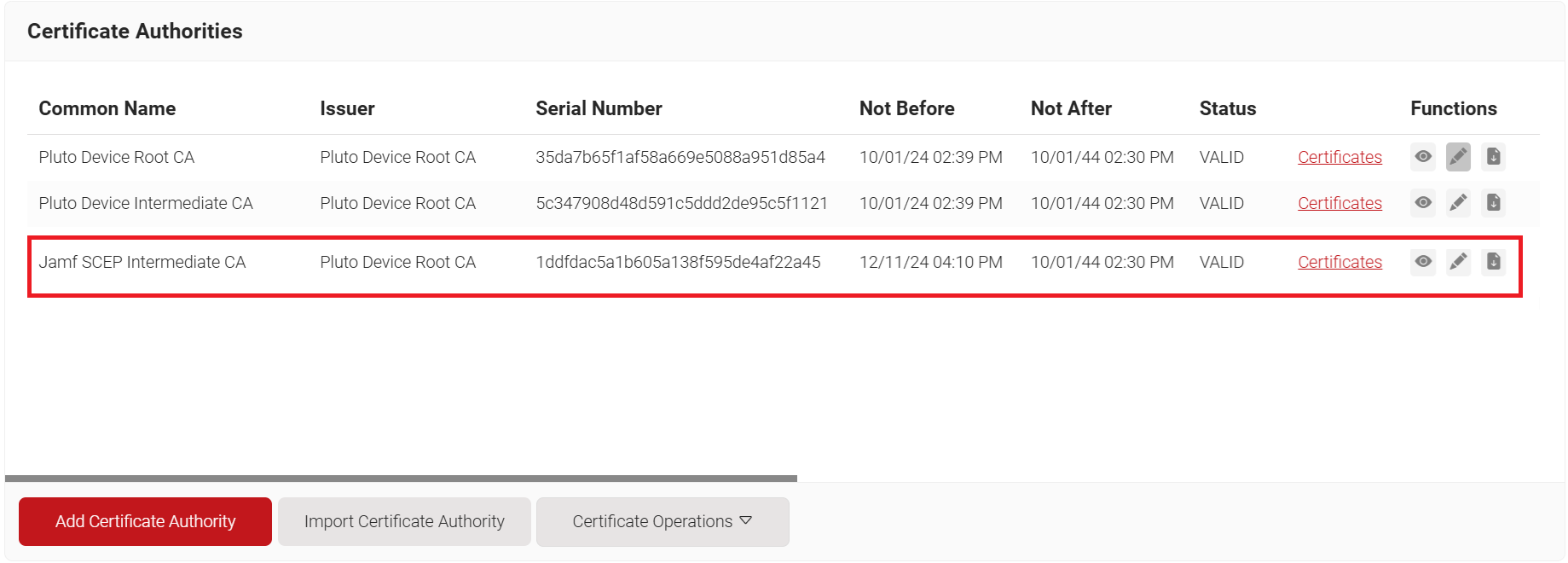
- Click Save. This generates the new intermediate CA.
Creating a Certificate Template for Jamf
A certificate template is a blueprint for attributes that must be encoded on a certificate and the certificate’s intended use case.
To create a Jamf Certificate Template:
- Navigate to Dynamic PKI > Certificate Authorities.
- Scroll to the Certificate Templates section and click Add Certificate Template.
- In the Basic section, enter the name of the certificate template in the Name field.
- In the Subject field, enter CN=${/device/clientId:/csr/subject/commonname}. This fetches the common name configured in the Jamf.
- In the Display Description field, enter a suitable description for the certificate template.
- In the Validity Period field, type the validity period of the certificate (based on the requirement).
- In the Override Validity Period field, choose a specific date to bypass the validity period.
- From the Signature Algorithm drop-down list, select SHA-256 as the signature algorithm for the certificate signing request.
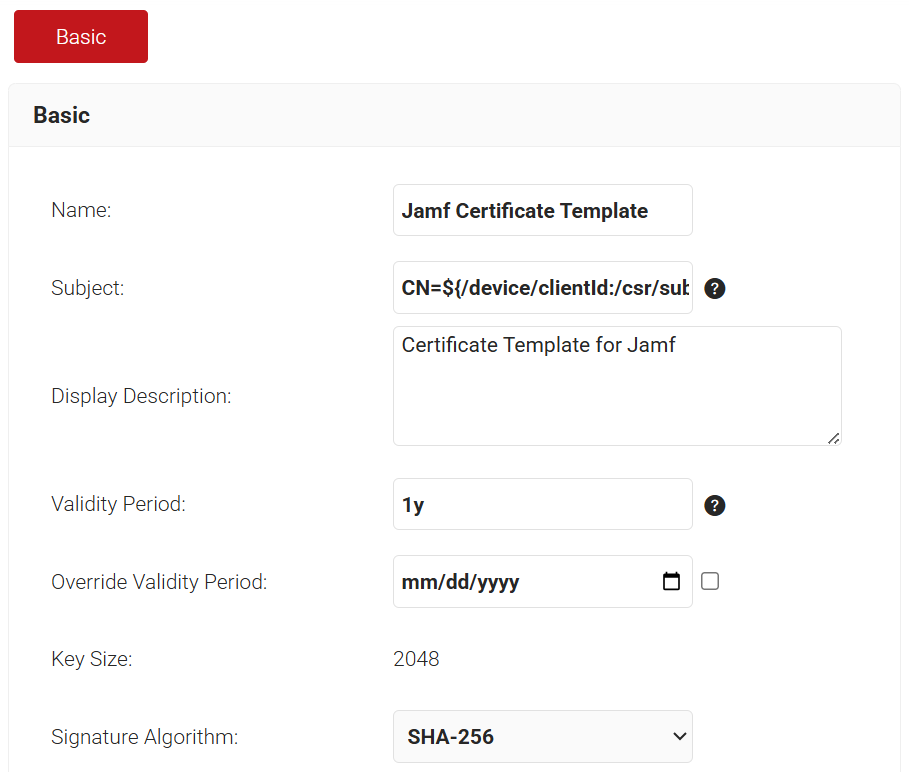
- In the SAN section:
- In the Other Name field, enter ${/device/userDescription:/csr/san/othername}
- In the RFC822 field, enter ${/device/userDescription:/csr/san/rfc822name}
- In the DNS field, enter ${/device/buildModel:/csr/san/dnsname}
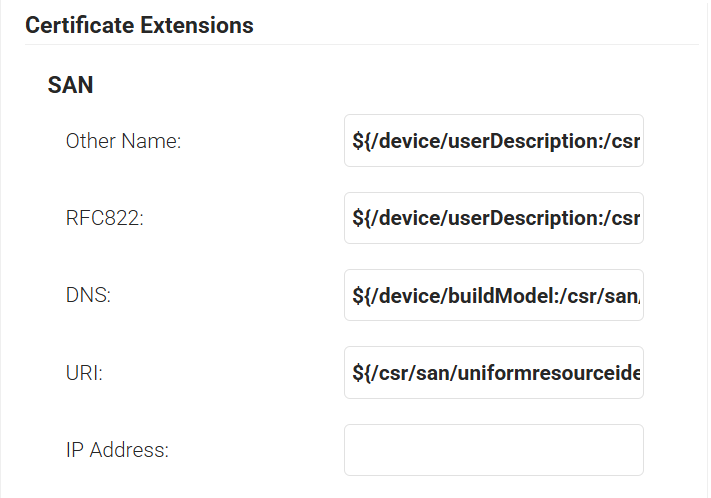
- In the Extended Key Usage section, from the Use Certificate For list, select Client Authentication.
- Click Save.
Creating a Signing Certificate for Jamf
Jamf requires a signing certificate to sign custom configuration profiles and packages. These profiles are then automatically trusted when installed on managed devices.
The signing certificate can be created from the JoinNow Management Portal using the Create Certificate option.
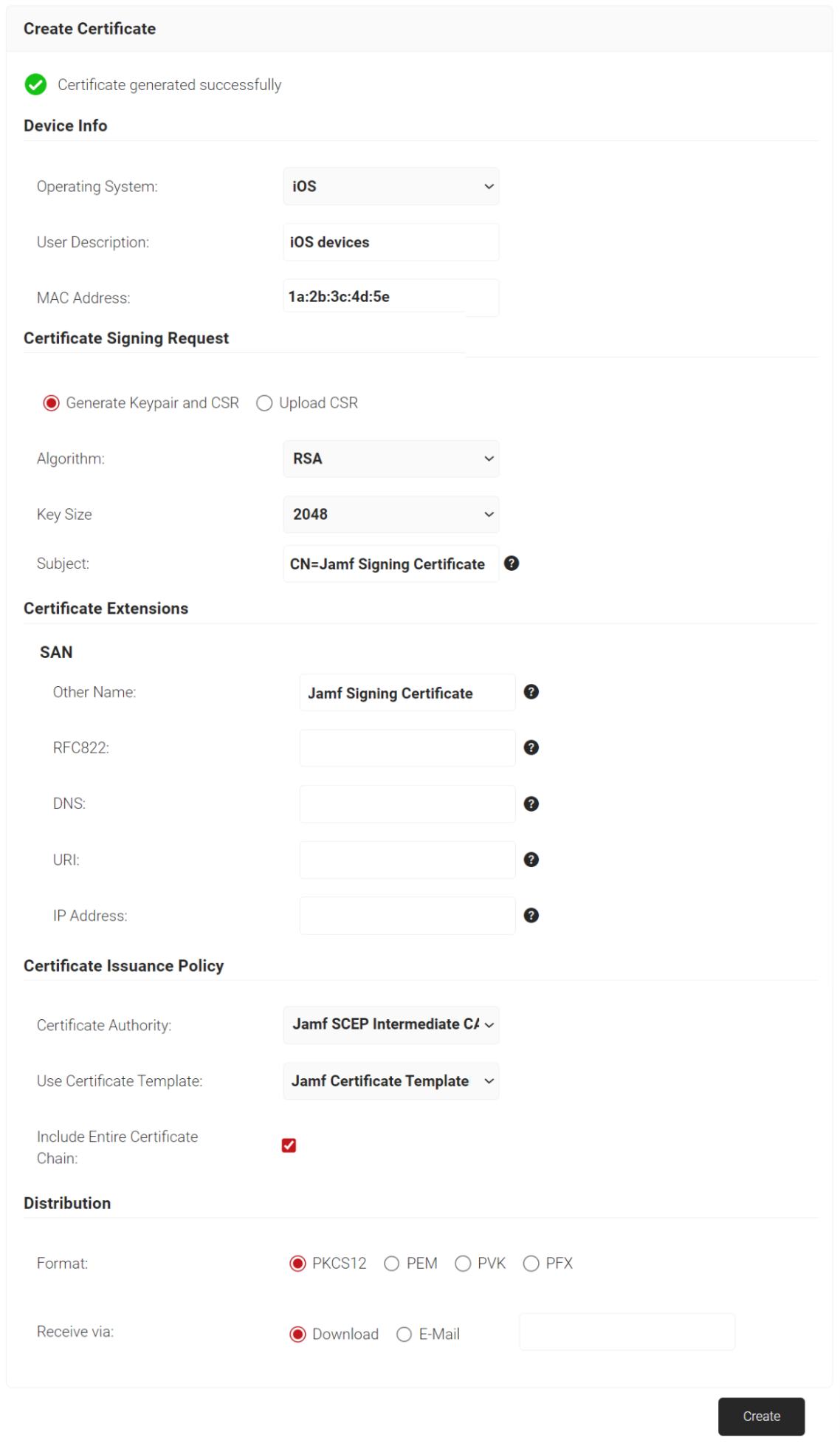
To create a Jamf signing certificate:
- Navigate to Dynamic PKI > Create Certificate.
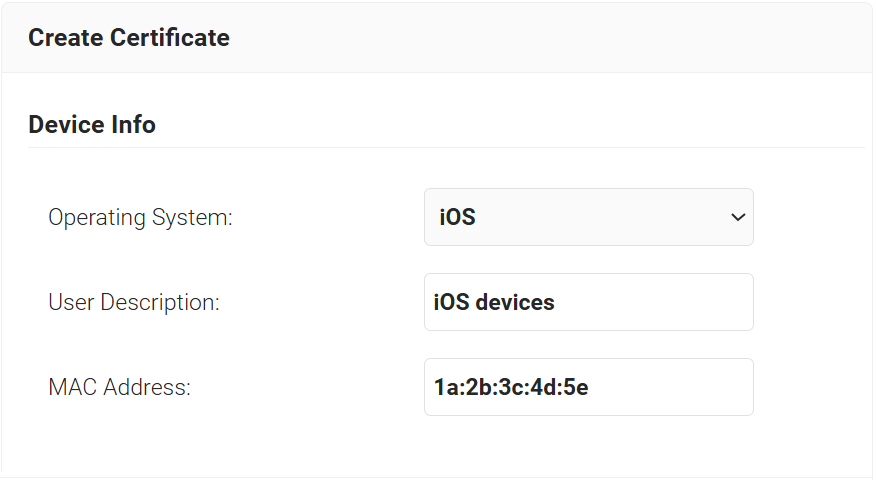
- In the Device Info section, from the Operating System drop-down list, select an operating system.
- For User Description, enter a suitable description.
- For MAC Address, enter a unique MAC address.
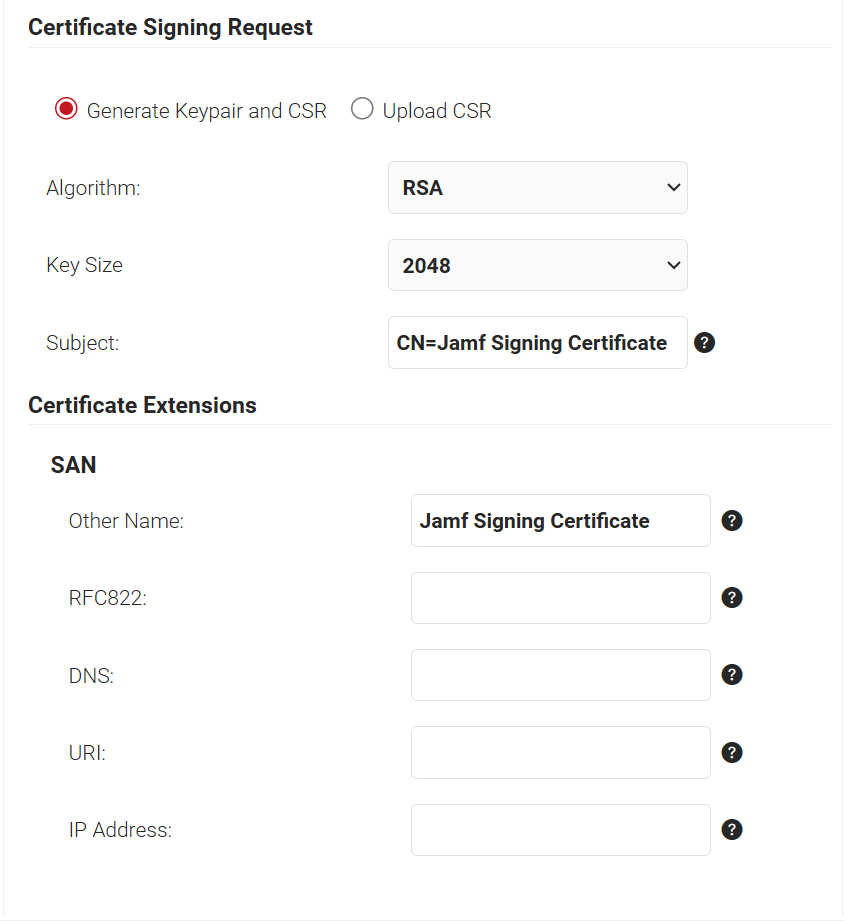
- In the Certificate Signing Request section, select the Generate Keypair and CSR option to generate a keypair and CSR file, and create client certificates.
- From the Algorithm drop-down list, select RSA.
- From the Key Size drop-down list, select 2048.
- In the Subject field, enter the common name (the recommended name format for the certificate is “Jamf Signing Certificate”. This helps in easy identification of the CA).
- In the Other Name field, enter the same value as in the Subject field. Ignore the other fields.
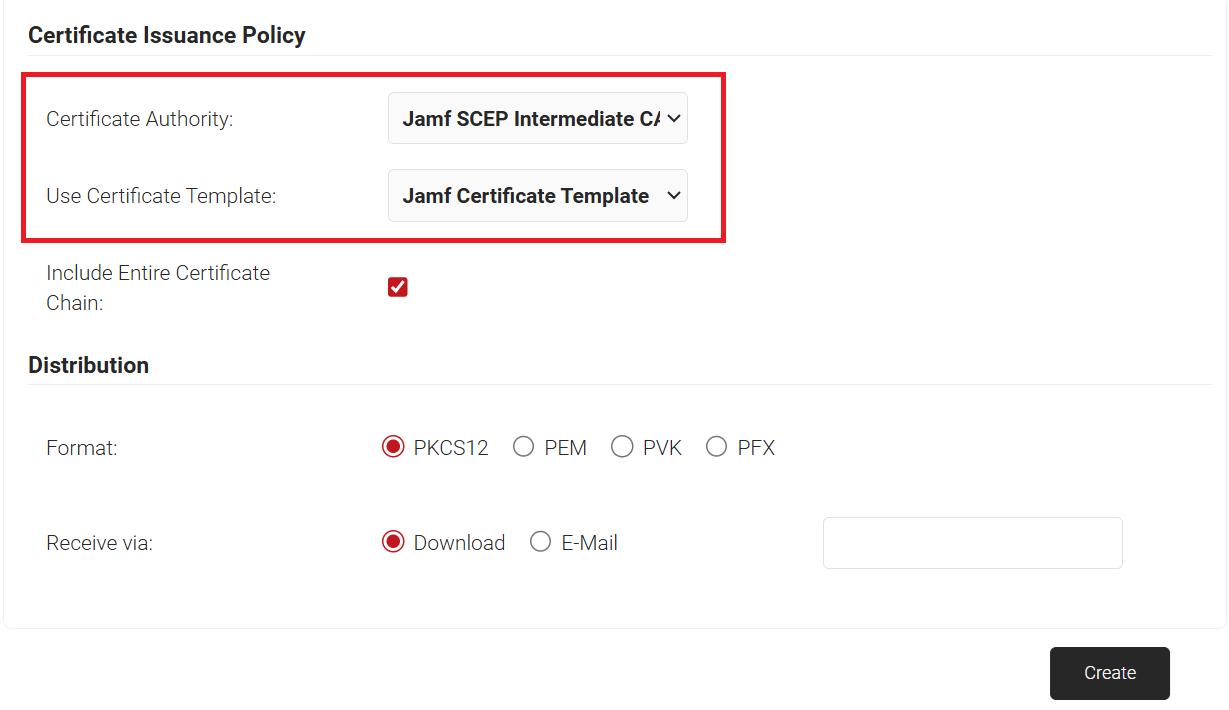
- In the Certificate Issuance Policy section, from the Certificate Authority drop-down list, select the intermediate CA created earlier for issuing certificates to clients using SCEP (refer to the Creating an Intermediate CA for SCEP Gateway Integration section).
- From the Use Certificate Template drop-down list, select the certificate template created in Creating a Certificate Template for Jamf.
- Select the Include Entire Certificate Chain checkbox. This is mandatory.
- In the Distribution section, for the Format field, select PKCS12.
- In the Receive via field, select Download.
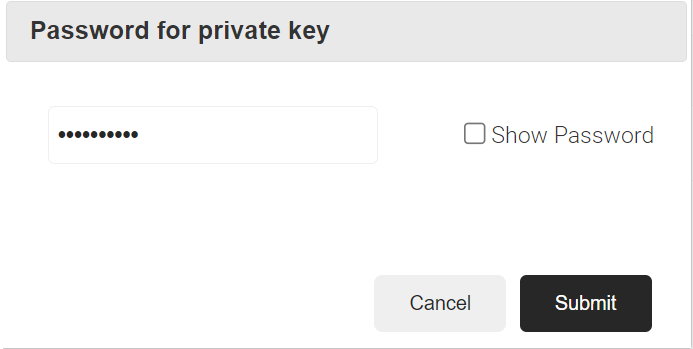
- Click the Create button, and a Password for private key pop-up window opens. Enter the password for the certificate file and click Submit.
Creating a Device Management Platform
The SCEP URL serves as an endpoint using which managed devices can connect with the SCEP server and enroll for certificates. The secret is also passed to Jamf’s external CA to authenticate these certificate requests.
A SCEP URL and secret can be generated by creating a Device Management Platform in the JoinNow Management Portal.
Additionally, the tokens created for SCEP Enrollment can be used in Policy Management to assign a user/device role based on the token in the incoming request.
To create a Device Management Platform, perform the following steps:
- Navigate to Integrations Hub > Device Management Platforms.
- Click Add.
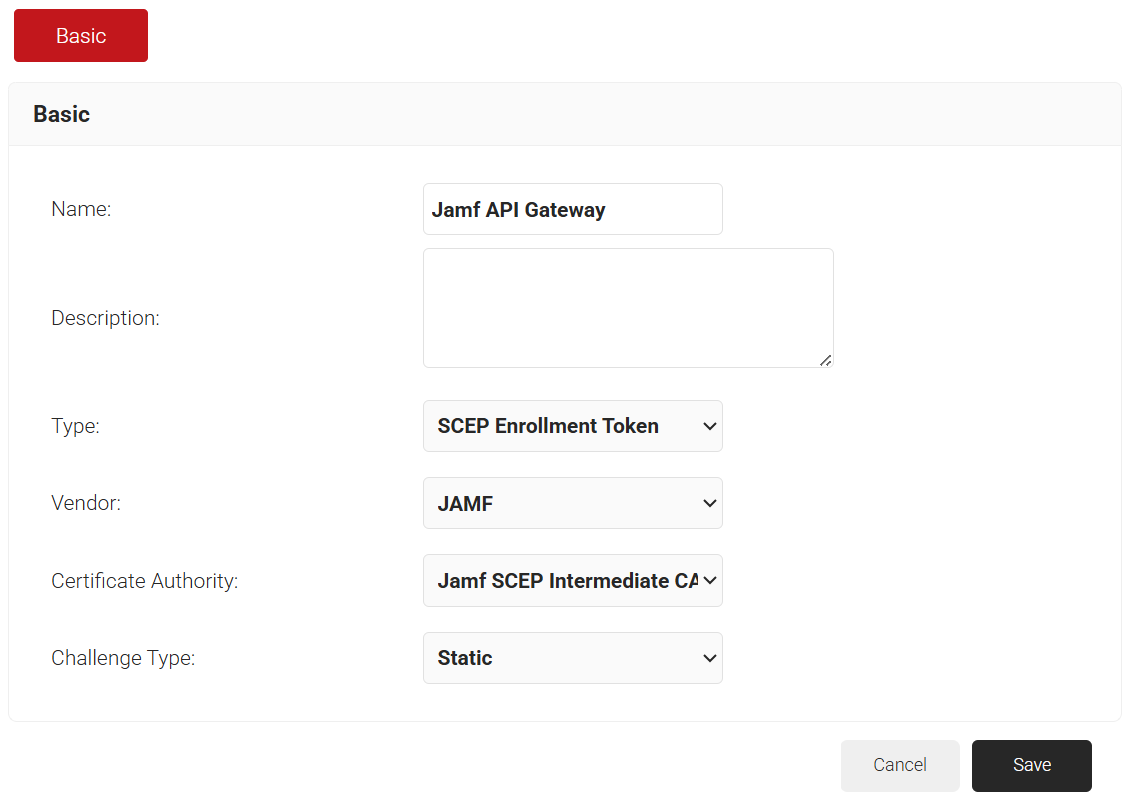
- In the Basic section, enter the name of the device management platform in the Name field.
- In the Description field, enter the description for the device management platform.
- From the Type drop-down list, select SCEP Enrollment Token.
- From the Vendor drop-down list, select JAMF.
- From the Certificate Authority drop-down list, select the Intermediate CA created in the Creating an Intermediate CA for SCEP Gateway Integration section. If you do not select a CA, by default, the organization CA is chosen.
- From the Challenge Type drop-down list, select the Static option.
- Click Save. A .csv file containing the API secret and Enrollment URL is downloaded, and the Enrollment URL is displayed on the screen.
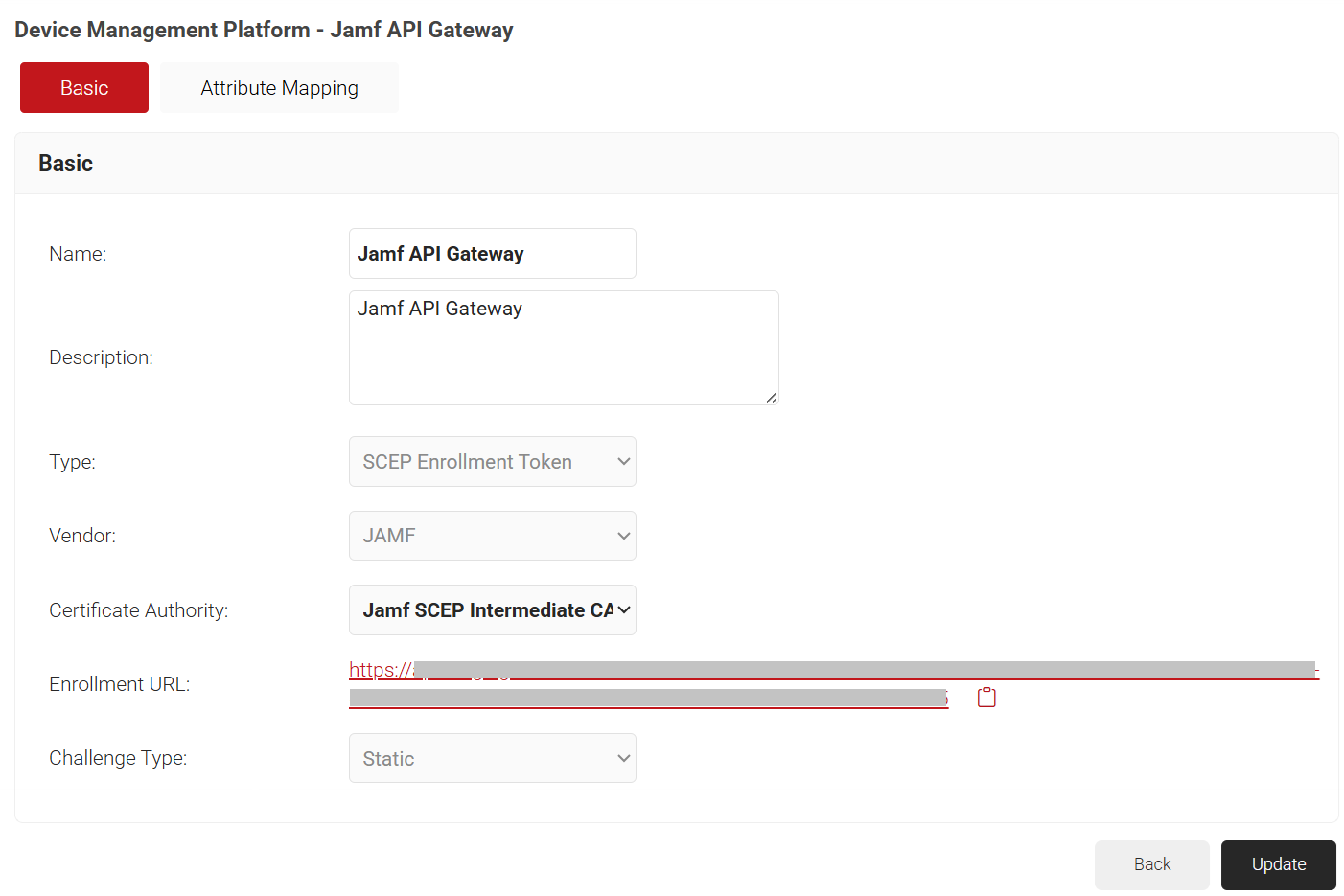
NOTE: Save this file securely. It is downloaded only once during token creation. If you lose it, you can not retrieve the secret.
- The page refreshes, and the Attribute Mapping tab is displayed.
- Click the Attribute Mapping tab to configure the required attributes for SCEP and click Update.
NOTE: You can also refer to the steps in Device Management Platform (SCEP Enrollment Token) in the JoinNow MultiOS and Connector Configuration Guide, which is available in the Management Portal.
Policy Management
This section describes the configuration process for different policies concerning certificate enrollment and network access. Through Policy Management, diverse rules can be set for each policy, which helps in selecting the correct certificate template for issuing the appropriate certificate to users. Likewise, Network Policy allows for the configuration of various rules to be applied based on user and device roles during network authentication.
When these rules align with the configured attributes during network authentication, suitable network attributes can be applied to the devices.
Creating a Policy Workflow
To configure a Policy Workflow:
- Navigate to Policy Management > Policy Workflows.
- Click Add Policy Workflow.
- In the Basic section, enter the name of the Policy Workflow in the Name field.
- In the Display Description field, enter a suitable description for the policy workflow.
- Click Save.
- The page refreshes, and the Conditions tab is displayed.
- Click the Conditions tab.
- From the Core Provider drop-down list, select the Device Management Platform you created earlier.
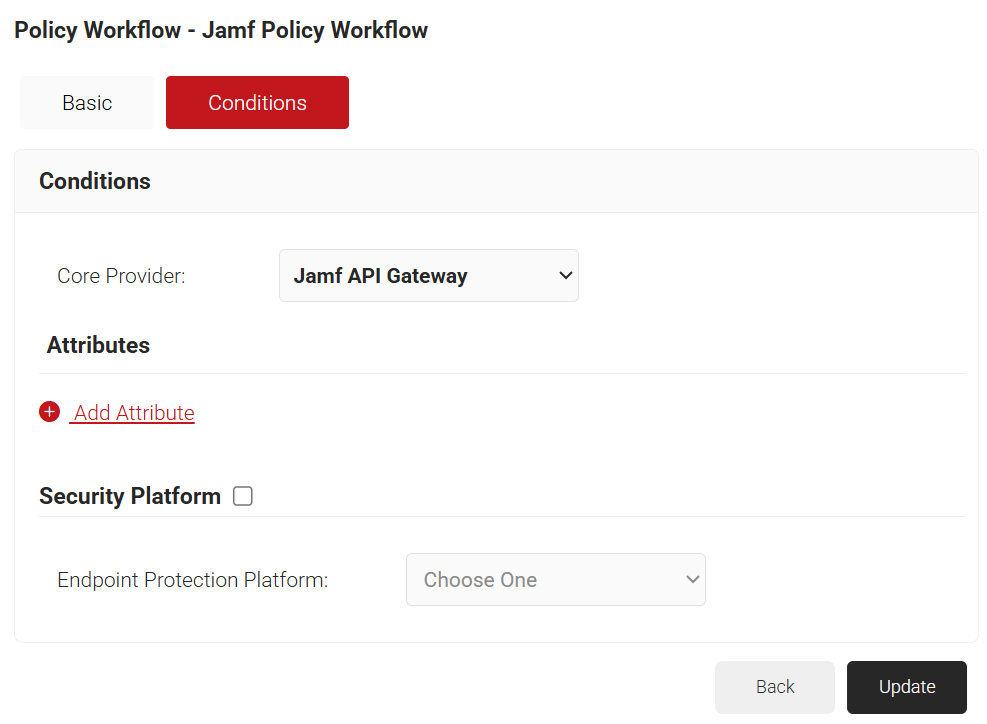
- Click Update.
Creating an Enrollment Policy
To add an Enrollment Policy, perform the following steps:
- Navigate to Policy Management > Enrollment.
- Click Add Enrollment Policy.
- In the Basic section, enter the name of the enrollment policy in the Name field.
- In the Display Description field, enter a suitable description for the enrollment policy.
- Click Save.
- The page refreshes, and the Conditions and Settings tabs are displayed.
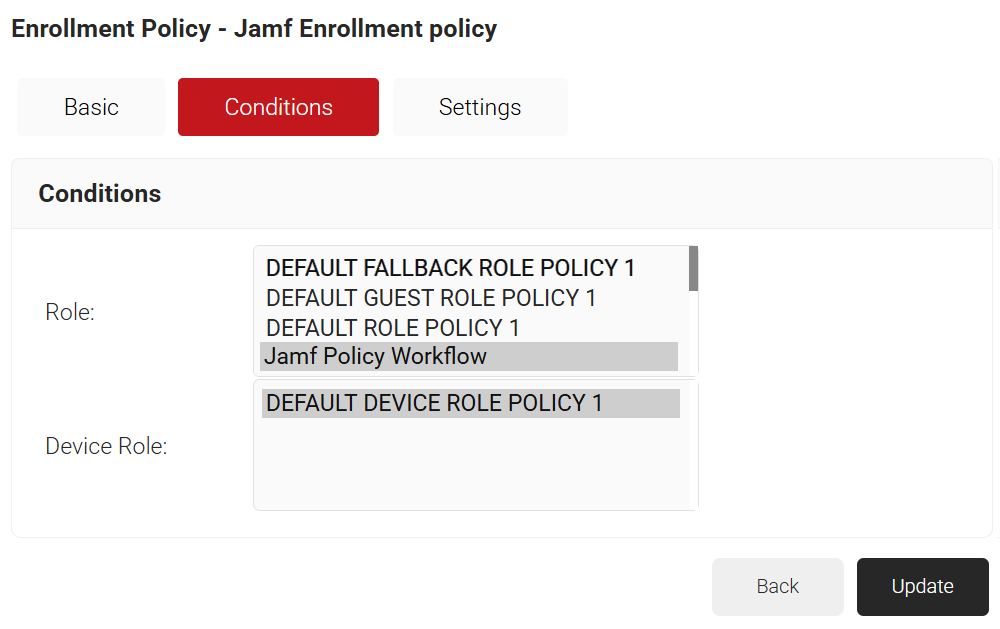
- Click the Conditions tab.
- In the Conditions section, from the Role list, select the role policy you created in the Creating a Policy Workflow section.
- From the Device Role list, select DEFAULT DEVICE ROLE POLICY.
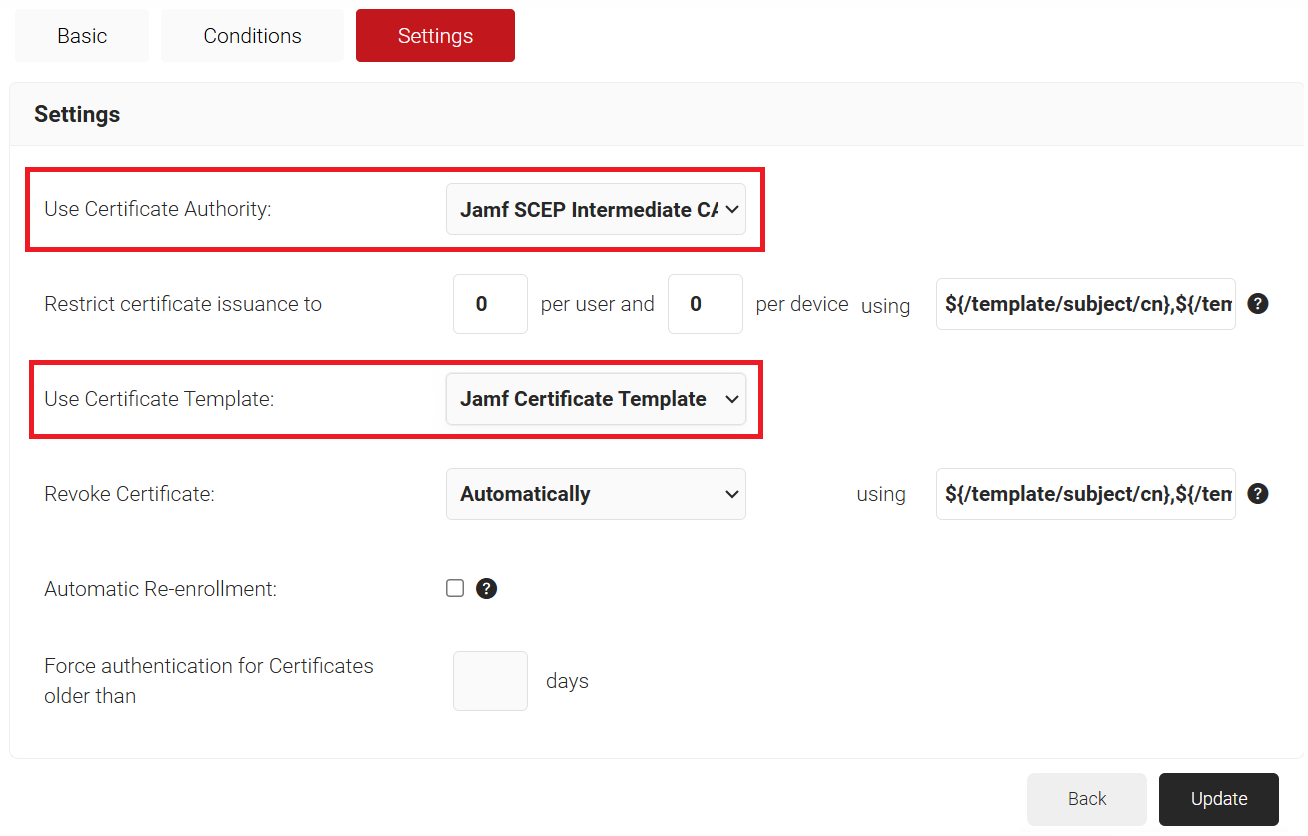
- Select the Settings tab.
- In the Settings section, from the Use Certificate Authority drop-down list, select the intermediate CA you created earlier (see the Creating an Intermediate CA for SCEP Gateway Integration section).
- From the Use Certificate Template drop-down list, select the template you created earlier (see the Creating a Certificate Template for Jamf section).
- In the other settings, retain the default values.
- Click Update.
Setting up Certificate Enrollment via SCEP on Jamf
In order to configure a Jamf Profile for the Simple Certificate Enrollment Protocol (SCEP), we need to configure our CA in our Global Management settings.
- Log in to the Jamf Pro console.
- Navigate to Settings > Global.
- Click PKI certificates.
- Select the Management Certificate Template tab, select External CA, and click Edit.
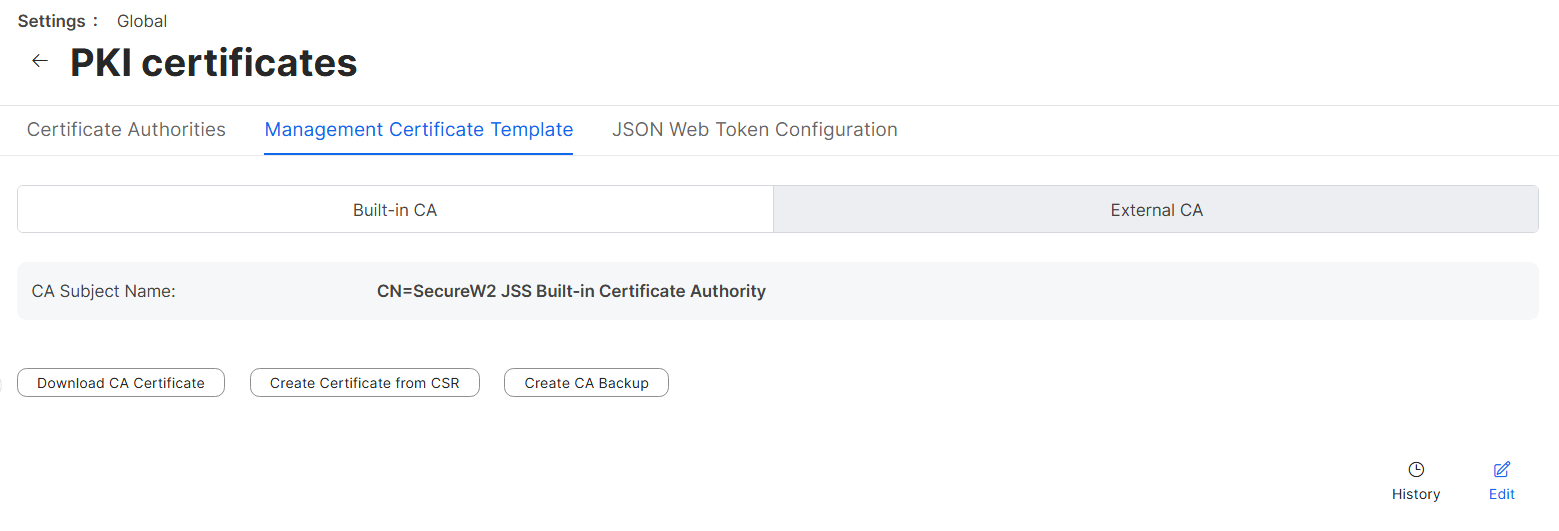
- Select the Enable Jamf Pro as SCEP Proxy for configuration profiles checkbox.
- In the URL field, enter the new SCEP URL you saved in the CSV file.
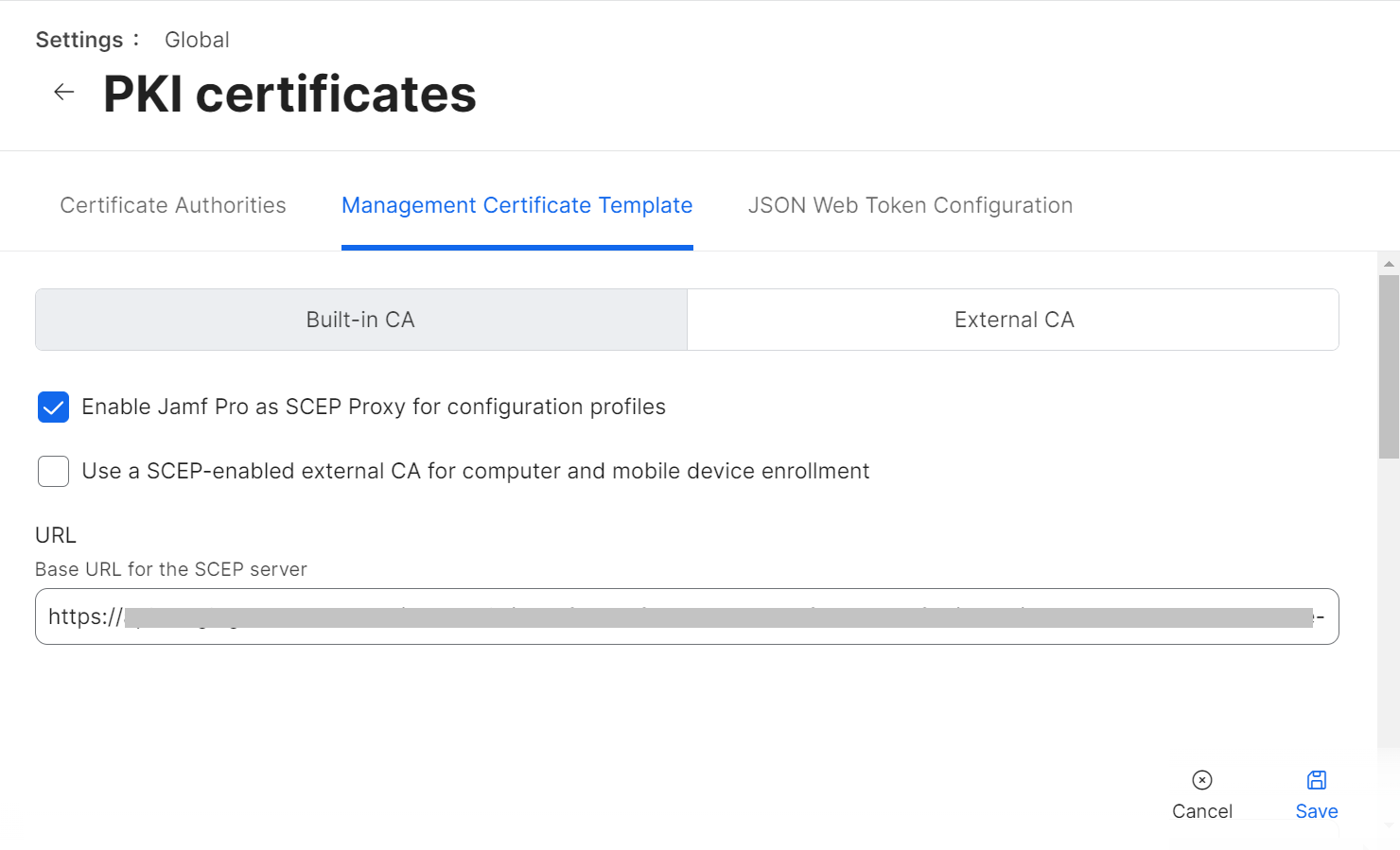
NOTE: You can also refer to the steps in Configuring API Tokens (SCEP Enrollment Token) in the JoinNow MultiOS and Connector Configuration Guide available in the Management Portal. - In the Name field, enter the name of the certificate issuing CA created in the JoinNow Management portal.
- In the Subject field, enter “CN=$EMAIL”.
- From the Subject Alternative Name Type drop-down list, select None.
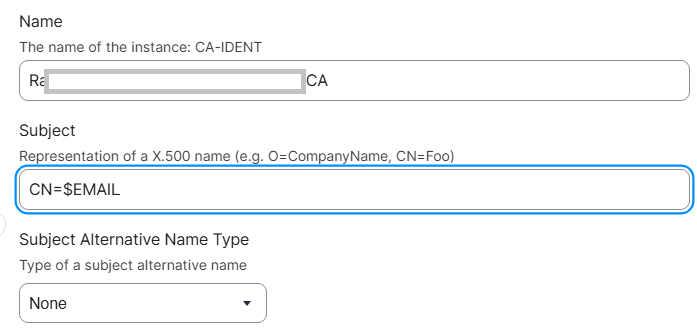
- From the Challenge Type drop-down list, select Static.
- In the Challenge and Verify Challenge fields, enter the Secret from the CSV file you downloaded in the Creating a Device Management Platform section.
- From the Key Size drop-down list, select 2048. SecureW2 does not recommend selecting 1024.
- Click Save.
- Under the Signing Certificate section, click Change Signing and CA Certificates to upload the signing certificate you created in Creating a Signing Certificate for Jamf.
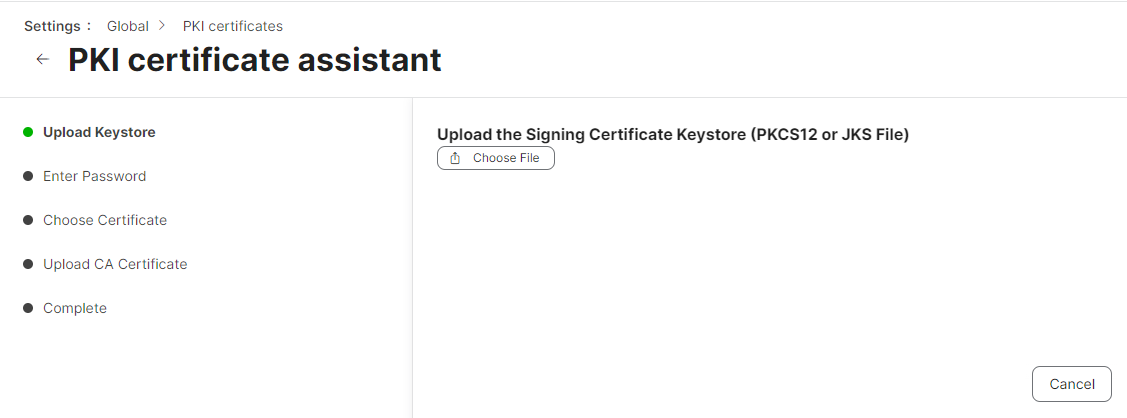
- Click Next.
- On the Enter Password step, enter the password you entered in the Password for private key prompt in the Creating a Signing Certificate for Jamf section when you created the certificate.
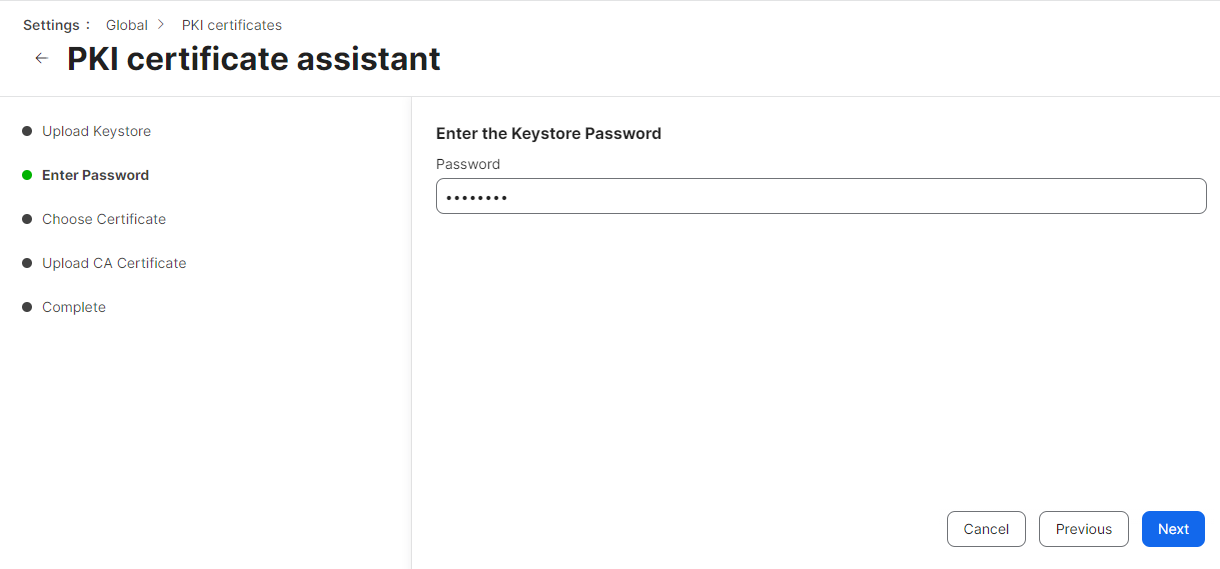
- Click Next.
- On the Choose Certificate step, verify that the correct CA certificate is selected from the Choose Certificate drop-down list and that the correct certificate chain is displayed.
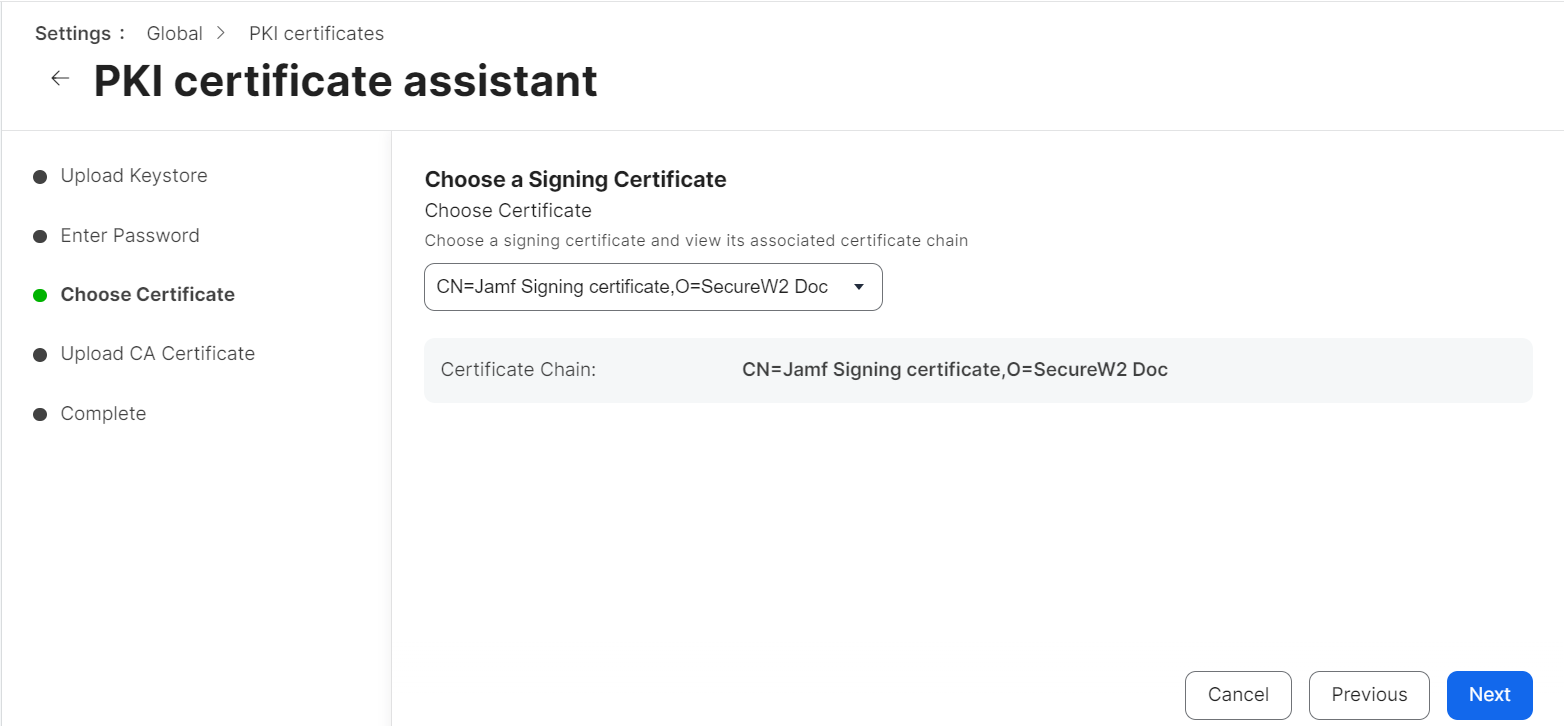
- Click Next.
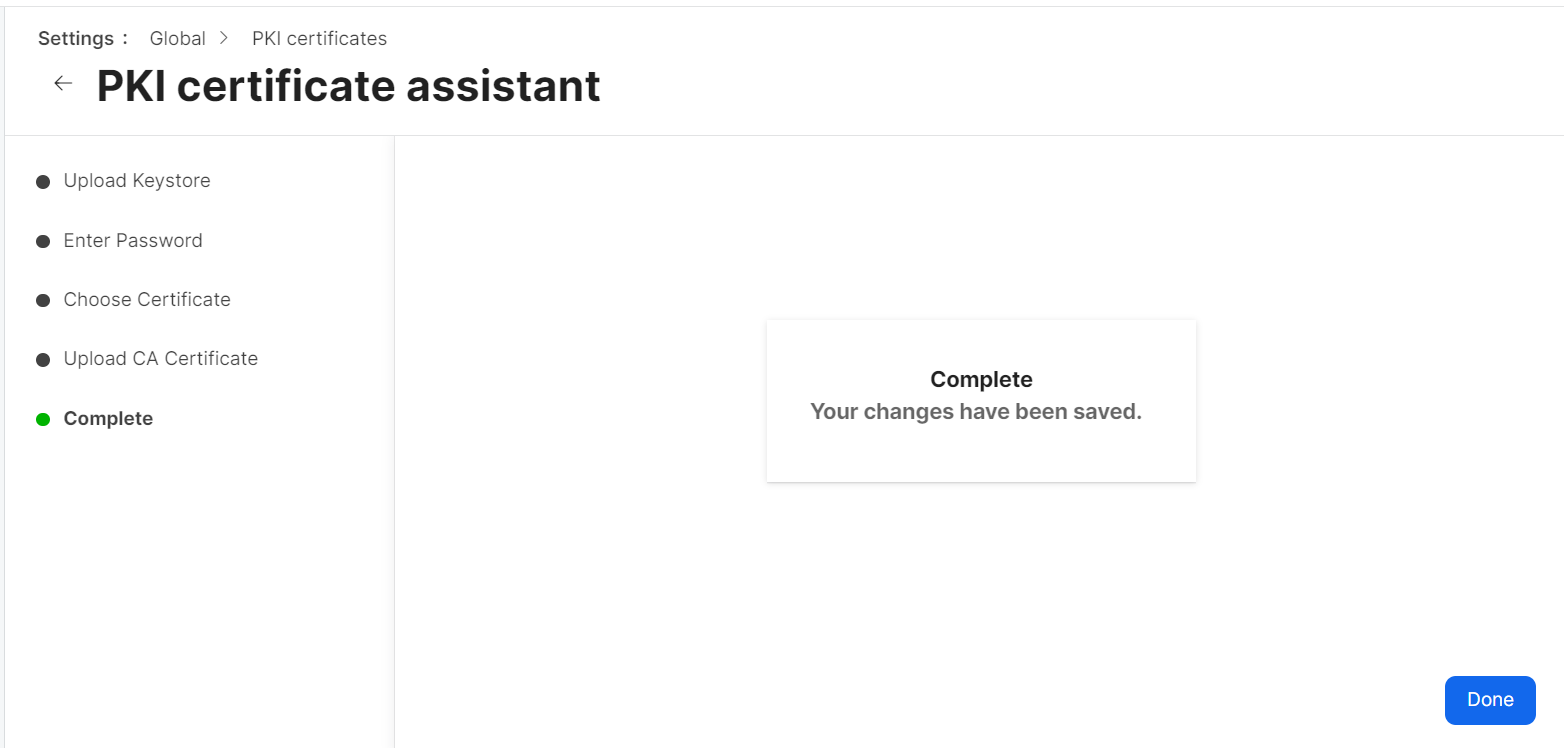
- On the Upload CA Certificate step, click Next to skip the upload. The CA certificate is already present in PKCS12.
- On the Complete step, click Done.
Configuration Profiles in Jamf Portal
Configuration profiles are XML files that are pushed to end-user devices along with certificates. These configuration files help Jamf MDM effectively manage mobile devices, computers, and users.
This section explains how to set up Jamf configuration profiles for iOS and macOS.
Setting up Jamf Configuration Profiles
This section explains how to set up Jamf configuration profiles for iOS and macOS.
For iOS
To set up a Jamf configuration profile for iOS, perform the following steps:
- From your Jamf Pro console, go to Devices > Configuration Profiles.
- Click + New.
NOTE: To update an existing configuration profile, click Edit for the profile.
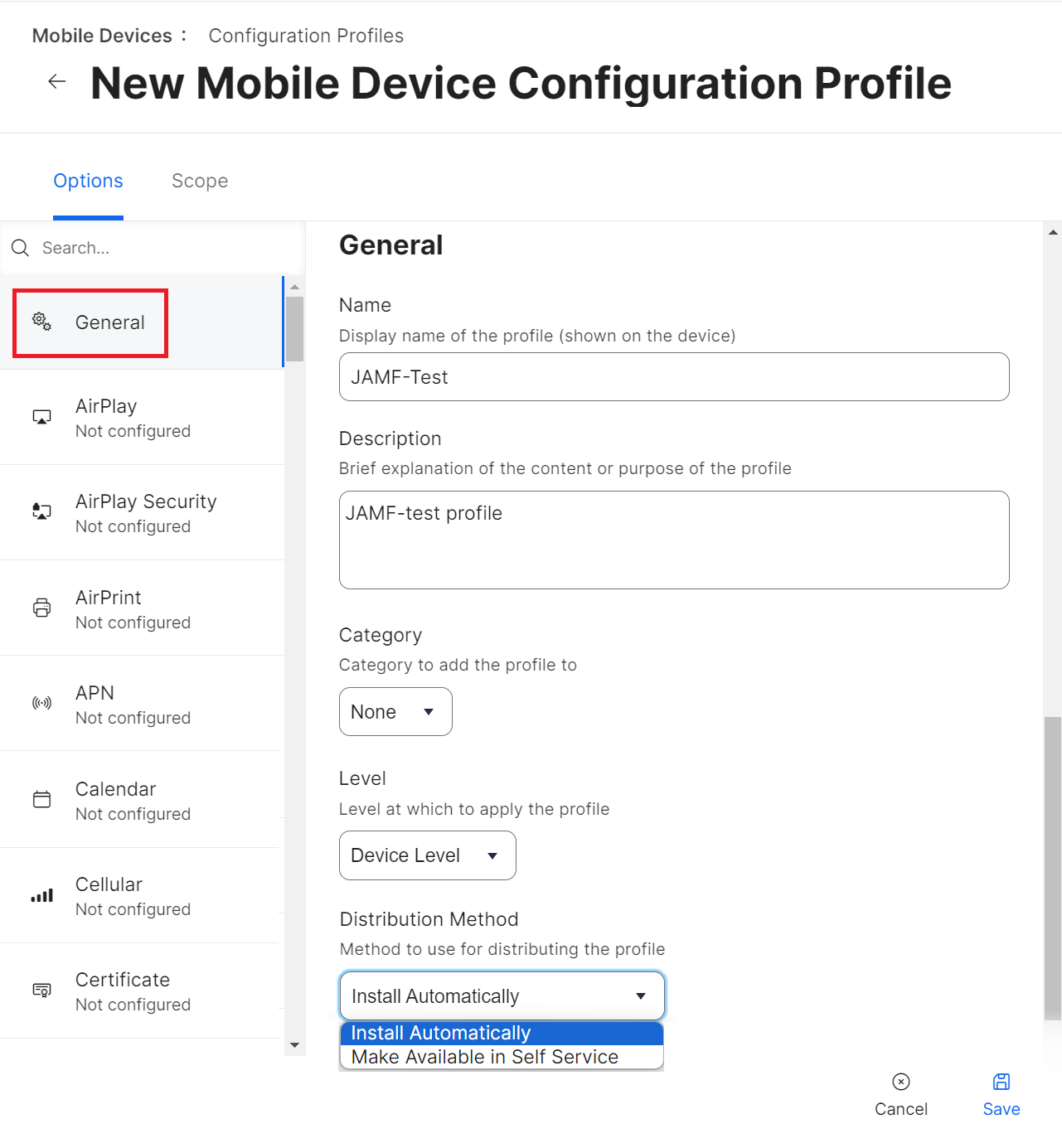
- Select Options > General.
- In the Name field, enter a name that can reflect the profile for the specific OS.
- In the Description field, enter a descriptive text explaining the purpose of this configuration.
- From the Distribution Method drop-down list, select Install Automatically or Make Available in Self-Service.
For macOS
To set up a Jamf configuration profile for macOS:
- From your Jamf Pro console, go to Computers > Configuration Profiles.
- Click New.
NOTE: To update an existing configuration profile, click Edit for the profile.
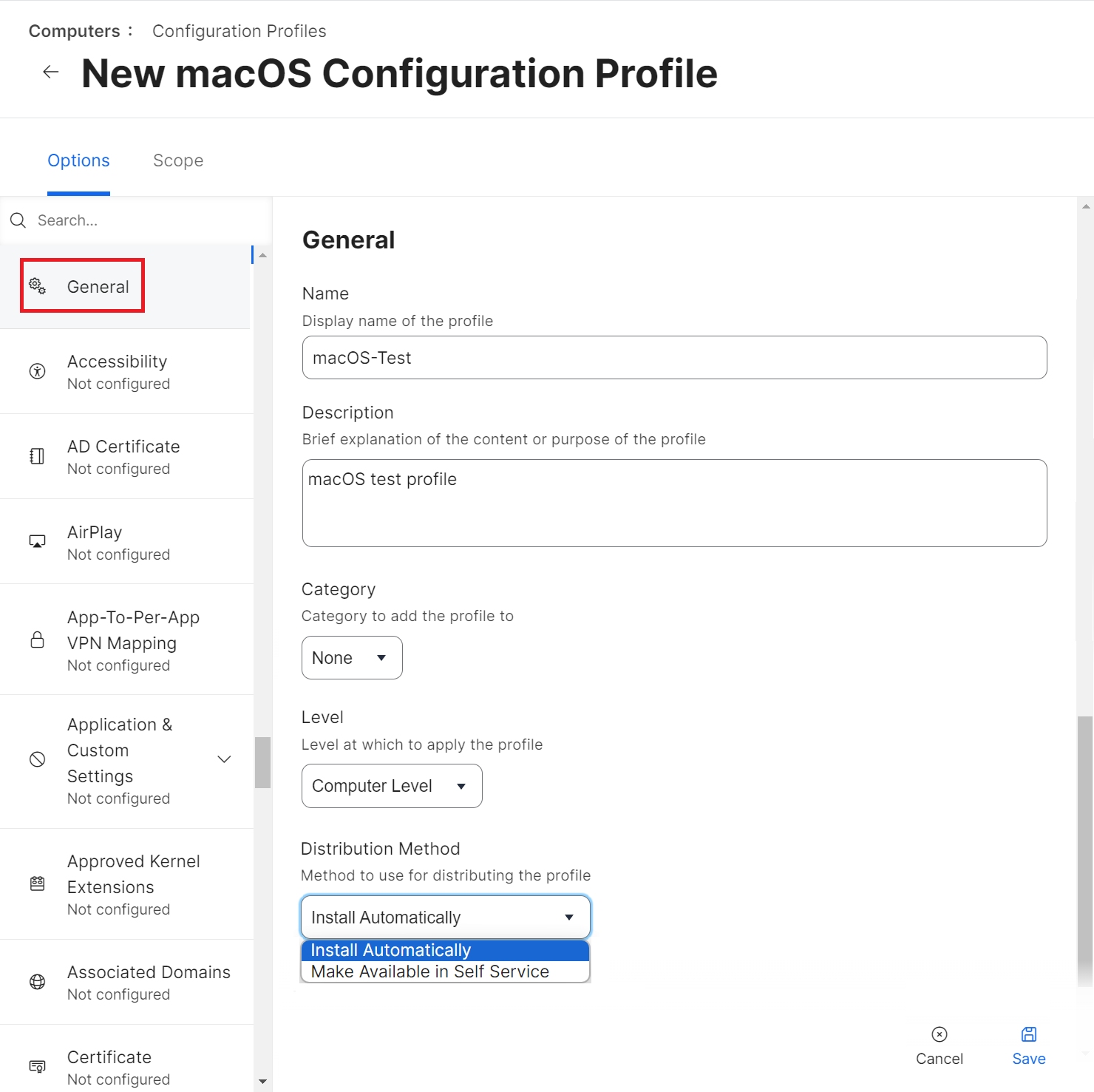
- Select Options > General.
- In the Name field, enter a name for the OS profile. E.g. MacOS_Office.
- In the Description field, enter a description for the configuration profile.
- From the Level drop-down list, select Computer Level.
- From the Distribution Method drop-down list, select Install Automatically or Make Available in Self Service.
Setting up the JAMF as SCEP Proxy for Configuration Profiles
Jamf can deploy configuration profiles that install certificates for users to access wireless networks. By setting up Jamf as the SCEP proxy in the configuration profile, Jamf communicates with the SCEP server to download and install the certificate directly on macOS or iOS devices.
To set up Jamf as a SCEP proxy, perform the following steps:
- From your Jamf Pro console, go to Options > SCEP. The steps are similar for both the iOS and macOS configuration profiles.
- Click Configure.
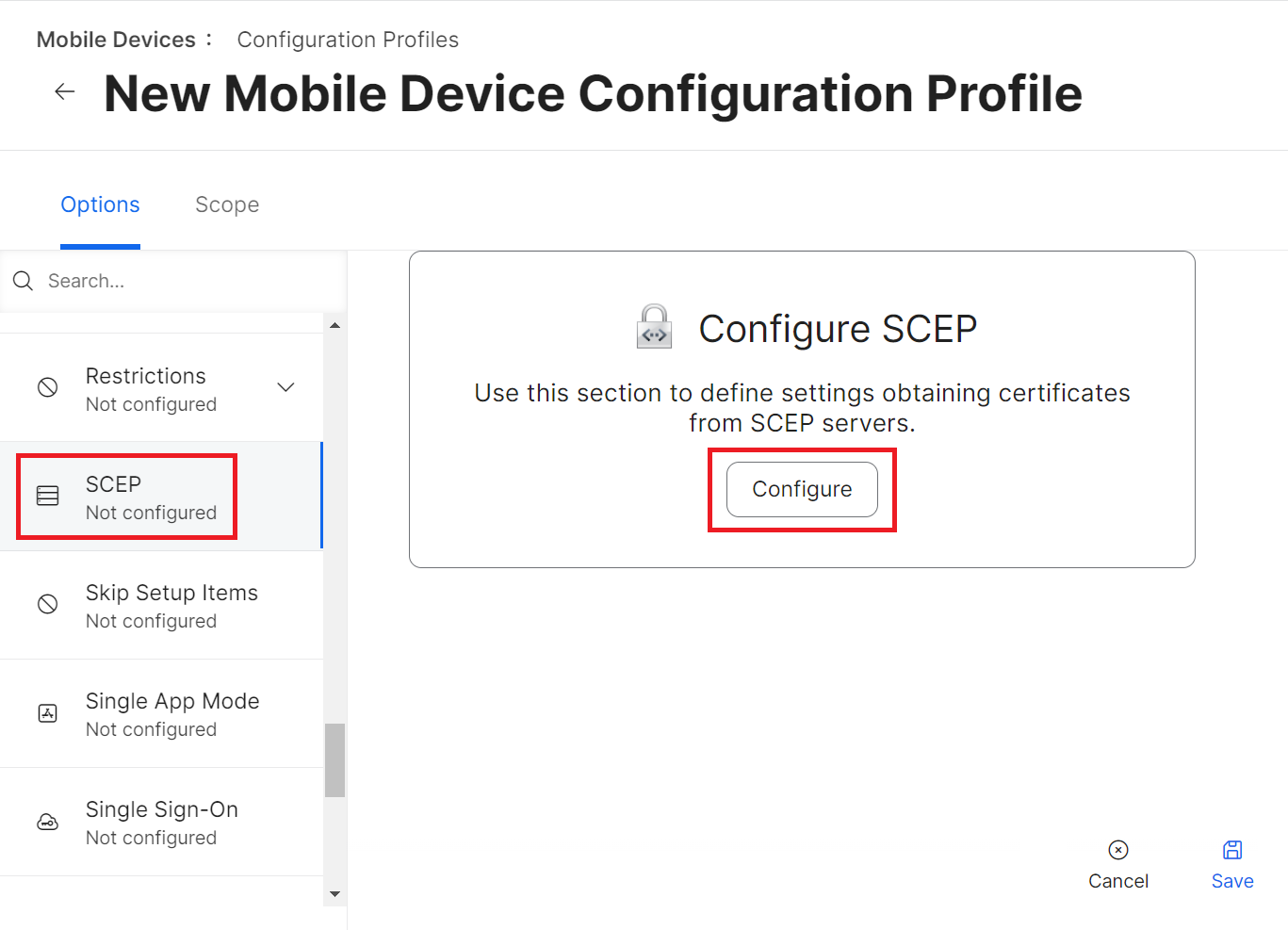
- Select the Use the External Certificate Authority settings to enable Jamf Pro as SCEP proxy for this configuration profile checkbox.
- In the Name field, enter the common name of the intermediate CA that will issue the certificate for the client. The common name can be found in the JoinNow Management Portal.
- From the Redistribute Profile drop-down list, select the desired number of days.
- In the Subject field, enter a value to help administrators identify the device. You can make this a static value if you wish.
Examples:
- CN=$DEVICENAME
- CN=$UDID
- CN=$SERIALNUMBER
NOTE: What you enter as Subject and Subject Alternative Name are referred to as payload variables and define the common name that you want to be encoded on certificates. You can find available iOS payload variables here: https://docs.jamf.com/9.9/casper-suite/administrator-guide/iOS_Configuration_Profiles.html
- From the Subject Alternative Name Type drop-down list, select the RFC 822 Name option.
- In the Subject Alternative Name Value field, use the appropriate variables as required. The recommended attributes are:
- $UDID
- $SERIALNUMBER
- $DEVICENAME
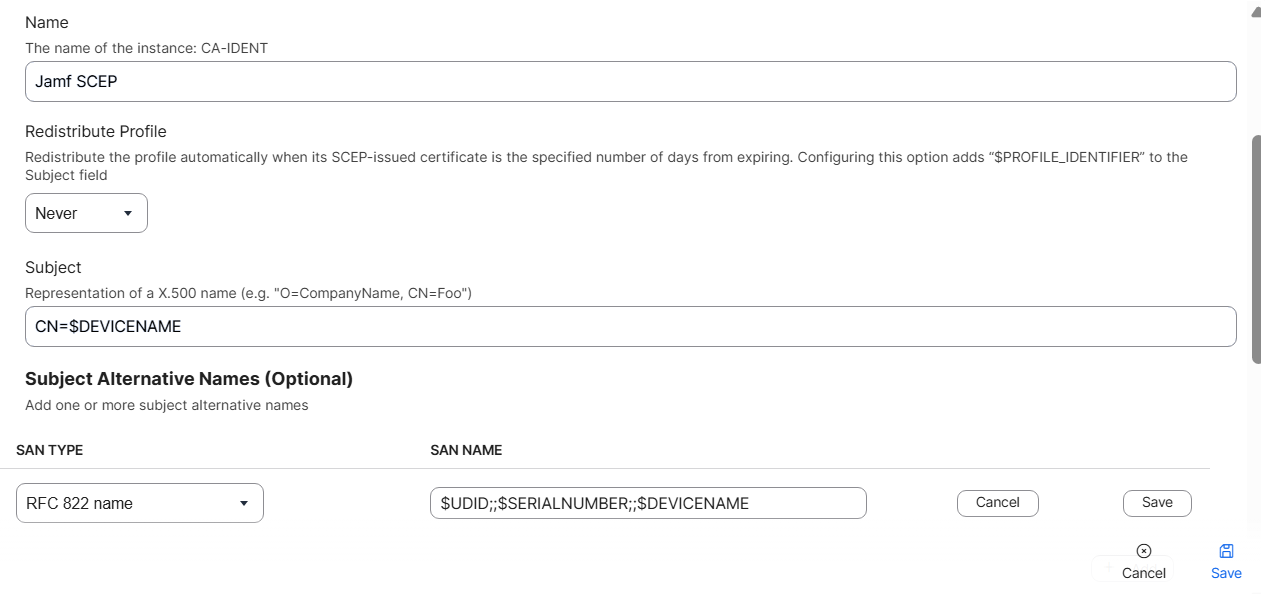
- Click Save.
- Navigate to the Scope section and update the scope for the devices to which the configuration profile will be pushed.
NOTE: If you want to change Jamf as an SCEP proxy in Settings > Global > PKI Certificates > Management Certificate Template > External CA, first disable the Use the External Certificate Authority settings to enable Jamf Pro as an SCEP proxy for this configuration profile checkbox. If you proceed without disabling this, it will affect the corresponding profile using Jamf as an SCEP proxy.
This section explains how to set up Jamf as SCEP proxy for the iOS and macOS configuration profiles.
Setting up the Certificate Payload for RADIUS Connections
This section explains how to set up the certificate payload to validate your RADIUS server. If your RADIUS server certificate also has one or more intermediate CA certificates as part of the certificate chain, you can add those certificates (Root and Intermediate) to this payload.
To set up a certificate payload, perform the following steps:
- From your Jamf Pro console, go to Devices > Configuration Profiles. Steps 2 to 10 are similar for both the iOS and macOS configuration profiles.
- Click Edit for the configuration profile you want to configure.
- Select Options > Certificate.
- Click Configure.
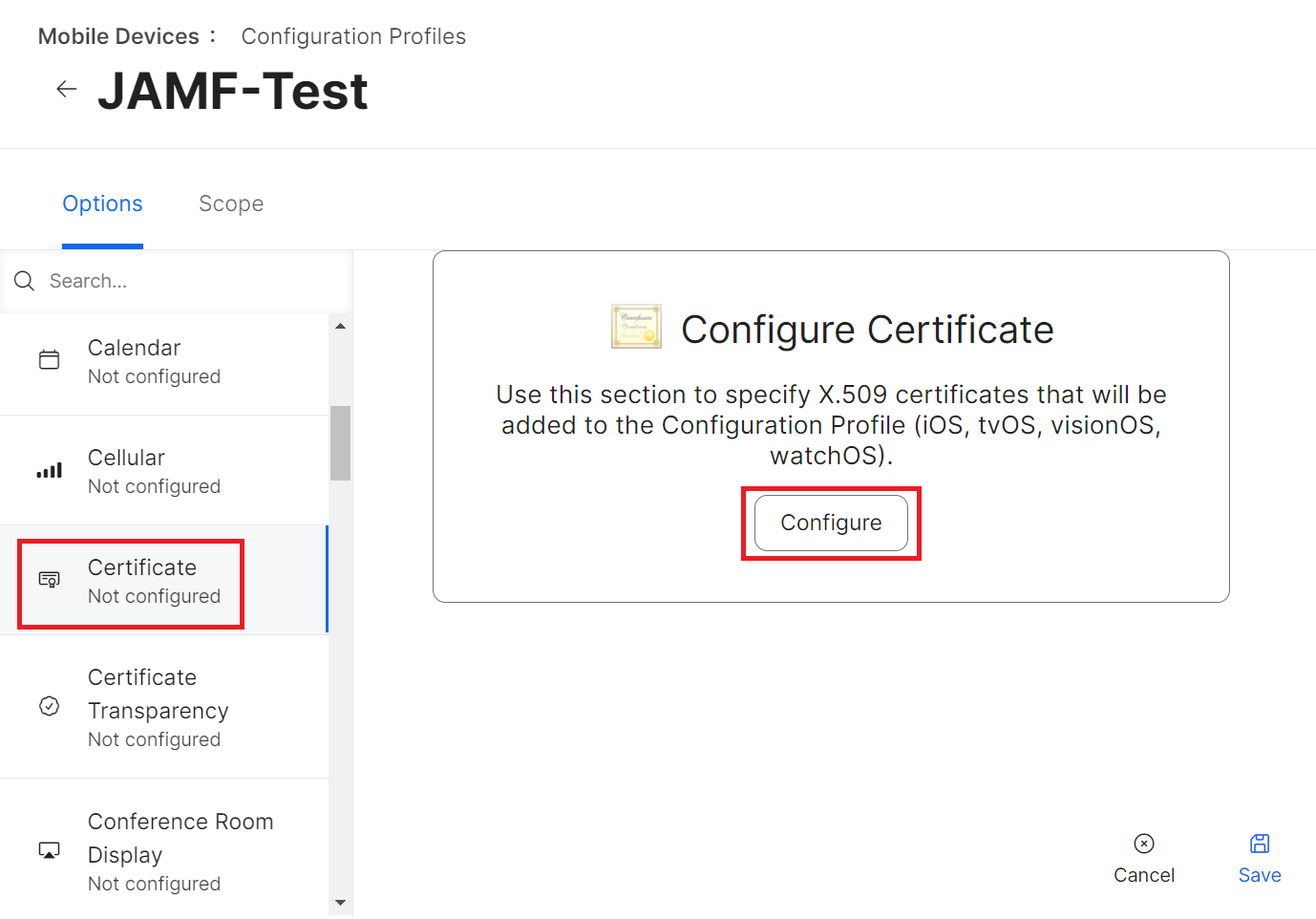
- In the Certificate Name field, enter the name of the added certificate. This will be the Common Name (Issued To).
- From the Select Certificate Option drop-down list, select Upload.
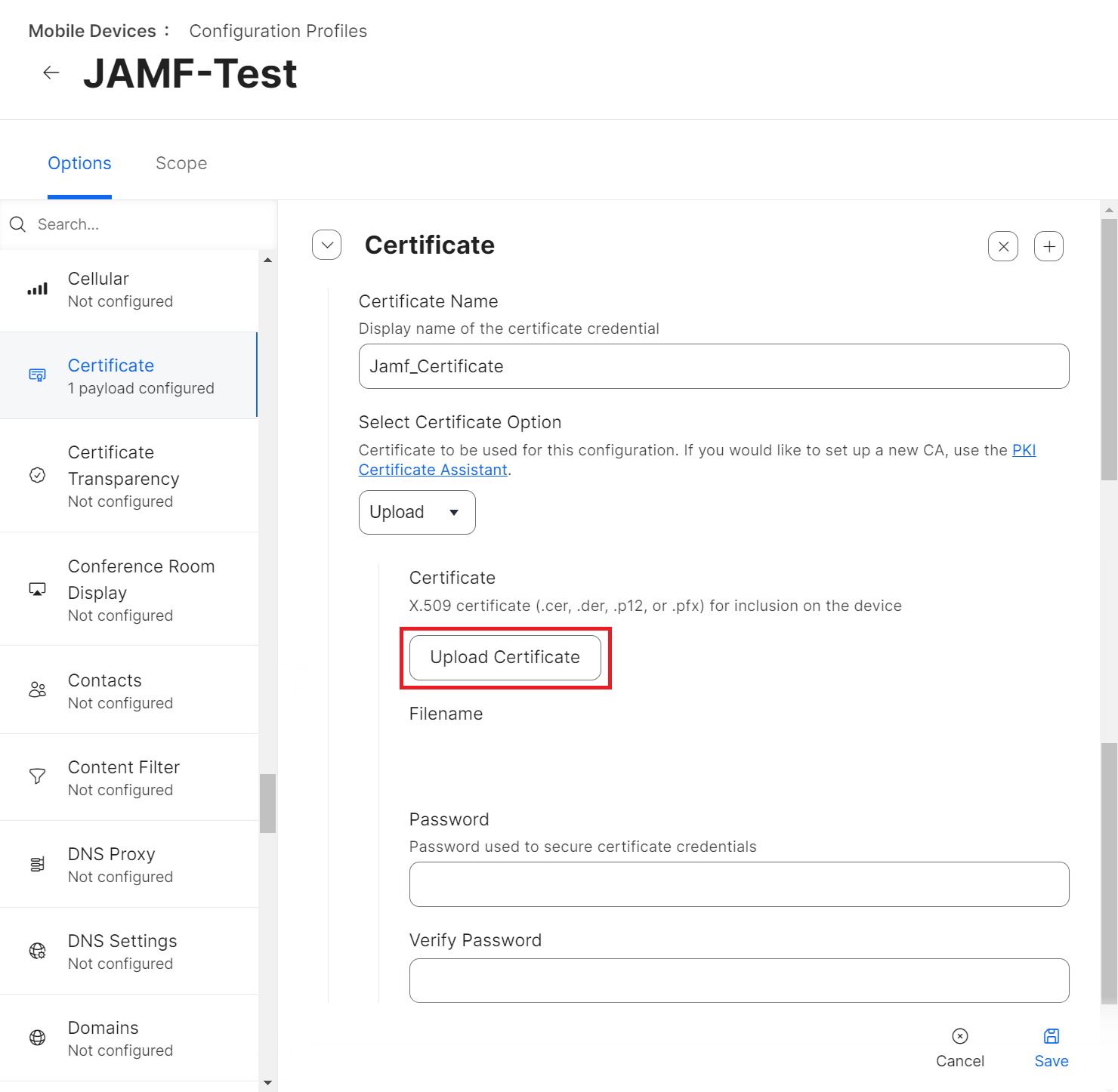
- Click Upload Certificate.
- On the Certificate pop-up window, click Choose File and upload the issuing Root CA from the JoinNow Management portal under PKI > Certificate Authorities.
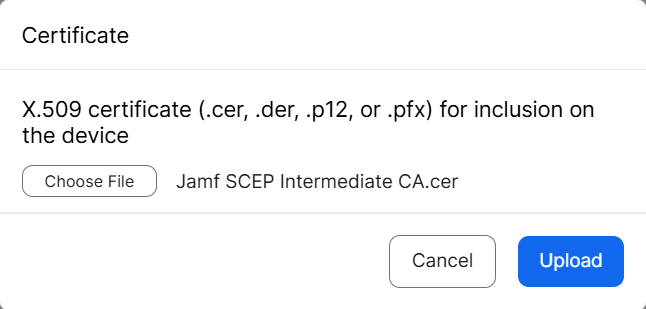
- Click Upload.
- After uploading the certificate, click Save.
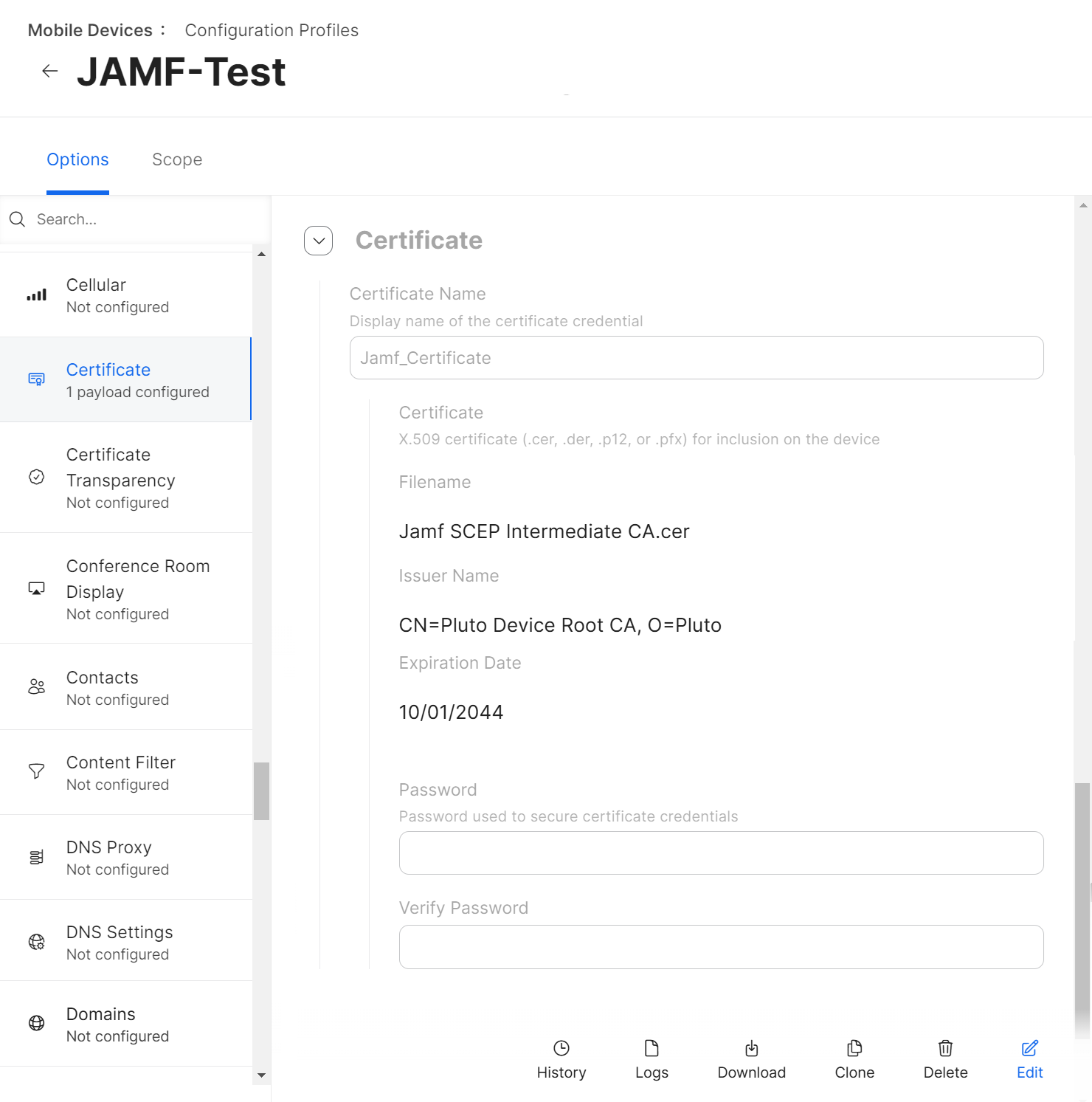
NOTE: If the setup has more than one RADIUS server for validation, you can add more than one Common Name with the same certificate payload configuration.
NOTE: Do not upload the actual RADIUS server certificate here.
This section explains how to set up a Certificate Payload for RADIUS Connections. It applies to both iOS and macOS configuration profiles.
Setting up the Wi-Fi Payload
The WiFi profile/payload helps in configuring the device to connect to the preferred secure network. Jamf includes built-in Wi-Fi settings that the admin can configure and deploy to the devices in your organization.
This Wi-Fi profile can be assigned based on different Device users and Device groups.
This section explains how to set up Wi-Fi Payload for iOS and macOS devices.
To set up the Wi-Fi Payload for iOS, perform the following steps:
- From your Jamf Pro console, go to Devices > Configuration Profiles. For macOS devices, navigate to Computers > Configuration Profiles > Edit > Options > Network. Steps 4 to 16 are similar for both the iOS and macOS configuration profiles.
- Click Edit for the configuration profile you want to configure.
- Select Options > Wi-Fi.
- Click Configure.
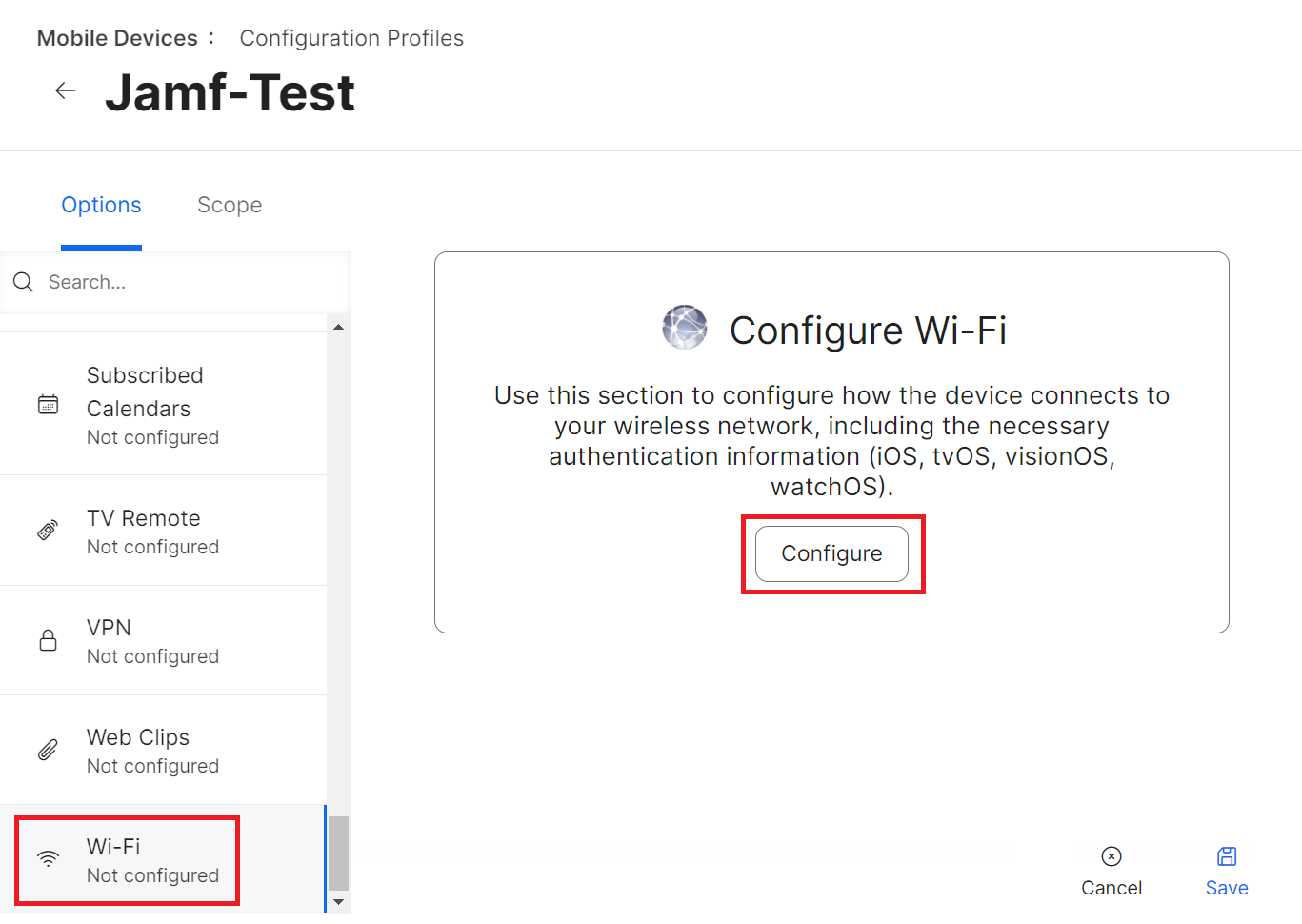
- In the Service Set Identifier (SSID) field, enter the name of the secure network.
- Select other applicable settings as per the organization’s requirements.
- From the Security Type drop-down list, select WPA2 Enterprise (iOS 8 or later except Apple TV).
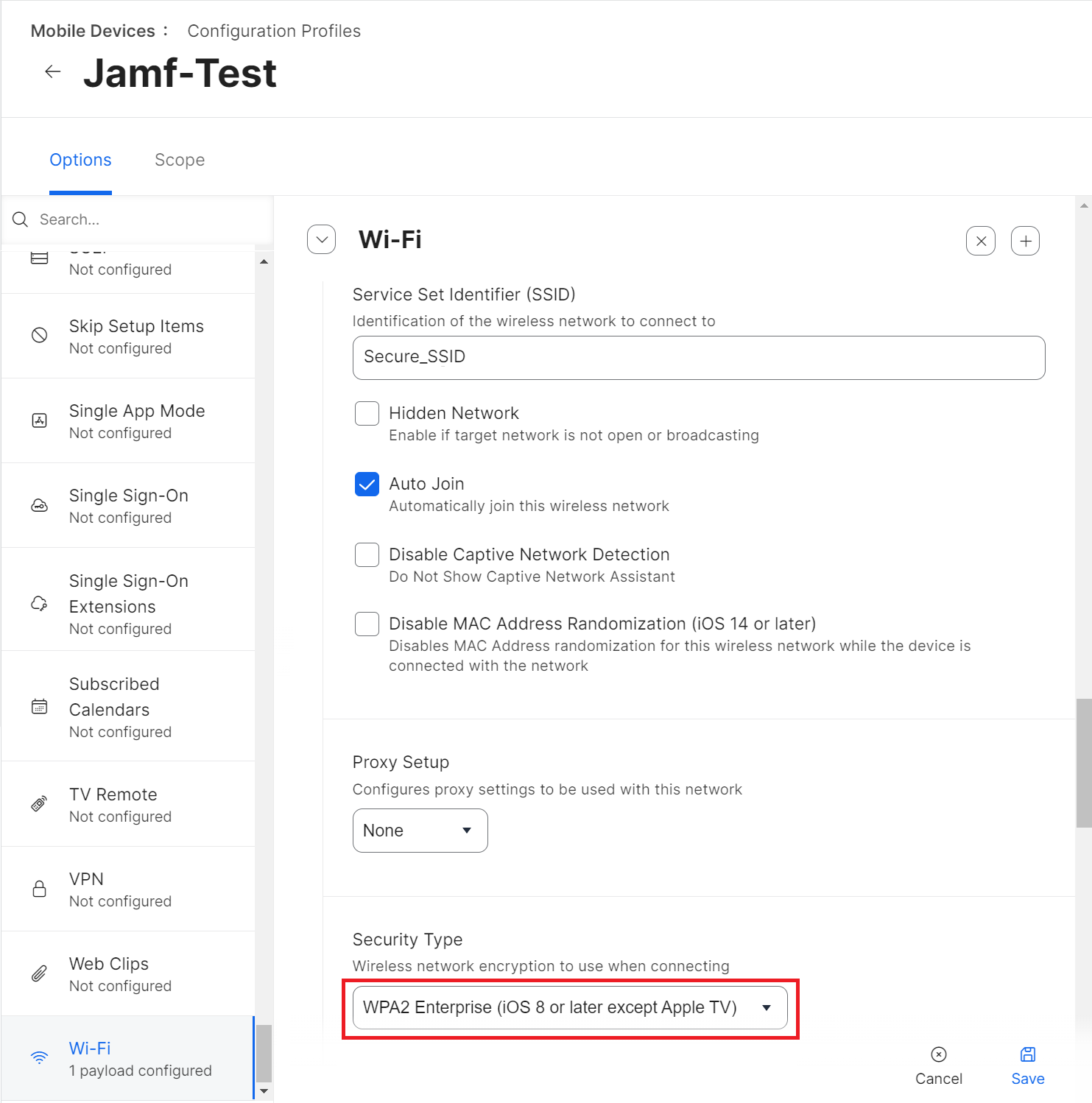
- Under the Network Security Settings section, select the Protocols tab.
- In the Accepted EAP Types section, select the TLS checkbox.
- Click the Trust tab.
- In the Trusted Certificates section, select the checkbox for the certificate you uploaded.
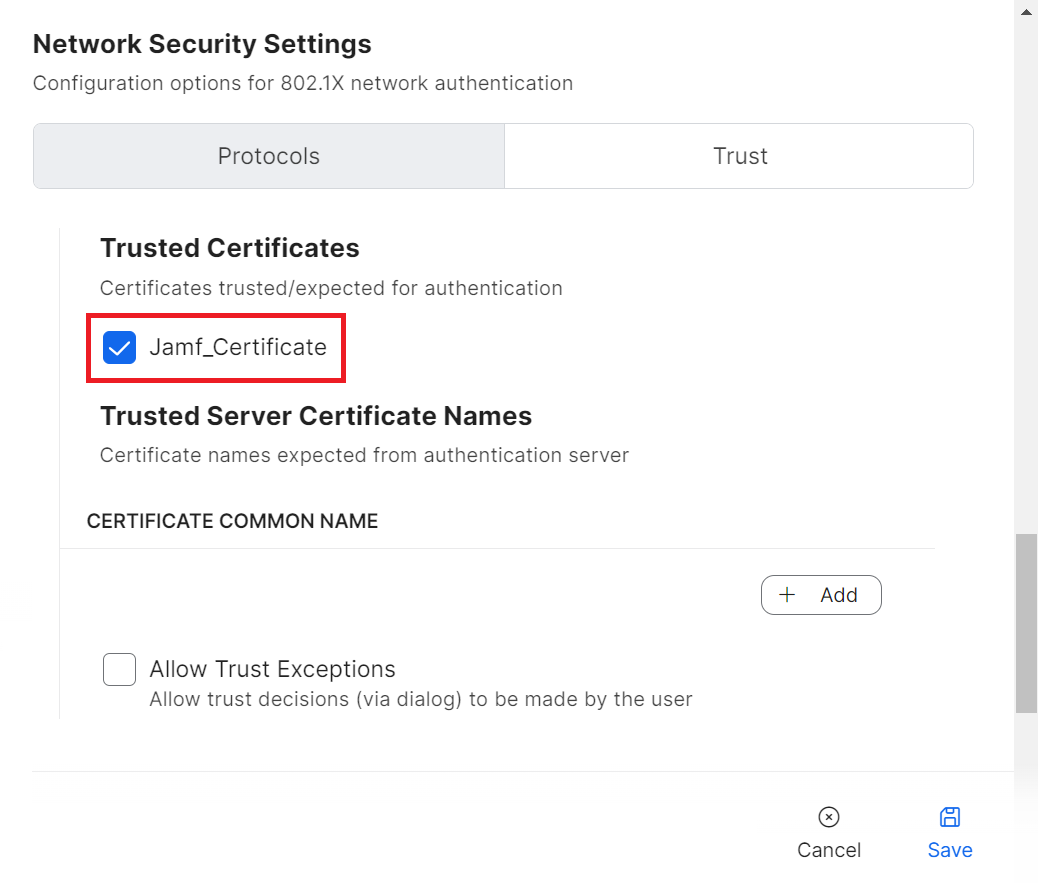
NOTE: Along with validating a RADIUS server by certificates, specify the RADIUS server certificate names for validation as an additional security measure. This is available in the Wi-Fi payload when the uploaded certificate is enabled. - In the CERTIFICATE COMMON NAME section, click + Add.
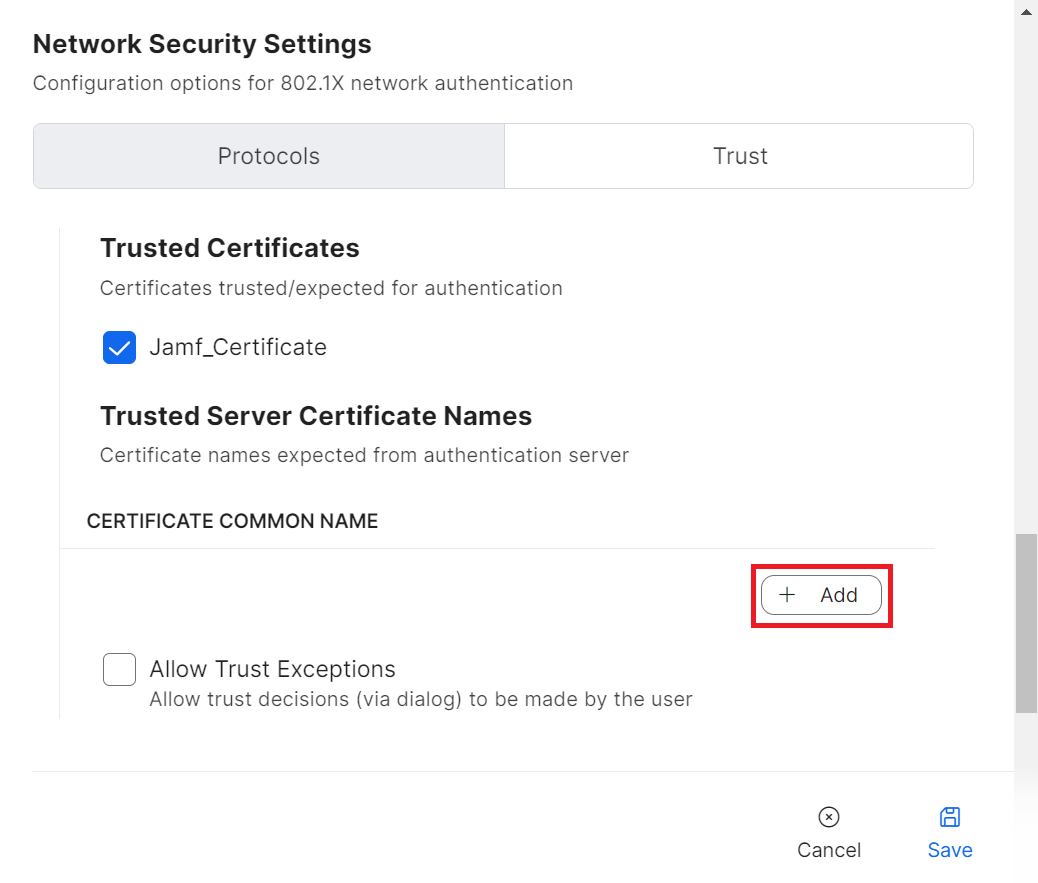
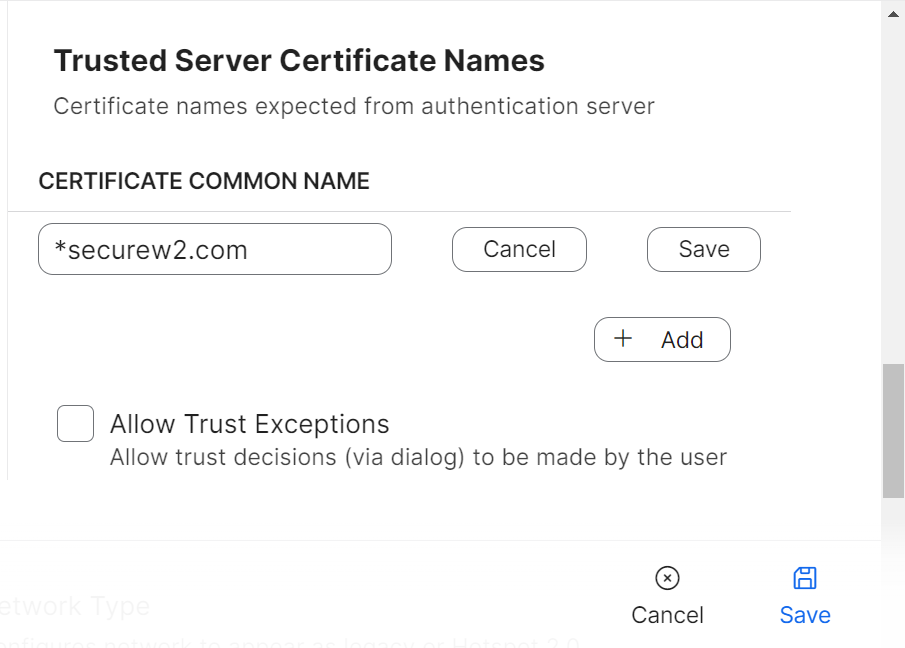
- In the field that appears, enter the name of the RADIUS server used for validation, and then click Save.
- Navigate back to the Protocols tab.
- From the Identity Certificate drop-down list, select the CA from the SCEP payload.
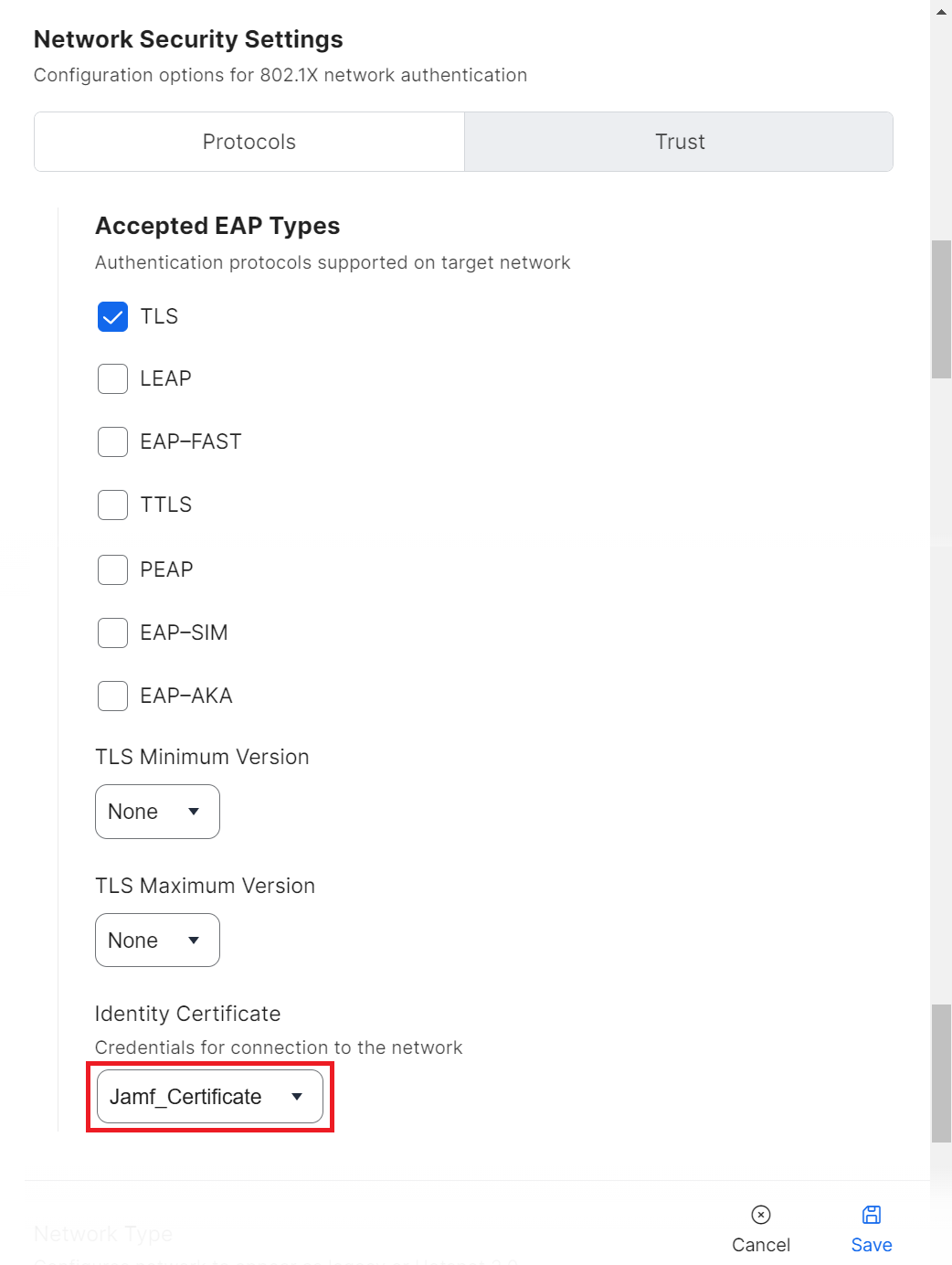
- Click Save to save the Wi-Fi payload.
When a device successfully enrolls, the Configuration Profiles table shows an increased value for Completed.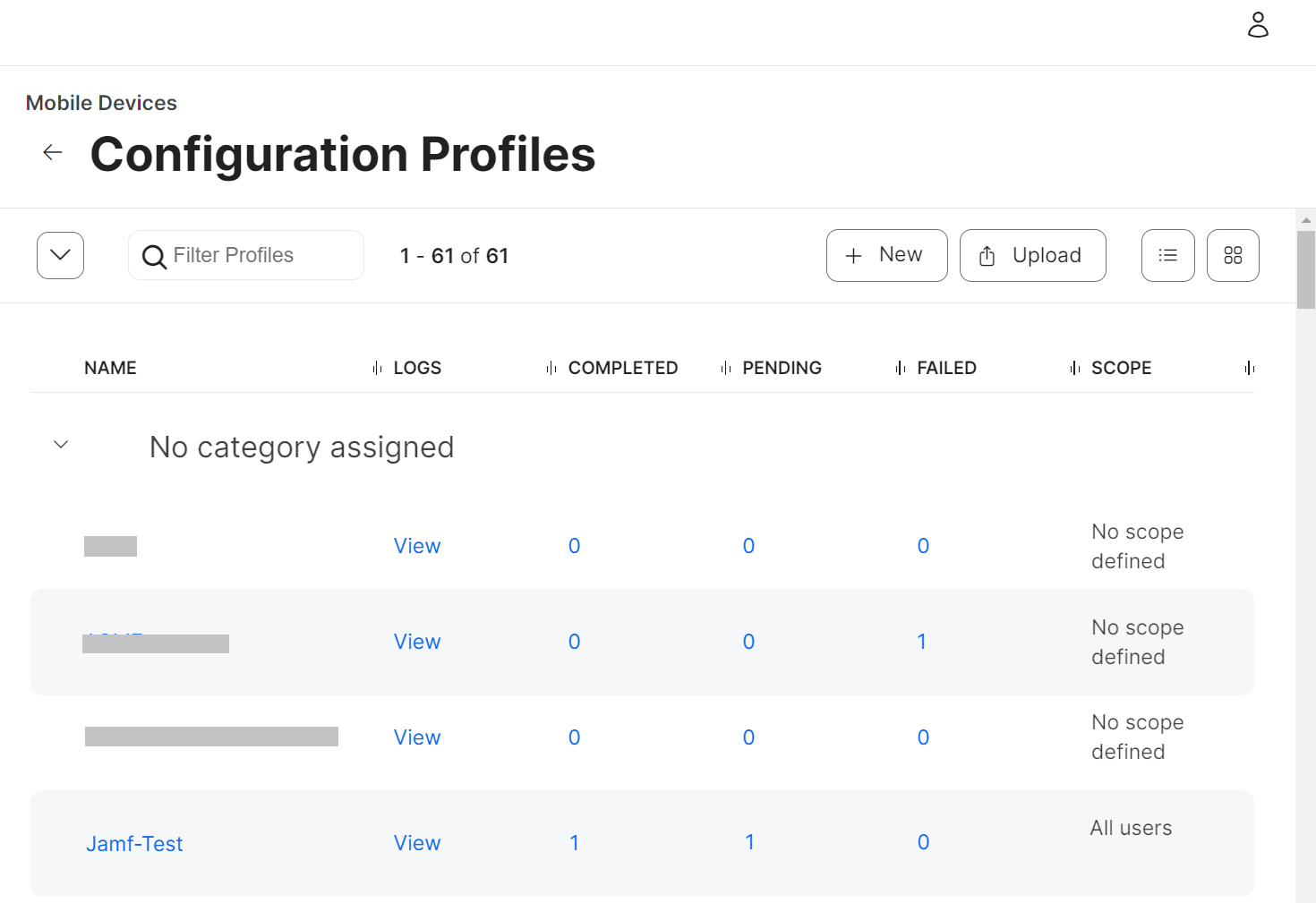
Integrating JoinNow with Okta for RADIUS Authentication
The following are the high-level configurations required for setting up RADIUS Authentication in JoinNow via Okta:
Creating an API Token in Okta
Cloud RADIUS talks directly with Okta (no LDAP required) using an API. To create an API Token, perform the following steps:
- Log in to the Okta Portal.
- On the left pane, from the Security menu, select API.
- Select the Tokens tab and on the displayed screen, click the Create token button.
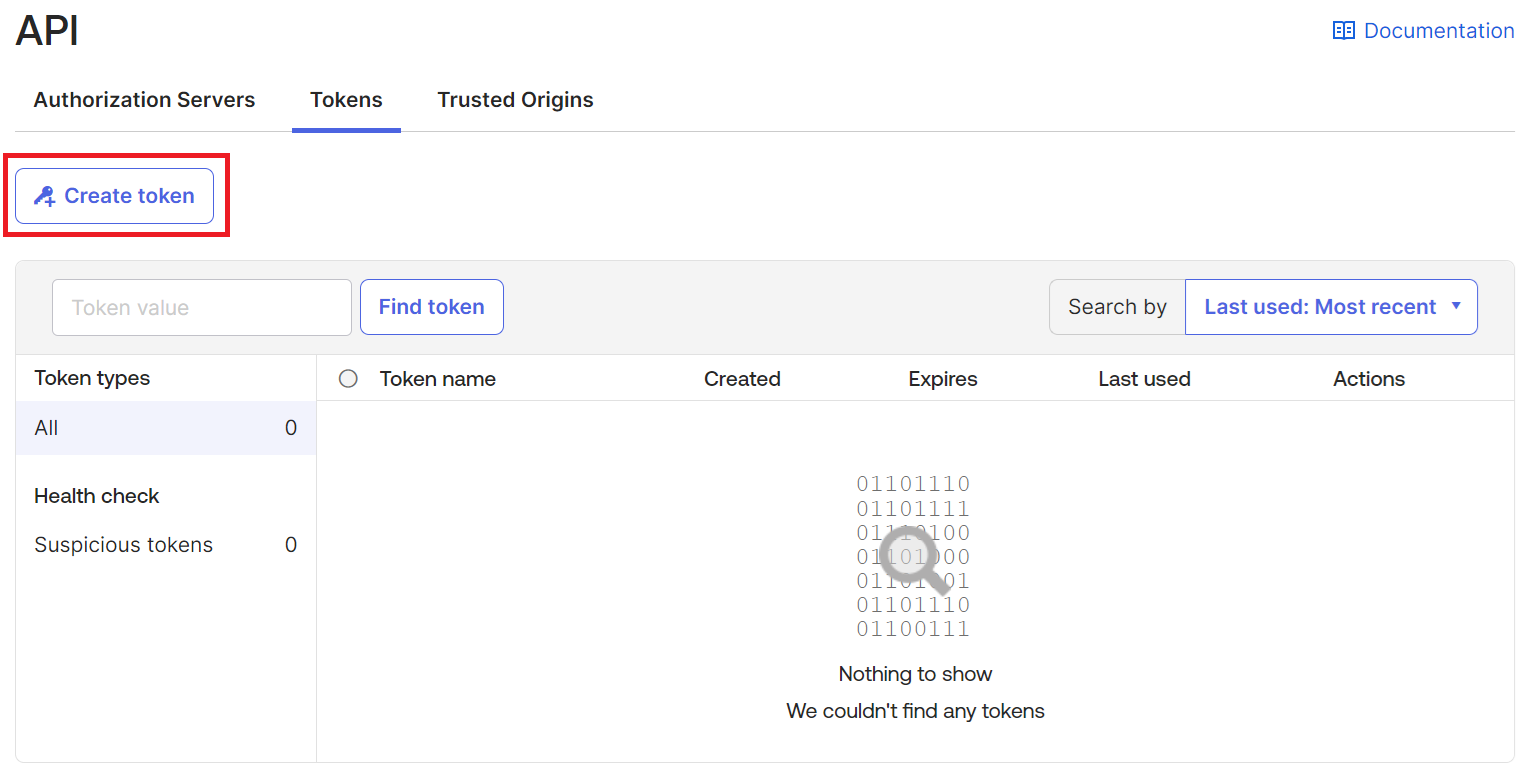
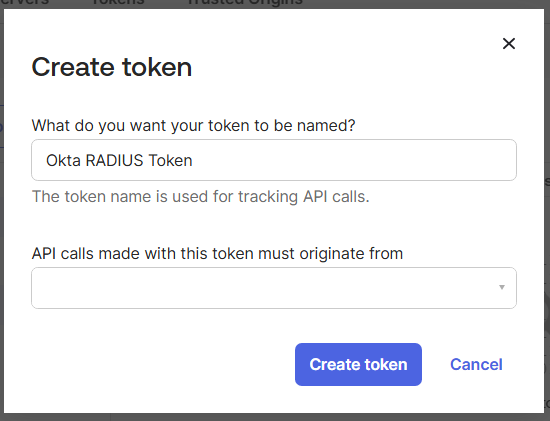
- In the Create token dialog box, enter a name for the token.
- From the API calls made with this token must originate from drop-down list, select the required API source(s).
- Click Create token.
- On the displayed screen, copy the token value to your console.
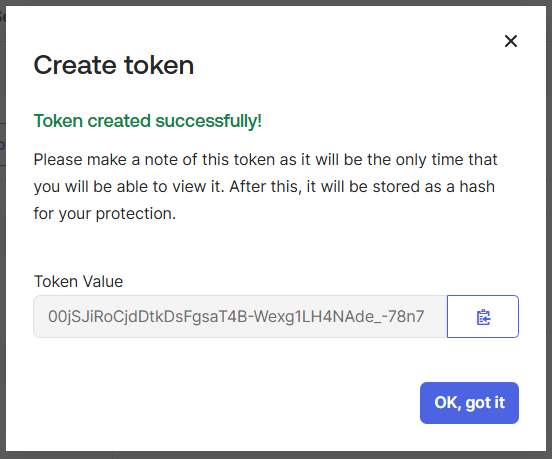
NOTE: Ensure that you save the token value on your console.
Integrating Okta with SecureW2’s CloudRADIUS
After we’ve created the API Token in Okta, we can configure the policies in the JoinNow Management Portal. These policies validate the certificate each time a Wi-Fi connection request is made, along with the user’s account status in Okta. This ensures that network access is dynamically authorized based on the user’s real-time status in Okta.
Creating a Core Platform
To create a Core Platform, perform the following steps:
- Navigate to Integrations Hub > Core Platforms.
- Click Add.
- In the Basic section, enter the name of the core provider in the Name field.
- In the Description field, enter a suitable description for the core provider.
- From the Type drop-down list, select Okta Identity Lookup.
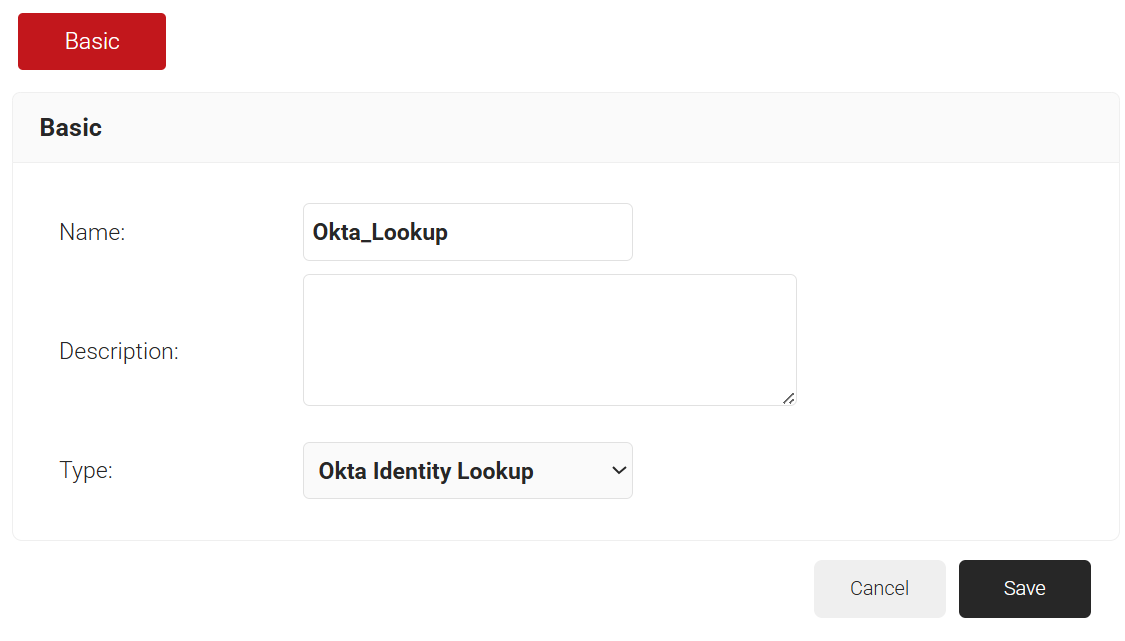
- Click Save.
- The page refreshes and displays the Configuration, Attribute Mapping, and Groups tabs.
- Click the Configuration tab.
- Under the Configuration section, Okta has two types of configurations available:
- Auto – Uses API token to automatically configure lookup with the Okta portal. Generating an API Token needs Super Admin privileges in the Okta Portal.For Auto Configuration:
- In the Provider URL field, enter your Okta organization URL. For example, https://dev-123456.okta.com/.
NOTE: Do not use “admin” in the organization URL, as lookup fails.
- In the API Token field, enter the token you obtained from the Okta portal (see the Creating an API Token section).
- Click Validate to check the connection with Okta.
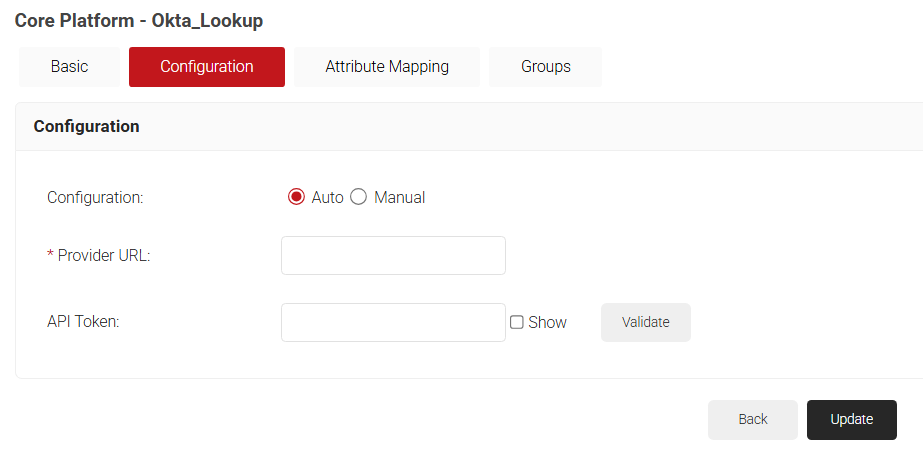
- Click Update.
- In the Provider URL field, enter your Okta organization URL. For example, https://dev-123456.okta.com/.
- For Manual Configuration:
- Click on the Manual radio button.
- In the Provider URL field, enter the Provider URL of your Okta account. For example, https://dev-123456.okta.com/.
- In the Client ID field, enter the client ID obtained from creating a lookup application in Okta.
- For the JWKS Key Pair field, click Choose File. Upload the Key Pair file saved from Okta.
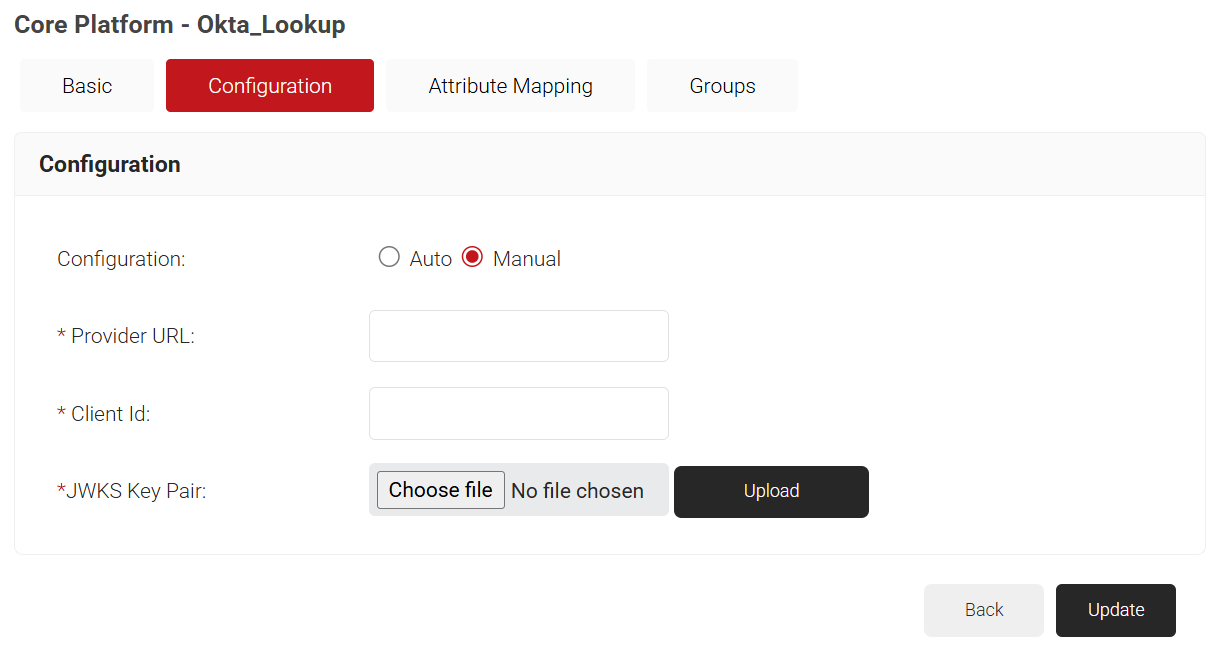
- Click Update.
- Auto – Uses API token to automatically configure lookup with the Okta portal. Generating an API Token needs Super Admin privileges in the Okta Portal.For Auto Configuration:
NOTE: If the Signal Source is deleted in the JoinNow Management Portal, the SAML app in the Okta portal is also deleted. API Token needs manual deletion.
Configuring Attributes
To add a custom attribute to the Identity Lookup Provider, follow the steps below.
- Navigate to Integrations Hub > Core Platforms.
- Click the Edit link on the Core Provider created earlier (refer to the Creating a Core Platform section).
- Click the Attribute Mapping tab.
- From the Attribute Type drop-down, select the category to display the recommended attributes. The following are the attribute types offered by JoinNow for Okta Lookup:
- User
- Custom
- Click Update after selecting the required attributes.
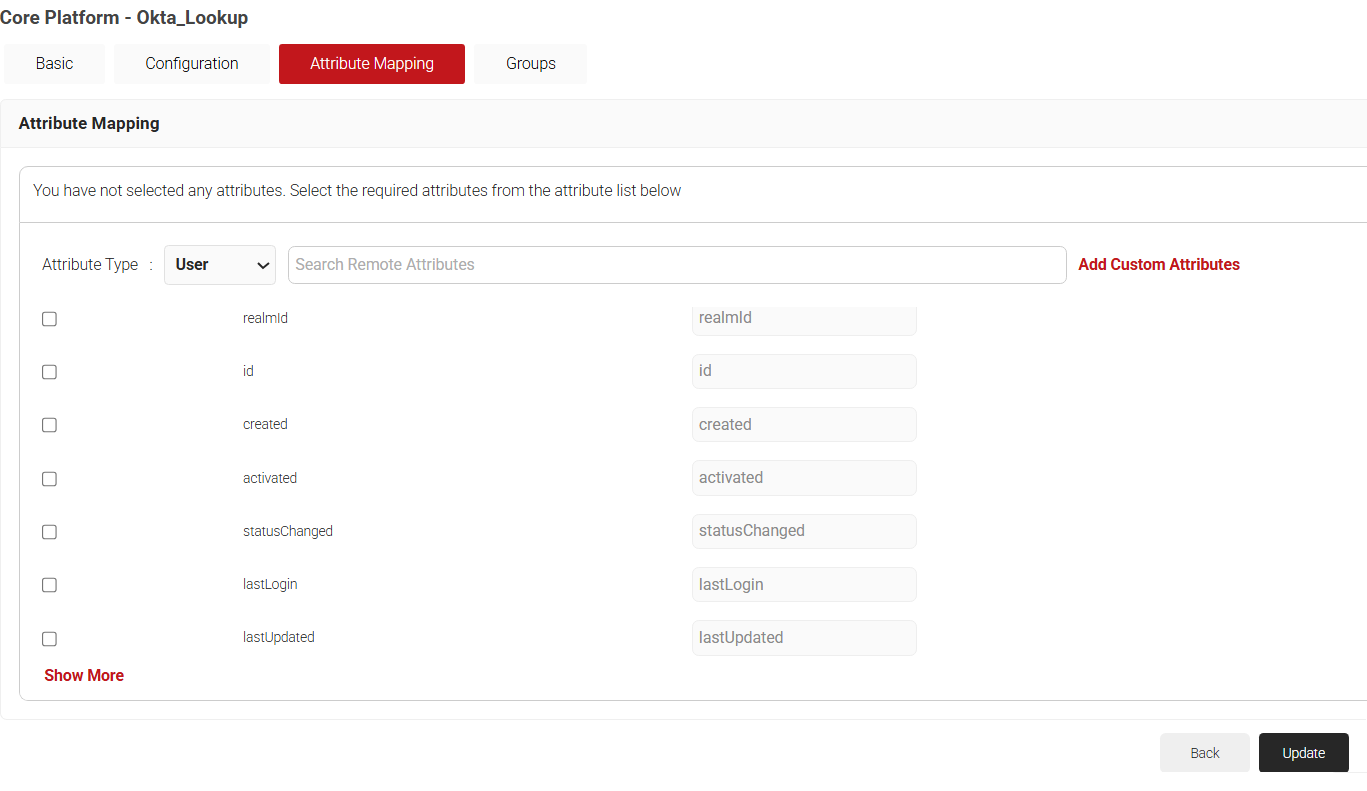
Configuring Groups
Here is where we will map the group attributes we want to use in our network policies.
- Navigate to Integrations Hub > Core Platforms.
- Click the Edit link on the Signal Source created earlier (refer to the Creating a Core Platform section).
- Navigate to the Groups tab.
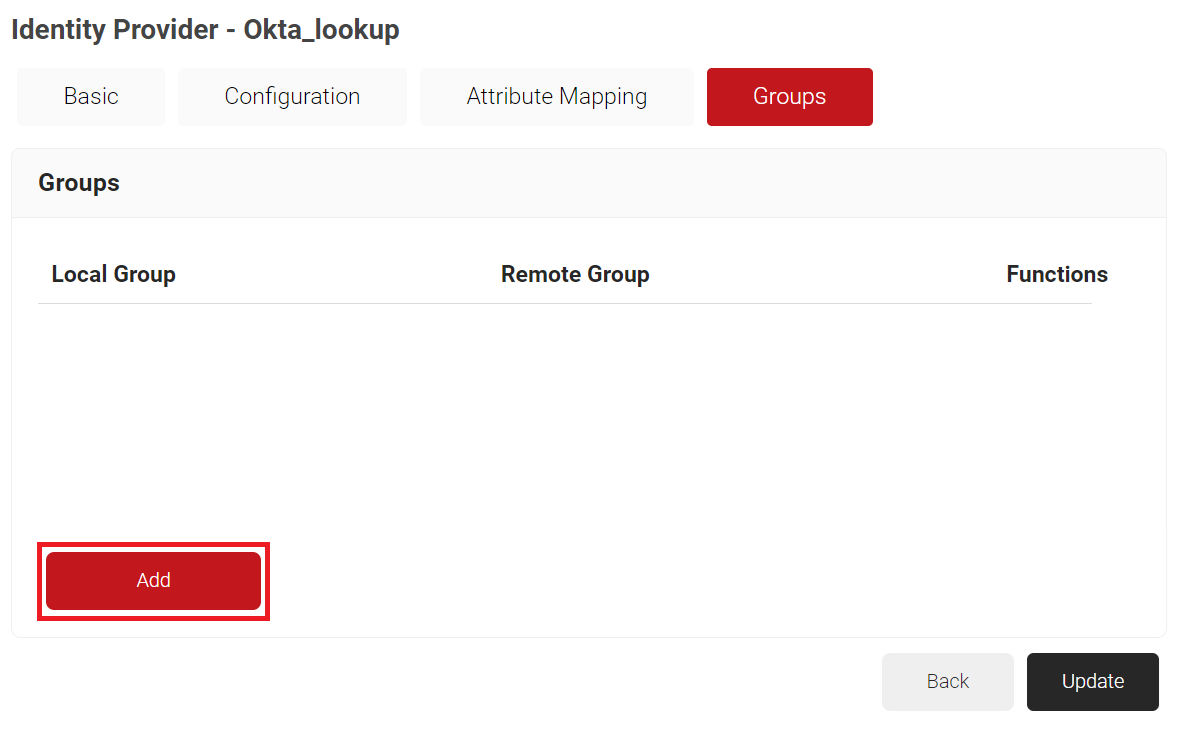
- Click Add.
- In the Local Group field, enter a name for the group. This group name can be used to configure network policies.
- In the Remote Group field, enter the name of your group as it is configured in the Okta portal.
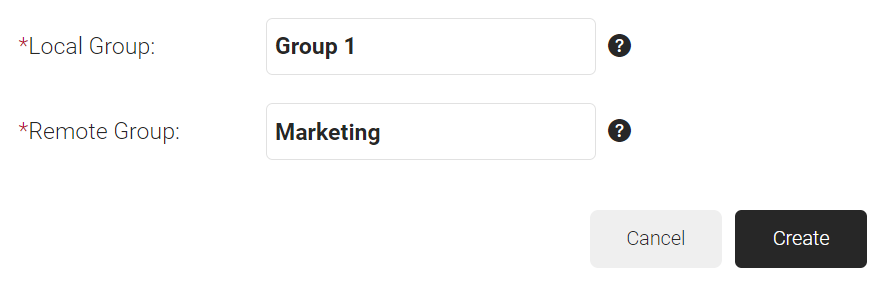
- Click Create.
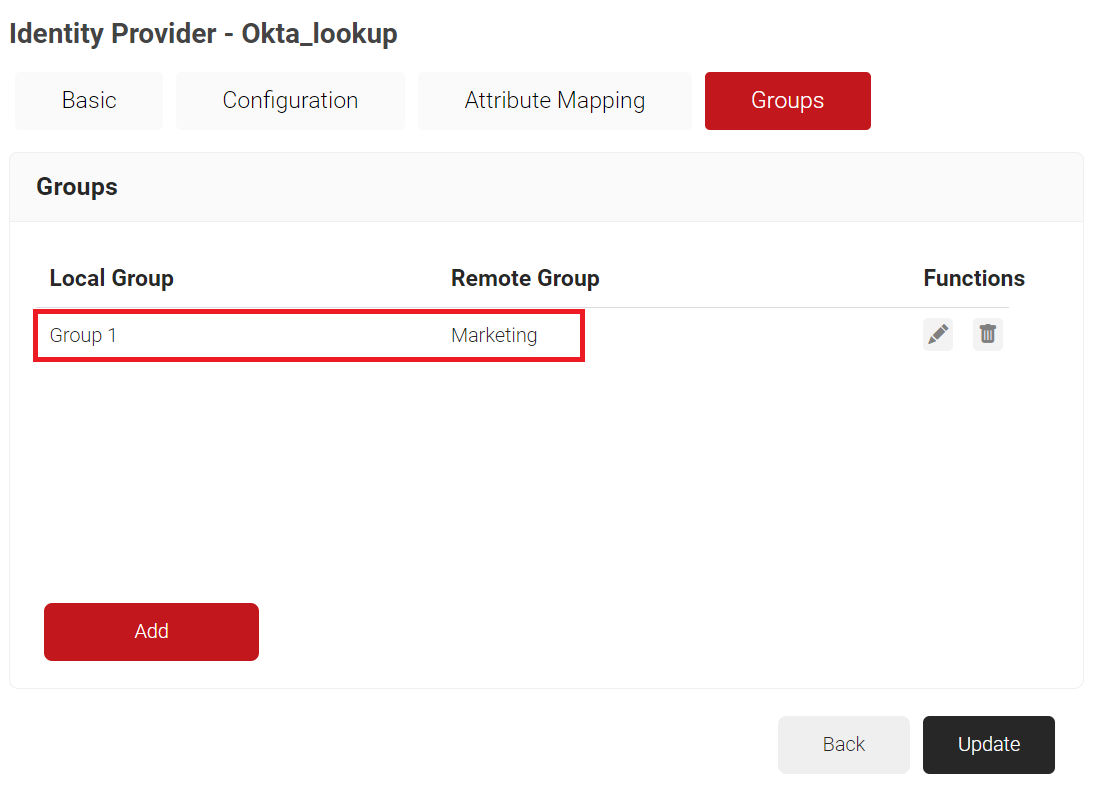
NOTE: Repeat the process as required for the groups you wish to create network policies around.
Configuring Policies
The following policies need to be configured:
Configuring a Security Signal Source
Lookup Policies tie our new Signal Source to domains. Here, we will create a condition that ties our domain to the new Signal Source we created in the previous section (see the Creating a Core Platform section).
- Navigate to Policy Management > Security Signal Sources.
- Click Add Security Signal Source.
- In the Basic section, enter the name of the Security Signal Sources in the Name field.
- In the Display Description field, enter a suitable description for the Security Signal Sources.
- In the Lookup Purpose field, select the RADIUS Authentication checkbox to add the policy to the RADIUS Authentication workflow.
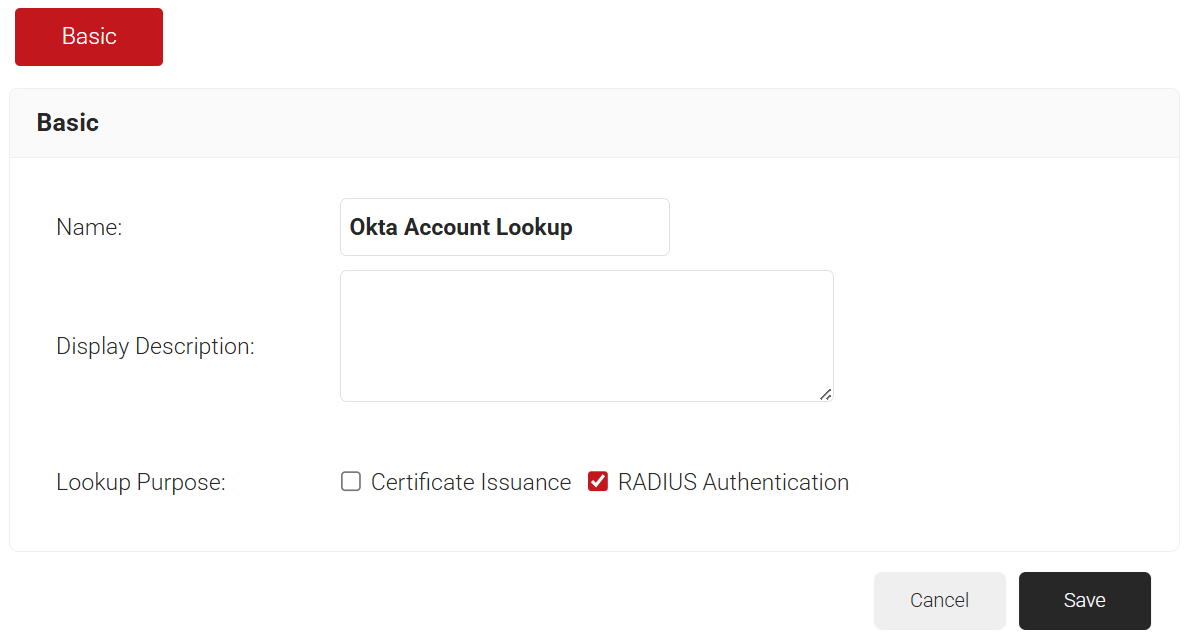
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
- Under the Conditions section, from the Provider drop-down list, select the management platform created in joinNow in the Creating a Device Management Platform section.
- From the Identity drop-down list, select Subject-CommonName under Certificate.
- Configure Regex to match the values of your devices configured in the Identity field.
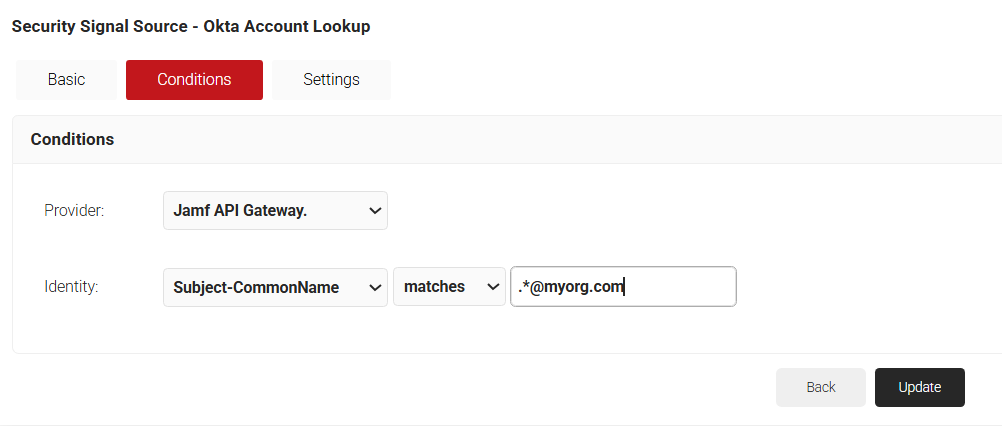
- Click Update.
- Select the Settings tab.
- Under the Settings section, from the Provider drop-down list, select the Signal Source created in the previous section (see the Creating a Core Platform section).
- From the Lookup Type drop-down list, select User. From the Identity drop-down list, select Subject-CommonName under Certificate.
- Select the Revoke On Failure checkbox to automatically revoke a certificate if an account lookup fails, if necessary.
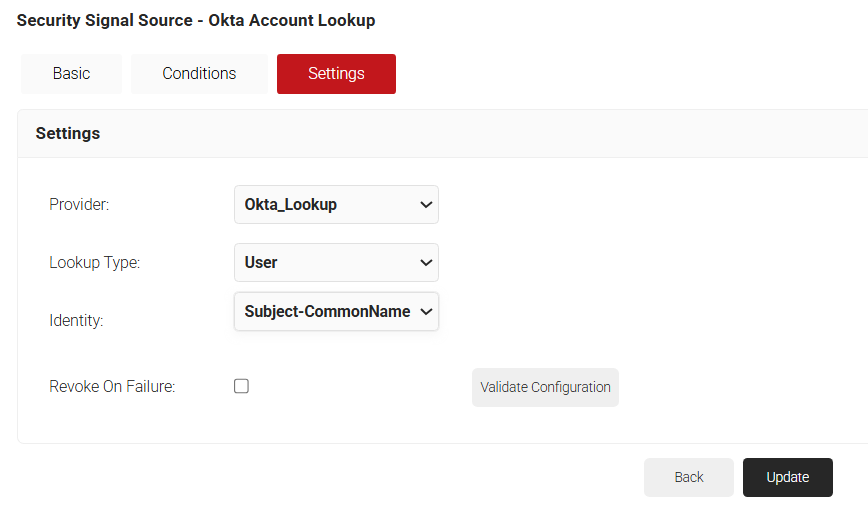
- Click the Validate Configuration button to check if the lookup is valid.
- On the Validate Configuration pop-up window, in the Enter a valid identity field, enter the identity (user/device) to validate the lookup, and click Validate.
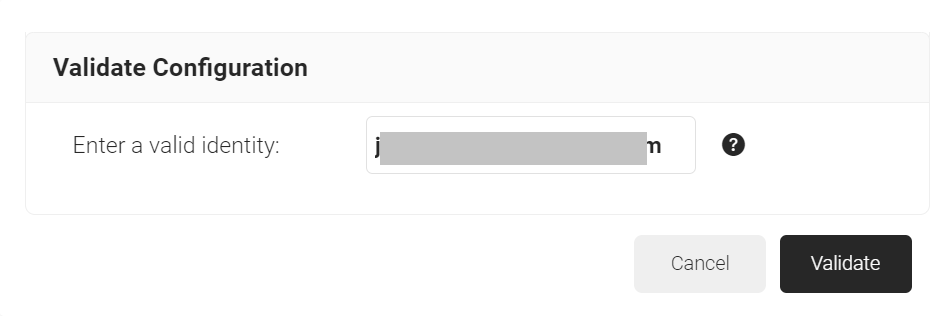
- After the successful validation, the associated attributes and groups of the Signal Source are displayed on the Lookup Details prompt. The admin can use this information to configure the network policies and verify the user’s validity.
NOTE: When the Admin enters an invalid identity on the Validate Configuration pop-up window, the following error message is displayed: “Account lookup failed.”
- Click Update.
Configuring Policy Workflow
Policy workflows will be used by Cloud RADIUS Dynamic Policy Engine to lookup user status at the moment of authentication. Then, Cloud RADIUS can dynamically apply Network policies, which you will configure next.
- Navigate to Policy Management > Policy Workflows.
- Click Add Policy Workflows.
- In the Name field, enter the name of the Policy Workflow.
- In the Display Description field, enter a suitable description for the Policy Workflow.
NOTE: Ensure that you create a separate Policy Workflow for authentication.
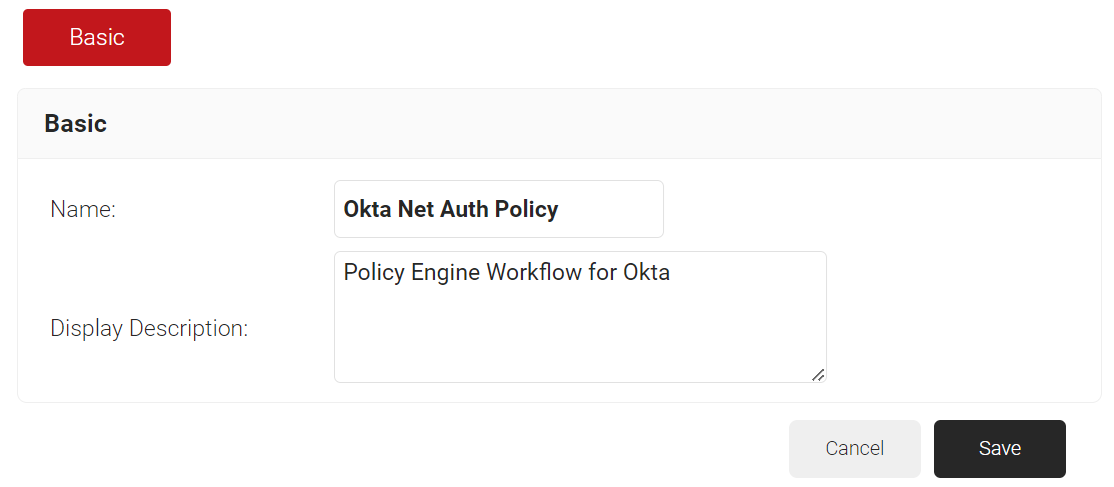
- Click Save.
- The page refreshes and displays the Conditions tab.
- Select the Conditions tab.
- From the Core Provider drop-down list, select the Okta Identity Lookup Provider created in the previous section (see the Creating a Core Platform section).
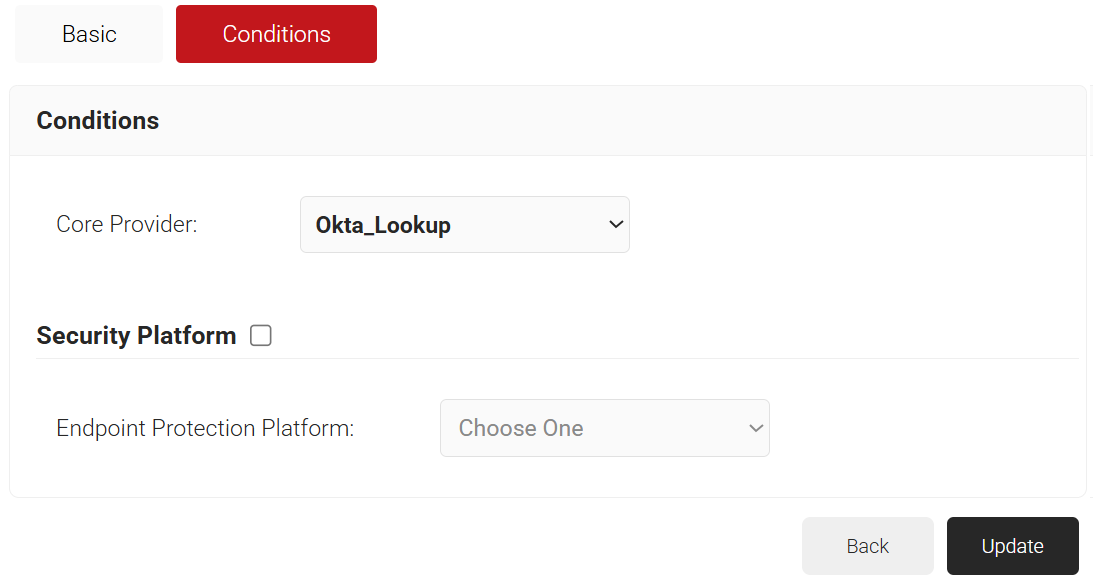
- Click Update.
Configuring Network Policy
A network Policy specifies how Cloud RADIUS will authorize access to a particular Policy Workflow.
A typical Network Policy would say something like the following: “If User Role = Staff, authorize access and assign them to VLAN 2.”
You can configure any RADIUS Attribute to be sent to the wireless controller. If you leave the attribute section blank, it will just send an Access Accept message.
To create and configure the Network Policy, follow the steps below:
- Navigate to Policy Management > Network.
- On the Network page, click Add Network Policy.
- In the Basic section, in the Name field, enter the name of the network policy.
- In the Display Description field, enter a suitable description for the network policy.
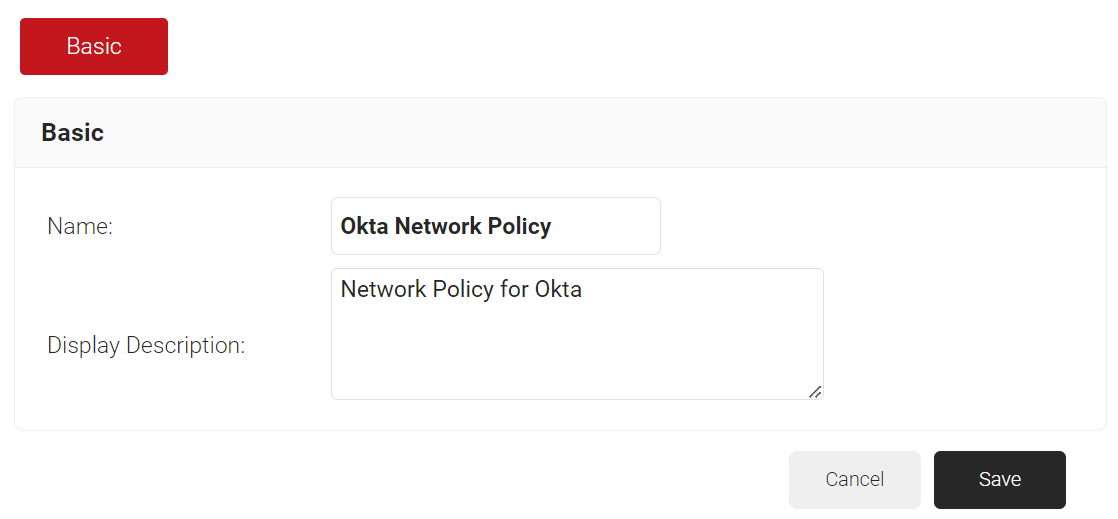
- Click Save.
- The page refreshes and displays the Conditions and Settings tabs.
- Select the Conditions tab.
- Select Match All or Match Any based on your requirements to set authentication criteria. In the case explained here, we are selecting Match All.
- Click Add rule.
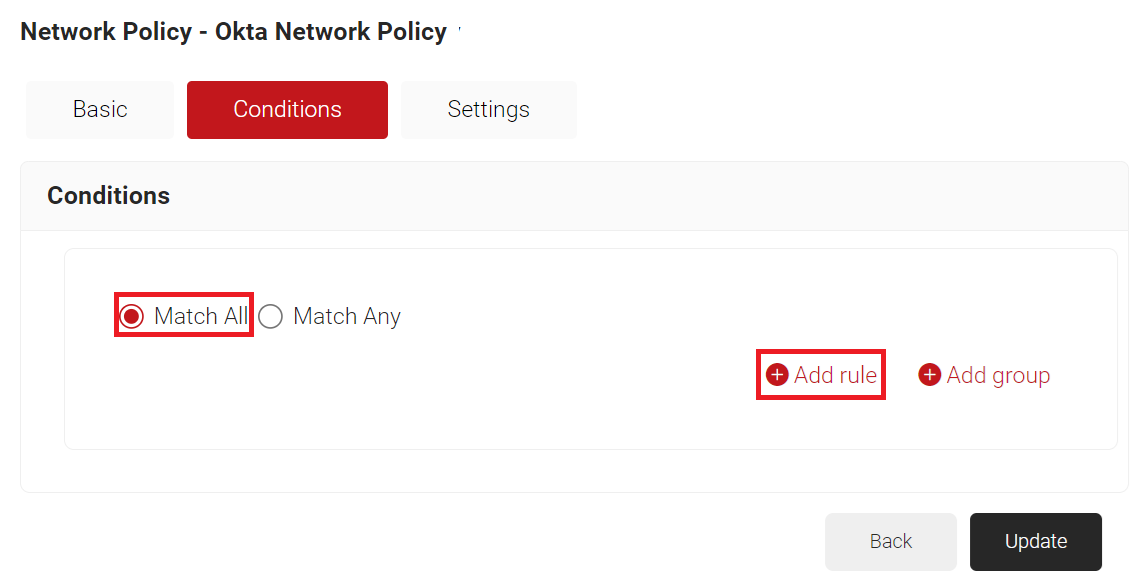
- Expand Device and select the Device Role option.
- Expand Identity and select the Role option.
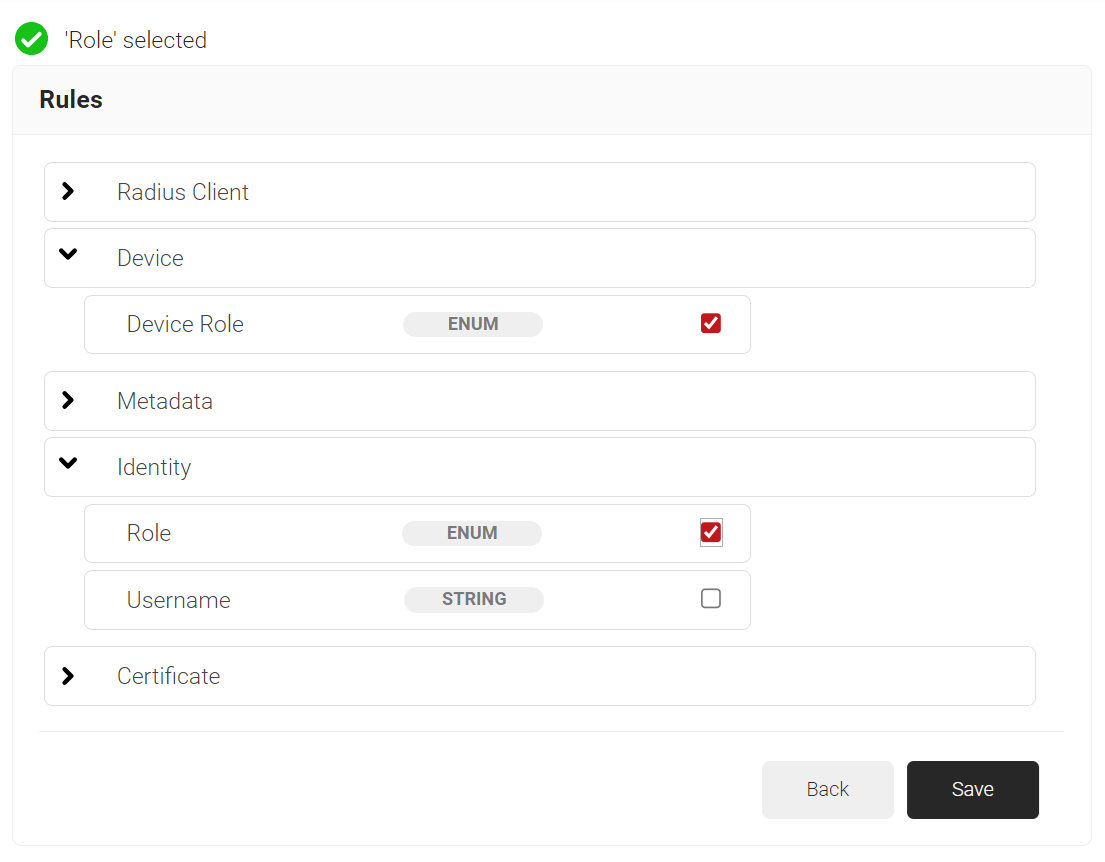
- Click Save.
- The Device Role and Role options appear under the Conditions tab.
- From the Device Role drop-down list, select the default device role policy.
- From the Role Equals drop-down list, select the Policy Workflow you created earlier (refer to the Configuring Policy Workflow section). You can select multiple Policy Workflows to assign to a Network Policy.
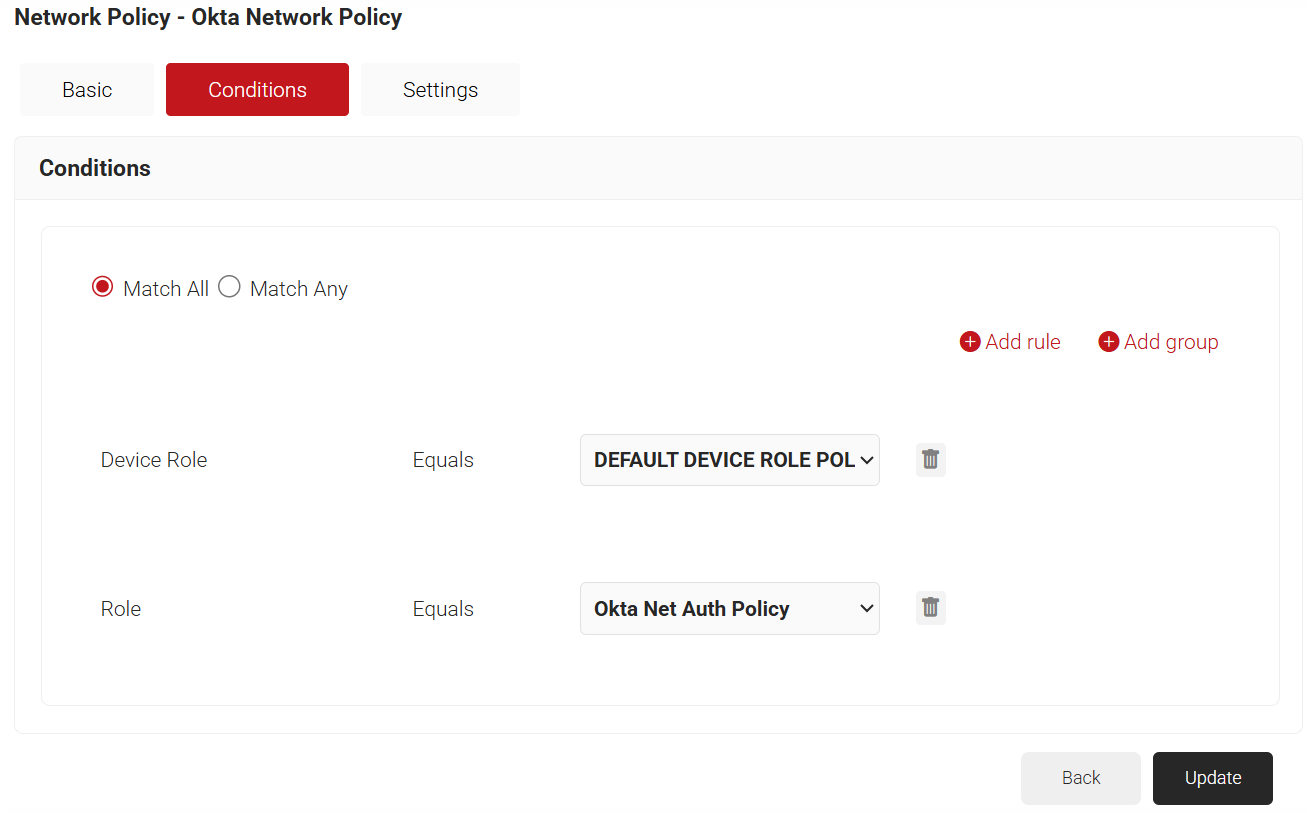
NOTE: You can assign a network policy to multiple user roles. - Select the Settings tab.
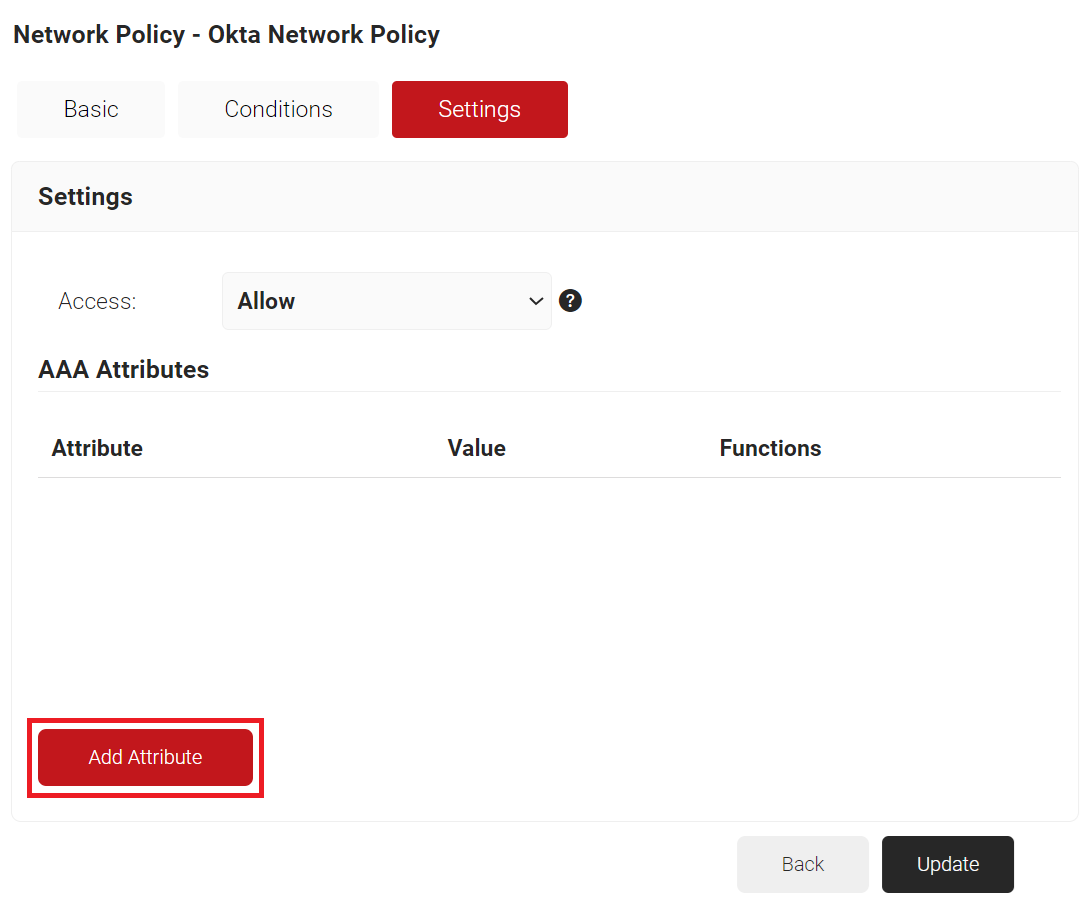
- Click Add Attribute.
- From the Dictionary drop-down list, select an option: Radius: IETF or Custom.
- From the Attribute drop-down list, select an option.
- In the Value field, enter the appropriate value for the attribute.
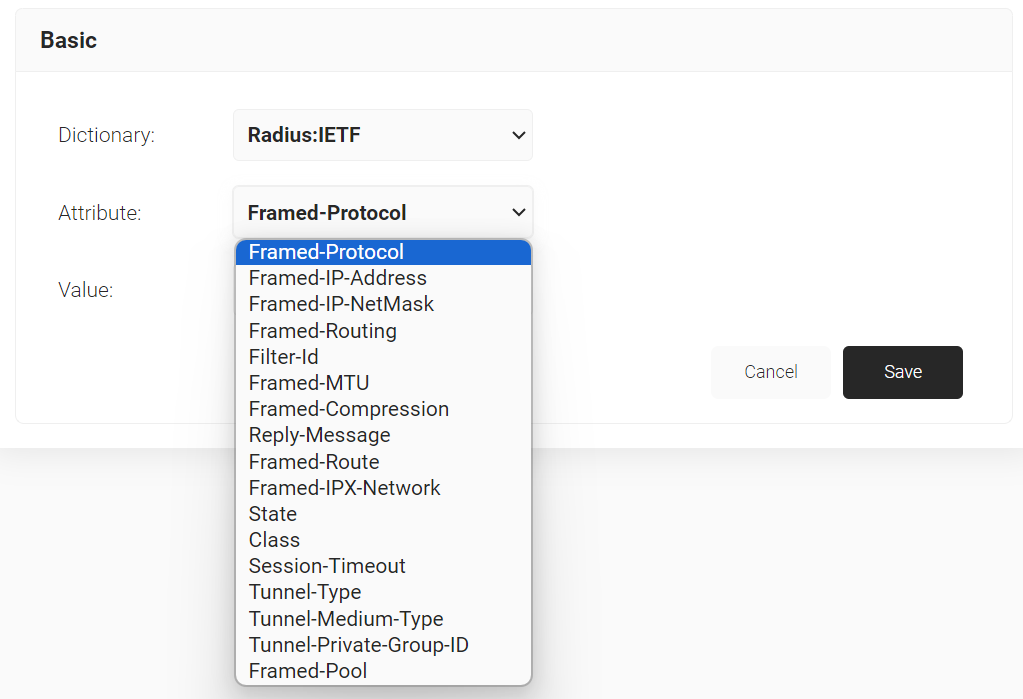
- Click Save.
- Click Update.
NOTE: Repeat the process for all the attributes you want to send to the Policy Workflow.